There’s been an evolution in the threat landscape in recent years, with threat actors relying more on social engineering tactics to prey on human vulnerability and execute their attacks. The top vector for deploying this attack strategy? Email. Attackers are using everything from ransomware and credential phishing to business email compromise (BEC) and supply chain attacks. That’s why choosing the right email security solution is essential to protecting your business.
Research and consulting firm Frost & Sullivan recently published its Frost RadarTM: Global Email Security Market, 2020 report, which analyses the global market for email security and leading vendors in terms of growth and innovation. The report is designed to help organisations choose an email security solution that best fits their needs. And we’re pleased to announce that Frost & Sullivan has recognised Proofpoint as a leader in email security.
In a field of more than 34 global industry participants, Frost & Sullivan’s analysis gave Proofpoint the highest score in both the Growth Index and the Innovation Index. Proofpoint is able to deliver on this by providing our customers with the following:
Risk Reduction Through Integrated Threat Detection
As mentioned earlier, threat actors are using everything from ransomware to credential phishing to BEC to supply chain attacks. And they’re relentless. An effective email security solution that reduces risk needs to provide a multi-layered, integrated offering. If the solution you’re using is only effective at detecting one type of threat, you’re still exposed to other threats. Not only does that increase your risk of experiencing a breach and financial loss, but it also increases the workload for your security teams.
Proofpoint delivers the most effective detection across multiple threats because of our machine learning and artificial intelligence (AI), the broad data we analyse across multiple vectors, and our expert human threat analysts. We analyse more than 2.2 billion emails, 35 billion URLs and 200 million attachments per day. We also monitor over 35 million cloud accounts and more than 400 million domains. And our global threat research team tracks over 100 threat actors.
Our Threat Protection Platform is integrated to provide end-to-end protection from prevention to detection to remediation. For example, we can identify an organisation’s most risky users or Very Attacked People™ (VAPs). Then, we can put isolation policies around those users for safe browsing and even arm them to identify suspicious messages based on how they’re being attacked. If a user reports a message, we automatically analyse it and quarantine that message if it’s malicious. Importantly, we can then find all the other messages in the organisation and quarantine them as well.
Proofpoint also integrates with the broader security ecosystem to apply adaptive controls around users and share threat intelligence for extended detection and response (XDR). We integrate with CrowdStrike, Okta, SailPoint, Palo Alto Networks and many others.
Unique People-Centric and Supplier Risk Visibility
Mitigating risk is every security team’s top goal. But prioritising security alerts and knowing which controls to apply—and to whom—and predicting their impact on risk is challenging. To help with this process, we provide our customers with the Nexus People Risk Explorer to gain visibility and actionable intelligence into the risks each user poses to the broader organisation by:
- Identifying user vulnerability, attack and privilege to build a risk profile
- Segmenting users based on the similarity of their profiles
- Recommending specific security controls to mitigate risk, reduce costs and save time
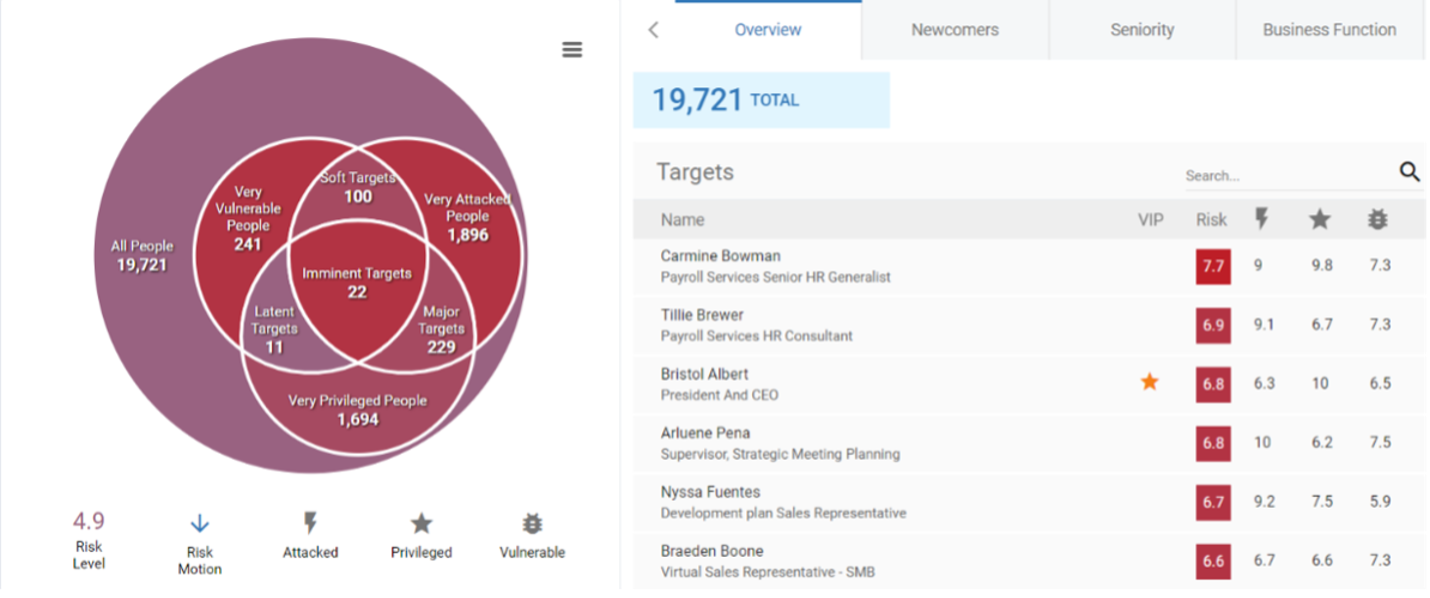
Figure 1: Nexus People Risk Explorer dashboard
You can read more about the Nexus People Risk Explorer here.
Proofpoint also provides visibility into supplier vendor risk through Supplier Risk Explorer, which helps organisations overcome the challenge of complex supply chain attacks. Supplier Risk Explorer automatically identifies your suppliers and the domains they use to send email to your users.
Integrated with Proofpoint’s industry-leading Threat Protection Platform, Supplier Risk Explorer analyses your email communications and provides a supplier-centric view of threats. It reveals the message volume, the threats detected from supplier domains, and the messages blocked from malicious lookalikes of your suppliers’ domains.
Supplier Risk Explorer then assesses the risk level of these supplier domains by evaluating several dimensions, including:
- Threats sent to your organisation
- Threats sent to other Proofpoint customers
- The lookalikes of supplier domains
- Whether the domain was recently registered
- Whether the domain has a DMARC reject policy
By ranking and prioritising the risk level of your supplier domains, your security team can see and prioritise which suppliers require the most attention.
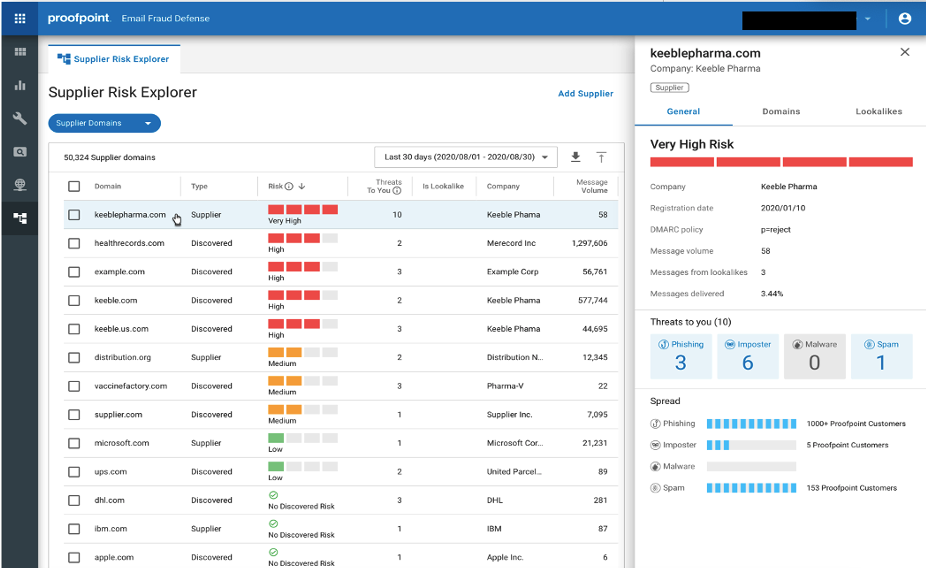
Figure 2: Supplier Risk Explorer dashboard
Operational Impact
The economic downturn due to the global pandemic has security teams doing more with less. Attackers are ruthless and security professionals are stretched. What security teams need are solutions that can help reduce the burden.
Proofpoint stops more threats before they reach the inbox and become incidents, reducing the incident response load. Equally, if not more, important, is that we can accurately detect and stop bad messages without blocking good emails. Email security solutions that generate a ton of false positives ultimately undermine the productivity of security teams, messaging teams and end users.
Proofpoint also provides SOAR capabilities that automate key incident investigation and response actions related to email threats. The volume of alerts, combined with the high likelihood that email threats can do your organisation real harm and the need for a rapid response to those threats, creates the perfect storm for automation.
Proofpoint can automatically identify all instances of a malicious email across the organisation and remove them all, including forwarded messages and messages sent to distribution lists. Customers have shared that this capability is game-changing, as what once took their security teams hours of highly manual work is now accomplished in minutes.
Get your complimentary copy of the Frost RadarTM: Global Email Security Market, 2020 report today to learn more about why Frost and Sullivan recognises Proofpoint as a leader in email security.











