Mitigating risk is every security team’s top goal. But prioritizing security alerts and knowing which controls to apply—and to whom—and predicting their impact on risk is challenging. Many organizations take a threat-centric approach to determine which controls to place around their most attacked users to reduce the risks they see in their environment. However, this is an incomplete view of risk.
Additionally, digital transformation and the related adoption of cloud applications and platforms have added another layer of security complexity for many organizations. Traditional network security approaches don’t provide the same level of protection because people bypass the network to access cloud apps. Having visibility into applications and traffic is important. But gaining visibility into all types of risk impacting an organization becomes harder with more variables to track.
According to the 2020 Data Breach Investigations Report from Verizon, the most successful attacks originate from stolen credentials; attackers leverage social engineering tactics to trick users into providing that information. Proofpoint, to undermine these attackers, introduced our VAP (Very Attacked People) model years ago to help security teams assess risk based on the behaviors and actions of their people. Our VAP model focuses on vulnerability, attack and privilege, so it offers a people-centric risk view that helps organizations determine:
- How people work in high-risk ways (vulnerability): whether they’re likely to fall for attacks
- How people are attacked by threats (attack): what the probability is that they will be attacked
- How people access valuable data (privilege): what the impact is for the rest of the organization if a specific user is attacked
By measuring the intersection of probability, likelihood and impact, Proofpoint helps organizations gain a more complete view of their people risk.
Introducing Proofpoint Nexus People Risk Explorer
We recently introduced Nexus People Risk Explorer—a unique dashboard available to all customers who adopt a bundled Proofpoint solution—to provide visibility into people risk in organizations. Nexus People Risk Explorer helps security teams gain visibility and actionable intelligence into the risks each user poses to the broader organization by:
- Identifying user vulnerabilities and privileges to build a risk profile
- Segmenting them based on the similarity of their profiles
- Recommending specific security controls to mitigate risk, reduce costs and save time
Vulnerability and privilege insight
Nexus People Risk Explorer looks at holistic risk by analyzing the vulnerabilities of user groups and the privileges they have based on their roles and associated activity. This view allows us to assign each person a risk score from 1-10, accounting for variables such as uncompleted or failed phishing simulation, clicker vulnerability, email and credential leaks, and more.
The integrated product data helps us surface vulnerabilities by breaking them down into logical categories and ranking them from most to least risk. Security teams can easily see the number of affected users for each vulnerability category, and the privileges individuals hold based on their business function.
As long as an organization has the Proofpoint Targeted Attack Protection solution, security teams can use the valuable insights into their people as well as the generalized control recommendations discussed below.
User segmentation
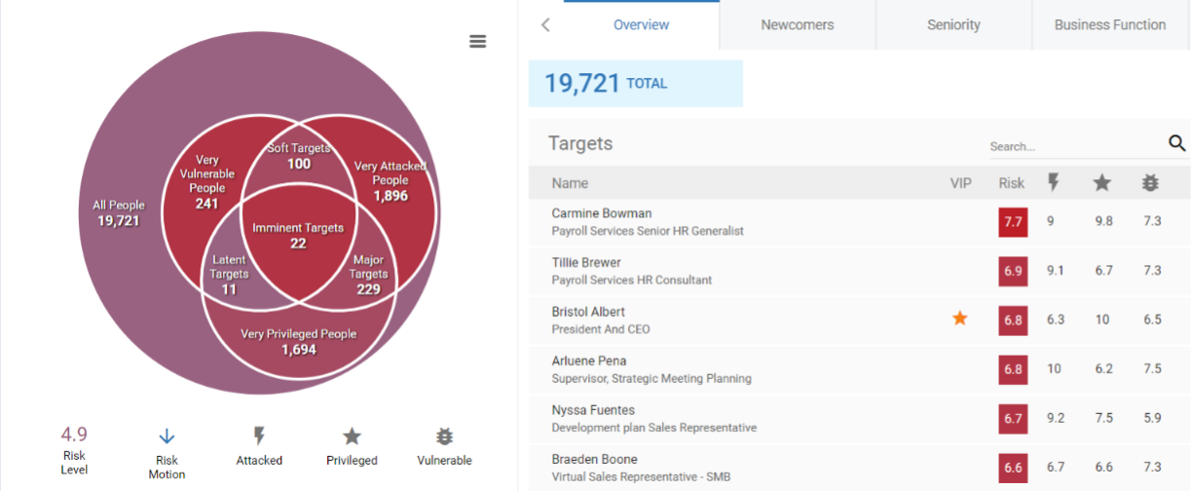
By ranking and grouping users based on similar risk profiles, security teams can prioritize their incident response actions according to which users represent the highest risk or impact. For example, focusing on imminent targets who are heavily attacked, likely to fall for attacks, and have access to sensitive data could significantly reduce risk.
Our integrated platform and synchronization with Active Directory allows for the segmentation of all users by business function, geography and department. These segmentations are dynamic. So, when security teams click “refresh,” they can be confident they’re looking at the most up-to-date memberships and user risk profiles.
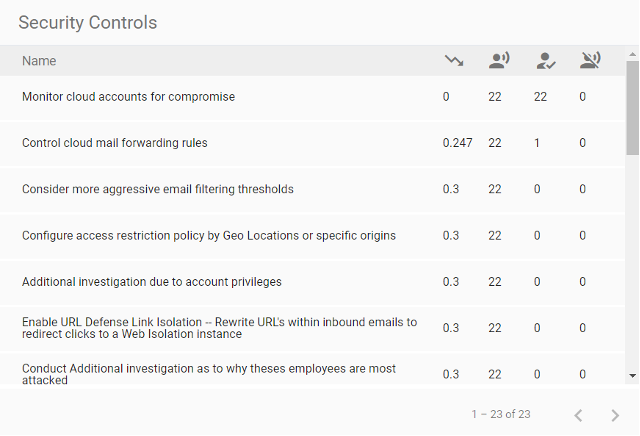
Security control recommendations and risk reduction scores
Security practitioners regularly request proactive security control recommendations from the tools they implement. Nexus People Risk Explorer suggests specific controls that security teams can apply within their existing tools to reduce risk in the desired user segmentation and manage the number of users to whom these controls are applied. If the organization has the integrated Proofpoint products related to these recommendations, security teams will receive additional, specific control instructions to protect their people.
Trending and risk calculation over time
Security teams are inundated with alerts they need to identify and sift through to surface the most critical items and prevent data breaches. Nexus People Risk Explorer provides trending insights that represent an organization’s people risk over time. This enables security practitioners as well as non-technical audiences to quickly comprehend the risk posture trends and potential impact on the business.
With data refreshed regularly, security teams can track their security controls and make changes in real-time based on what effectively mitigates risk. Proofpoint is the only vendor in the market that aggregates as much risk data and compiles it into an understandable visual for non-technical audiences and the board.
Summary
Cyber attackers are relentless in tricking users into clicking on malicious URLs, providing their credentials, or falling for phishing lures or other threat-scenarios. Nexus People Risk Explorer aggregates data insights from Proofpoint products to provide a people-centric view into risk within the organization. This increased visibility equips security teams with an effective way to prioritize incident response and risk mitigation projects, providing operational benefits.
By prioritizing resources and focusing the implementation of relevant adaptive controls based on the threat landscape, Nexus People Risk Explorer saves security teams time and money to protect what really matters: their people and the data they create and access.
For more information, download the Proofpoint Nexus People Risk Explorer data sheet here.











