Remote and hybrid work models, which require a large portion of business to be conducted outside the internal corporate network and in the cloud, have opened the floodgates to ransomware attacks. Phishing attacks and ransomware-infected webpages targeting remote and hybrid workers are rampant.
During the first half of 2021, the number of ransomware attacks doubled year-over-year, with an attempt on a U.S. business every 11 seconds, according to the Cybersecurity and Infrastructure Security Agency (CISA). The global cost of damages due to ransomware attacks, including forced downtime and lost productivity, is expected to exceed $20 billion this year.
Preventing, detecting and remediating ransomware attacks requires a comprehensive strategy and several technologies. This blog focuses on how many organizations have found that a modern, cloud-native secure web gateway (SWG) can play a critical role in curtailing ransomware attacks, especially when combined with isolation technology.
Even trusted domains can present ransomware risk
The best way to manage ransomware is preventing it from entering your environment, of course. So, the first line of defense against ransomware attacks is making sure users don’t go where ransomware lives and preventing users from engaging in potentially dangerous activities.
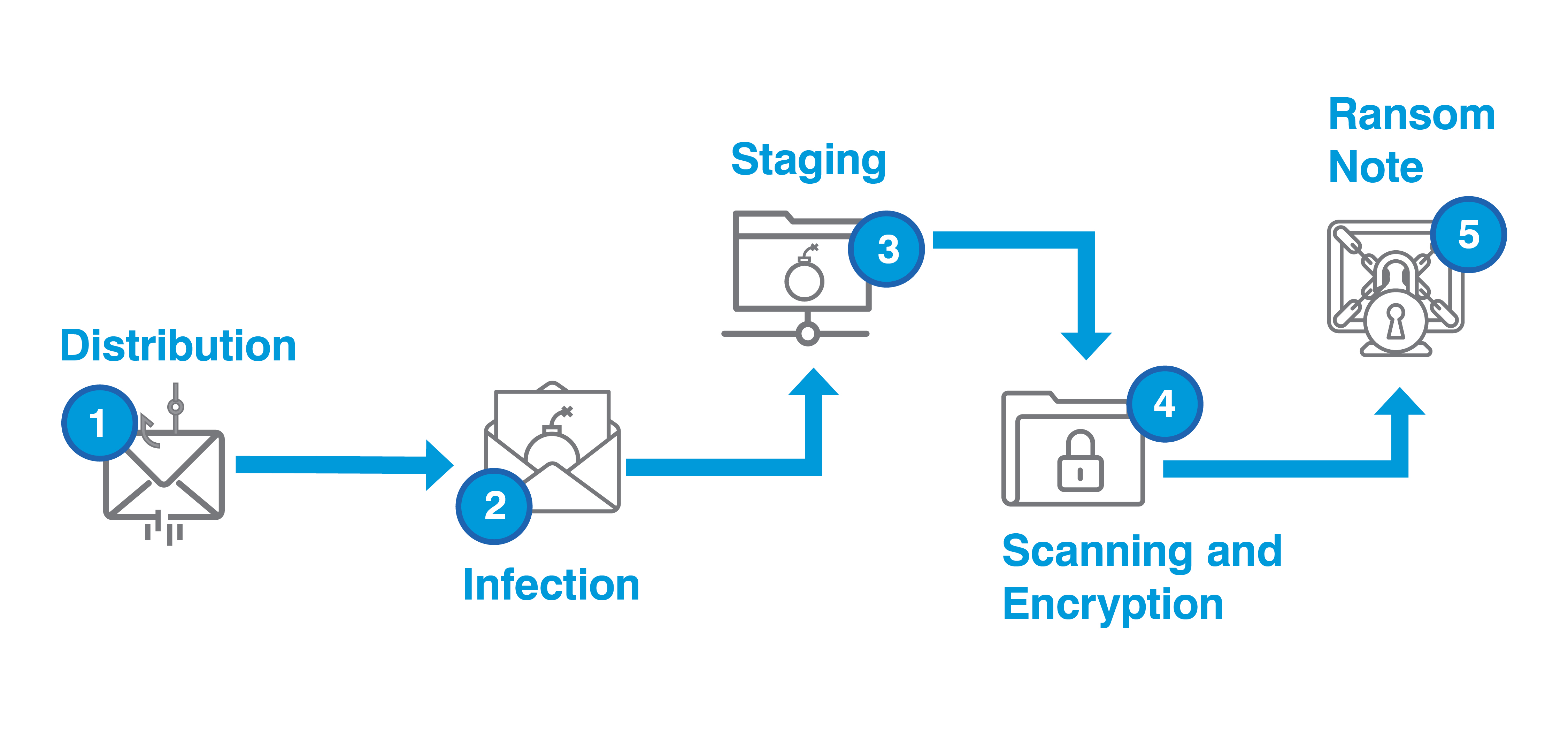
Ransomware attacks can start in several ways. Links to a compromised website may be included within phishing emails sent to a corporate or personal account, or through corporate or personal messaging apps. Also, ransomware can be delivered to an end user’s device through a malware-infected webpage. Today, some of the most trusted domains on the internet — like Microsoft Office 365 and Google Workspace properties — are also some of the most dangerous. Typically, a malicious actor will insert malware on a legitimate website so that the malware will automatically download onto a user’s device without their knowledge.
SWG and isolation technologies, working in tandem or in lieu of a secure email gateways (SEGs) can help to protect against these ransomware attacks. Operating between the user and the internet, an SWG inspects and filters malicious and risky web traffic to protect users from threats and data breaches when they browse the web. The policies it enforces also prevent dangerous and unauthorized user behavior.
A way to prevent ransomware operators from achieving their goals
Cloud-native SWGs, such as Proofpoint Web Security, are especially effective for managing the web activity of remote workers and preventing ransomware attacks. Web Security inspects all SSL traffic to expose threats and prevent users from accessing malicious sites. Like our email security and information protection solutions, Web Security is powered by the threat intelligence of the Nexus Threat Graph, which analyzes 26 billion URLs and 5 billion emails daily.
Web Security employs a people-centric approach that provides threat visibility across email, web and cloud. Using rich, cross-channel intelligence, Web Security will either block or isolate a browsing session based on the category, risk score and geolocation of a site. If a user tries to access a suspicious or unknown site, Web Security will automatically redirect the session to Browser Isolation, where content can be safely accessed off-network and off-device.
When a user arrives at an infected webpage of a site that’s generally thought to be safe, our Web Security solution will do one of two things:
- Block any file downloads based on file type and direct files to the in-line sandboxing function.
- Redirect the session to Browser Isolation, where file downloads are blocked automatically.
In either case, ransomware will never reach the end-user’s device or the corporate network, and the ransomware operator won’t realize their goal.
However, if ransomware compromises a device, it will signal the ransomware operator’s servers. It then awaits its next set of instructions. With control of the device, the ransomware operator can perform a range of actions, ranging from distributing ransomware throughout the network to exfiltrating data.
Proofpoint Web Security blocks these command-and-control connections to compromised sites, as well as any data exfiltration. In effect, it prevents the ransomware operator from being able to control the device and cause further damage.
Don’t miss our upcoming webinar
To learn more about how Proofpoint Web Security can help your organization defend against ransomware and why it’s the best alternative to traditional SWGs, register for our 30-minute webinar, “Protect Remote Workers from Ransomware,” which you can view live on Tuesday, November 30, at 1 p.m. ET/10 a.m. PT.











