Ransomware is one of the most active and profound threats facing organizations of any size today, and these attacks can be crippling to business operations. What often begins with a simple click on an inconspicuous email or link can result in a complete shutdown of business operations until ransoms are paid. And digital currency like Bitcoin makes it quick and easy for cyber criminals to collect ransoms.
Last year, the United States saw more than 65,000 ransomware attacks. The recent Colonial Pipeline attack triggered panic purchasing among U.S. citizens that emptied most gas stations across the Southeast. And a separate attack on meat processing company JBS USA Holdings, Inc., sparked fears about a domestic beef supply shortage. Following these attacks, the U.S. government proposed new efforts to combat ransomware. Ransomware was also a hot topic at the 2021 G7 Leaders’ Summit.
That said, many organizations are unprepared for a ransomware attack. Just 13% of IT experts surveyed by Ponemon Institute said their organizations can prevent ransomware. And more than 68% consider themselves “vulnerable” or “very vulnerable” to such an attack.
Key Trends Observed by Proofpoint Threat Research Analysts
These attacks are detrimental to local communities. They can put victims out of business, force hospitals to turn away patients, and prevent access to critical government services. These targeted attacks with their disruptive activities, high payouts and collaboration across cyber-criminal ecosystems have led to a perfect storm of cyber crime that has become a national security issue — and a risk that CISOs and boards of directors are taking seriously.
While each ransomware attack is unique, Proofpoint Threat Research analysts have observedcommon trends related to high-profile attacks from the past year:
Ransomware delivered as a multi-stage payload
What many once knew as a single-stage ransomware attack that encrypted individual machines for small ransoms has evolved to more elaborate multistage payloads.
Proofpoint Threat Research has observed that initial access brokers compromise victims with the initial payload, which is a malware downloader such as The Trick, Dridex or Buer Loader. The initial access brokers will then sell their access to ransomware operators.
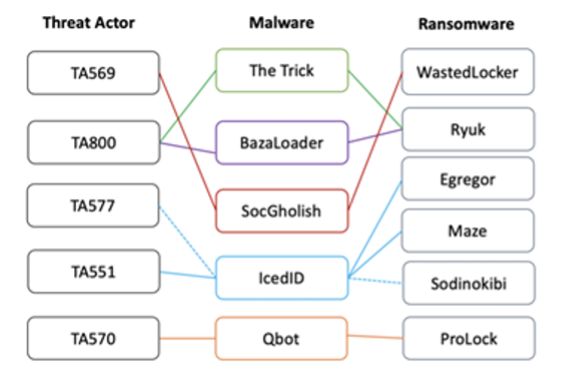
Figure 1. A sample of malicious actors, the initial access payloads they deliver, and the associated ransomware that resulted from the initial access
Human operated surveillance and delivery
There’s also been a shift from the automated “spray and pray” model, which was prevalent back in 2017 with ransomware like Locky, to a more hands-on, human operated ransomware approach.
Today’s ransomware operators will often conduct surveillance to identify high-value targets and determine which machines are most vulnerable and who is most likely to pay a ransom.
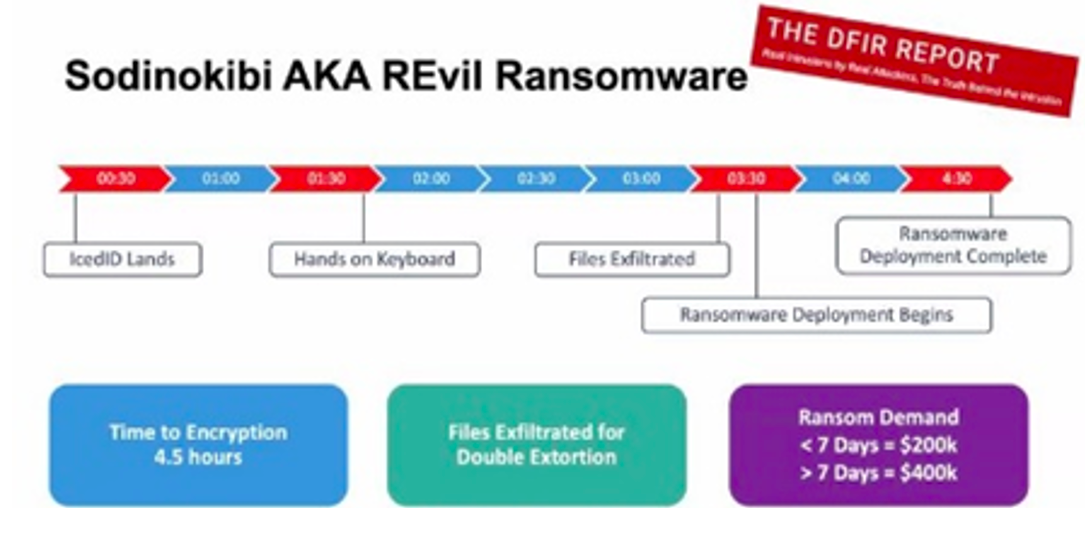
Figure 2. A timeline of infection example for the notorious REvil ransomware group’s methods, which have led to shorter dwell times and higher payouts
Less volume, more targeted lures towards larger industries
Ransomware attackers have also shifted to a “big game hunting” approach. They focus less on volume and more on targeting larger industries, specifically industries that have critical implications if business disruptions occur for prolonged periods.
According to the latest FBI IC3 report, recent ransomware attacks “have been more targeted and sophisticated” than past opportunistic attacks. Ransomware actors also exfiltrate data and threaten to release it for double extortion.
Vulnerabilities that provide common entry points
Email plays a critical role in the delivery of Ransomware, especially among larger organizations. Other attack vectors like Remote Desktop Protocol (RDP) and virtual private network (VPN) vulnerabilities and misconfigurations are also common entry points for ransomware attackers. Work-from-home protocols due to the COVID-19 pandemic have also likely contributed to a spike in ransomware attacks by allowing malicious actors to use attack vectors that didn’t exist before.
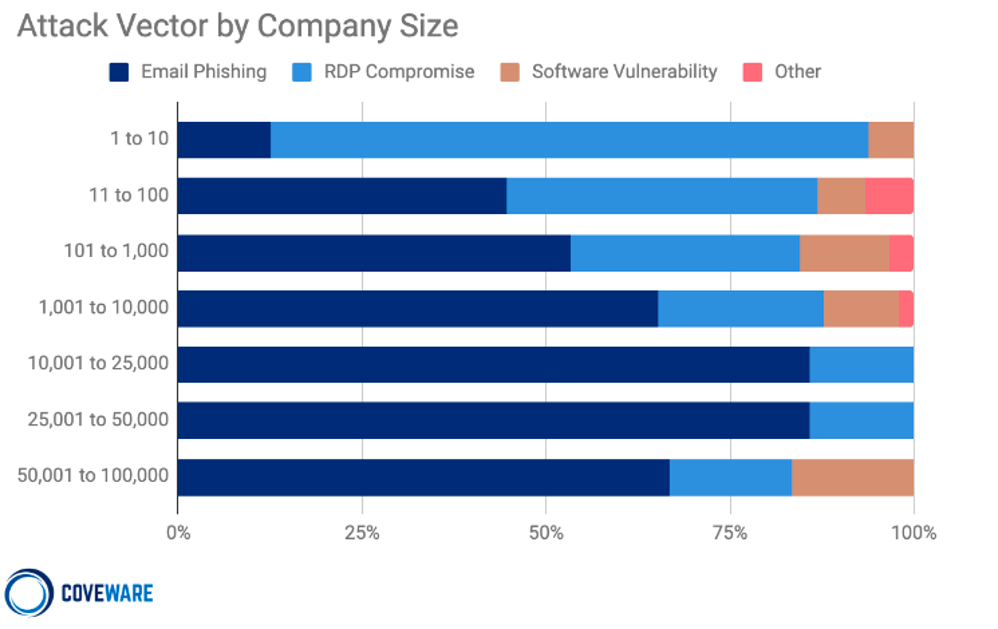
Figure 3. Attack vector by company size (Source: Coveware Q4 2020 Ransomware Report)
Key recommendations to prevent ransomware
Having the right strategy in place is essential to protecting your organization and minimizing the damage in the event you’re hit with a ransomware attack. Developing your strategy will require taking a holistic approach that includes technical controls, people and processes.
With a well-thought-out strategy in place, you’ll then be able to answer critical questions such as:
- What is our business process in the event we’re infected with ransomware?
- Do our users know what to look out for? Do we have the right detection tools?
- Should we pay a ransom?
- Do we have a post-mortem plan to prevent further disruption?
Technology and controls are critical for detecting ransomware attacks early
Because email is one of the key attack vectors, it’s important to invest in advanced email threat detection to identify threats early. Most ransomware attacks begin with first-stage malware or downloaders. Preventing ransomware via email is pretty straightforward: If you block the downloader, then you block the ransomware.
Email detection tools can stop downloaders early and give you visibility into ransomware-linked malware campaigns. Solutions like Proofpoint’s Targeted Attack Protection are excellent at tracking trends and giving you visibility into threats and the threat actors associated with these ransomware attacks. Email isolation is another layer of security that protects the click by providing safe access to content while preventing first-stage downloaders and credential theft. It can even provide adaptive controls inside Targeted Attack Protection to isolate the riskiest URL clicks for your Very Attack People. If a malicious or unwanted email does get through, then Proofpoint’s Threat Response Auto-Pull can automatically quarantine messages after delivery – even if that message had been forwarded.
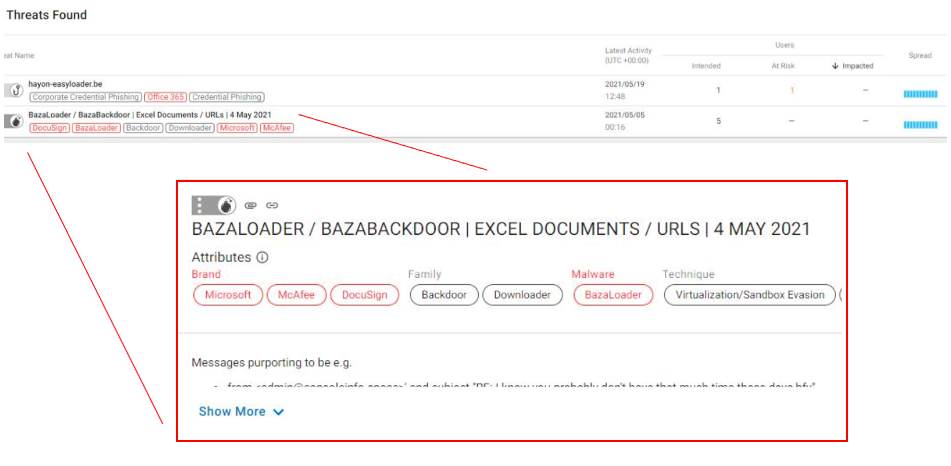
Figure 4. Proofpoint Targeted Attack Protection provides visibility into first-stage payloads and the malicious actors associated with those attacks
Closing RDP ports and patching VPNs are also vital measures to prevent easy entry points for ransomware operators to launch their attacks. Computers with RDP ports exposed online for remote systems access and VPNs that have not been patched for new bugs provide a huge target for threat actors to carry out brute-force attacks, in attempts to guess their respective credentials.
Security awareness is key as people are your last line of defense
Ransomware requires users to click or download to activate the threat, which is why user education and training is a must. Delaying these efforts is risky: According to the latest State of the Phish report from Proofpoint, only 33% of users actually understand what ransomware is. Solutions like Proofpoint’s Security Awareness Training help ensure your users know what to do when faced with a real threat by providing them with targeted education around malware, ransomware, safe browsing, and other areas.
Having a program like this that utilizes real-world attacks will better train your users to spot malicious messages. Give your users an easy way to report suspicious messages and reinforce that behavior with confirmation that they’ve done the right thing. After all, an alert user will not only be less likely to click, but they could also provide the organization with an early warning of a ransomware threat.
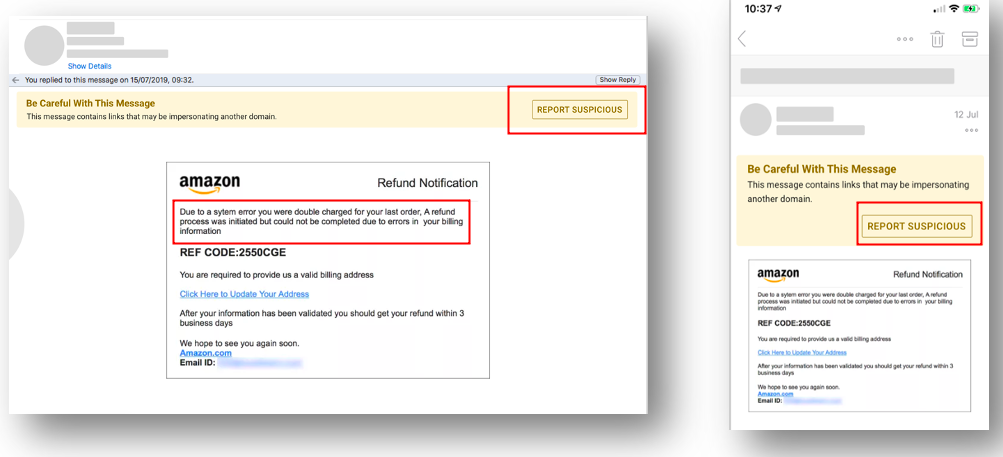
Figure 5. Email warning tags for email users
Ongoing communication with employees through newsletters, town halls, attack spotlights, videos or posters is also important for maintaining ransomware awareness.
Processes can lead to quicker response time and faster business decisions
Lastly, make a point to meet with your people leaders to create a ransomware preparation and response plan. Security controls take time to implement. But gathering with your leaders to formulate a viable plan and potential answers for tough business questions requires only a few hours.
Of course, one of the crucial questions you’ll need to consider is: Should we pay the ransom? That question is best answered before a ransomware attack happens, not during one. And should you decide that your organization wants to be ready to pay the ransom, then you’ll need to work out an oversight and legal process that includes key executives and operational staff.
For more of the latest Ransomware trends and what you need to know to better protect your company then check out our on-Demand Webinar with Ryan Kalember, EVP of Cybersecurity Strategy, and Sherrod DeGrippo, Sr. Director of Threat Research & Detection.











