The modern workplace has expanded beyond email. Attackers now exploit collaboration tools, supplier relationships and human trust to bypass defences and compromise accounts. This five-part blog series raises awareness around these shifting attack tactics. And it introduces our holistic approach to protecting users.
In our past instalments, we have covered one attacker’s tactics for exploiting new digital channels, why these channels are vulnerable, how business communications are compromised and why security awareness must evolve. Now in Part 5, we explore the importance of automatically detecting and responding to account compromises.
Organisations must understand that there are countless ways for attackers to gain access, including methods like multifactor authentication (MFA) bypass that don’t require phishing or direct engagement with a person. But the attack doesn’t stop at the initial compromise—it’s multistage. That’s why detecting malicious activity at any stage is critical to minimising impact and ensuring a complete, resilient defence.
The birth of identity providers
Many years ago, when I was a young security software product manager, I had the great fortune of working on a small team that invented, standardised and popularised the SAML standard. SAML, and its cousin technologies, serve as the technical basis for federated SSO, providing users with the ability to centrally login once and be redirected to all their authorised enterprise applications. One login to rule them all.
This enables both a great user experience and, when combined with MFA, strong identity confirmation. That was the dream. And the dream has become reality. Popular identity services—such as Microsoft Entra ID, Ping, Okta, Google Cloud Identity and others—grew out of this initiative, enabling users to centrally login once and be redirected to all their authorised enterprise applications.
Threat actors pivot to attacking identity providers
At the time, even back then, we thought that if we were truly successful in getting this centralised approach widely used, threat actors would take notice and would focus on cracking these high-value identity provider accounts. But that was a problem for another day.
Unfortunately, that day has arrived. The reality is that SSO works for both legitimate users and fraudulent ones. This part of our federated SSO/SAML dream has also come true.
MFA is good, but not good enough
Fast forward to the current day. As Proofpoint recently reported, in 2024, 99% of organisations monitored by Proofpoint were targeted for account compromise. And 62% of them experienced successful account compromises. Somewhat more unsettling is that 65% of the compromised accounts had MFA enabled.
Which accounts do the threat actors focus on compromising? The same ones that serve as gateways to a bevy of enterprise applications: Entra ID, Ping, Okta, Google Cloud Identity and the others. Why hack an organisation when you can just log in?
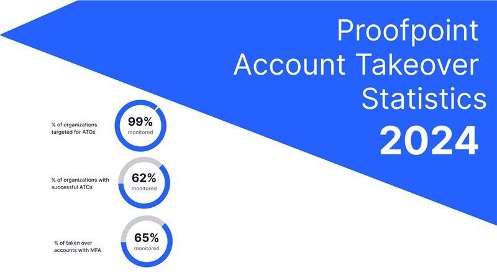
2024 Proofpoint account takeover statistics.
Our earliest federated SSO dream included MFA to strengthen user authentication. But unfortunately, MFA is a good, but not good enough, control. How do attackers crack MFA? They bypass MFA-based authentication using a number of techniques. This includes MFA fatigue, session hijacking and help desk social engineering. Or they land RAT malware or increasingly legitimate remote management software on endpoints. Clearly, MFA is not a silver bullet when it comes to defending against these attacks. If you need a tangible example as to how an MFA configured account can be so easily taken over, take a look at this demo video and this blog post on MFA bypass.
Fast response to ATOs is critical
What can you do to better protect your organisation against these human-focused, account takeover (ATOs) attacks? Keep in mind that time is of the essence. In fact, Crowdstrike’s 2025 Global Threat Report reveals that the average breakout time after an account compromise was just 48 minutes. So, if you want to limit the damage, you need to detect and respond to compromised accounts quickly.
The solution to this challenge is multichannel, multistage defence. In this case, Proofpoint Prime Threat Protection is the industry’s first and only comprehensive human-centric cybersecurity solution. It brings together previously disparate critical threat defence capabilities—protection against multistage attacks across digital channels, impersonation protection and risk-based employee guidance and education—in a single integrated solution. And it’s built to protect people wherever and however they work.
This blog focuses on Proofpoint Prime Threat Protection’s multistage attack protection capabilities—designed to identify and respond to account compromises at every phase, whether the attack begins with phishing, brute-force login attempts or suspicious post-access behaviour.
Multistage account takeover protection
Multistage attack protection is all about layering your defences. And Prime can detect malicious activities associated with account takeover at any stage of the attack.
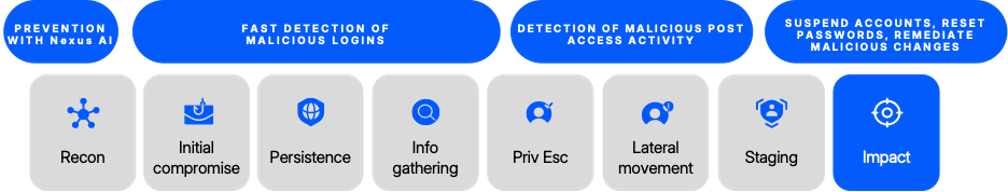
Multistage attack protection for ATOs provided by Proofpoint Prime Threat Protection.
First, using multichannel defence with Nexus AI, Prime defends against initial compromise. Next, it provides advanced security measures that are designed to quickly detect malicious logins and accurately confirm any account takeover. Further, it uses direct API-connected cloud account monitoring combined with machine learning, behavioural analytics and our proprietary threat intelligence to analyse account activities in real time, detecting attempts to escalate privileges or move laterally. Finally Prime can automatically suspend accounts, reset passwords or remediate malicious changes before threat actors can achieve their goal.
Protect your people with human-centric security
As digital workspaces expand, attackers continue to target people. While email remains the primary threat vector, cybercriminals are exploiting new channels like collaboration platforms, social media apps and file-sharing services. This has created the risk of a fragmented security landscape with disconnected point products, resulting in higher operational costs and increasing security gaps. This is where Proofpoint can help.
Proofpoint Prime Threat Protection provides a single, comprehensive solution to defend against all human-centric threats, both current and emerging. It combines a wide range of security protections to help you maximise threat prevention. It features:
- Accurate threat detection—Helps prevent the widest variety of threats
- AI-powered account protection—Defends against account takeovers and compromised supplier accounts
- Risk-based targeted training—Guides users to make safer choices when faced with threats
- Phishing protection across platforms—Blocks malicious links from multiple platforms
- Impersonation protection—Protects your brand reputation from being abused by attackers
- Human-risk management—Identifies high-risk users and automates adaptive security controls
With Proofpoint Prime, you can better protect your people and business by reducing alert fatigue with highly accurate threat detection, improved efficiency through detailed risk insights and automated security workflows. Combined with pre-built integrations and shared threat intelligence, your security and IT teams can accelerate deployments while reducing costs by eliminating fragmented point solutions across your organisation.
Learn more about Proofpoint Prime.
Read our Expanding Attack Surface series
Learn more about the evolving threat landscape and get insights into how to stop these attacks.











