This blog post is part of a monthly series exploring the ever-evolving tactics of today’s cybercriminals. Cybersecurity Stop of the Month focuses on the critical first steps in the attack chain – stopping the initial compromise—in the context of email threats.
The series is designed to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
The first three steps of the attack chain: stop the initial compromise.
In our previous posts, we have covered these attack types:
- Supplier compromise
- EvilProxy
- SocGholish
- E-signature phishing
- QR code phishing
- Telephone-oriented attack delivery (TOAD)
In this installment we examine a payroll diversion threat that Proofpoint detected during a recent threat assessment. We also cover the typical attack sequence of payroll fraud and explain how Proofpoint uses multiple signals to detect and prevent these threats for our customers.
Background
Business email compromise (BEC) continues to grow in popularity and sophistication. The 2022 FBI Internet Crime Report notes that BEC attacks cost U.S. businesses $2.7 billion last year. The global figure is no doubt much higher. Ransomware victims, in contrast, lost just $34 million.
Payroll diversion is a form of BEC. Typically, employees who have direct access to fulfilling payroll-related requests are prime targets. In these attacks, a bad actor pretends to be an employee who needs to update their direct deposit information. The new information is for an account that the bad actor owns. Once the fraudulent request is complete, the lost funds cannot be retrieved by the business.
Payroll diversion fraud isn’t a new form of BEC, but the frequency of this type of attack is on the rise. Proofpoint continues to see this type of threat getting through the defenses of other email security tools. Across all of our October 2023 threat assessments, we found that more than 400 of these threats got past 12 other email security tools.
There are a few reasons why it’s difficult for a lot of email security tools to detect or remediate these threats. The primary reason is because they don’t usually carry malicious payloads like attachments or URLs. They also tend to be sent from personal email services—like Google, Yahoo and iCloud—and target specific users.
Notably, API-based email security tools that scan for threats post-delivery are the most susceptible to not being able to detect or remediate this type of threat. This partly comes down to how they work. In order for them to be effective, they need security and IT teams to manually populate them with a dictionary of possible display names of all employees, which is a very time-consuming effort that is hard to scale.
To avoid this, many organizations simply choose to enable display name prevention for their senior executives only. But bad actors behind payroll diversion don’t just impersonate executives, they target anyone in the organization who can access corporate funds.
In our example below, an attacker took advantage of this exact weakness.
The scenario
Proofpoint detected a payroll diversion attempt where the attacker posed as a non-executive employee. The email was sent to the director of human resources (HR) at a 300-person company in the energy and utilities industry. The company’s incumbent email security tool delivered the message, and its API-based post-delivery remediation tool failed to detect and retract it.
The threat: How did the attack happen?
Here is a closer look at how this payroll diversion scam unfolded:
1. The deceptive message: The attacker sent a request to update their direct deposit information from an account that appeared to be a legitimate employee’s personal email account.
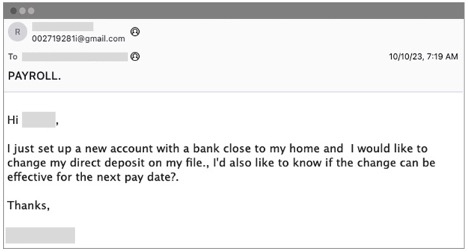
The original malicious message delivered to the recipient’s inbox.
2. Payroll diversion attack sequence: If the recipient had engaged, the attacker’s goal would have been to convince them to transfer funds into another bank account that was not owned by the impersonated employee.
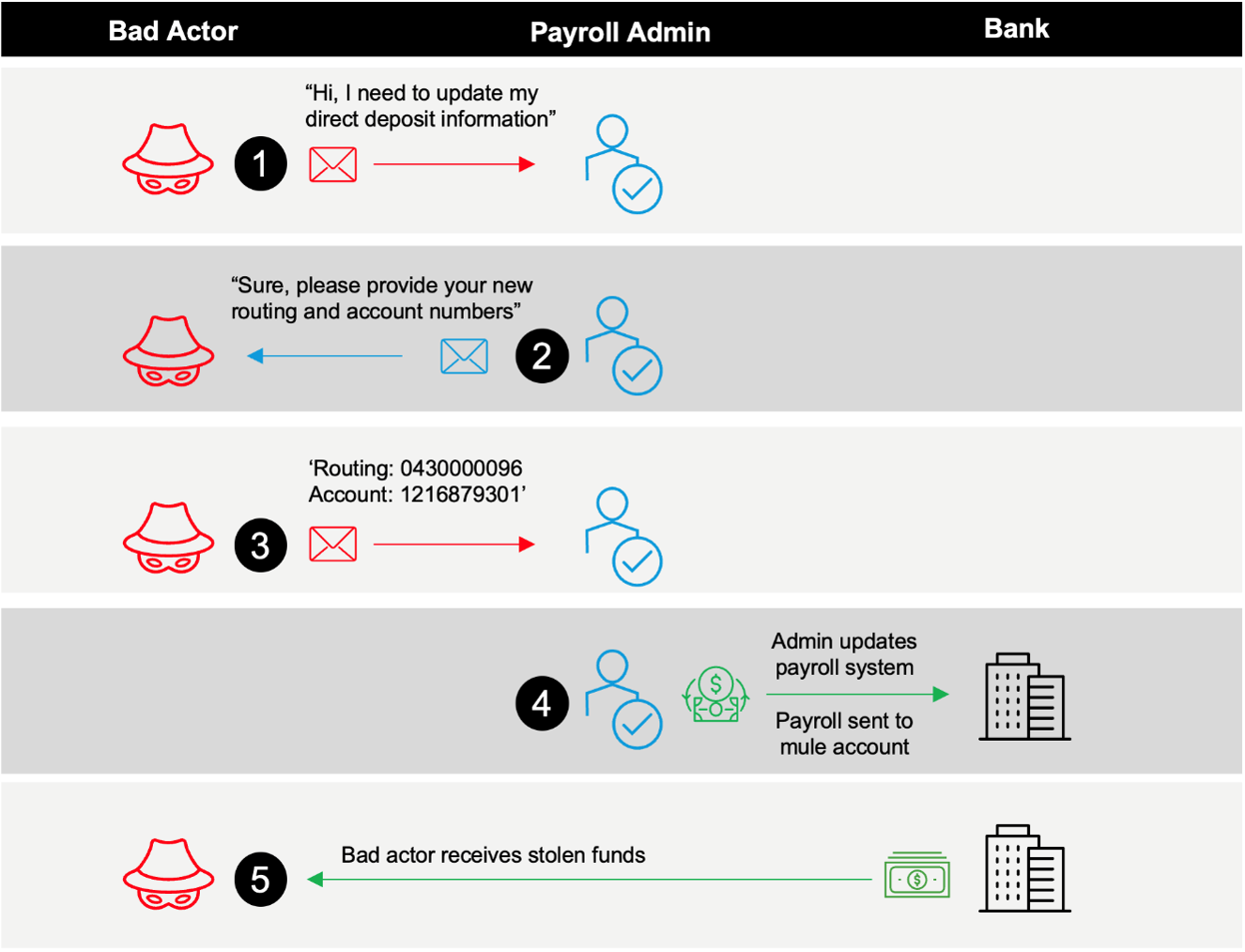
The typical attack sequence of a payroll diversion attack.
Detection: How did Proofpoint prevent this attack?
As noted earlier, payroll diversion threats can be hard to detect because they often don’t contain malicious payloads. A bad actor aims to convince the recipient that the email sender is contacting them from their personal email account. That is why these threats usually originate from consumer email services like Google, Yahoo and iCloud. Typical email authentication signals are ineffective at preventing these attacks. To decipher the true objective of an email, an email security tool must interpret a message’s contextual tone and intent.
Proofpoint uses multiple detection signals, analytic engines and behavioral artificial intelligence (AI) to help decipher whether an email is uncommon or malicious. One signal we use to detect emails that may be malicious is the commonality and frequency of communication from senders.
In the example above, it was rare for the director of HR at this energy company to receive emails from that employee from a personal email address. For most email security tools, stand-alone, uncommon or unusual sender signals create a high number of false positives. Unfortunately, API-only email security tools rely heavily on these signals when they analyze messages post-delivery. That’s why these tools generate excessive noise from unusual senders.
To reduce noise from detection, Proofpoint combines many signals to ensure we do not rely too much on one or two signals that create a high level of false positives. By combining the uncommon sender signal with an analysis of the language in the body of the message, Proofpoint extracts the tone and interprets the intent of an email.
We continuously train our AI and machine learning (ML) techniques with millions of daily email messages from our worldwide threat intelligence ecosystem to deliver higher-level fidelity detection and confidence when blocking these types of messages.
Based on the language in the email, Proofpoint determined that the message in the example above was a fraudulent financial request.
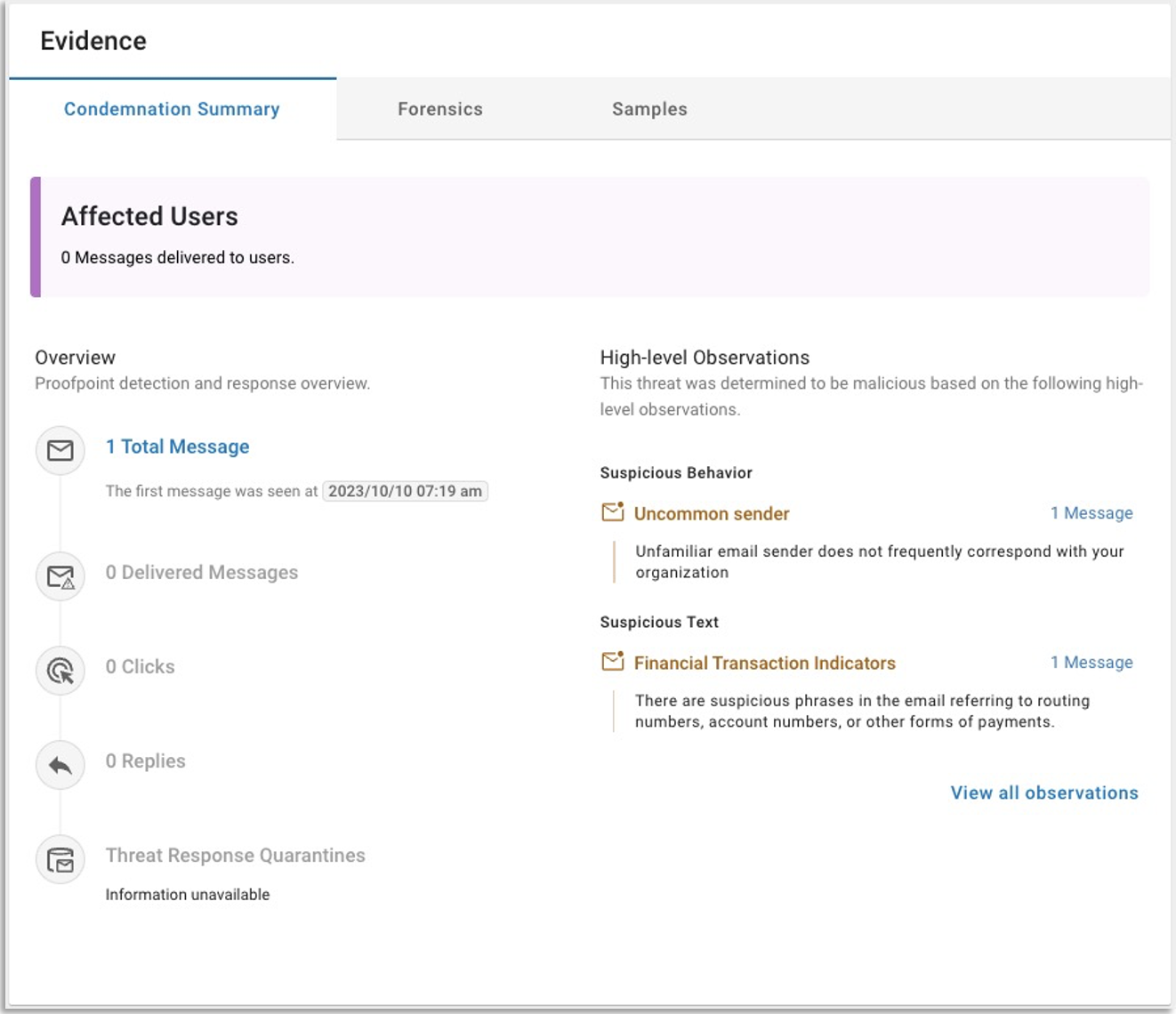
The Condemnation Summary outlines the signals detected by Proofpoint which led us to condemn this threat.
By combining the AI-driven detection stack with our pre-delivery filtering, Proofpoint can prevent threats before they are delivered to an employee’s inbox—even when the threat has not been seen before. While this particular payroll diversion campaign contained only one message, it was targeted at one customer—and no other Proofpoint customer had seen this message. Despite that, we were still able to detect it.
While API-only email security tools claim to offer AI, they typically cannot prevent these messages from being delivered or remediated. APIs can have gaps in availability, which can create gaps in visibility and detection. And the longer a malicious message sits in a user’s inbox, the more a business is left open to risk. A case in point: Threat research from Proofpoint shows that one in seven users clicks on a malicious email within one minute.
Unlike API-based solutions, Proofpoint constantly trains our AI on a large and diverse mix of emails, including clean and malicious messages. Data context and diversity is vital to create a resilient and effective AI solution. With our pre-delivery AI-native detection engines, Proofpoint continues to identify and block these threats proactively. This helps to break the attack chain for our customers.
Remediation: What are the lessons learned?
To prevent payroll diversions and other threats that use social engineering, businesses need to implement proactive measures like:
- Pre-delivery email detection. Blocking malicious messages before they are delivered is how to protect your users and keep your organization safe. Look for a solution that combines ML algorithms with advanced threat detection to identify and block threats. The Proofpoint Aegis threat protection platform stops threats before they’re delivered to users. While other API-only email tools claim to detect these types of threats, they only do so post-delivery. That means users are exposed to threats like payroll diversion and potential financial fraud caused by them.
- User education. Your employees, contractors and partners are your first line of defense. So make sure you have a security awareness program that teaches them about all types of BEC attacks. Help them learn how to stay alert for deceptive emails, suspicious tasks and unusual requests. This can greatly reduce their chances of becoming a victim.
Proofpoint helps break the attack chain
The incident described in this blog post is a strong reminder of the ever-present dangers for businesses and users in today’s cyberthreat landscape.
To learn how Proofpoint can help protect you against BEC threats like payroll diversions, download our e-book, The Definitive Email Cybersecurity Strategy Guide.











