Three years ago, Proofpoint published a brief that describes a three-phase methodology for building an effective security awareness and training (SA&T) programme. It’s called the ACE framework. And the best time to use it is when you’re building a robust, year-long curriculum that covers foundational cybersecurity topics.
In other words, the ACE Framework is helpful for creating a proactive security awareness programme in the sense that it’s designed to meet learners where they are. It helps to advance their understanding of this complex domain.
However, the threat landscaping is constantly evolving. Just in the past two years, we’ve seen a rise in QR code phishing and the abuse of chatbots and large language models (LLMs). We also know that our employees are knowingly taking risky actions. So, how do we cope with these more transient and near-term security challenges?
Our response is to evolve the ACE framework into what we refer to as the DICE framework. Here’s what these two frameworks look like, how they relate to each other and how to use them.
ACE framework basics
The ACE framework is a proactive approach to security training. Fundamentally, it has three phases:
- Assess. At the start, your learners get familiar with the subject by doing quizzes, using simulations and taking surveys.
- Change Behaviour. Interventions draw on learning principles from cognitive science. As such, they’re meant to both increase a learner’s understanding of security and motivate them to take the right action when it’s required.
- Evaluate. In the final phase, you determine how effective the educational interventions have been.
Once these steps have been completed, the loop then restarts and continues all over again because—let’s be honest—cybersecurity education is never complete.
DICE: Taking the ACE framework to the next level
As we looked to evolve the ACE framework, we split up its first phase, Assess, into two distinct processes: Detect and Intervene.
- Detect. This can mean detecting external threats or internal ones. When it’s detecting external threats, it typically refers to those that target an individual, like a business email compromise email message, which is identified by Proofpoint Targeted Attack Protection. When it’s detecting internal threats, it’s often about identifying the behaviour of an individual and deciding if it’s either consistent with company policy (like reporting a phish) or inconsistent (like using an unapproved USB device). In this latter case, a data-loss prevention (DLP) violation will be triggered.
- Intervene. Once a risky behaviour has been detected, it’s time to intervene. Ideally, an intervention happens at the time of the incident. For example, a teachable moment will display after a learner fails a phishing simulation. Sometimes they happen a few days later. So, if a learner fails a phishing simulation, they are automatically assigned an anti-phishing training.
The last two steps of the DICE framework largely follow the same pattern as the ACE framework.
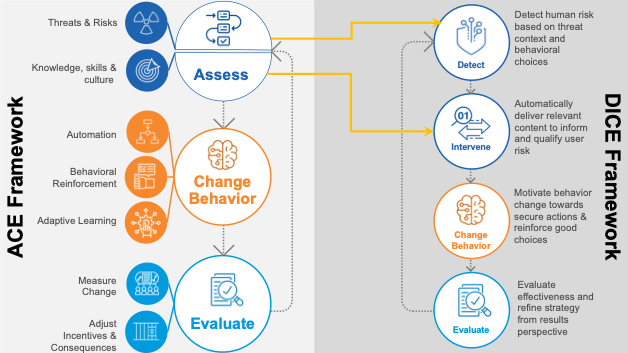
The evolution of ACE framework into the DICE framework. The Assess phase is split into the Detect and Intervene processes. The Change Behaviour and Evaluate phases remain largely analogous.
When to use DICE
The DICE framework is more reactive than ACE in the sense that it addresses security-related issues that are happening in the moment. Moreover, DICE nicely aligns with a human risk management (HRM) approach to cybersecurity because the educational experience is continuous and driven by what the learner needs to know.
What are the conditions under which the DICE framework is best applied? We recommend applying it when:
1. New threats are targeting your organisation. In this case, you need to quickly bring people in your organisation up to date with information pertaining to these types of attacks. You want to teach them:
- What to look for
- How to report it
- The consequences of falling for an attack
2. Unsecure behaviours are detected. This might be through Proofpoint services or third-party integrations. As a result, you want to re-educate and/or nudge learners on best practices.
Conclusion
We think the best way to approach security education is with two complementary approaches. A proactive approach (ACE) provides foundational knowledge, while a reactive approach (DICE) supplements core knowledge with ongoing information that’s immediately applicable. This way, a learner has the knowledge they need to securely complete their job-related tasks.
Learn more about offensive and defensive security training.











