Protecting sensitive data is a challenge. The constant barrage of headlines about data breaches and insider threats is evidence enough of that. And it’s easy to understand why the risk of data loss is high. Employees have access to more intellectual property from more channels, devices and tools than ever before. On top of that, the amount of new data that is created, captured, replicated and consumed is expected to double between 2022 and 2026.
It is not surprising then, given these dynamics, that information protection is a top priority for many CISOs globally.
The importance of integrating with existing investments
Protecting your organization’s most sensitive data, at rest or in motion, requires an effective information protection solution. That solution should provide visibility, contextualized insights and streamlined workflows that can help your security team quickly determine the best response.
Equally important is determining how that solution integrates with your existing investments. Data protection is just one part of your overall cybersecurity strategy. To create a strong security posture, you need to understand how data protection fits in with other solutions, including:
- Identity and access
- Endpoint detection and response (EDR)
- Security information and event management (SIEM) and security orchestration, automation and response (SOAR)
- Network security
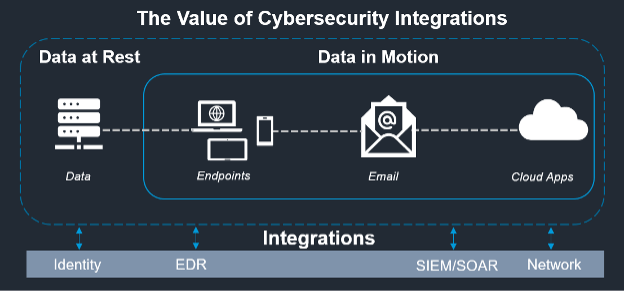
An overview of the value of cybersecurity integrations. Data security needs to integrate with existing investments.
The value of integrations: 1+1 = 3
Take a bird’s-eye view of cybersecurity, and it’s easy to see that the industry is highly fragmented. Hundreds of companies offer solutions for very niche problems. This helps drive innovation and a healthy pipeline of emerging solutions. But the downside is that it can quickly lead to tool sprawl.
In the Cyber Resilient Organization Study by Ponemon Institute, a third of respondents reported that they have more than 50 security tools and technologies deployed. Another third said that they use 30 to 50 tools. And a Proofpoint webinar poll about optimizing the data security stack with integrations found that an overwhelming majority of attendees (74%) said tool sprawl is a challenge for their organization.
It’s tempting to chase shiny new tools. But when you end up with too many disjointed and siloed tools, it can increase challenges and complexity for your security team. You also need to have dedicated skills and resources on hand to manage and maintain each tool. This can lead to:
- A lack of visibility. Security analysts must switch from tool to tool to get a complete picture. This consumes valuable time. Worse, it doesn’t even provide a clear view into all the telemetry needed to triage an incident.
- Inefficient and error-prone processes. When an analyst must piece together data from multiple tools manually, the process can be extremely inefficient. There’s also lots of room for error.
- Analyst burnout. Under these conditions, security analysts tend to burn out easily. That, in turn, leads to attrition, which further compounds the issue of having too few available resources.
Integrations alleviate these challenges by providing seamless connections between products. When complementary solutions can work together, they create more value than they do on their own.
To protect your sensitive data effectively, security teams need solutions that work together effortlessly as part of a broader ecosystem. That will allow them to detect and respond to cybersecurity threats faster. In essence, the value of integrations is 1+1=3.
In the next blog in this series, we’ll explain how Proofpoint Information Protection can extend your data security through integrations with leading security vendors.
Learn more
To learn more about how you can optimize your data security stack with integrations, check out this webinar.
Find out more about Proofpoint’s technology and alliance partnerships here.











