Complementary solutions that work together can create more value than they do on their own. In other words, the value of product integrations is as simple as 1+1=3, as we discussed in the first post in this series.
Integrations provide visibility into security telemetry that helps analysts triage incidents more effectively. They also enable automated workflows, which save time and increase efficiency. Ultimately, integrations can help lower the risk of analyst burnout. That is a key benefit for any security team today that’s challenged in training and retaining talent.
Your business can also use integrations to help keep your data safe. In this post, we look at how to extend data security with Proofpoint integrations for information protection.
Extend data security with Proofpoint integrations
With the right information protection platform, you can prevent data loss, investigate insiders and block cloud threats for data in motion and at rest. The platform you use also needs to protect data whether users are accessing it via the endpoint, email or a cloud application. It must also integrate with your existing ecosystem.
The Proofpoint Sigma Information Protection platform can do all the above. It’s based on an open API approach, and it integrates with:
- Identity and access management (IAM) solutions
- Endpoint detection and response (EDR) solutions
- Security information and event management (SIEM) and security orchestration, automation and response (SOAR) solutions
- Network security solutions
Proofpoint integration partners for information protection include leading vendors such as Okta and SailPoint for IAM; CrowdStrike for EDR; Splunk and ServiceNow for SIEM/SOAR and service management; and Palo Alto Networks and Zscaler for network security.
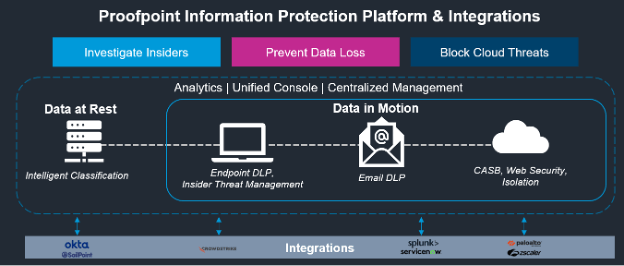
An overview of the Proofpoint Information Protection Platform and integrations.
Addressing specific use cases
Proofpoint integrations for information protection can help your security teams address an array of use cases. Incident management workflow, correlation of security data, Internet Content Adaptation Protocol (ICAP) integration for data loss prevention (DLP), and intelligence sharing are just some examples. Here’s a closer look:
Incident management workflow
The Proofpoint integration with ServiceNow can help security analysts simplify their workflows and manage alert triage consistently.
Once the Proofpoint platform generates alerts, it sends the alerts directly to the DLP incident response app—ServiceNow DLP IR. Alerts from ServiceNow can be sent to the Proofpoint platform as well, so that analysts have a consistent view of their status.
The Proofpoint integration with ServiceNow can be achieved with any service management solution that can receive webhooks and call into a RESTful API.
Correlation of security data
The Proofpoint and Splunk integration provides a comprehensive view of user activity. It sends DLP and Insider Threat Management (ITM) alerts to Splunk. That, in turn, helps security analysts correlate data during their investigations.
Alerts can be sent through webhooks into Splunk. Or they can be copied into a third-party repository. An AWS S3 bucket or Azure Blob storage are examples of repositories.
ICAP integration for DLP
The Proofpoint integration with Zscaler uses ICAP to send files to Proofpoint for DLP inspection. (ICAP is a standard protocol.)
Proofpoint DLP augments Zscaler’s web proxy by applying best-of-breed DLP inspection to the web channel and presenting it within the same console where DLP events from endpoint, cloud and email channels are generated.
Intelligence sharing
The Proofpoint and CrowdStrike partnership automates orchestration and response in multiple Proofpoint and CrowdStrike solutions. The partnership enables threat intelligence (file, device and user risk) sharing across platforms.
The Proofpoint Information Protection integration with CrowdStrike uses CrowdStrike’s intelligence on file risk. For example, if a user uploads a file into a repository that CrowdStrike knows is malware, Proofpoint will quarantine the file. The result is that Proofpoint can use best-of-breed file risk threat intelligence for enhanced protection.
Best practices for approaching integrations
When you are developing an integration strategy for your organisation, be sure to consider the following best practices:
Align with your information protection blueprint. A blueprint provides structure to your approach. It also helps you achieve your goals. Take an inventory of current investments when designing your blueprint. These investments include the IAM, EDR, SIEM/SOAR, and network security solutions you currently have in place. And when you’re evaluating vendors, be sure to look for areas where you can gain efficiencies and augment your security workflows.
Identify strategic solutions. When investing in new solutions, choose integrations that will help to strengthen your platform. The integrations should also enable use cases and align to the 1+1=3 approach.
Ensure a fit with the broader ecosystem. The new solutions you choose should be “good citizens” within your broader security ecosystem. So, make sure to choose vendors that take an open API approach and support standardised mechanisms like webhooks and ICAP.
Learn more
Interested in learning more about how to optimise your data security stack with integrations?
Watch this on-demand webinar from Proofpoint.
To find out more about Proofpoint technology and our alliance partnerships, see this page.











