

Proofpoint DLP vs. Microsoft Purview
Are you struggling to make Purview work? Streamline your program with Proofpoint.
Overcome Data Security Complexity with Proofpoint’s Modern Solution
Customers choose Proofpoint over Microsoft Purview because its human-centric approach delivers superior multi-channel data protection and immediate time-to-value. So whether you’re just starting your data security journey and evaluating solutions or your Microsoft deployment has stalled, our comprehensive platform deploys quickly and accelerates incident resolution, saving you time and resources.
Why switch to Proofpoint?
Our SaaS-native, modern data security architecture scales automatically and assures fast time-to-value, even if you’ve been mired in a lengthy and unproductive Microsoft Purview deployment.
Maximize the success of your data security program with Proofpoint professional and managed services that will provide design, operational and optimization support.
Take advantage of our economically attractive packages and get your data security program up and running immediately. Contact one of our experts to learn more.
AI-powered Data Classification
Microsoft's limited support and surcharges for non-Microsoft data sources and high rates of false positives and negatives from pattern-based classification result in incomplete data visibility, compliance gaps, and increased security costs and risks. As a result, organizations cannot achieve a unified and accurate understanding of their sensitive data landscape for effective policy enforcement.
Proofpoint provides superior classification across a wide range of data sources, including non-Microsoft data stores. Our autonomous custom classifiers are capable of continuously learning an organization's unique data patterns and dynamically refining data classes unique to your organization with minimal human input. Proofpoint also delivers high-fidelity classification that eliminates up to 99% of false positives on PII data, significantly reducing the manual tuning and operational overhead that often burdens administrators.
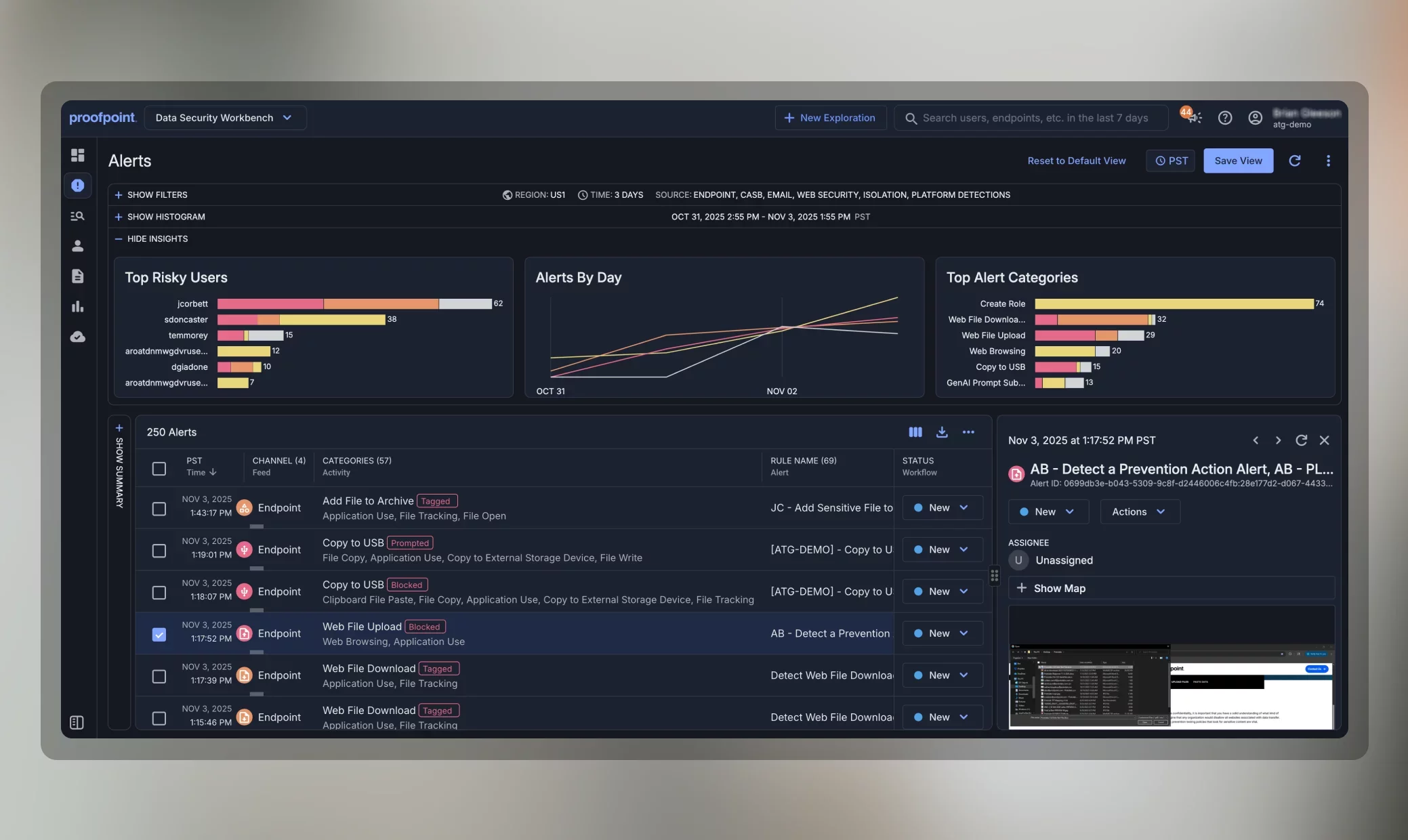
Visibility to Data Loss and Insider Threats
Microsoft’s mostly data-centric alerts are spread across multiple, fragmented consoles. With inflexible reporting tools, the context of data security alerts cannot be determined. This approach makes investigating alerts burdensome, time-consuming and leads to missed violations that increase risk.
Proofpoint is the only solution that brings together the telemetry of content and user behavior across the most critical data security channels—email, cloud applications, endpoint, and web. Our unified console provides all administrators and analysts need to quickly resolve incidents and prevent data loss: policy management, workflows, alert management, classification sophistication, reporting.
Operational efficiency
Microsoft requires manual processes to define policy exceptions to circumvent product limitations and numerous prerequisites prior to installation. This makes system management inefficient, costly and error prone. In addition, changes to policies are frequently pushed after long delays.
Proofpoint delivers straightforward policy management provides clear visibility into all data and events, supports granular privacy and role-based access controls and streamlines day-to-day management with policies installed in near real-time.
Implementation
Microsoft is time-consuming and difficult to implement, leading to increased costs. Deploying Purview requires installing multiple agents and plugins on the endpoint, yet it can only support limited file types. Since Microsoft doesn’t have native professional or managed services for data security, organizations must either implement the solution themselves or hire a third party, further adding to costs.
Proofpoint is quickly implemented, employs a single, user mode agent for data security and Insider Threat Management, and supports many file types across all channels. Its endpoint protection is agnostic for greater flexibility. Our approach assures fast time to value and can accelerate deployment with its native professional and managed services offerings.
Proofpoint vs. Microsoft Purview at a glance:
| Features/Tools/Products | Microsoft M365 E3 | Microsoft M365 E5 | Proofpoint |
|---|---|---|---|
| Deep user & file context |
No
|
Partial |
Yes
|
| Screen capture for forensic evidence |
No
|
Partial |
Yes
|
| Threat hunting for pro-active detection/investigation |
No
|
Partial |
Yes
|
| Adaptive DLP controls based on user behavior |
No
|
Partial |
Yes
|
| Single, user-mode agent for DLP and ITM |
No
|
Partial |
Yes
|
| DSPM for data at rest discovery, classification, risk prioritization and labeling |
No
|
Partial |
Yes
|
| Rich DLP detections (Regex, OCR, IDM, EDM) & MIP classification |
No
|
Yes
|
Yes
|
| Monitor & detect file movements with data lineage |
No
|
No
|
Yes
|
| Integration with 3rd party proxy & redirect to Isolation |
No
|
No
|
Partial |
| Account Threat Protection & 3rd party apps (PFPT Threat Intel) |
No
|
Partial |
Yes
|
| Dynamic shadow IT (PFPT & Ecosystem) |
No
|
Yes
|
Yes
|
| API, forward & reverse proxy modalities |
No
|
Yes
|
Yes
|
| Broad application connectors |
No
|
Yes
|
Yes
|
| Pre-built data identifiers and dictionaries |
Yes
|
Yes
|
Yes
|
| More than 300 file types scanned out of the box |
No
|
No
|
Yes
|
| Fingerprinting of sensitive documents |
No
|
No
|
Yes
|
| Misdirected email solution |
No
|
No
|
Yes
|
| Content matching: IDM, EDM and OCR |
No
|
Partial |
Yes
|
| Unified alert management & DLP Configuration |
No
|
No
|
Yes
|
| Granular Data Privacy & Access Controls |
No
|
Yes
|
Yes
|
| Security ecosystem integration (SIEM/SOAR/Teams) | Partial | Partial |
Yes
|
| Managed Data Security |
No
|
No
|
Yes
|
| Professional services for Data Security |
No
|
No
|
Yes
|

Customers Recognize Proofpoint’s Market Leadership
Proofpoint was recognized as a 2025 Gartner® Peer Insights™ Customers’ Choice for Data Loss Prevention.
Realize Business Value with Proofpoint Data Security
Data security is not just a set of tools. It is a program. A successful data security program is like a three-legged stool that encompasses people, processes and technology. Only Proofpoint provides all three legs so you can reliably defend your organization’s data and realize true business value.
Return on Investment
Microsoft provides an incomplete set of disparate data security tools that are minimally integrated, expensive to deploy and require a team of costly, highly-trained technologists to operate. It comes with only one leg of the stool needed for a successful data security program – technology.
Proofpoint provides you with people, processes and technology needed for a successful data security program. Proofpoint ZenGuide helps change the behavior of your people by providing best-in-class cybersecurity user training. Proofpoint Applied Services provides you with highly skilled experts to co-manage the processes of your data security program. And Proofpoint’s adaptive, human-centric technology transforms data security across email, cloud, endpoint and web. Proofpoint’s superior time-to-value, visibility into data security events, and usability guarantees that you will realize ROI immediately and throughout your program’s life.
We’re recognized as an industry leader by leading analyst firms and customers alike.

Continuously Strengthen Your Data Security Posture with Proofpoint DSPM
Read More
2025 Data Security Landscape

Transforming Data Security
Request a demo
Learn how our integrated platform helps you:
-
Stop cyberattacks
-
Prevent data loss
-
Reduce human risk across your environment










