Ask Yourself: Are You Giving Attackers Too Much Visibility into Your Organization?
Social and digital media have made it much easier to find information about people and open lines of communications. But this is a double-edged sword: It’s great for customers and trustworthy people who want to reach out to your company and find answers, but a nuisance — even a danger — when it comes to unsolicited and malicious emails, text messages, phone calls, and social connections.
It can be difficult to determine the right line to walk when it comes to sharing details about your organization and staff via public-facing channels like websites, social profiles, and even annual reports. In the end, this decision is one that organizations must evaluate individually, based on their communication goals, brand vision, and regulatory requirements.
Still, there are some basic thoughts and best practices to consider with details like this:
Know What’s Out There – and Tell People about It
Since infosec teams are on the hook to protect organizations from attack, they should become familiar with the information that’s being offered on public channels, including the following:
- Email aliases
- Names, roles, and personal information about staff members
- Insights into travel and event schedules for particular individuals
- Staff members who have high-visibility social channels and post company business
Cybercriminals will use these pieces of information to launch phishing and other social engineering attacks, so they should be on your radar as well. All inbound email channels (even aliases) should be monitored, and individuals who receive and respond to messages received via aliases should be trained to treat these communications with extra care. In addition, any individuals whose information is being placed on a public channel should be alerted to that fact and cautioned that cybercriminals could use those details to craft attacks (phishing, vishing, or otherwise) that feel more personal.
Become a Privacy Advocate
When possible, work with marketing, human resources, legal, executives, and other teams to determine the right level of detail for public channels. Many times, there’s a desire (from a brand perspective) to add a personal touch to customer-facing assets. But how much is too much?
As noted prior, this can be a difficult question to answer … but it should be thoughtfully answered. We suggest trying to strike the right balance between what needs to be available (from a business perspective) and details that are strictly designed to promote a feeling of personal connection. Here’s a good question to ask those who want to push the envelope: Is it necessary that any visitor to a website be given the ability to directly contact specific individuals within the company, without any sort of qualification? Frankly, in many cases, that answer is no.
For instances in which it’s determined that a specific person’s contact information (email, phone number, or otherwise) should be made public, try to offer some level of insulation, particularly if it’s a person with privileged access. For example, instead of publishing a corporate email address, use an alias that doesn’t match internal email conventions — JosephSmith@company.com rather than jsmith@company.com, for example — and provide some education about what to look for. This approach can help recipients to better qualify incoming messages, and because they break “normal” email address constructions, spoofing may be more likely to raise a red flag.
Educate Users about Cybercriminals’ Methods
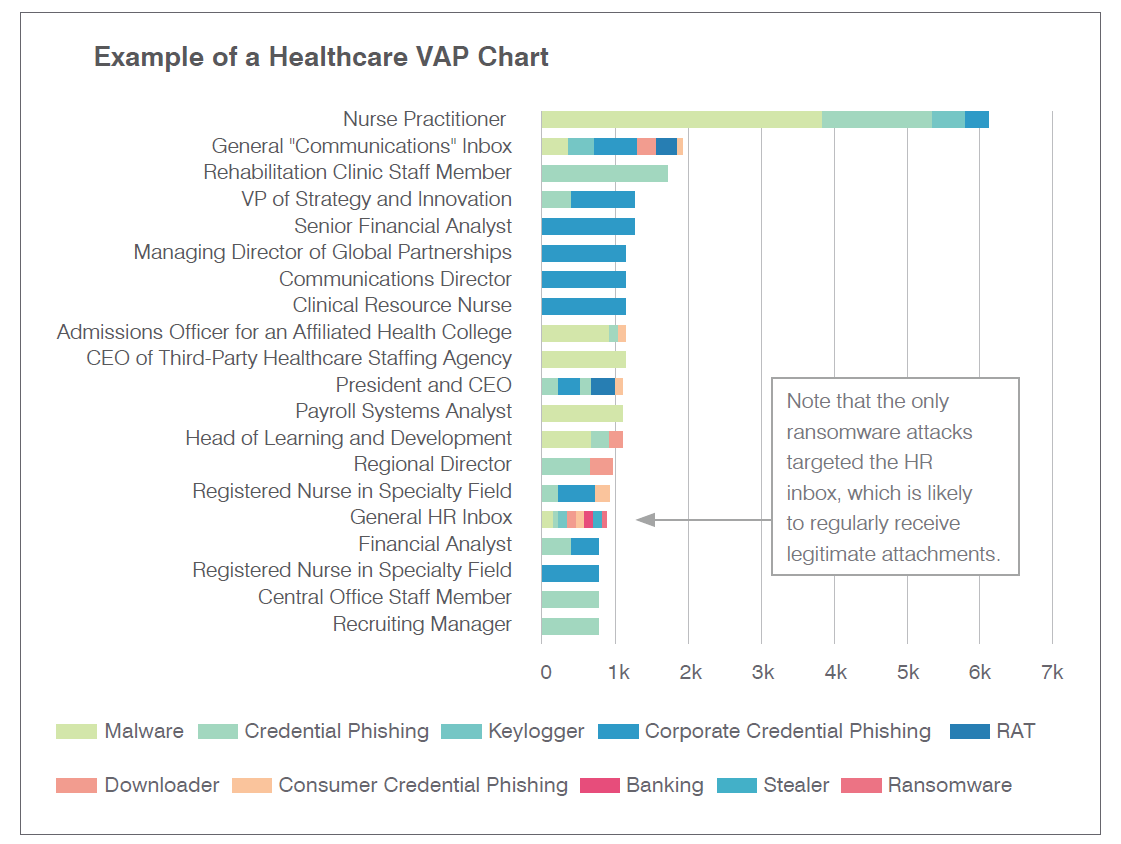
Our State of the Phish Report clearly illustrates that targeted individuals vary from industry to industry and organization to organization. (Download your copy to compare the above VAP chart to one from a manufacturing organization.) Virtually anyone could be (or become) a VAP. As such, you should raise awareness of cybercriminals’ use of channels like LinkedIn, Google, Facebook, and other public sources of personal information; provide education about best practices for sharing data; and train employees to identify and avoid attacks that exploit these identifying details.
But don’t stop there; take a truly people-centric approach to cybersecurity. How? Identify the VAPs within your organization, examine your anti-phishing training data to reveal the most vulnerable users, and use those metrics to quiet the perfect storm that’s brewing: the overlap between these two populations. The opportunity to deliver the right phishing training to the right people at the right time should not be squandered.
Learn more about phishing impacts and opportunities in our State of the Phish Report webinar.











 It no secret that cybercriminals are doing all they can to find direct lines to end users and using social engineering techniques to fool them into making bad decisions. It’s a topic we cover at length in our recently released
It no secret that cybercriminals are doing all they can to find direct lines to end users and using social engineering techniques to fool them into making bad decisions. It’s a topic we cover at length in our recently released