Executive Summary
Every day, Proofpoint analyzes more than 5 billion email messages, hundreds of millions of social media posts, and more than 250 million malware samples as part of the company’s ongoing effort to protect organizations around the world from advanced and persistent threats.
Proofpoint’s researchers continue to observe and monitor sophisticated threats across email, social media, and the web, which provides a unique vantage point from which to reveal and analyze the Tactics, Techniques, and Procedures (TTPs) of today’s cyberattacks.
This report highlights the threats, trends, and key takeaways from Proofpoint’s research organization based on quarterly observations within its large customer base and the broader threat landscape. It provides actionable intelligence organizations can use to combat today’s attacks, anticipate emerging threats, and manage security awareness. Along with research and findings, the report recommends steps organizations can take to protect their people, data, and brands.
Key Takeaways: Emotet returns while RATs and bankers fill in the gaps
Below are the key takeaways from the third quarter of 2019.
- Malicious URL messages made up 88% of global combined malicious URL and attachment message volume, a slight increase from Q2, but overall in-line with the trend for 2019.
- Global combined malicious URL and attachment message volume decreased by nearly 40% compared to Q2, largely as a result of Emotet’s absence for the first 10 weeks of the quarter.
- Despite this decrease, overall volumes of banking Trojans and RATs increased by 18% and 55%, respectively vs. Q2 volumes
- Ransomware remained virtually absent as a primary payload in malicious emails, with the exception of smaller campaigns generally distributing Troldesh and Sodinokibi.
- Emotet returned mid-September, with sufficient volume to make it almost 12% of all malicious mail in Q3.
- Threat actors leveraged the Keitaro Traffic Distribution System (TDS) in both malvertising and URL-based email attacks, building on the trend of more complex attack chains and redirections to hide their activities and exploit multiple vectors, including exploit kits.
- Sextortion remained widespread in Q3, with the appearance of malware that could potentially provide actual evidence of adult activity for threat actors instead of strictly relying on social engineering and related scams.
- Over 26% of fraudulent domains used SSL certificates, over three times the rate of domains across the web.
Overview
Key stat: 15% of malicious payloads were remote access Trojans and 45% were banking Trojans, up from 6% and 23% in Q2 2019, respectively.
The most notable change in the malware landscape in the second quarter of 2019 was the disappearance of the Emotet botnet at the end of May. Likewise, the most notable change in Q3 was the return of Emotet in September with regular, high-volume campaigns that, with only the last two weeks of September in action, accounted for over 11% of all malicious payloads for the entire quarter. Emotet’s absence for most of the quarter, however, was largely responsible for a 39% drop in overall message volume from Q2 2019.
At the same time, though, we observed higher levels of web-based threats, generally originating with malvertising and often leveraging the Keitaro traffic distribution system (TDS). Victims were redirected to instances of the RIG or Fallout exploit kits (EKs), which in turn dropped a loader and secondary payloads including banking Trojans, RATs, and more.
The relative volumes of messages with malicious attachments vs. URLs remained largely unchanged from Q2 to Q3, with the trend towards URL-based malware distribution continuing. Overall, URL volumes rose to almost 88% of total malicious messages (an increase of two percentage points vs. Q2), demonstrating an apparent continued response to our increasing exposure to cloud-based sharing and documentation in business environments. Infection chains associated with these URLs are also increasingly complex, with URL-based threats providing new opportunities for actors to conceal threats under layers of redirection.
Malware by the numbers
Key Stat: URL-based malicious messages comprised 88% of overall malicious message volumes in Q3
With the exception of spikes in attachment-based malicious emails in June and September, Figures 1 and 2 show the ongoing dominance of URL-based email threats, both in Q3 and quarter-over-quarter. As noted, URL-based malicious messages comprised 88% of overall malicious message volumes in Q3, despite significant shifts in final payloads throughout the quarter and vs. Q2.
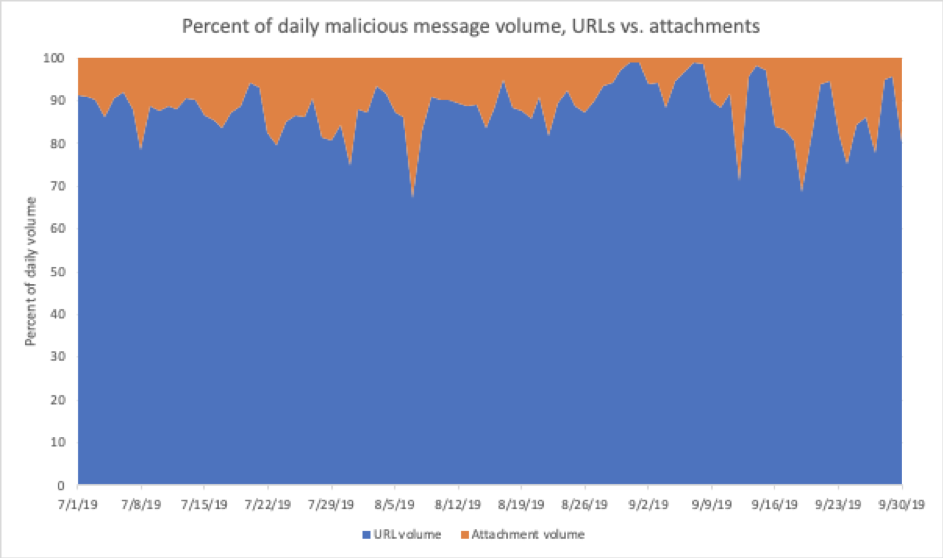
Figure 1: Indexed relative volume of malicious messages with attachment-based vs. URL-delivered payloads, Q3 2019
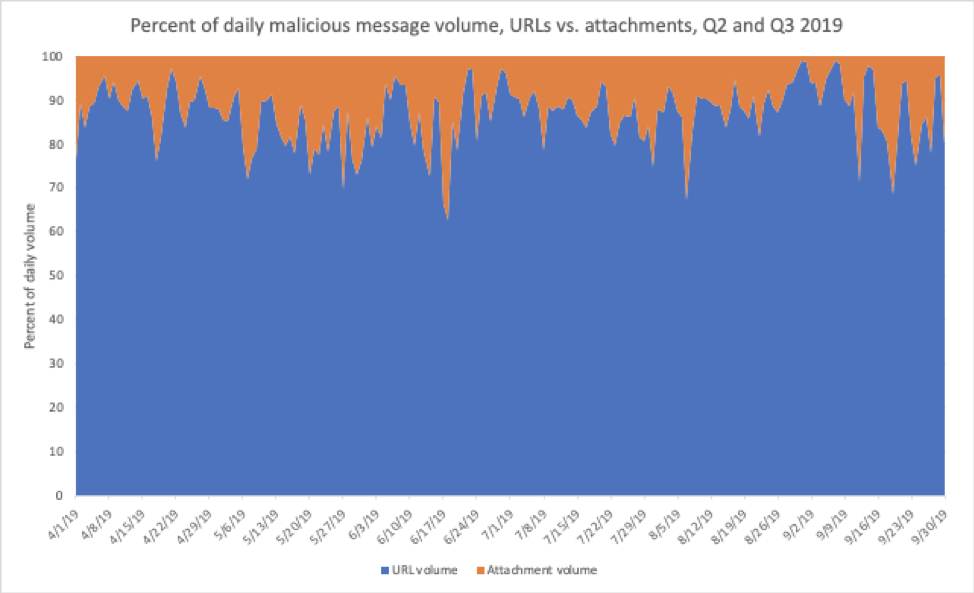
Figure 2: Indexed relative volume of malicious messages with attachment-based vs. URL-delivered payloads, Q2 and Q3 2019
Figure 3 shows the overall distribution of message volumes by malware family in Q3. With Emotet — by far the largest contributor we track to the botnet family — absent for the first ten weeks of Q3, banking Trojans and remote access Trojans (RATs) became the dominant payloads, making up 61% of all malicious payloads collectively.
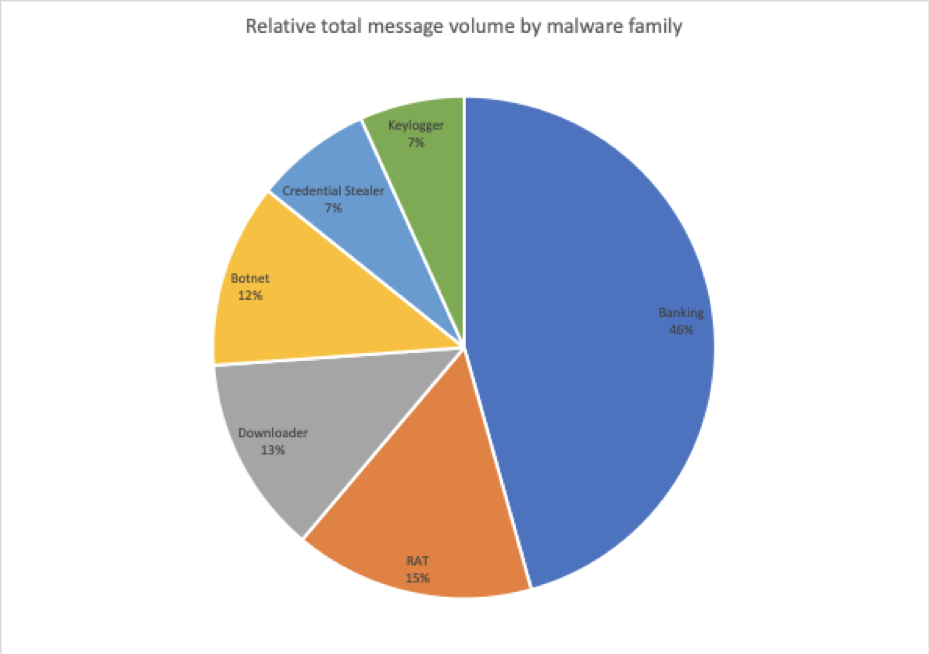
Figure 3: Relative message volumes associated with the top malware families in Q3 2019
The shift in payloads from Q2, when Emotet remained active for the first two months of the quarter, is illustrated in Figure 4. Banking Trojans, RATs, downloaders, and keyloggers all increased relative to overall malicious message volumes; bankers and RATs also increased in terms of absolute message volumes, despite an overall decrease in malicious messages for the quarter, driven by a small number of prolific actors. In general, though, actors continue to focus on distributing versatile malware designed to reside undetected on compromised machines to collect credentials, conduct reconnaissance, move laterally on networks, and enable at-will distribution of secondary payloads.
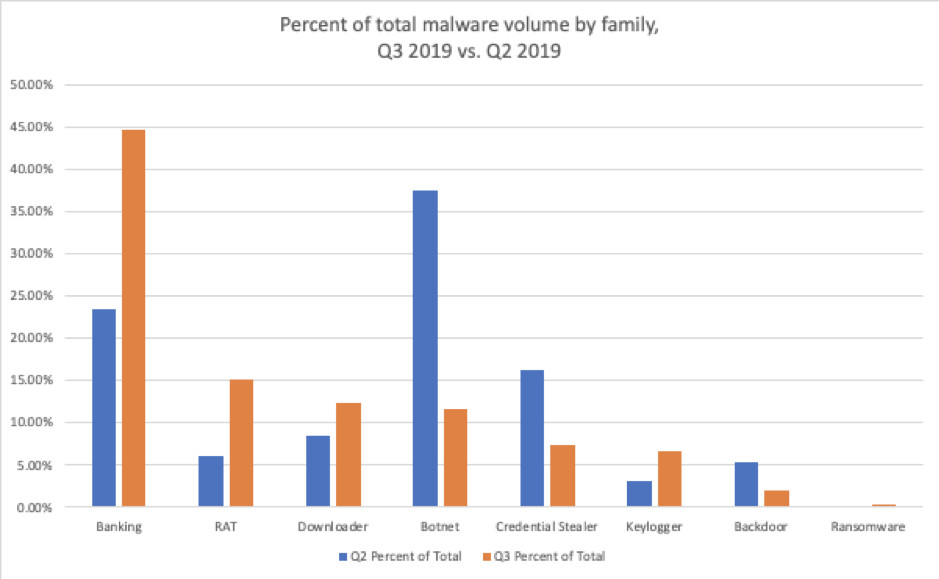
Figure 4: Quarter-over-quarter comparisons of malicious message volume by malware family
As we have seen in recent quarters, ransomware was virtually absent in Q3, although overall volumes of messages with ransomware as the primary payload increased slightly over Q2, driven primarily by small Troldesh and Sodinokibi campaigns throughout the quarter. While specific credential stealer activity decreased, RATs and banking Trojans are increasingly used to steal a range of credentials, with threat actors continuing to deploy robust, modular tools instead of more specialized malware.
Bankers and RATs fill the gap before Emotet returns
Key stat: Overall volumes of banking Trojans and RATs increased by 18% and 55%, respectively vs. Q2 volumes, despite an overall decrease in malicious message volume.
Although the overall volume of malicious messages decreased in Q3 by 39% - largely as a result of the absence of Emotet’s consistent high-volume campaigns - both relative and absolute volumes of banking Trojans and RATs increased, to some extent filling the gap left by Emotet’s absence for most of the quarter. As shown in Figure 4, the relative volume of banking Trojans increased by 21 percentage points relative to other malware families in Q3. RAT volumes increased 9 percentage points vs. Q2. These increases are not simply artifacts of lower overall volumes, however: Actual banking Trojan volumes increased 18% and RAT volumes increased 55% over observed volumes in Q2.
While many actors distributed banking Trojans in Q3, two, in particular, drove volumes with large Ursnif campaigns (actors we track as TA556 and TA544); others consistently distributed The Trick (also known as Trickbot) and an actor we track as TA516 frequently distributed IcedID throughout the quarter. As shown in Figure 5, these three strains made up 83% of banking Trojan payloads in Q3.
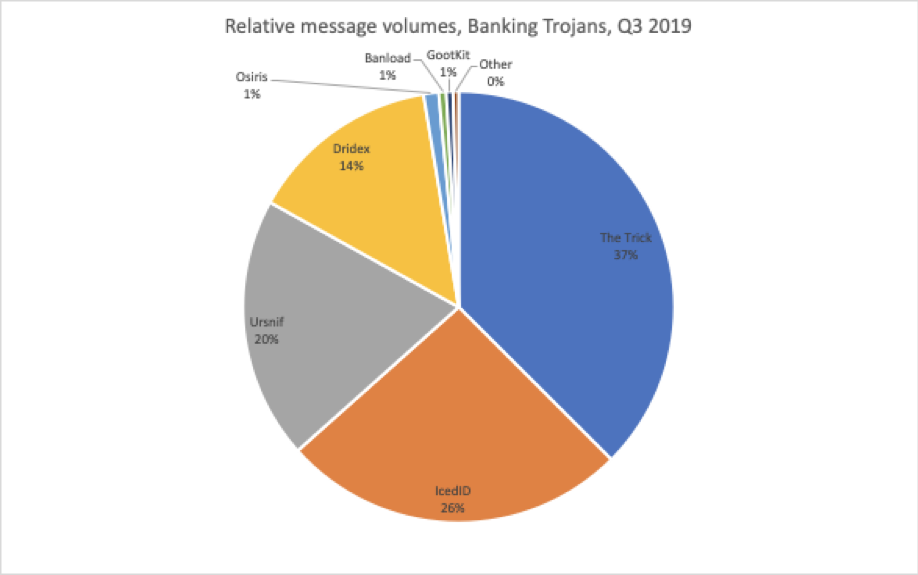
Figure 5: Relative banking Trojan volumes distributed via email in Q3
Similarly, a growing number of actors regularly distribute RATs, but TA505 led with large FlawedAmmy and FlawedGrace campaigns, accounting for 75% of all RAT payloads in Q3 (Figure 6).
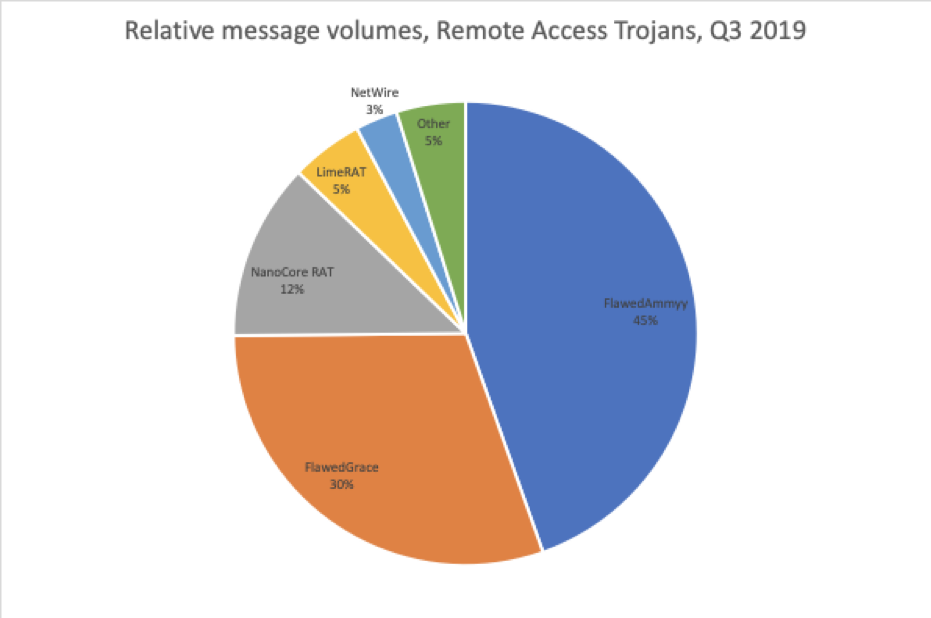
Figure 6: Relative RAT volumes distributed via email in Q3
Emotet roars back in September
Key Stat: Since its return in September, Emotet volumes were sufficient to make up almost 12% of all malicious email samples for Q3 2019.
Between mid-2017, and May 1, 2019, a highly prolific actor we track as “TA542” launched hundreds of increasingly large malicious campaigns distributing the Emotet botnet. Eventually, these campaigns targeted every major geography (North and South America, Western Europe, Asia, and the Middle East) and collectively distributed tens of millions of messages across all industries.
After consistent distribution for the better part of two years and ongoing evolution from a banking Trojan to a robust modular botnet, the malware appeared to be on hiatus throughout the summer of 2019. However, the botnet re-awakened in September and has now fully resumed campaigns in all global geographies through the end of Q3.
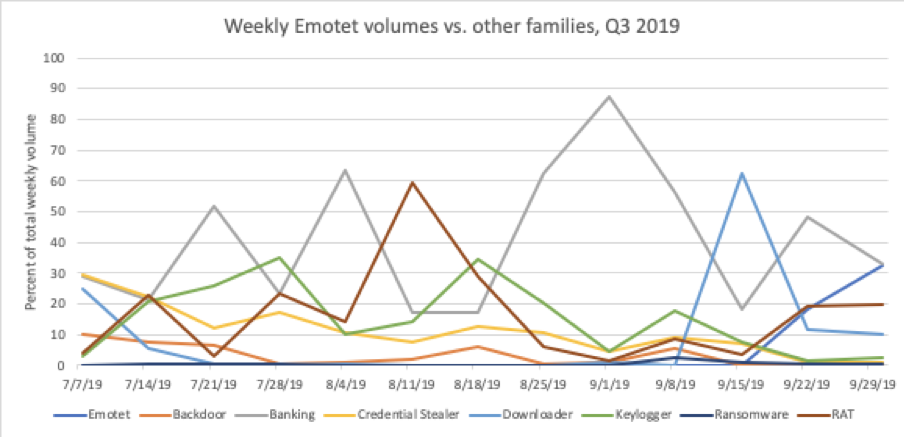
Figure 7: Weekly breakdown of malware message volumes as a percent of total messages comparing Emotet with all other active families for Q3 2019
When campaigns by TA542 resumed on September 16, they generally followed the same model we observed historically: geographically-targeted emails with local-language lures and brands, often financial in theme, and using malicious document attachments or links to similar documents, which, when users enabled macros, installed Emotet.
Within the remaining weeks of Q3, TA542 delivered millions of messages with URLs or attachments leading to infection with Emotet. Volumes were such that Emotet alone made up almost 12% of malicious email samples.
In the third quarter of 2019, the most significant changes in Tactics, Techniques, and Procedures (TTPs) included the addition of new target countries (Italy, Spain, Japan, Hong Kong, and Singapore). Long-standing targets such as the United States, Canada, the United Kingdom, Germany, and Australia, among others continue to be affected.
Notably, the group used a news-related “Snowden” email lure in a campaign on September 23, hearkening to the actor’s much more common practice in 2018 of using seasonal and topically-themed email lures. This practice gave way in 2019 to reliance on email lures with more generic financial themes.
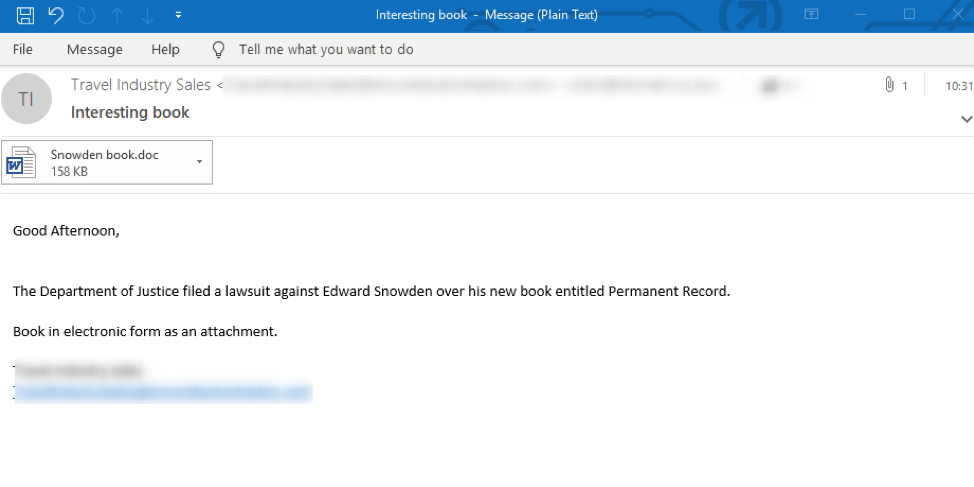
Figure 8: English-language email targeting US and UK organizations with an attachment that, when opened, will prompt the recipient to execute Visual Basic/Microsoft Word macros that will download Emotet
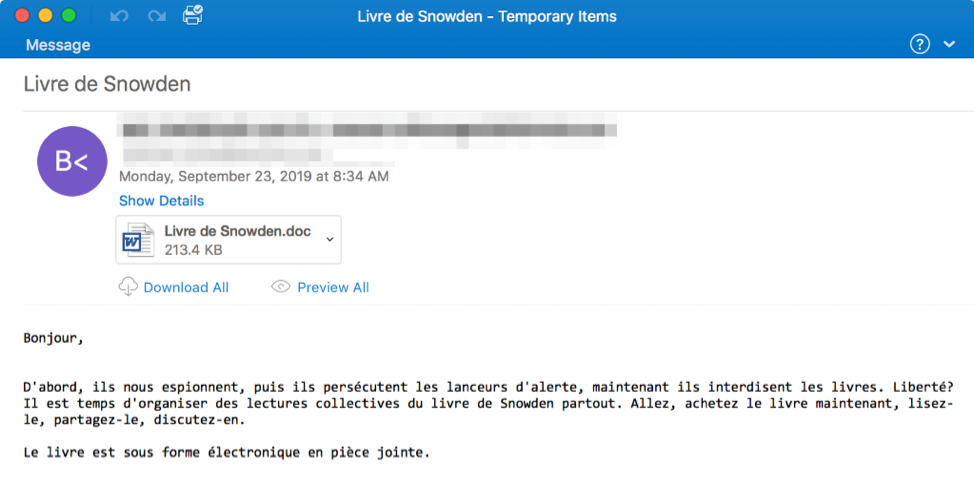
Figure 9: French-language email targeting French and Swiss customers with an attachment that, when opened, will prompt the recipient to execute Visual Basic/Microsoft Word macros that will download Emotet. We also observed local-language, geo-targeted emails in German, Castilian Spanish, and more attempting to install Emotet.
Although Emotet has its own banking module, TA542 continues to use its downloader module to load third-party malware, as well as additional modules for spamming, credential stealing, network spreading, and email harvesting. This behavior following the hiatus mirrors behavior observed beginning in mid-2018 when the actor stopped using Emotet’s banking capabilities and focused on other functions of the botnet, continuing to operate what appears to be a malware-as-a-service operation.
Sextortion Campaigns leverage the Human Factor and highlight new malware behavior
Key Stat: Sextortion remained widespread in Q3, with the appearance of malware that could potentially provide actual evidence of adult activity for threat actors instead of strictly relying on social engineering and related scams.
In the third quarter of 2019, Proofpoint researchers observed continued widespread instances of traditional sextortion via social engineering methods as well as malware campaigns (as we saw with recent PsiXBot activity) with the potential to feed sextortion scams with actual video, locally stolen credentials, and more to increase the likelihood of recipients making the requested blackmail payments.
In many campaigns, such as those sent September 7 through 14, a user is sent an attachment (usually a PDF) requesting payment by Bitcoin to avoid video and keylogger evidence of potentially embarrassing online activity being sent to the recipient’s email and social media contact list.
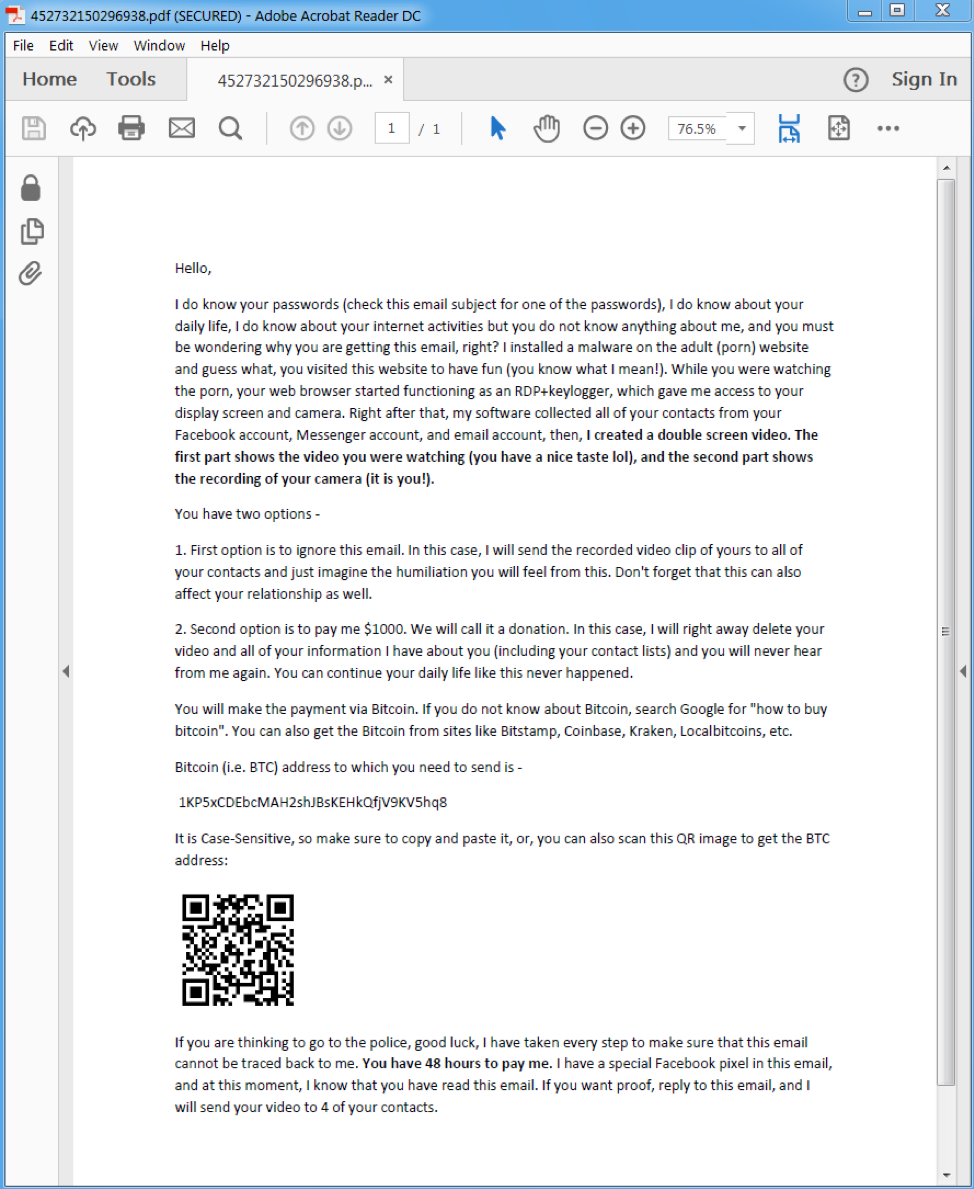
Figure 10: Sample email attachment requesting Bitcoin payment by a sextortion social engineering actor.
Noteworthy campaigns were also sent via the Phorpiex botnet. Phorpiex sextortion campaigns in Q3 used social engineering instead of actual evidence of questionable activity to trick recipients with a sextortion scam. Subject lines in these emails include:
- Can publish everything
- Dirty video of you
- I know everything
- I recorded you
- Pervert
- Recorded you
- Save yourself
- Seen everything
- Video of you
- You better pay me
- You got recorded
- You pervert
- Your chance
- Your privacy
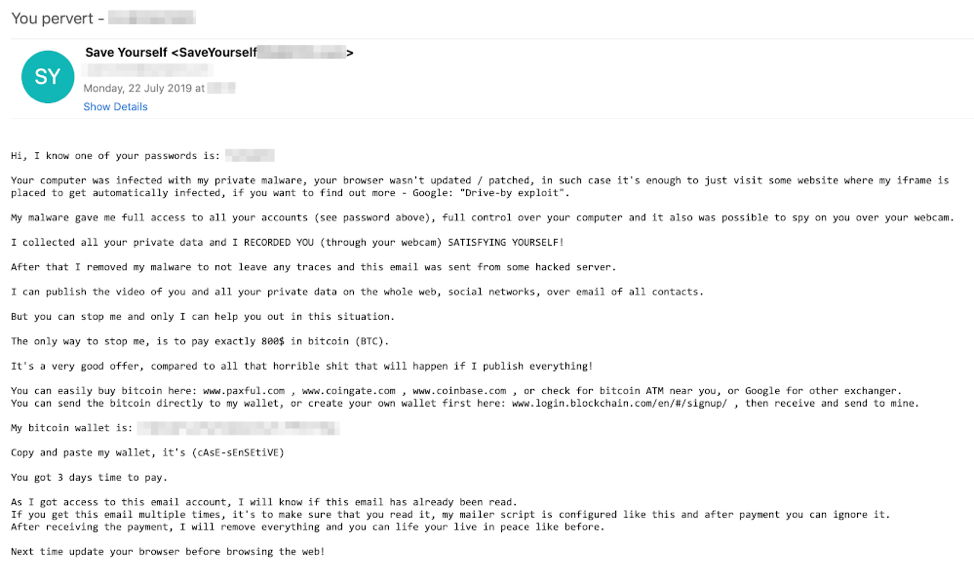
Figure 11: An example of a malicious social engineering email sent by the Phorpiex spam agent.
In addition to traditional social engineering-based sextortion attacks, in the third quarter of 2019, Proofpoint researchers observed malware with potentially much more sophisticated extortion capabilities. One malware, PsiXBot, a remote access Trojan (RAT) installed via malicious email attachments and Windows exploit kits, expanded its stealthy communication capabilities in September and raised the stakes for sextortion with the addition of a new “PornModule”.
Similar to functionality observed recently in other malware campaigns, this malware module contains a dictionary containing pornography-related keywords used to monitor open window titles. If a window matches the text, it will begin to record audio and video on the infected machine. Once recorded, the video is saved with a ".avi" extension and is sent to the command and control server, and then (presumably) used for extortion purposes.
This module appears incomplete and will likely be modified in future releases. We will continue to monitor this activity both in PsiXBot and in the broader landscape.
Keitaro TDS breathes new life into RIG and Fallout exploit kits
Key stat: Threat actors leveraged Keitaro TDS in millions of malvertising impressions and URL-based malicious messages.
Recently, Proofpoint has observed several malicious email campaigns, as well as dedicated malvertising campaigns, with links ultimately leading to a range of malware that leverage the Keitaro TDS and various exploit kits (EKs) to evade detection. Traffic distribution systems (TDS) like Keitaro are software and service packages that intelligently route web traffic, providing high degrees of flexibility and control for threat actors. Keitaro is actually a legitimate service (https://keitaro[.]io) that can be used by online advertisers but is frequently abused by malvertisers and others looking to segment web traffic for nefarious purposes.
When users click links to Keitaro sites in malicious emails, they may be redirected to:
- Sites with malvertising, which lead to infection via exploit kit
- Directly to hosted malicious files such as zipped VBS or JavaScript
- Legitimate sites.
We also observed Keitaro appearing in collateral activity with users encountering malvertising and then being directed to EKs via Keitaro.
Redirection is based on a number of factors including:
- Browser version
- Geographic location
- OS/platform
- Mobile carrier
Keitaro can be used to detect potential markers of research environments and sandboxes, redirecting browsers seamlessly to legitimate sites and thwarting automated detection of malicious redirection. Because Keitaro also has many legitimate applications, it is frequently difficult or impossible to simply block traffic through the service without generating excessive false positives, although organizations can consider this in their own policies.
In August, Keitaro redirected users to either Fallout or RIG EK, often via malvertising, depending upon geography and potential vulnerability, ultimately leading to potential infections with malware strains including:
- AZORult (sometimes downloading ServHelper)
- Predator the Thief downloading some CoinMiner
- KPOT
- SystemBC
- Osiris
- Chthonic
- Vidar Stealer
- Amadey downloading Danabot "40"
- Amadey downloading Vidar
- Gootkit
- Onliner
We continue to proactively monitor Keitaro to improve immediate detection of abusive applications, rewriting and condemning URLs in malicious email campaigns.
Domain Threats
Key Stat: 26% of fraudulent domains detected in Q3 used a secure certificate.
With the rise in URL-based malicious messages, as well as ongoing use of web properties for a variety of nefarious purposes, we regularly track suspicious and fraudulent domains across the web. For Q3, most notably, the trend towards the disproportionately high implementation of secure certificates on fraudulent websites continued, with over three times as many fraudulent sites using SSL certificates as observed on all domains. Over 26% used an SSL certificate, up from 20% at last report in Q1. This contributes dramatically to social engineering around these domains as users have been conditioned to look for the padlock icon as a sign of security and safety as they browse.
Similarly, a far greater percentage of fraudulent websites resolve to an IP address and generate an HTTP response, indicating that they are actively maintained and ready for use in malicious campaigns. This remains in contrast to domains across the web that are often parked, forgotten, or simply registered without an associated web presence. Lower implementation of MX records among fraudulent domains continues to suggest that threat actors only create such records if they intend to use the domains for email-based attacks.
|
Type of suspicious domain/web property |
% resolving to an IP address |
% with an HTTP response |
% with MX records |
% with an SSL certificate |
|
All domains |
69.64% |
48.98% |
42.32% |
7.95% |
|
Fraudulent domains |
87.5% |
82.9% |
27.29% |
26.08% |
Table 1: A comparison of fraudulent and legitimate domains by resolvable IP addresses, MX records, and valid SSL certificates
Moreover, the top-level domains (TLDs) used with fraudulent sites continue to reflect their use in social engineering, relying most heavily on .com. This remains the most common and trusted TLD on the broader web, with widespread associations with legitimate web properties (Figure 10).
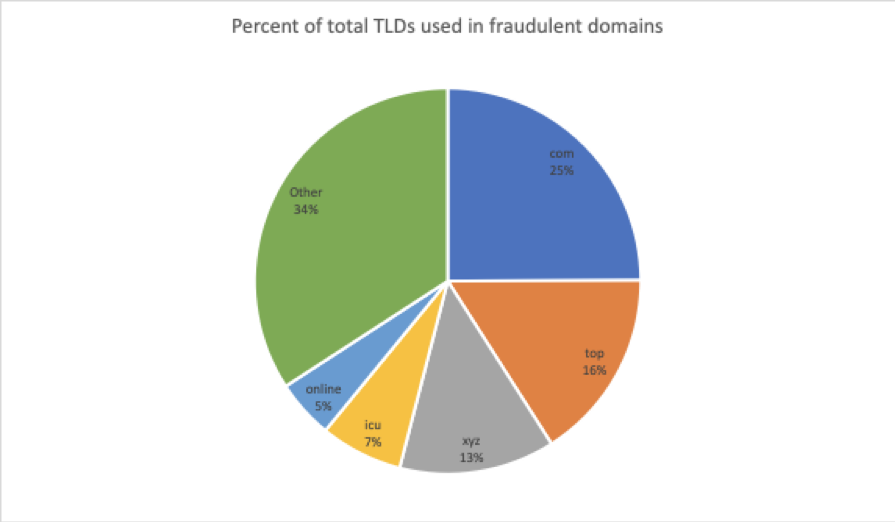
Figure 12: Top TLDs used for fraudulent domains
Proofpoint Recommendations
This report provides insight into the shifting threat landscape that can help inform an organization’s cybersecurity strategy. Here are our top recommendations for how companies can protect their data, customers, and brands in the coming months.
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Deploy robust layered defenses. Threats range from high-volume malware to highly-targeted, low volume business email compromise scams that often have no payload at all and are thus difficult to detect. Network and web-based threats may also affect users, while impostor threats require scalable solutions that defend against a variety of identity deception techniques and should, where possible, include full implementation of DMARC.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile — especially fraudulent accounts that piggyback on your brand. Look for a comprehensive domain fraud solution that scans the web and reports fraudulent and suspicious activity.
Partner with a threat intelligence vendor. Smaller, more targeted attacks call for sophisticated threat intelligence. Leverage a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets — and then learns from them.











