Overview
This week Proofpoint researchers observed several noteworthy changes in the macros used by an actor we refer to as TA530, who we previously examined in relation to large-scale personalized phishing campaigns [1] [2]. This new campaign included evasive macros, which, while not unusual for this group (earlier versions were analyzed by Mcafee [3] and Checkpoint [4]), demonstrated continued evolution in their latest iteration. Most notably their new macro looks up the public IP address of the client and does not download the payload if it finds that the IP address is associated with a security vendor, certain cloud services, or a sandbox environment.
This week, we observed TA530 using their evasive macros to deliver Nymaim, Ursnif, and Dridex 124. The Dridex payload with botnet ID 124 is a previously unseen sub-botnet which is targeting Swiss banking sites, while the Nymaim and Ursnif payloads targeted North America and Australia, respectively.
Email Campaign
Following their usual trend [1], TA530 used personalized messages (Figure 1 and 2) utilizing company names, personal names, titles, etc, to deliver the Word documents (Figure 3 and 4). Document lures were tailored to the target’s language based on location and continue to be regularly updated.
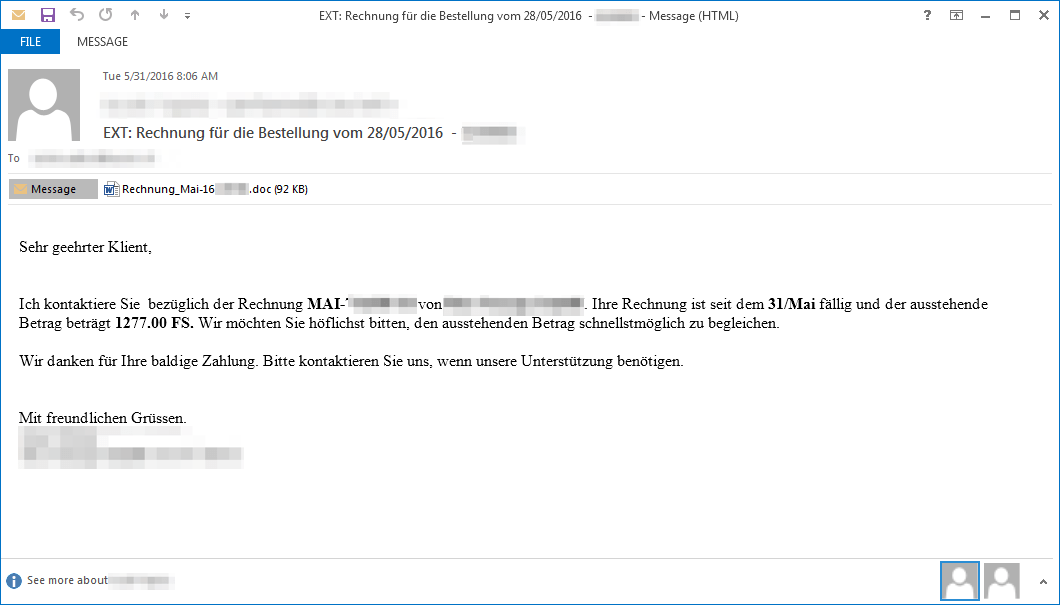
Figure 1: Email with a German-language billing (“Rechnung”) lure used to deliver Dridex botnet 124
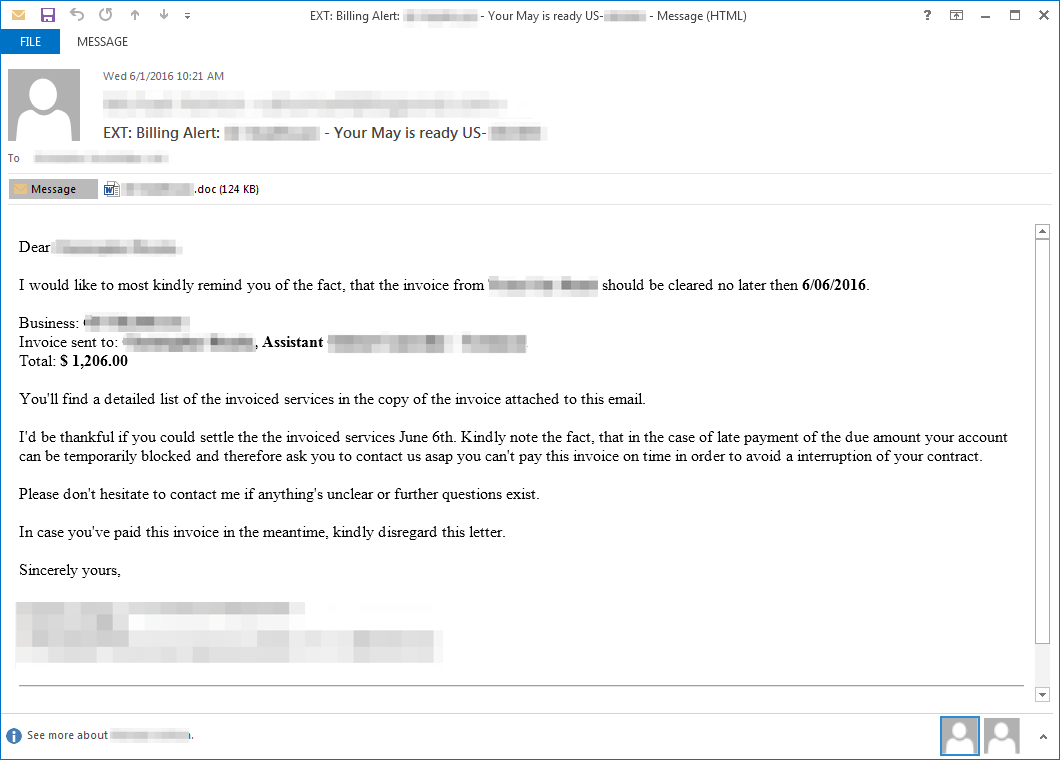
Figure 2: Email with an English language invoice lure used to deliver Nymaim
Figure 3: Document attachment used to deliver Dridex botnet 124
Figure 4: Document attachment used to deliver Nymaim with a spoofed Intuit logo to increase the sense of legitimacy
Macro Analysis
The macros contact a well-known geo-location service (MaxMind) and check the returned result against a blacklist of strings. These strings are actually network names corresponding to the client’s IP address. If a match is found, the macros exit without downloading the payload. The deobfuscated array of blacklisted networks includes the names of some security vendors and research groups that the actors want to avoid, as well as generic terms for hosting and services that might indicate a connection to vendors or researchers:
Array("Amazon", "Anonymous", "Blue Coat Systems", "Cisco Systems", "Cloud", "Data Center",
"Dedicated", "ESET, spol", "FireEye", "Forcepoint", "Hetzner", "Hosted", "Hosting",
"LeaseWeb", "Microsoft", "NForce", "OVH SAS", "Security", "Server", "Strong Technologies",
"Trend Micro", "blackoakcomputers")
The macros also contain a new check for the number of files recently accessed by Microsoft Word using the Application.RecentFiles property [5]. This is an attempt to prevent the malicious document from executing in a sandbox environment, since sandboxes will most likely not have any recently-opened files. The check specifically verifies that more than two Word files were recently opened:
If CallByName(CallByName(Application, "RecentFiles", 2), "Count") < 3 Then Error 4 End If
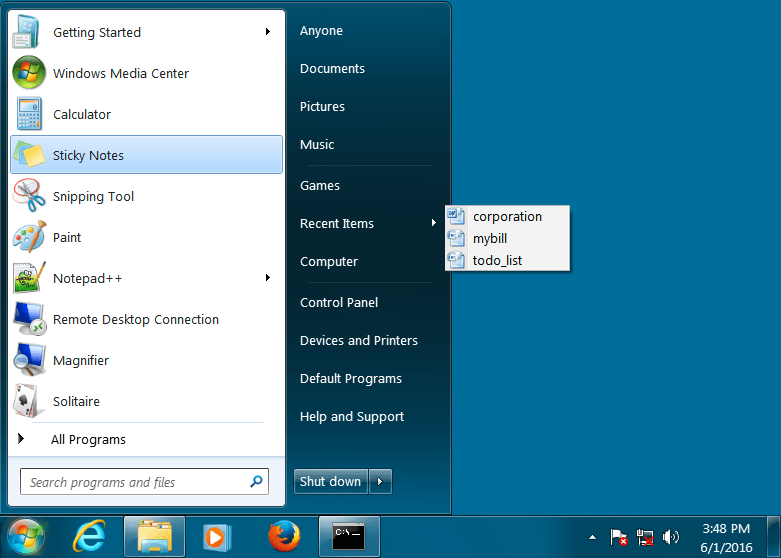
Figure 5: If the “Recent Items” menu does not contain 3 or more recently-opened Microsoft Word documents as shown in this figure, the malicious Word document will not fetch the secondary payload
The macros used by this actor have been using sophisticated string obfuscation for some time. For example, the string “RecentFiles” used in the check for presence of recently opened files is actually encoded and deobfuscated by the following code, which excludes the characters in the second string from the first string:
hpkdusyqHacWI.FcQeBZj("8Rxe5cexnDQtF8ivlQe 5s", "x5vQ2D HC8y")
Dridex Payload
The Dridex being delivered by TA530 this week is using a previously unobserved sub-botnet ID “124”; however, the command and control (C&C) infrastructure is shared with the other 12x botnets. We have observed this botnet targeting Swiss banking sites with its webfakes (phishing pages replacing the actual content). TA530 has delivered Dridex in the past (botnet 222 and 322), but those botnets targeted UK banking sites, so the Swiss targeting appears to be a change in targeting for this group.
Conclusion
TA530 continues to innovate with its macros and delivery tactics. This particular sandbox evasion technique has not been observed in the past on this scale, and we can expect that this threat actor will continue improving their evasion tactics. This will demand continued vigilance on the part of security researchers and vendors, as well as savvy end users trained to spot suspicious emails and potential lures.
References
- https://www.proofpoint.com/us/threat-insight/post/phish-scales-malicious-actor-target-execs
- https://www.proofpoint.com/us/threat-insight/post/abaddonpos-now-targeting-specific-pos-software
- https://blogs.mcafee.com/mcafee-labs/macro-malware-employs-advanced-obfuscation-to-avoid-detection/
- http://blog.checkpoint.com/2016/05/20/spear-phishing-2-0-adds-social-engineering-vm-evasion/
- https://msdn.microsoft.com/en-us/library/office/ff195679.aspx
Indicators of Compromise (IOC)
|
IOC |
IOC Type |
Description |
|
a8ae681463b75470be8dc911f0cf7ca01a2eaea87005564263a5bbe38d652369 |
SHA256 |
Nymaim Document |
|
f73fcbf4cf9a775d4d4abf53c13a0136a120d5a7e015942a7a43f686f266bf70 |
SHA256 |
Ursnif Document |
|
72acb7dd6bea232c623367a4d3417d0ee7d412d3df5a0287d621716f5a69ab06 |
SHA256 |
Dridex Document |
|
[hxxp://britcart[.]com/britstar/office12.data] |
URL |
Example Ursnif Download |
|
[hxxp://arabtradenet[.]com/info/content.dat] |
URL |
Example Nymaim Download |
|
[hxxp://onehealthpublishing[.]com/image/office.gif] |
URL |
Example Dridex Download |
|
f34589058db1a8cdb31c79eec88bd851cf3e2157501760f1c0263523d614d8f9 |
SHA256 |
Example Nymaim Payload |
|
6b588ff17412c4a8221521ab70d7d0230c339ed4c5c96c181e4010ba0007e879 |
SHA256 |
Example Ursnif Payload |
|
97b1e8282d1ec8f82a83eb3d8a991f494e332e4059b1c9f0d53beda257e21629 |
SHA256 |
Example Dridex Payload |
Select ET Signatures that would fire on such traffic:
2022799 || ET TROJAN Malicious SSL certificate detected (Ursnif Injects)
2816668 || ETPRO TROJAN W32/Nymaim Checkin 6
2816395 || ETPRO TROJAN Nymaim Checkin 5
2816669 || ETPRO TROJAN W32/Nymaim Checkin 7
2404312 || ET CNC Feodo Tracker Reported CnC Server group
2022627 || ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex)











