Business email compromise (BEC) and email account compromise (EAC)—a collective $26B problem—are issues that organizations of all sizes, in all industries, must address.
Our "Combatting BEC and EAC" blog series dives into how you can stop these threats at your organization. Each post focuses on one of seven key steps. We tackle the fifth step in this blog post: visibility into who attackers are targeting.
From LinkedIn to Google and other various websites, there is plenty of information that attackers can use to be prescriptive about who they target within an organization. But the question is, do you know who they are targeting and why? It may be a surprise that it’s not only C-level executives that are targeted by these types of threats. We have seen threat actors target regular employees with BEC and EAC as they have financial permissions and access critical systems as well.
That is why you need a solution that can give you detailed visibility into the threat landscape. Proofpoint is the only vendor who can give insight into who your Very Attacked People are and if they are being targeted by Impostor or BEC and credential phishing, which leads to EAC. These attacks are hard to pinpoint because they are exceptionally few and contain no payload. However, in the TAP dashboard, you can easily identify which users are being targeted by these types of threats.
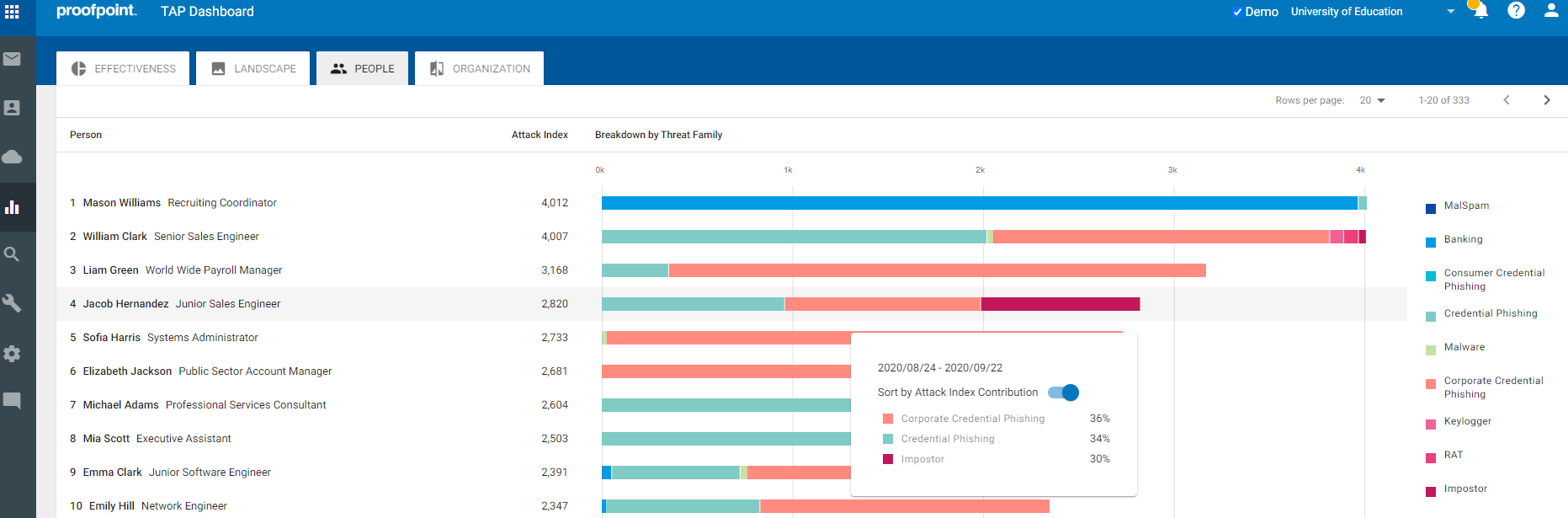
Figure 1: VAP Report inside TAP Dashboard
In figure 1, you can see the TAP Dashboard showing who your VAPs are and threats targeting each of them. Specifically, impostor or BEC threats are highlighted in dark red.
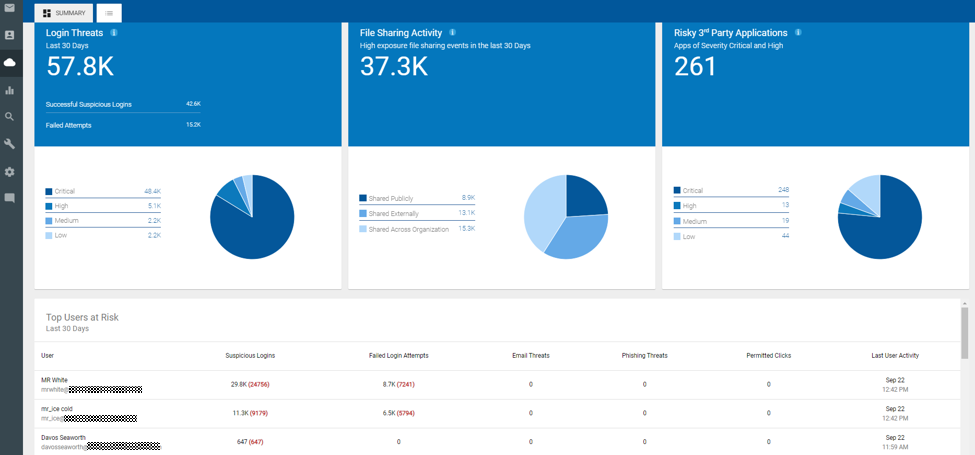
Figure 2: Cloud App Activity Report inside TAP Dashboard
In terms of EAC type threats, Proofpoint is the only vendor who cross correlates cloud and email threat data to understand which accounts may be at risk of compromise. Again, in figure 2, the TAP dashboard shows your top users at risk based on suspicious log-ins and failed log-in attempts.
You can even see if those users have received phishing threats or even clicked on a URL that had the user surrender their log-in information.
What can you do with this visibility?
There are a number of adaptive controls that you can implement based on this detailed visibility:
- Enroll users in specific training. Proofpoint has over 170 Training modules that help users understand the latest on the threat landscape and how to identify if they are being targeted. Organizations can also leverage the VAP data to enroll users into specific targeted training for the right people at the right time.
- Enable risk-based isolation for URL clicks. Organizations can extend protection for VAPs through integration with Proofpoint Email Isolation. It does this by enabling risk-based isolation for URL clicks within corporate emails. With our unique approach to protecting people, we can highlight your most attacked people and determine the riskiest URLs that get into your users’ inboxes. By doing this, we can isolate risky URL clicks to help prevent threats and credential phish from impacting your organization.
- Leverage Ecosystem Partners. Proofpoint partners with other security industry leaders such as Okta, SailPoint and CyberArk. With our ability to detect users clicking on suspicious URLs, we can pass this information to anyone of these partners along with our VAP intel. From there, Okta, SailPoint and CyberArk can apply adaptive controls to these users.
Learn More
As BEC and EAC expand, having multi-layered security is critical to protecting your organization from these costly threats. To find out if your organization is adequately protected from BEC and EAC attacks, take our complimentary assessment here.











