The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organisations better fortify their defences to protect people against today’s emerging threats.
This month’s Stop highlights one of the most high-risk, high-impact attack scenarios that we see: account takeovers (ATOs). While phishing emails are often the entry point, today’s attackers have multiple options for breaking in. These include brute-force attacks, multifactor authentication (MFA) bypass (like SIM swapping), adversary-in-the-middle (AiTM) attacks, helpdesk social engineering and malware, to name a few. All these tactics can lead to a successful ATO, especially in digital workspaces where identity is the new perimeter.
Background
ATOs are so dangerous because once an attacker gains access to a legitimate account, the system they’ve breached assumes they’re trustworthy. It doesn’t matter if that account belongs to an employee, a partner or a supplier.
Once inside, attackers can bypass many security controls and cause exponential damage. Potential activities include internal phishing, business email compromise (BEC), financial fraud and data theft.
To give you a sense of the scope of this problem, here are just a few ATO statistics from Proofpoint proprietary data:
- 99% of organisations observed attempted account takeovers
- 62% of organisations experienced a successful ATO
- Even with safeguards in place, 65% of compromised accounts had MFA enabled
The scenario
An employee at a global technology company was tricked into entering their credentials into a spoofed login page. As a result, their Microsoft 365 account was compromised. Proofpoint could not attribute the attack to a specific known threat actor group; however, we identified that it came from a residential IP address in Ilorin, Nigeria—a city that’s known for cybercriminal activity.
The threat: How did the attack happen?
Here’s what the attack flow looked like:
1. Gaining initial access. The attacker likely initiated the compromise using social engineering tactics, which led the victim to a spoofed login page. While the exact entry method is unclear, the infrastructure and tactics used suggest a phishing-as-a-service (PhaaS) toolkit was involved. Specifically, it looked like the AiTM reverse proxy tool known as Sneaky 2FA.
2. Bypassing MFA. Once credentials were entered, Sneaky 2FA intercepted the session token. This allowed the attacker to bypass MFA and hijack the user’s session.
From there, the attacker:
- Inserted a mailbox rule labelled ‘.’. This subtle naming choice was intended to evade notice if the account owner reviewed their mailbox rules; however, more importantly, the rule rerouted emails from a specific sender (a supplier’s production manager) into the junk folder. This effectively hid evidence of the compromise from the legitimate user and allowed the attacker to operate under the radar.
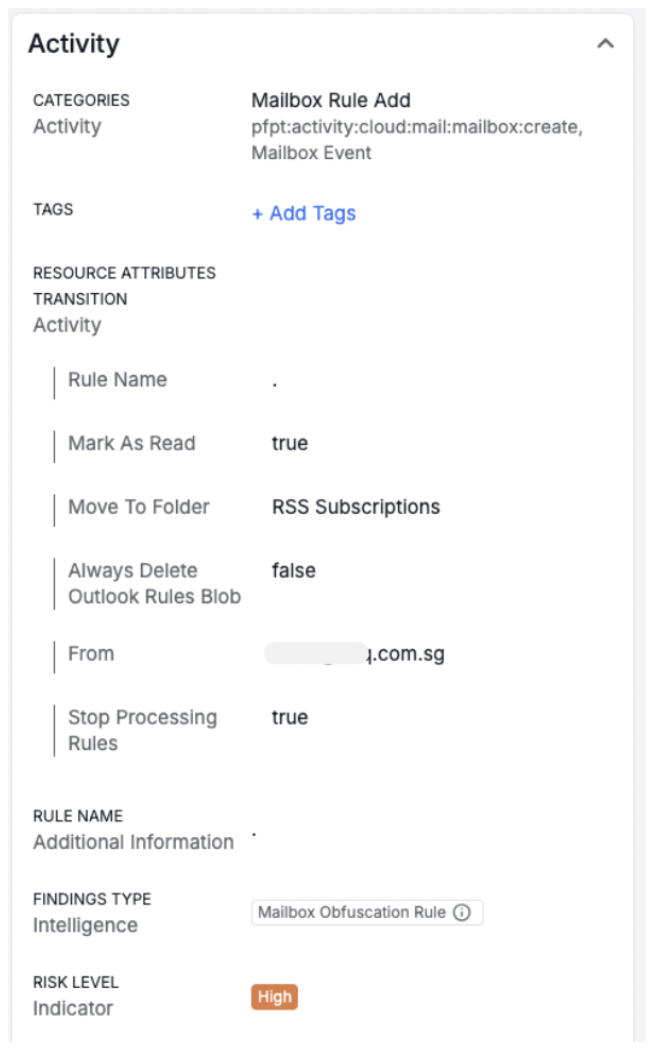
Proofpoint Prime Threat Protection identifies a mailbox rule ‘.’ was added.
- Accessed 164 emails. The threat actor targeted documents that were related to quality management, sales performance and financial statements. It’s unclear whether they had a specific goal, but the behaviour indicates they were searching for high-value data that could be sold.
- Shifted IP locations throughout the session. The attacker attempted to mask their location as Singapore via VPN. At some point, though, it appeared that their connection was interrupted, which exposed their residential IP in Nigeria.
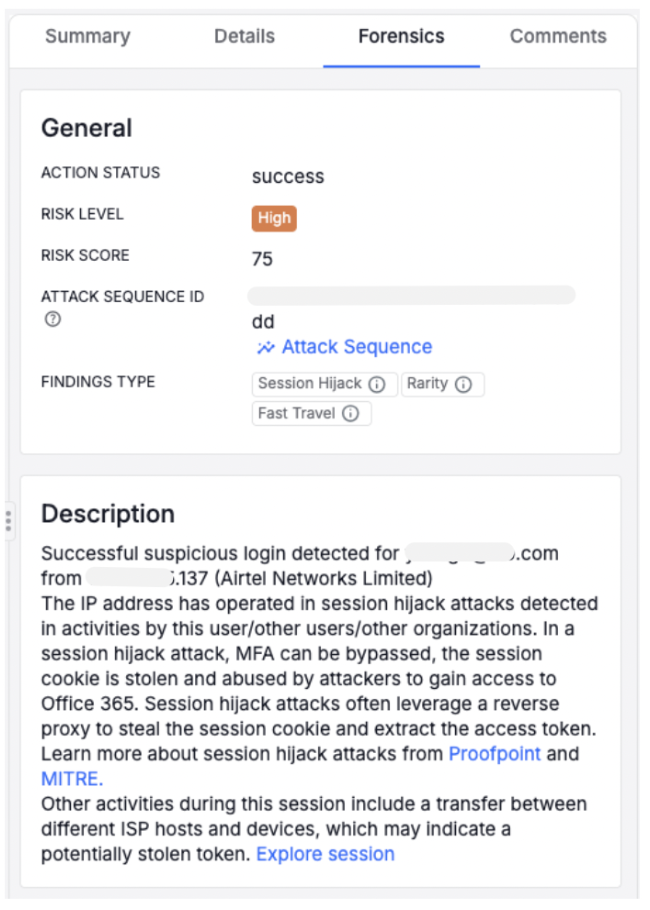
Proofpoint Prime Threat Protection identifies the same Microsoft session with different access sources (Nigeria and Singapore).
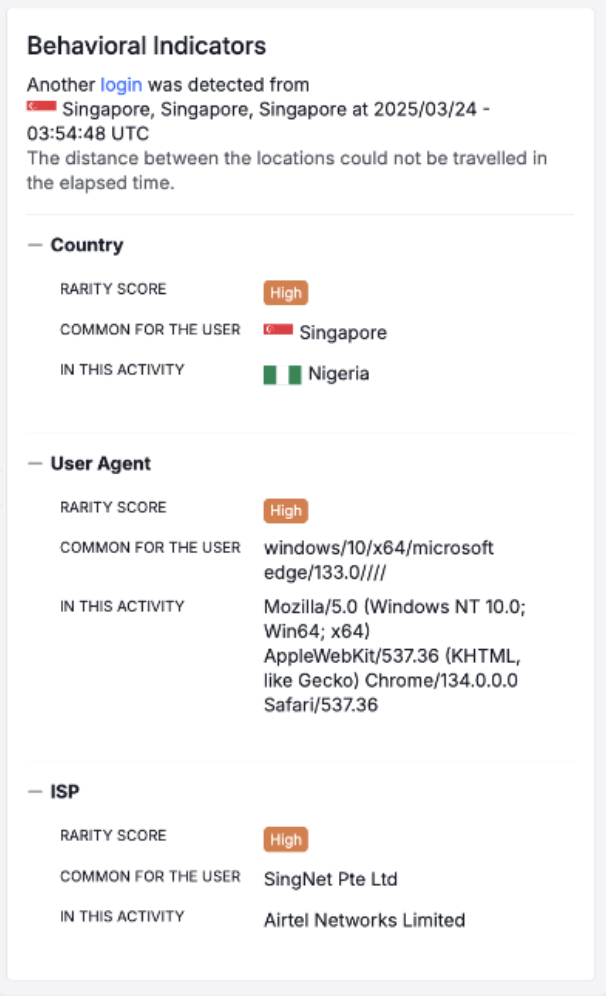
Proofpoint Prime Threat Protection identifies logins from Singapore and Nigeria in a short time span as well as access from unusual locations and devices.
Ultimately, the attack was disrupted before any damage could be done, but it still provides a valuable lesson about the danger of ATOs. This attack shows that once an ATO occurs, bad actors can deeply embed themselves within an environment.
Several months later, more access attempts coming from an IP in Nigeria were identified and blocked. This validates the need for ongoing monitoring and layered defences.
The detection: How Proofpoint stopped the attack
Proofpoint’s Nexus AI was instrumental in detecting this account compromise. A part of our human-centric security platform, Proofpoint Nexus is an ensemble of AI models. It continuously analyses billions of email, web and cloud interactions to detect and prevent human-targeted threats, including ATOs, phishing and data exfiltration.
In this incident, Nexus AI detected suspicious activity through a combination of behavioural and contextual signals, including:
- The post takeover activity, including an added mailbox rule with a vague rule name and a reverse proxy login sequence that indicated the use of a phishing-as-a-service MFA bypass kit (AiTM)
- Sudden ISP and user agent changes mid-session, from Singapore to Nigeria
- A significant deviation from normal user behaviour, such as abnormal login geography and devices
These insights were not only informed by customer-specific baselines, they were also enriched by real-time threat intelligence across Proofpoint’s global customer base. Nexus AI is powered by a combination of AI-driven models, including advanced machine learning and large language models (LLMs). These tools are trained on real-world user communication behaviours and the tactics, techniques and procedures of threat actors observed across more than two million customer deployments. All of them work together to flag high-risk activity quickly and accurately.
As a result, Proofpoint automatically flagged the session as an ATO. This triggered swift investigation and containment through automated remediation workflows, effectively stopping the attack before any damage could be done.
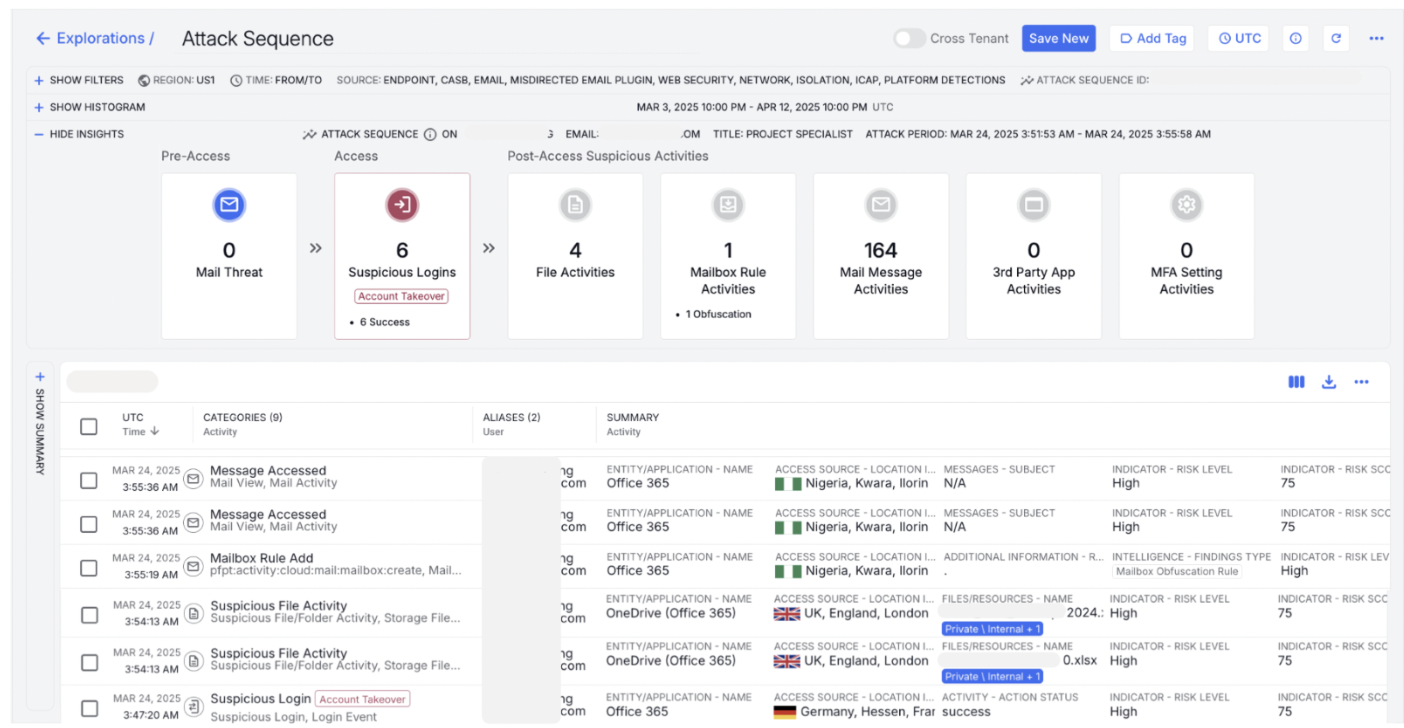
Prime Threat Protection reports ATO and post-ATO sequence.
The remediation: What are the lessons learned?
This incident reinforces several critical truths about cybersecurity:
- MFA is good, but not good enough. Tools like Sneaky 2FA can bypass MFA, especially when AiTM tactics are in play. While MFA raises the bar for attackers, it’s not a silver bullet.
- Attackers exploit multiple channels. Not every ATO begins with a malicious email. Attackers can use other tactics to achieve a successful account takeover. They include brute-force attacks, MFA bypass techniques, like SIM swapping, helpdesk social engineering and malware.
- Visibility is critical. The moment an attacker gains access, every second counts. Without immediate detection and response, attackers can move laterally, exfiltrate sensitive data or establish long-term persistence. To stop them, organisations need to see what threat actors are doing. This ensures they can quickly detect the intrusion, understand what happened and contain the threat.
- Automation helps with damage control. Automated tools for response limit an attack’s impact and ensures that the right follow-up actions are taken. (In this case, the action was automatically disabling a malicious mailbox rule.)
Why Prime Threat Protection matters
This real-world scenario underscores why modern organisations need more than siloed solutions. In today’s continuously evolving threat landscape, no single security control is 100% effective. A strong defence-in-depth strategy is critical to stop an account takeover. You need advanced threat detection and targeted guidance, education and tools to protect against ATO attacks.
Proofpoint Prime Threat Protection gives you a comprehensive platform that not only can help prevent threats across multiple channels and attack stages but can also help detect and remediate sophisticated compromises like the attack above. It can even help protect your organisation when MFA is bypassed.
At the heart of Prime is ATO Protection. This solution continuously analyses login behaviour, location shifts, session patterns, post access impacts and threat intelligence to detect and shut down suspicious activity in near real time.
If your security stack can’t catch an attack like this one, especially before damage occurs, it’s time to rethink your approach. Proofpoint Prime delivers the visibility, automation and speed you need to stay ahead of today’s human-centric threat landscape.
Learn more about Proofpoint Prime Threat Protection.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our other blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analysing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioural AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Vendor Email Compromise in the Public Sector (November 2024)
- How Proofpoint Stopped a Dropbox Phishing Scam (December 2024)
- E-Signature Phishing Nearly Sparks Disaster for Electric Company (January 2025)
- Credential Phishing that Targets Financial Security (February 2025)
- Luring Victims with Free Crypto to Steal Credentials and Funds (April 2025)
- Stopping Phishing Attacks that Pivot from Email to SMS (May 2025)
- Adversary-in-the-Middle Attacks that Target Microsoft 365 (June 2025)











