Security practitioners need effective ways to predict and reduce future sources of risk to prevent their organizations from getting breached. Research for the 2021 Voice of the CISO Report from Proofpoint underscores that need: Only 66% of chief information security officers (CISOs) surveyed said they believe their organization is prepared to cope with an attack. With 90% of Enterprise organizations targeted by ransomware attacks via email in Q4 of 2020 alone, security teams must remain vigilant to keep their users safe.
Identifying user risk and its impact can go a long way toward helping an organization prevent a breach. Proofpoint’s Nexus People Risk Explorer looks at holistic risk by analyzing the vulnerabilities of user groups and the privileges they have based on their roles and associated activity. It accounts for the following variables:
- Likelihood of a person falling for an attack
- Probability of a person receiving an attack
- Impact on the broader organization if a person with access to sensitive data falls for an attack
Nexus People Risk Explorer aggregates Proofpoint product data and uses it to provide greater visibility into people risk. By surfacing the riskiest users, displaying their vulnerabilities and privileges, and providing security control recommendations, security teams can more effectively:
- Identify people for investigation (triage)
- Evolve decisions about the security controls they should apply and to whom
- Monitor risk changes over time to justify future security spend and projects to management and the board
The depth and breadth of Proofpoint’s product integrations help our customers predict and reduce future sources of risk.
Recent risk study finds senior leadership roles are primary attack targets
Proofpoint recently conducted a risk study of Nexus People Risk Explorer users. The purpose of the 10-day study, which included 6.5 million unique users, was to analyze how risk manifests by seniority and business function across attack and vulnerability risk variables.
The data below shows that executives, vice presidents and directors have, on average, higher attack risk scores than other roles lower in the organizational hierarchy (such as managers, employees and contractors). While the difference between attack scores might be slight, executives, vice presidents and directors are still more attacked than other roles.
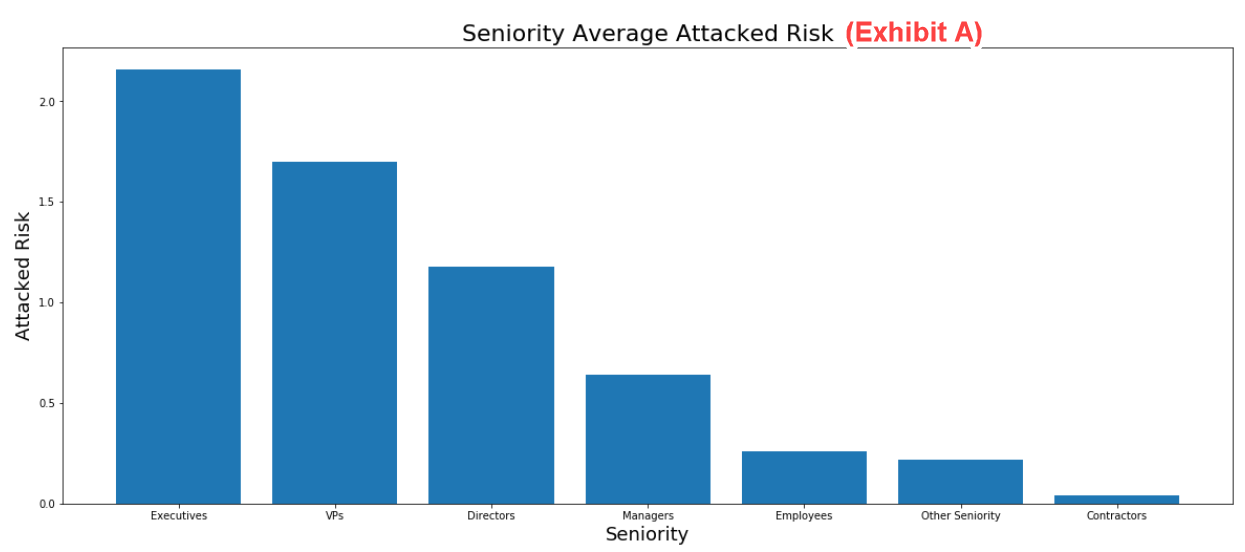
Figure 1. Seniority average attack risk data
Inferences and recommended actions
We hypothesize that attackers target senior leadership more heavily because these roles typically have access to privileged company information and the authority to sign off on payments and other financial documents.
We recommend that security teams assess the controls they’ve implemented for people who are more visible in the organization and more attacked than others based on their role. CISOs should consider working with a cybersecurity vendor who can help ease the burden on their teams and aid the organization in mitigating risk by increasing visibility into all activity.
Risk study surfaces unexpected “highly attacked” roles
The business function data from our recent risk study shows that the top three riskiest business functions are purchasing, business development and finance. These functions are likely prime targets for cyber attackers because the people who work in these functions have access to sensitive financial information, business relationships and transactions.
The legal function ranks fourth in attack risk. That’s not surprising, given that legal teams can negotiate contracts and pricing, and they’re involved in mergers and acquisitions and other transactions.
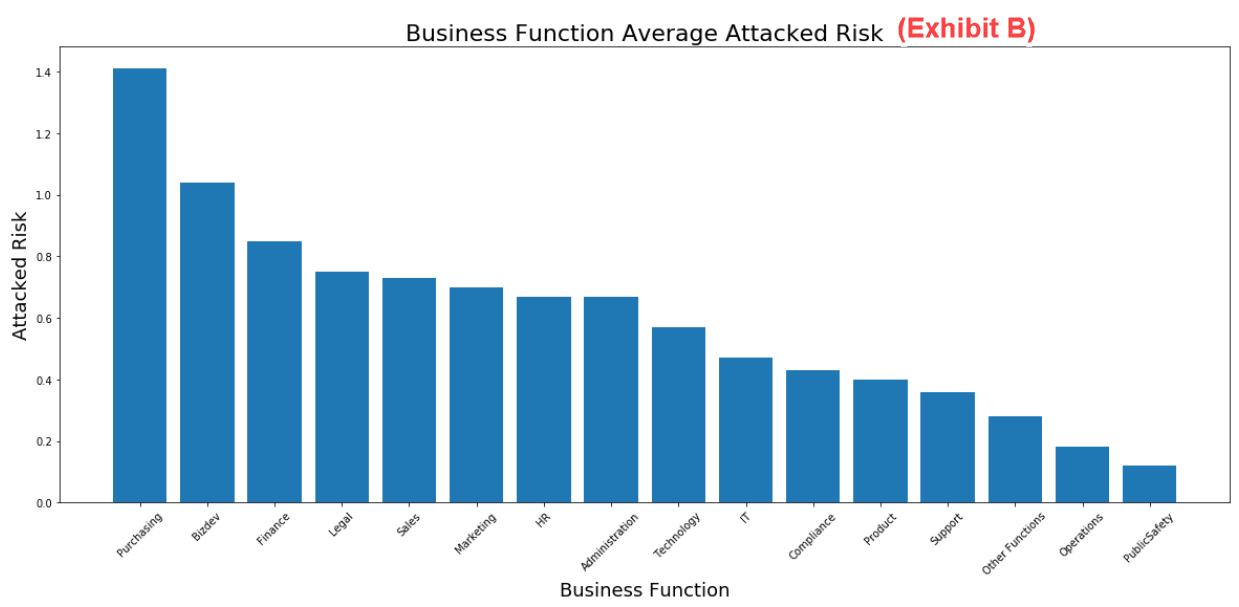
Figure 2. Business function average attack risk data
Sales ranked fifth in attack risk. That high ranking is likely due to several factors: Sales professionals typically promote themselves to their customers, communicate via email frequently and have a strong social media presence, for example. The fast-paced nature of their jobs may also reduce the time they have to be vigilant about risky emails and links—making them more susceptible to compromise.
Inferences and recommended actions
The sales team can be a top target for business email compromise and email account compromise (BEC and EAC) campaigns. Cyber attackers are constantly looking for opportunities to move laterally through organizations by exploiting the trust sellers have with customers. However, all the functions mentioned above that received high rankings for attack risk could be prime targets for BEC and EAC campaigns.
Additionally, threat actors increasingly launch ransomware attacks to exploit the sensitive information held by departments like Purchasing, Business Development, and Finance. By leveraging banking trojan distributors and incorporating malicious links and attachments in emails, they use a backdoor to enter organizations and steal data without getting noticed. This results in extortion and release of data to public sources.
We recommend that security teams look closely at the risk scores for these top five business functions within their organization. Then, they should analyze each function’s top vulnerabilities, including the risky users in those functions, and implement the associated security controls and security awareness training to help users be better prepared to respond to future attacks.
Vulnerability risk data highlights similarities among all roles
Comparing Figure 1 with Figure 3 shows a very small difference in vulnerability between the various roles we examined in our recent risk study.
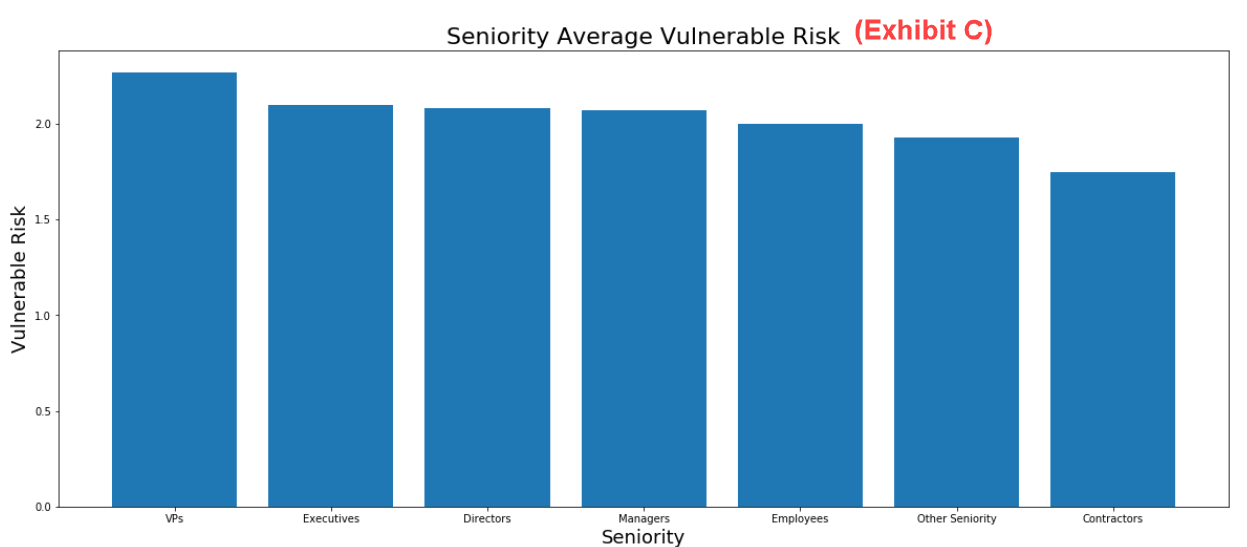
Figure 3. Seniority average vulnerability risk data
Figure 4 also shows that the most vulnerable users are sales team members, followed by marketing and business development staff. The graphs illustrate that all users in an organization, from senior executives to contractors, can be vulnerable to attacks due to their risky behaviors.
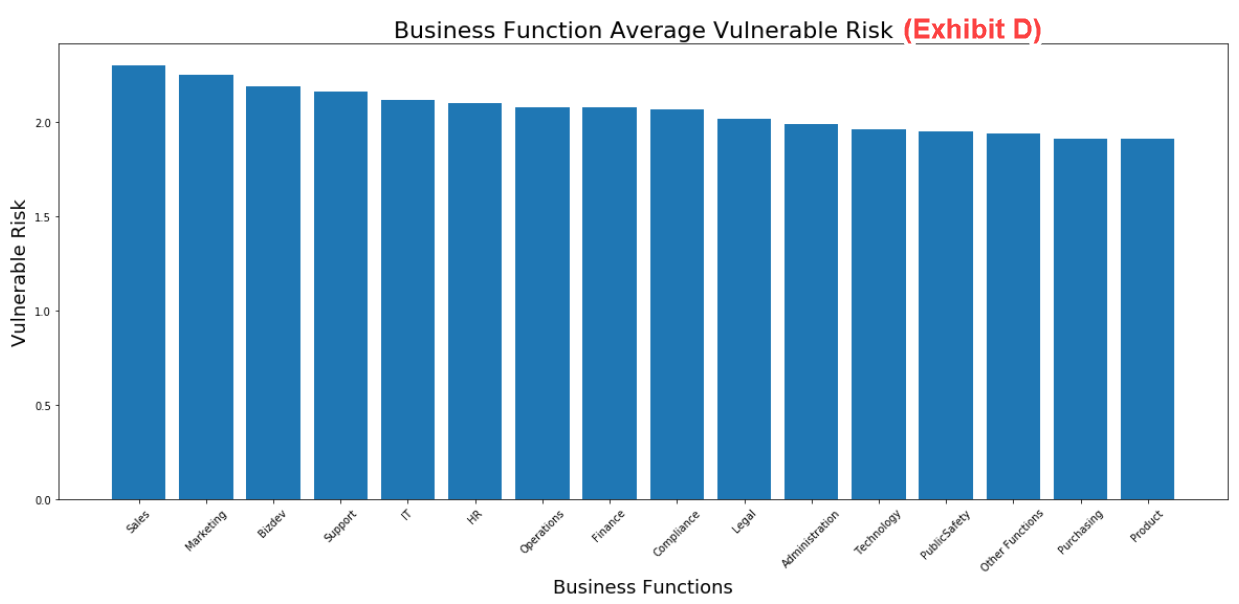
Figure 4. Business function average vulnerability risk data
Inferences and recommended actions
Analyzing who is most attacked is only one part of the risk story—vulnerability is another. Knowing if attacked users are likely to fall for attacks will help predict the likelihood of a breach, and the findings from our recent study imply that no one in an organization is immune to risk.
Without visibility into vulnerability, security teams are pressed to define the best controls to help users adopt less risky behavior. The insights from Nexus People Risk Explorer can help security teams develop more security awareness training by providing teachable moments to reduce behavioral vulnerabilities—for example, users who fall for interesting lures or fail to recognize impostor emails.
We recommend that security teams look at the vulnerability categories affecting their riskiest user subgroups and implement the recommended controls to reduce these vulnerabilities. This process will help ensure that security teams mitigate risk in an informed manner.
Enhanced visibility helps security teams reduce people risk
Proofpoint aggregates data from different products to provide greater risk visibility across several risk variables. We collect Attack Index data from the Targeted Attack Protection (TAP) dashboard, detect potentially compromised cloud accounts through our Cloud App Security Broker (CASB) and Cloud Account Defense (CAD) product, and identify behavioral vulnerabilities through our Security Awareness Training.
These integrations will only grow over time. If you already have a Proofpoint bundle, contact your account manager to turn on your customer data in the dashboard. If you’re unsure whether you have a bundle, ask your account manager how to get one, so you can gain access to the enhanced risk visibility the Proofpoint Nexus People Risk Explorer provides.











