If you’ve read our updated Ransomware Survival Guide, you already know that modern ransomware is rarely delivered directly by email. These days, ransomware gangs prefer to partner with initial access brokers (IABs). IABs operate by distributing malware in high volume campaigns and then selling access to compromised systems. But there are still some edge cases where threat actors try to cut out the middleman and deliver ransomware directly.
A recent example of this is Knight or Knight Lite ransomware (a rebranded version of the Cyclops ransomware-as-a-service). In August 2023, Proofpoint researchers saw several campaigns in which Knight was delivered directly via email. These campaigns were mostly low volume, with fewer than 500 messages, though one campaign contained over 1,000. The campaigns predominantly targeted English-speaking users but we also noted campaigns targeting users in Italy and Germany in those languages.
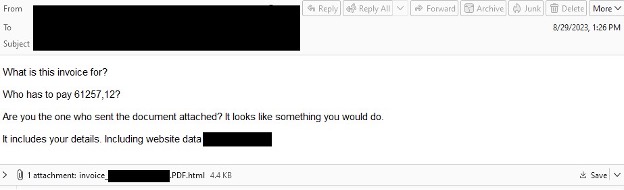
An invoice-themed lure sent in a recent Knight campaign.
Email lures in these campaigns have included bogus messages from a well-known travel website aimed at hospitality organizations, as well as more standard billing lures. Emails contain an HTML attachment that loads a browser-in-the-browser interface spoofing the legitimate site. This interface then prompts the victim to click and download a zipped executable or XLL file containing the ransomware. In some later campaigns targeting Italian users, the attack chain was modified to include an interstitial zip file containing either an LNK linking to a WebDAV share or an XLL, both of which install a downloader. This in turn installs the Knight payload. The downloader used in these later attack chains has not been seen before in our data, and our researchers are investigating. In all attack chains, once installed, Knight ransomware begins lateral movement, scanning for private IP addresses as a precursor to encrypting networked devices.
Files are encrypted with a .knight_l extension, and a ransom note is left demanding sums ranging from $5,000-$15,000 in Bitcoin. The threat actor provides a link to a site containing additional instructions and an email address to notify them when a payment has been made. Currently, there is nothing to indicate that data is being exfiltrated as well as encrypted.
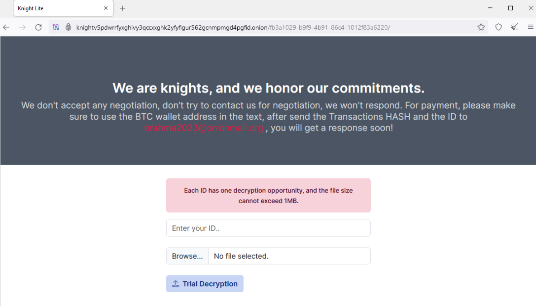
Screenshot of the Knight ransomware Tor webpage.
The threat landscape has changed considerably since the days of high volume Locky ransomware campaigns. In fact, the recent Knight campaigns are the first time since 2021 that Proofpoint researchers have seen email ransomware delivery in consecutive weeks using the same campaign characteristics. But with recent disruption to Qbot—a large scale malware botnet commonly used by many IABs—ransomware attackers may decide to revisit these delivery methods.
For more insight into the developing ransomware landscape, check out the Ransomware Survival Guide and subscribe to our Threat Insight blog.











