Your biggest asset is also your biggest risk. The greatest security challenge organizations face today is people - vendors, contractors, privileged users and business users... the insiders with access to key systems, critical assets and data. It is important security and IT teams leverage user activity monitoring tools to help combat insider threats , bridge compliance gaps, and stop data leakage.
Two solutions commonly leveraged to monitor user activity are Citrix Session Recording and Proofpoint ITM. Citrix Session Recording is a premium feature for Citrix Platinum Edition while Proofpoint ITM is a pure play Insider Threat Monitoring and Prevention solution. Proofpoint ITM’s robust feature set not only provides the ability to capture user sessions, but also empowers security and IT teams to quickly detect concerning behavior, account for all user activity within Citrix XenApp and XenDesktop, and effectively respond.
This post looks at 10 ways Proofpoint ITM goes above and beyond a session recorder.
1.Platform Coverage and Deployment Flexibility
The ITM architecture is built with maximum user density in mind. A standard deployment takes hours, local agents have a minimal footprint of 1% CPU utilization (0% CPU when users are inactive), and consumes 50% less backend storage than a session recorder such as Citrix Session Recorder. Proofpoint ITM agents support all versions of Windows, 30 versions of Unix/Linux, Mac, Citrix, and are deployable in AWS or for AWS machines.
2. Detailed Capture of Every User Action
Instead of basic session recording,
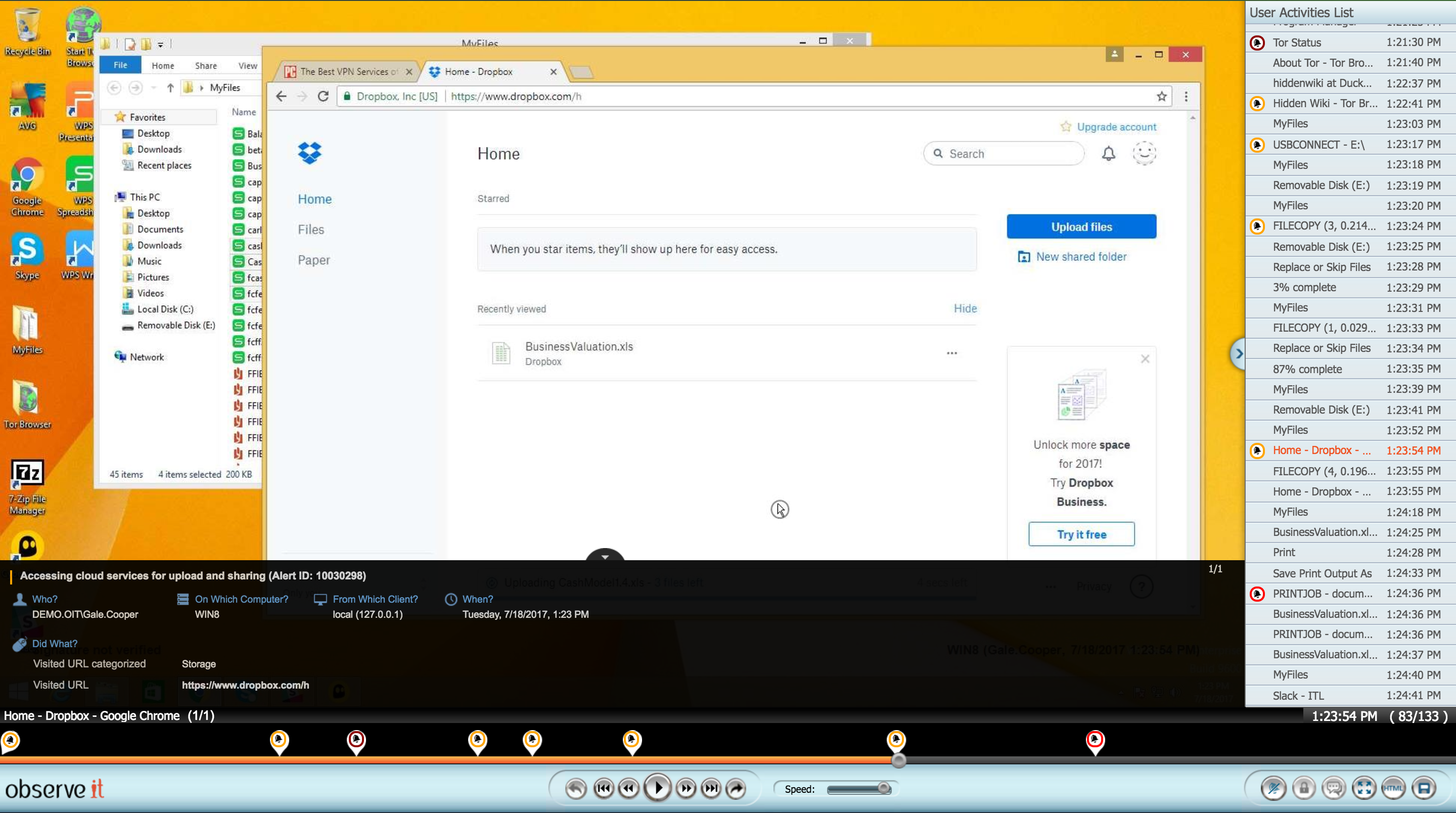
Proofpoint ITM collects detailed logs focused on user activity. All user activity in Windows and Unix/Linux sessions is captured and indexed with video and detailed metadata showing exactly what the user was doing before, during asnd after the incident in question. Proofpoint ITM’s user activity monitoring feature also provides powerful keyword-based searching of all collected data. All of the indexed metadata can be accessed historically and administrators can remotely observe users’ sessions in real-time.
Administrators, security officers and auditors can quickly find specific user actions such as:
- Application & Process Names
- Files and Folders Access
- Titles of Windows Opened
- URLs Accessed via Browsers
- Key Logging
- Commands and Scripts Run
- File Copies, Print-jobs, USB Insertions, and more
Every resulting search is linked directly to the portion of the video where the action occurred making it incredibly easy to find the exact moment a particular action was performed from among thousands of hours of user activity.
3. Advanced Insider Threat Detection
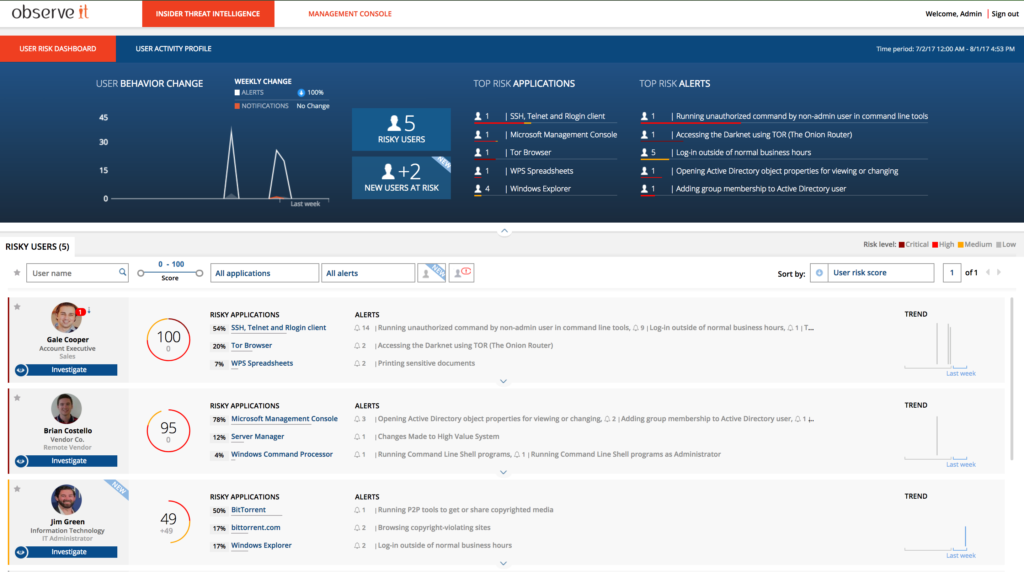
Proofpoint has worked with industry experts to carefully calibrate hundreds of out-of-the-box Insider Threat Rules that provide insight into many insider threat vectors.
These out of the box alerts serve as an early warning system to address scenarios such as:
- Data Exfiltration
- Privilege Escalation
- Unauthorized Access
- Unapproved Application Use
- Configuration Mistakes
- Malicious Actions
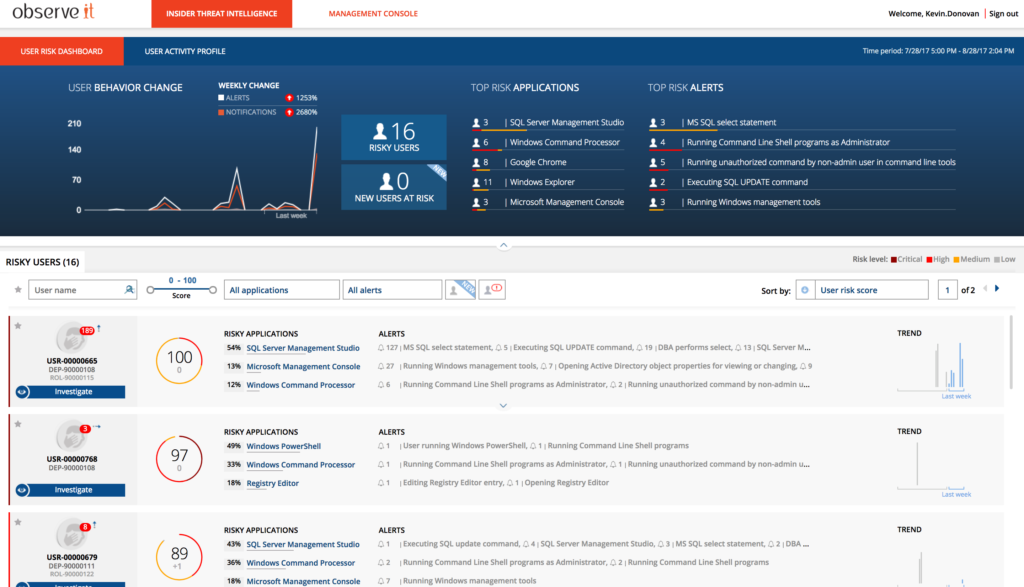
4. User Activity Analytics
Proofpoint ITM captures detailed session activity data and displays information in an activity profile.
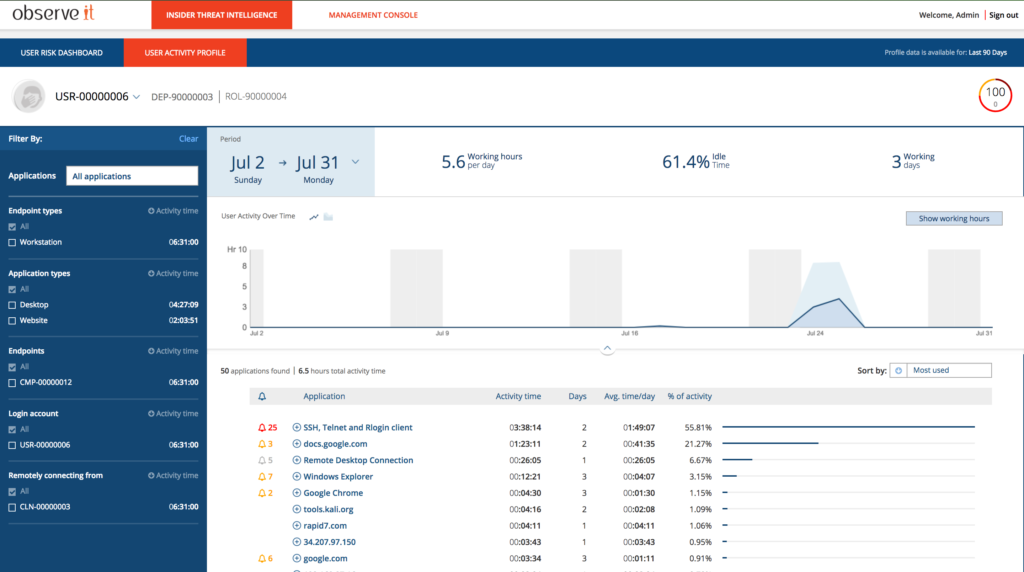
Administrators, IT security officers and auditors can easily view a baseline of activity and rapid access to reporting around:
- Names of Applications Run
- Titles of Windows Opened
- Accounts Used
- System Access
- URLs Accessed
- Alerts Generated
- Timestamps
5. Ability to Identify Users Logging in Via Shared Accounts
Proofpoint ITM includes a “secondary identification” feature that uniquely identifies each specific user, even when using shared accounts such as administrator, root, and generic service accounts. After logging into a server using a shared account, the user is required to enter his personal credentials which are then logged together with the shared account access. This secondary identification feature adds individual user context, bringing user transparency and accountability to all shared-account login sessions using Active Directory exclusively.
6. Flexible Prevention
With Proofpoint ITM you can directly enforce company security policy—automatically and in real time—to promote security awareness and prevent insider threats. Proofpoint ITM enables the ability to warn users against proceeding with actions that violate policy as well as the ability to block actions to reduce non-compliant actions and help stop incidents before they progress.
7. Privacy Controls
Proofpoint ITM can fully anonymize user data to protect employee and 3rd party privacy. This further helps to meet regulations, such as GDPR, follow proper chain of custody, and maintain trust with your users. Additionally, with Proofpoint ITM, you have the ability to control access to any captured sessions with an active directory integration. This allows you to ensure only authorized administrators have access to the information that is being captured and recorded.
8. Leverage More Flexible Recording Policies
Proofpoint ITM gives administrators the ability to create custom server/endpoint recording policies based on specific users or groups of users, as well as specific applications in an include/exclude fashion. Additionally, because of its activity capture capabilities, ITM recording policies can also record portions of sessions containing specific applications, windows and even website URLs. Furthermore, Proofpoint ITM allows selective recording of screen capture and/or metadata, allowing the recording of only activity log data without screen video.
9. Integrate with SIEM and Log Management Systems
Add user session data to SIEM dashboards and reports, including lists of applications run, data visualization showing active users and servers, and detailed lists of specific user actions—all linked directly to session recording. With Proofpoint ITM integrated into your SIEM or log management solutions, draw a clearer picture of exactly what happened before, during, and after an incident.
10. Integrate with Ticketing Systems and Automation Tools
Proofpoint ITM offers native integration with IT ticketing systems, which allows administrators, auditors, and investigators to click a link within any ticket record to immediately access video recordings and textual activity logs of all server sessions related to the ticket. This provides comprehensive logging of all system changes. Additionally, ITM can be configured to require that users logging into sensitive servers provide a valid ticket number (verified by ITM in real-time) before access to the server is granted.
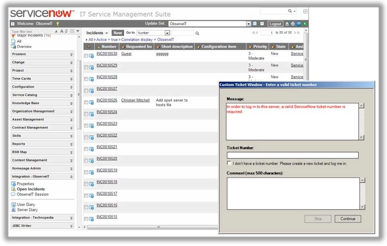
Ticketing System Integration with ServiceNow
1,500+ organizations worldwide leverage Proofpoint ITM to identify and eliminate insider threat and the solution is trusted on millions of endpoints across every major vertical. Proofpoint ITM is certified Citrix Ready for capturing, detecting, and analyzing session activity in Citrix XenApp and XenDesktop environments. This certified integration ensures a reliable, full-featured solution to monitor all XenApp and XenDesktop users.
Go above and beyond simple session recording; leverage Proofpoint ITM to help protect your organization today.
Start monitoring in minutes, try it free.
BTW, can we send you an email?
Once a week or so we send an email featuring our newest blog. Interested?















