What is EDR?
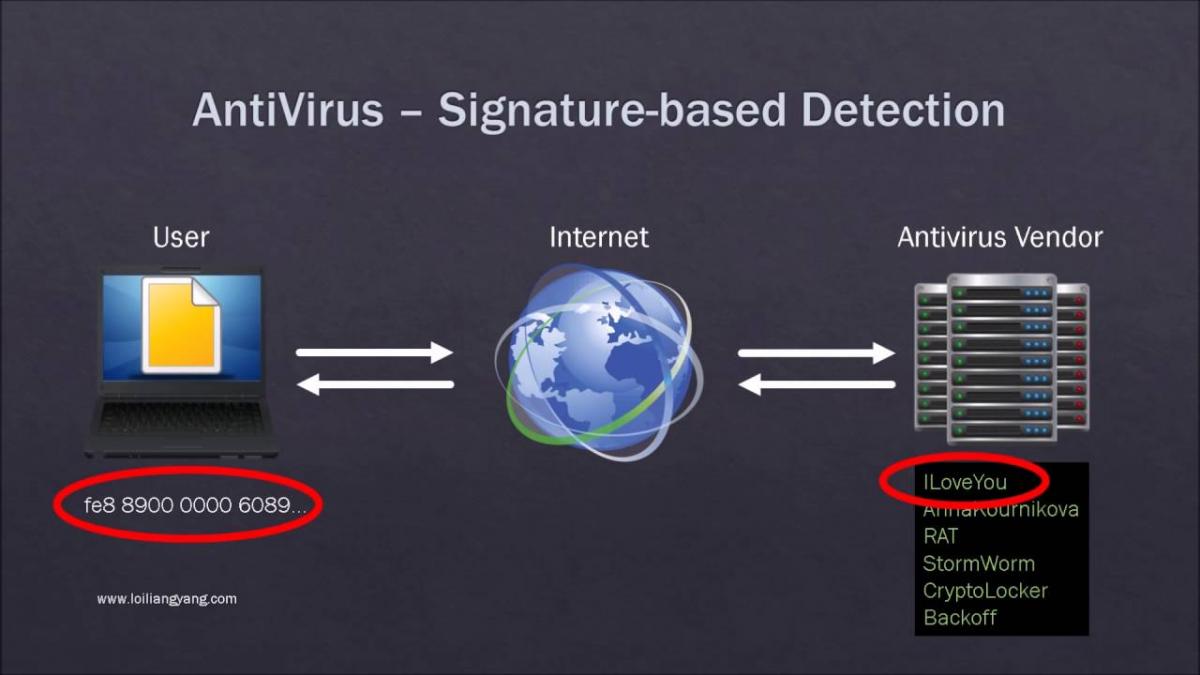
EDR stands for Endpoint Detection & Response. These tools are security solutions designed to help security teams detect malicious activity on endpoints, understand the chain of attack, and enable administrators to respond appropriately. To truly understand the value of EDR you first have to understand how traditional anti-virus searches and identifies threats. Anti-Virus tools tag known computer viruses with a signature that uniquely identifies a specific virus. Then when scanning a system the software will a search a system to find and remove these threats.
The problem with this methodology is that viruses are morph and are created daily. Traditional anti-virus is only as good as its database of signatures, leaving endpoint systems exposed to zero day threats that have not yet been identified. EDR tools that aim to provide toolsets to detect and remediate these emerging threats.
EDR
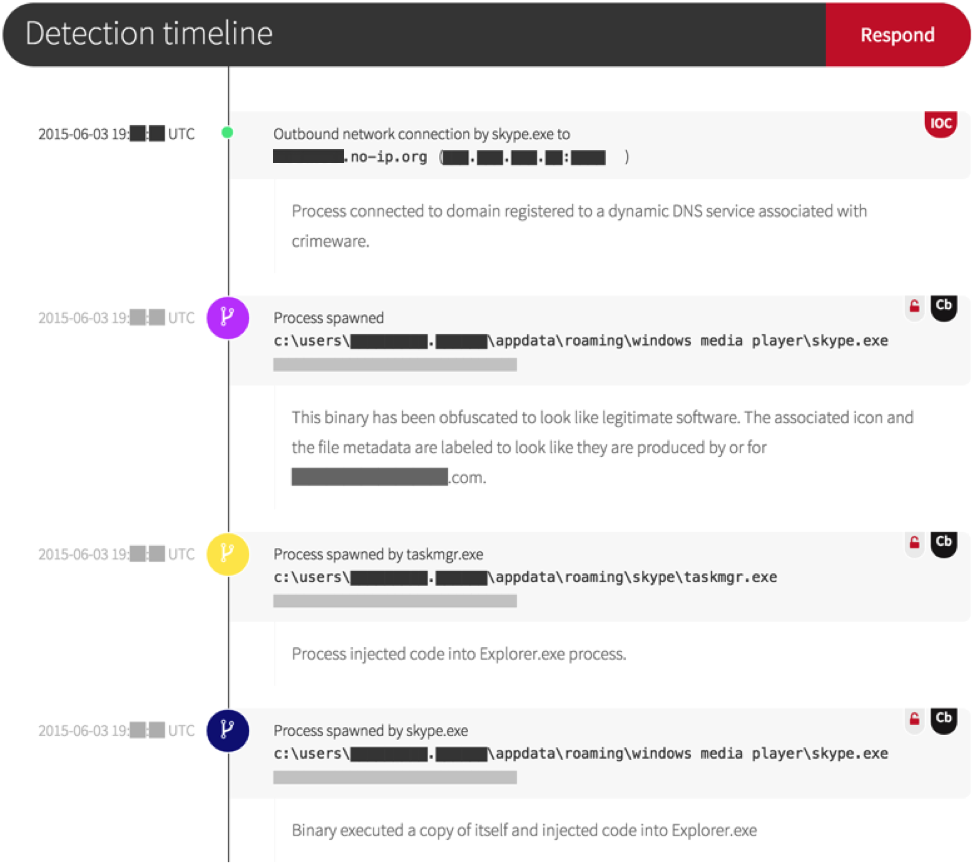
EDR tools continuously monitoring endpoints for technical changes that occur at the system level. Providing admins intel on everything that that computer is doing, so they can formulate a chain of attack and respond.
As seen below, information provided in EDR detection timeline's are focused on system level data to uncover a root kit being installed on an endpoint masked as legitimate software:
Proofpoint
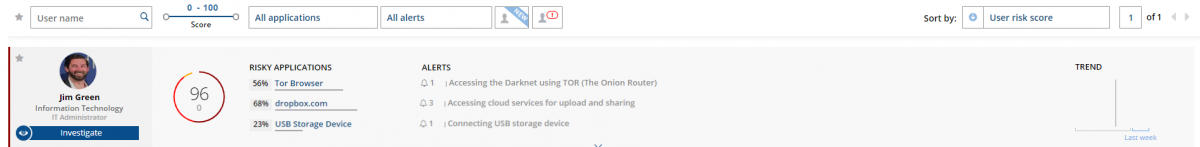
Proofpoint ITM takes a similar approach to detect an insider threat. The software will first identify common insider threat indicators, such as data exfiltration, privilege escalation, and careless behavior on an endpoint:
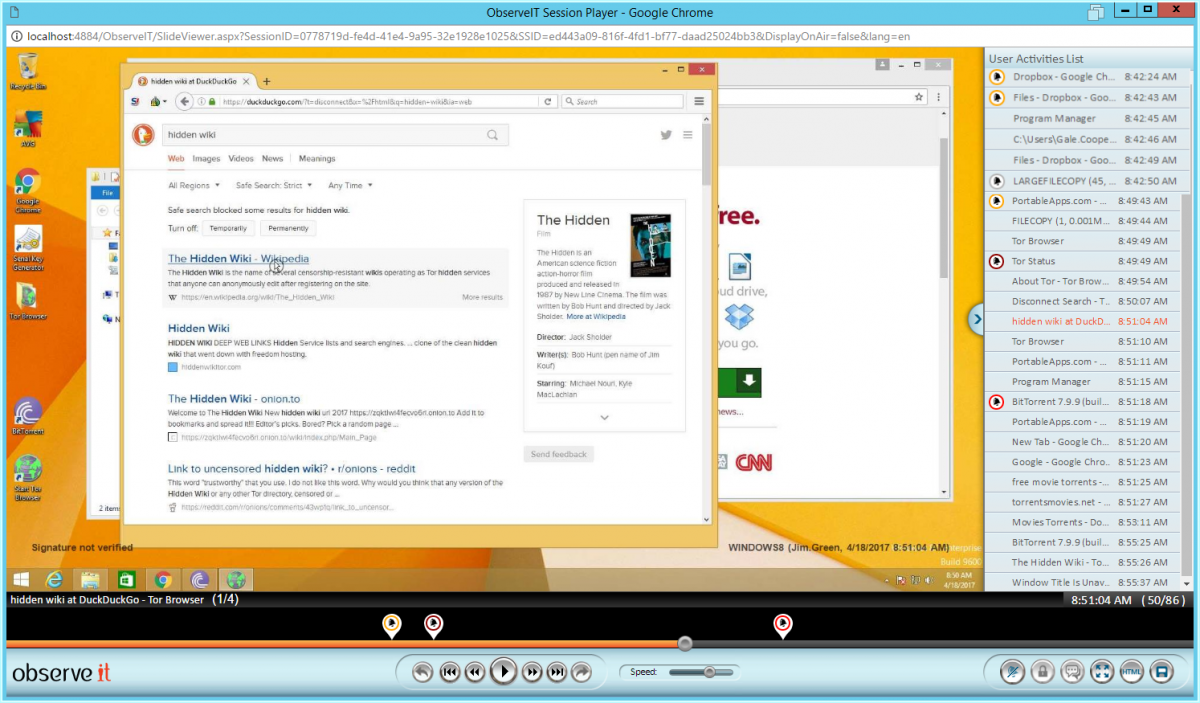
Then provides detailed information of exactly what took place , so that administrators can respond:
In this case, we see a user by passing security controls, connecting a USB drive, copying large amounts of company data to a personal dropbox account, and carelessly browses the deep web on a company laptop)
By analyzing user activity Proofpoint ITM focuses on the root of the insider threat problem, people.