The concept of “cybersecurity” is daunting for many people and often associated with being the sole responsibility of security teams. But attackers don’t respect roles or teams when they strike. They attack people in any department and level with access to sensitive data, often before security teams have time to investigate attacks. So, it’s no surprise that the National Cybersecurity Alliance (NCA) states:
“It is critical for security teams to promote good cyber habits through education and find ways to engage users to instil the belief that they have an active role in helping the organisation stay safe.”
This year’s Cybersecurity Awareness Month Kit from Proofpoint aligns with the NCA’s key themes for 2022 and aims to help you educate your users on diverse types of cyber threats. By equipping your users with tools to identify, resist and report threats, we hope you can build positive cybersecurity habits and a stronger line of defence in your organisation.
Before delving into this year’s themes, it’s critical to explore why security awareness is relevant and necessary.
Why is security awareness important?
Attackers largely target users over infrastructure because it’s easier and faster to trick people than to break into a firewall or hack an account. Inevitably, a threat will pass through the email gateway. And when that happens, users must know how to recognise threats and how to respond to reduce the likelihood of a compromise.
Security awareness training provides examples of real-world threats, educates users on what to do when faced with threats, helps build positive cybersecurity habits, and gauges how users apply what they learn to real-world situations.
To help you better prepare for National Cybersecurity Awareness Month, Proofpoint followed the NCA’s guidance and features the following topics as the themes for this year’s kit:
- Using multifactor authentication (MFA)
- Creating strong passwords
- Updating software
- Recognising and reporting phishing
Using MFA to protect your accounts
Most accounts require multiple ways to authenticate your identity to ensure that only you can access your information and systems. Some common examples of MFA options are additional passwords, a physical key (via a USB device), biometrics (e.g., fingerprint, voice) or a GPS location on your device.
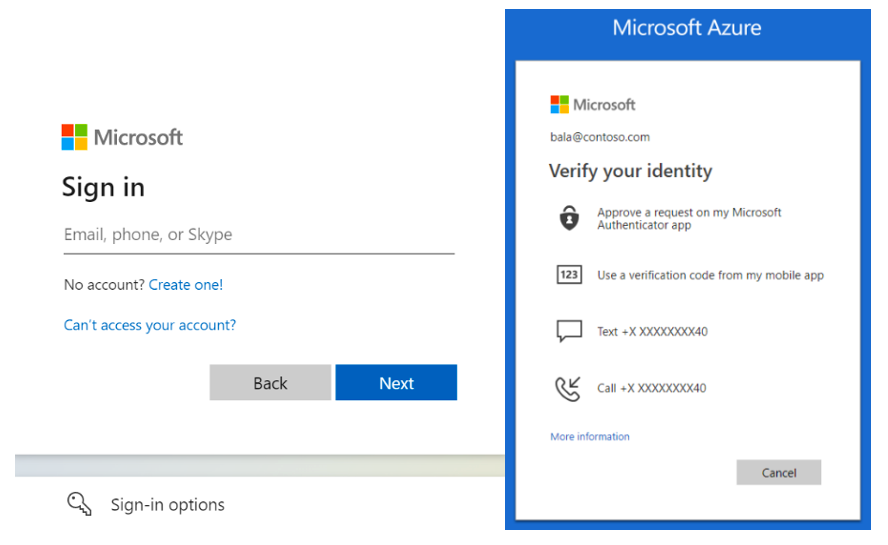
Figure 1. These images are examples of typical MFA options to log into common Microsoft cloud accounts (images courtesy of the Microsoft Azure Directory Authentication Overview site).
Attackers know how useful and common MFA has become and have found ways to bypass it using “MFA fatigue attacks” or “MFA bombing” when they have access to a person’s credentials. In this case, bad actors send several “push” notifications or MFA pop-ups via phone or email. Their hope is that the user will tire of entering their credentials and simply “accept” a fake MFA request to stop receiving further messages.
To keep your accounts safe, watch out for unusual MFA requests on your devices and be wary of receiving multiple MFA requests in a short period. Only approve MFA requests when you’re attempting to log into your accounts and set up alerts on your devices to notify you of suspicious activity.
While it may seem cumbersome to input various codes, biometric scanners or fingerprint IDs, set up MFA on all your accounts and take the extra time to verify what legitimate MFA prompts ask of you. That can help keep your data safe and ensure you’re notified when there’s been an attempt to compromise your account.
Create strong passwords and regularly update software
It can be challenging to remember different passwords for the several accounts we log into daily—and thus, tempting to use the same password across multiple platforms. However, attackers often use open-source websites designed to input a string of randomised characters into any account, with the hope of “guessing” a password correctly.
Weak passwords make it easier for these sites to eventually guess the right combination. Also, if the same password is used in several locations, it increases the likelihood of bad actors compromising multiple accounts once they guess the password. Creating strong passwords with a mix of various characters, symbols and numbers makes it harder for hackers to break in.
The image below shows the difference between a weak password and strong password:
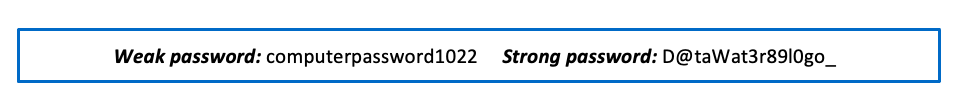
Figure 2. The weak password lacks different character combinations or capital letters throughout and includes a birthdate, which can be easy to guess using open-source websites. The strong password includes a mix of characters and random words.
Educate your users on password best practices with our Free Password Awareness Kit.
Another component of protecting your information is protecting your devices through software updates. Security teams work hard to identify bugs that require patches. Sometimes, these bugs can leave software with vulnerabilities if they’re left unchecked. Even though software updates might cause your computer to slow down during the install or require a restart that takes time away from your task at hand, it’s important to ensure that you use the latest software so you can “lock the door” and keep out attackers attempting to gain entry to your devices and accounts.
Be vigilant for phishes in the workplace and at home
In today’s remote work world, people are distracted by multiple devices and competing priorities, making it easy for attackers to get you to click on a phish while you’re distracted. Being able to spot and know how to report phishes can help your colleagues avoid falling for these tactics and prevent breaches.
Phishing emails take on different forms, are constantly evolving, and make use of social engineering tactics to become appealing to users. For example, earlier this year, several phishing campaigns capitalised on people’s emotions about the Russia-Ukraine conflict by sending fraudulent emails requesting financial assistance and donations.
Fraudulent Fundraising for Ukraine Clothing Website Attempting Financial Gain

Figure 3. The image above shows a fraudulent fundraising email attempting to gain financial payment details by using the emotional incentive of supporting Ukraine through the purchase of clothing.
Having a security awareness training solution that educates users on real-world threats increases the likelihood of users reporting the next phish they receive and doing their part to protect the rest of the organisation.
How to use the Cybersecurity Awareness Month Kit from Proofpoint
User awareness and application is critical to reducing cybersecurity risks. To help your users build positive security behaviours, we have curated a selection of free resources to support your users’ successful use of MFA, creation of strong passwords and timely software updates. We also provide education to help them avoid falling for phishing and other socially engineered lures. We have divided our kit into a four-week programme featuring:
- Week 1 (Launch): Recognise the Value of Security Awareness and Befriend MFA
- Week 2: Use Strong Passwords
- Week 3: Update Your Software
- Week 4: Recognise and Report Phishes
Use the “Start Guide” to craft your weekly campaign messages and help your users see themselves as part of the security team.
Next step: Download the kit
Security awareness affects everyone, not just security teams. Moreover, everyone’s actions either have the power to help protect the organisation at large or can accidentally put the organisation at risk. To stay safe online, it’s important to develop better cybersecurity habits, stay vigilant for the slightest sign of suspicious behaviour and take the appropriate action when faced with threats.
Download and use the Cybersecurity Awareness Month Kit from Proofpoint and visit our Cybersecurity Awareness Hub to learn tips and tricks to help your users become cybersecurity warriors and stay safe online both at work and at home.











