Social media plays an undeniable role in the business world, as it’s the fastest avenue to share content globally with customers and colleagues and solidify company brands.
The pandemic’s “new normal” of remote work has heightened social media’s use in corporate environments, and it only takes a couple of clicks to connect with or send information to someone across the world. Attackers know that people are constantly “connected,” so they exploit personal information shared to infiltrate accounts, steal information and breach organizations.
Just like tending to a garden regularly leads to a successful bloom, tending to your social media accounts, knowing what to post, and employing security awareness training and best security practices are all essential to keeping the social media “bugs” and “weeds” at bay.
Criminals pose as harmless “friends” on social media to build trust
A good way to build a strong customer base or promote company messaging is by growing your “followers” or “connections” on social media—but attackers can use this as an entryway to build trust.
For users looking to connect with customers for speaking engagements or meetings, LinkedIn is one of the best social media platforms. It provides insight into a person’s role in the company and their potential challenges so employees can have a more productive conversation with their customers.
Unfortunately, LinkedIn is heavily used by attackers who also want to learn about a person’s role so they can determine who has higher privilege to sensitive data and thus makes better “bait.”
Attackers, to exploit human nature, always choose realistic scenarios. They also manipulate emotions to trick or threaten their victims to take actions in favor of the attacker.
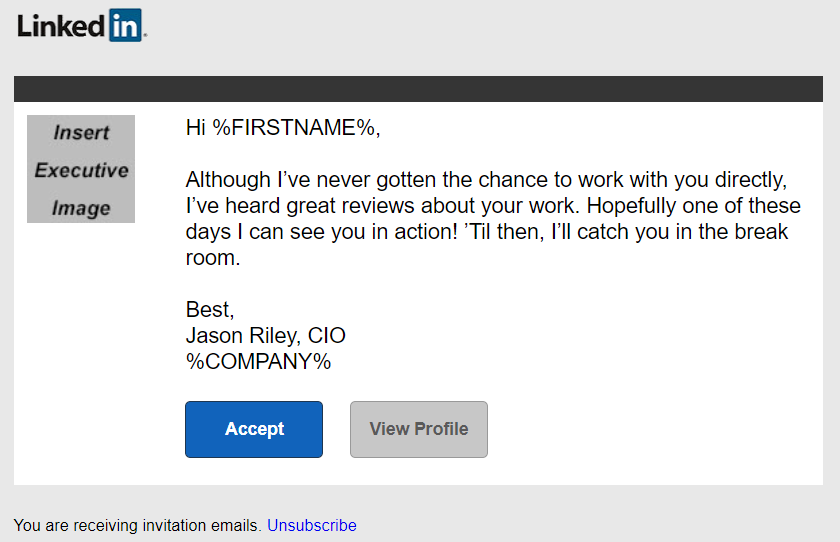
Figure 1. Attackers use realistic social media templates to connect with strangers and learn more about their privilege in organizations.
In the example above, the cyber criminal sent a seemingly personalized message to their target with an invitation to connect. The attacker posing as “Jason Riley” tries to establish a rapport by indicating they work indirectly with the recipient. They even note that they look forward to running into this person in the “break room.” Because large companies can have hundreds of employees at their offices, users can easily believe that the attacker is an employee from a different department, and they will likely accept the request.
Another manipulation tactic the attacker uses in the example above is complimenting the target on the “great reviews” about their work. This strategy makes the recipient feel good—and the attacker appear more likable.
Accepting a stranger’s connection request without checking their profile closely might cause users to accidentally give criminals access to information about the privilege they have in the company, access to other colleague “connections” on their team and details about their experience in their resume or CV. This wealth of data can help cyber criminals identify an ideal victim for their next attack.
Attackers use shared personal information to take over accounts and steal data
It can be tempting to share a lot of information on social media because it’s a powerful communications medium for building genuine and transparent connections. However, cyber criminals are always on the lookout for sensitive data they can use to steal your identity and information.
Many of us spend the greater part of most days at work. And naturally, there are times when we want to share important events with our friends and colleagues on social media platforms while we’re at work. So, it’s critical to know what is appropriate or dangerous to share on your social media accounts so that you don’t accidentally give criminals the key to open the door to stealing accounts and personal information.

Figure 2. People can unknowingly share sensitive information that criminals will use to steal accounts and corporate information.
Take the example above: An employee who just started a new job or transferred teams is taking a selfie including his badge and workstation. Despite the harmless intention of wanting to share a milestone event on his network, this picture exposes critical information that the employee should never share on social media, such as his employee ID (on the badge), his job title, and an open document with what appears to be invoice information.
Attackers will now know this person’s privilege and can use the information from the company invoice to launch future attacks, making fake requests more credible.
It only takes one employee’s unsafe behavior to put the organization at risk. Security teams must educate users on the “do’s” and “don’ts” of what should be shared on social media and what best practices to follow when using social platforms. Remind people to think twice before they post anything that might be used against them or the company.
Equip users with social media best practices to avoid future breaches
Helping to ensure your users know how to share and connect on social media platforms appropriately requires regular nudges. The Proofpoint Social Media Awareness Kit can help. It provides bite-sized content that users can fit into their daily lives to learn best practices and tend to their social media “gardens.” What’s more, this kit extends the skills users learn beyond work and into their personal and family lives so they can protect their individual information.
This two-week program centers on the following themes:
- Week 1: Program launch—defining “safe” versus “risky” social media habits
- Week 2: Expanding education with actionable tips to avoid phishing on social media
Nurturing a garden takes work, as pests are always nearby waiting for an opportunity to take nutrients. In a similar way, social media accounts require maintenance to deflect attackers and flourish. With the Social Media Awareness Kit from Proofpoint, you can prepare your users for World Social Media Day on June 30 and help them make smart choices when sharing content on social platforms so they can keep attackers at bay.











