As COVID-19 vaccinations accelerate and the U.S. coronavirus relief package nears enactment, threat actors continue to use the ongoing crisis to exploit fears. Pandemic-themed attacks remain ever-present, and we’ve never observed such a convergence around a single social engineering lure for such an extended time. These campaigns transcend borders, languages, and industries.
Below are six examples that illustrate how threat actors are actively working to exploit public interest in COVID-19 relief, vaccines, and variant news. Many of these lures spoof trusted brands, including the Centers for Disease Control (CDC), U.S. Internal Revenue Service (IRS), U.S. Department of Health and Human Services (HHS), World Health Organization (WHO), and DHL. Their goal is simple. Convince recipients to click in order to steal personal information, siphon funds, harvest user credentials, or execute malicious payloads for future compromise.
Specifically, we’ve observed the following campaigns:
- Three malware examples: A new Dridex malware attack that leverages IRS branding and promises COVID-19 relief; a COVID-19 vaccine news-themed campaign featuring the HHS brand; a COVID variant-themed message that purports to be from the WHO.
- Two business email compromise (BEC) attacks: Both cite the COVID-19 vaccine as the impetus for urgent requests for W2s, 1099s, W9s, and even gift card purchases.
- Credential Phish: A COVID-19 vaccine phishing campaign targeting pharma organizations that also employs DHL branding.
Dridex Campaign Spoofs IRS Brand, Promises COVID-Relief
Last week one actor attempted to entice both Americans and Canadians with the promise of COVID-19 American Rescue Plan checks. In a campaign consisting of thousands of emails, the threat actor used fake IRS-branded emails to convince recipients to unknowingly download Dridex, a trojan that steals personal banking information and credentials.
Oddly, it didn’t deter the threat actor that the COVID-19 American Rescue Plan hadn’t yet passed, nor are Canadians eligible. The fraudulent COVID-19 American Rescue Plan messages targeted the infosec and technology sectors while employing subject lines ranging from “Joe Biden Rescue Plan Act” to “IRS Rescue Plan Form” and “President's Rescue Plan Act.” Each message featured a sender display purporting to be the IRS American Rescue Plan Dept from email addresses that include <us_irs@federa1.irs.c0m>, <rescue_plan@federa1.irs.c0m>, and <american_rescue@federa1.irs.c0m>.
Below is a sample message featuring spoofed IRS branding and even a “qutoe” [sic] for skipping the vaccine queue.
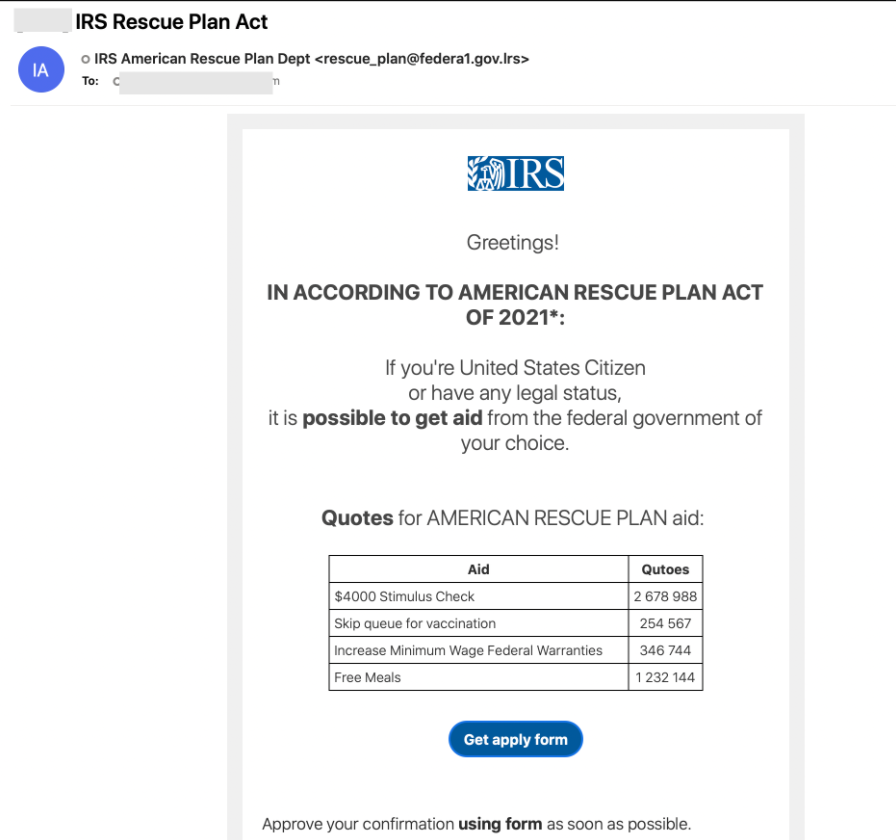
Figure 1: Spoof IRS branded message promising American Rescue Plan aid.
If a recipient clicks on the “get apply form,” an excel file appears with a prompt to “enable content,” which is a malicious macro that leads to Dridex malware.
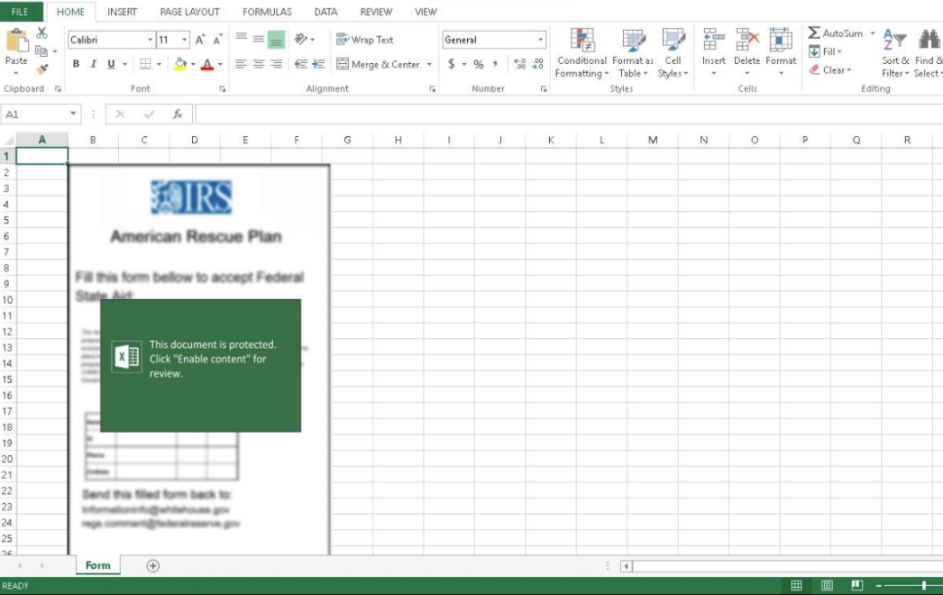
Figure 2: Excel file prompt, which leads to Dridex malware.
COVID-19 Vaccine News Lure Features HHS Fake Branding
Last week we also observed a threat actor attempt to lure recipients in the entertainment/media and telecom sectors with a fake U.S. Department of Health and Human Services message that offers the latest COVID-19 vaccine news. While this campaign was very low volume, if the Java Network Launch Protocol (.jnlp) is activated it installs Amadey downloader, which leads to additional payloads and compromise.
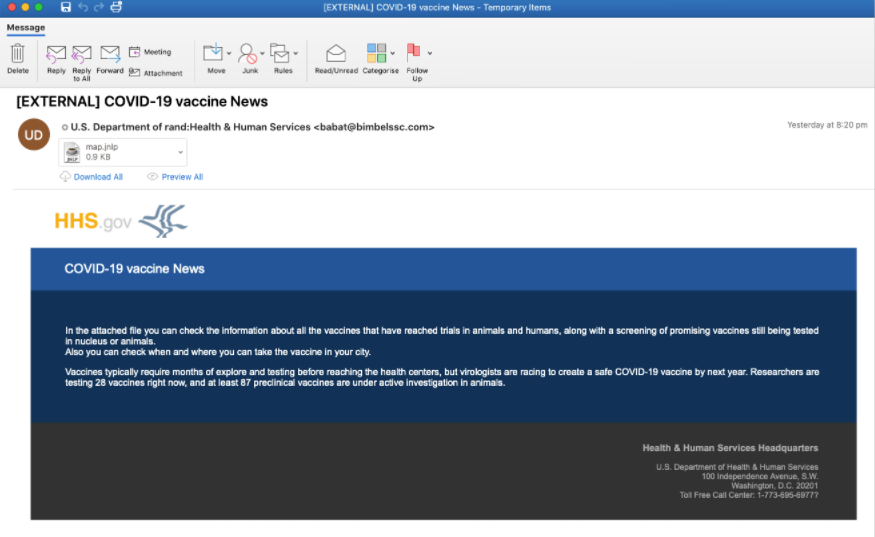
Figure 3: Fake HHS email promising COVID-19 vaccine news.
WHO Brand Spoofing Example Exploits Variant Fears
In late February we also observed a low volume email campaign targeting U.S. aerospace organizations with emails purporting to be from the World Health Organization (<awareness@whocoronavirus.com>) with the subject line “New Deadline Variants of COVID 19.” These emails spoofed the WHO brand and featured a malicious attachment file entitled “deadly variants of covid 19.doc.” That file exploits equation editor to download AsyncRAT, which is a remote access trojan that provides the threat actor with access to a recipient's system.
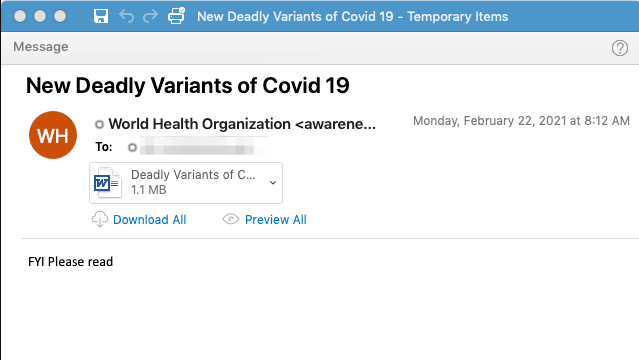
Figure 4: WHO branding spoofed in COVID-19 variant-themed campaign
COVID-19-themed BEC Examples
BEC email fraud and email account compromise is one of the most expensive threats on the landscape, and we anticipate threat actors will continue to employ it in their attacks as the pandemic continues. In the example below, a BEC attacker has sent an “urgent request” to the recipient asking them to purchase $500 gift cards for use at a COVID-19 vaccine conference:
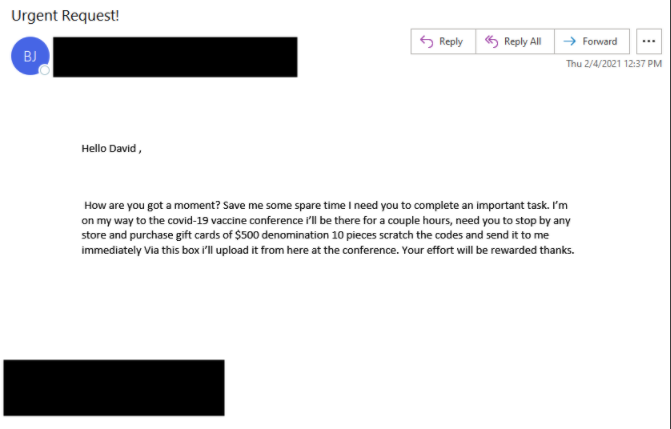
Figure 5: BEC attacker requests $500 gift cards
In the second BEC example below, the threat actor is using a COVID-19 vaccine conference as the reason why they urgently need all W2, W9, and 1099 forms for the entire organization.
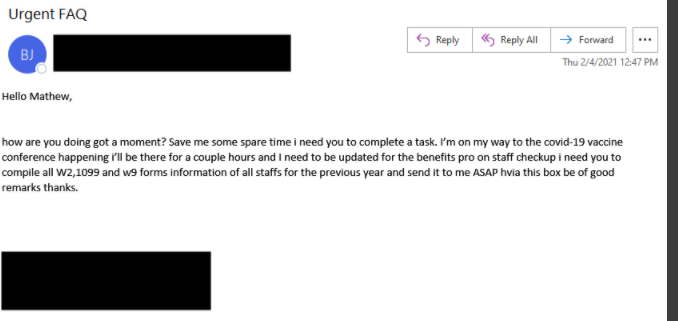
Figure 6: BEC threat actors use COVID-19 vaccine to request W9, W2, and 1099 forms
COVID Vaccine Appointment Lure
In early February we also saw a low-volume campaign that was targeting U.S. organizations in the pharma sector. The emails claimed to be from "DHL Express" with the subject line "Confirm Your Delivery Address: COVID-19 vaccine appointment." These messages contained a URL link to a fake DHL authentication page designed to steal a user's credentials.
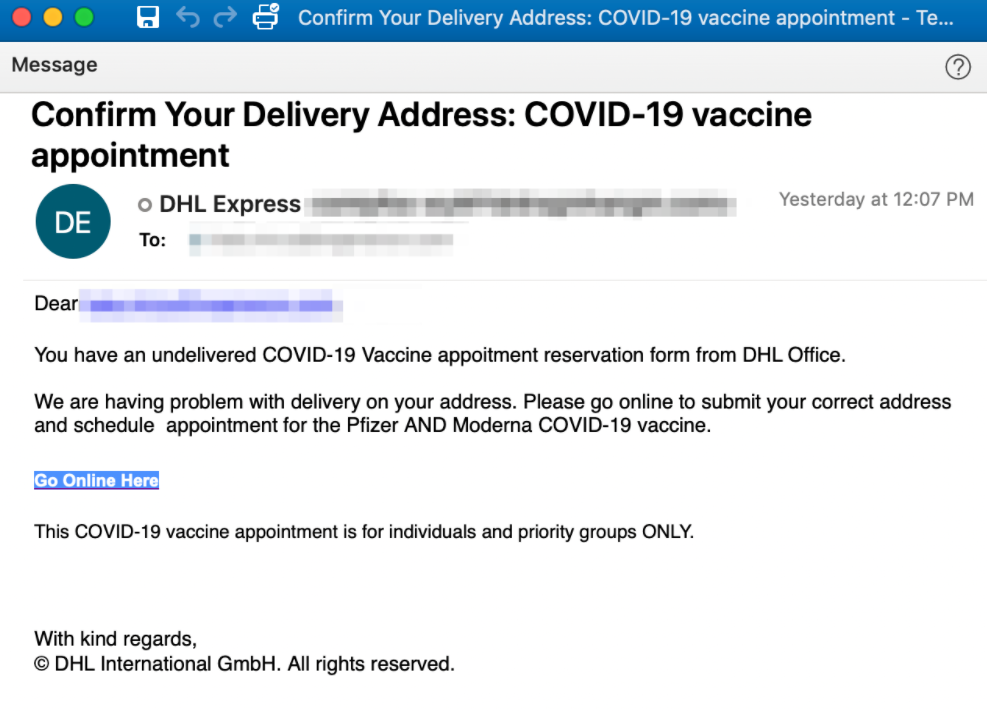
Figure 7: COVID-19 vaccine appointment lure designed to convince recipients to click.

Figure 8: The fake DHL-branded landing page that harvests user credentials.
Threat actors will continue to follow the money, spoof trusted brands, and rely on social engineering to succeed. It’s important to remain wary of any unexpected messages and remember that the IRS will never contact you through email. For additional COVID-19 vaccine lure examples, please see our blog from January 2021, and for tips on how to keep any future IRS stimulus payments secure, please visit https://www.proofpoint.com/us/blog/security-briefs/proofpoint-cso-how-safely-obtain-your-irs-stimulus-payment.











