Proofpoint has observed the use of COVID-19 in broad-scale social engineering attacks leading to malware, credential phishing, and BEC since the beginning of the pandemic. We have observed COVID-19 themes consistent with current events throughout this healthcare crisis. Initially, we saw lures around the virus's existence, which then turned to ancillary lures such as medical supply shortages.
As anticipated, over the last two months, Proofpoint researchers observed more attacks that leverage the COVID-19 vaccine news, such as approvals of the vaccine by world governments, logistics of vaccine deployment, and distribution of the vaccine to frontline responders and other individuals.
In this blog, we provide examples of email-borne attacks spreading malware, phishing, and BEC. These examples exemplify abuse of popular brands such as WHO, DHL, and vaccine manufacturers delivered to users in organizations located in the United States, Canada, Austria, and Germany. The lure themes leveraged a range of topics, including fear that a person had encountered an infected individual; government vaccine approvals and economic recovery fueled by the vaccine; as well as sign up forms to receive the vaccine, information updates, and vaccine shipment delivery.
“COVID Vaccine Anticipation Merger and Acquisition” BEC
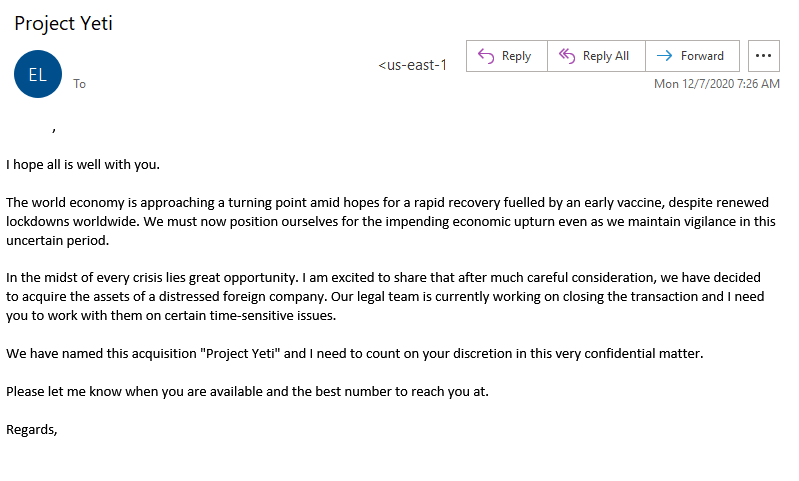
Figure 1: A malicious email purporting to be from an executive and asking the recipient for their cooperation in a confidential acquisition.
From December 1 to December 15, 2020, Proofpoint observed a large BEC campaign (thousands of emails) spoofing executives and attempting to elicit the recipient's support in a bogus merger and/or acquisition. These emails targeted various personnel in roles such as Vice President, General Manager, and Managing Director. The emails were primarily sent to companies in the United States.
These emails projected that COVID-19 vaccines would fuel the world's economic recovery. The email purported to be from an executive asking the recipient for their cooperation in a confidential acquisition of a foreign company. It claimed that this is an opportune moment to make the acquisition as in the "midst of every crisis lies a great opportunity."
Office 365 Phishing
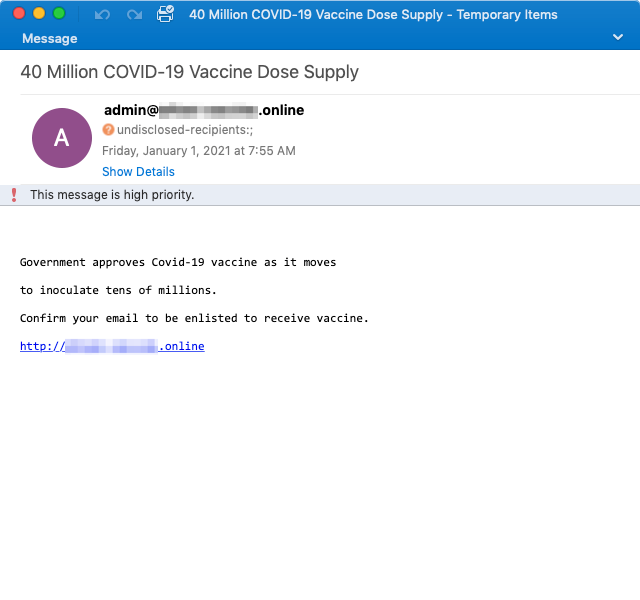
Figure 2: Email screenshot of the malicious email with an Office 365 phishing URL
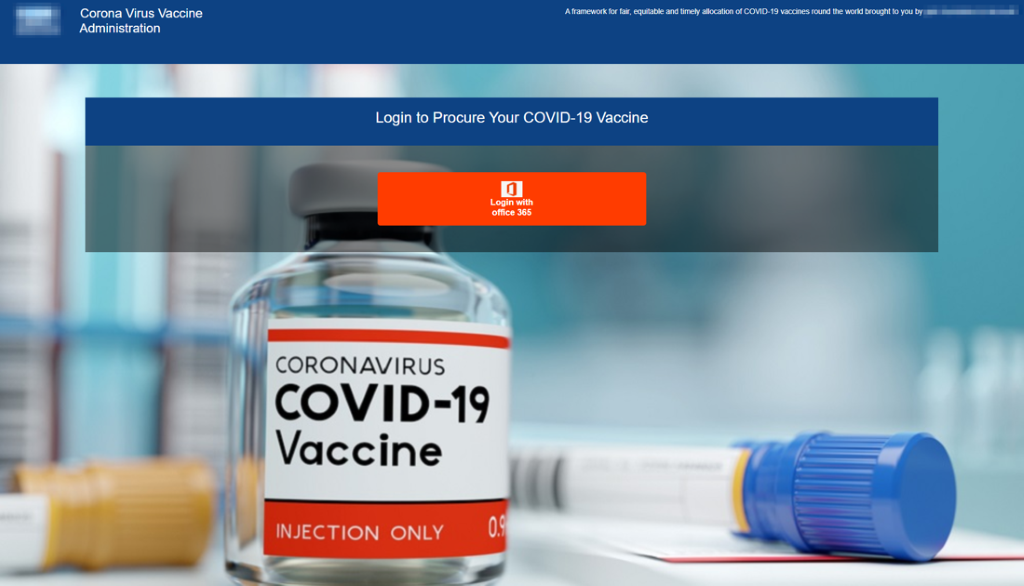
Figure 3: Phishing landing page with a red button asking users to “Login with office 365”
In this medium-sized campaign (hundreds of messages), threat actors began delivering messages on January 1, 2021, over four days, targeting dozens of different industries in United States and Canada. The emails urged the potential victims to click a link to "confirm their email to receive the vaccine". The goal of this phishing campaign was to steal Office 365 login credentials (email and password).
This campaign was notable because it capitalized on the recent government approval of vaccines and the rush to receive it. Specifically, the email talks about "Government approval of the COVID-19 vaccine" and provides a link where one can supposedly register to receive it. At the time of this campaign, the vaccine in the United States was still available to first responders and doctors on the front lines.
The campaign also abused the brands of COVID-19 vaccine manufacturers as the lure in some of the emails. Other emails did not mention specific brands.
Example subjects included:
- [Vaccine manufacturer] COVID_19 Vaccine
- 40 Million COVID-19 Vaccine Dose Supply
- COVID-19 Vaccine
“Complete a task for me, before I leave for a covid-19 vaccine meeting” BEC
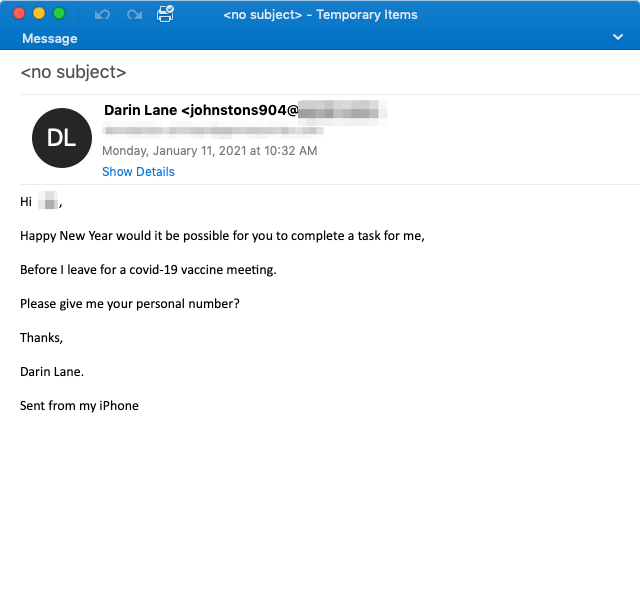
Figure 4: Email screenshot of the malicious email asking the recipient for their personal information
On January 11, Proofpoint researchers observed another small (under 100 emails) BEC email campaign. The emails targeted various industries in the United States.
This campaign is another excellent example of BEC actors picking vaccine lures in an attempt to exploit their targets. This specific email only mentions the COVID-19 vaccine meeting in passing; however, it adds urgency—a common BEC technique—to the follow-up request: "Please give me your personal number?". This attempts to increase the stress by giving the recipient less time to think about their response and allowing the attacker to pivot outside of a protected ecosystem.
AgentTesla Malware

Figure 5: Agent Tesla abuses World Health Organization Brand
On January 12, 2020, Proofpoint observed a medium-sized (several hundred messages) email campaign targeting many industries in the United States. The email contained an attachment, "DOWNLOAD-NEW VACCINES-COVID-19-REPORT-SAFETY1.xlsx.iso" which included an embedded executable file named "DOWNLOAD-NEW VACCINES-COVID-19-REPORT-SAFETY1.xlsx.exe". This executable, if run by the user, drops and runs the AgentTesla keylogger.
This campaign is notable due to the subject, "COVID-19 APPROVED NEW VACCINES", in the email lure and abuse of the World Health Organization logo and name. Additionally, Proofpoint has observed this specific actor spreading RATs, stealers, keyloggers, and downloaders since at least 2019. In March 2020, they used their first COVID-19 email lures, and since then, we have watched them adapt their COVID-19 lures to the current news cycles, to include mentions of the vaccine.
DHL Themed Phishing
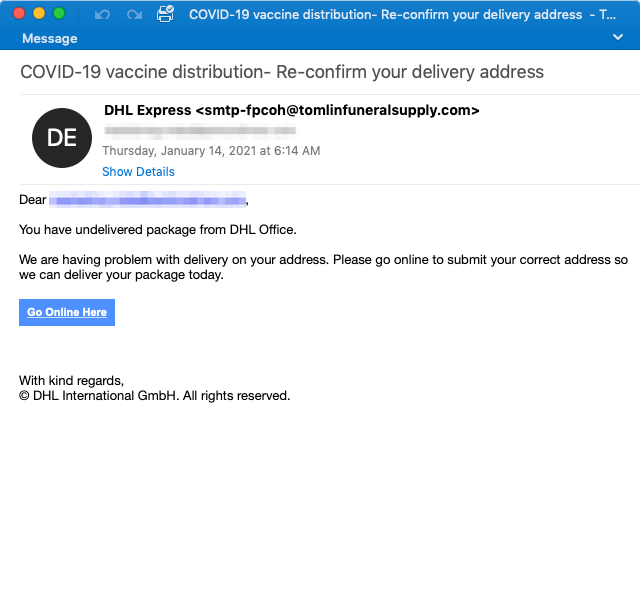
Figure 6: A screenshot of an email purporting to inform the recipient about an undelivered DHL vaccine package

Figure 7: Phishing landing page with DHL branding asking for user’s username or Email address and password
On January 14, 2021, Proofpoint researchers observed a medium-sized (hundreds of messages) campaign targeting dozens of different industries in the United States, Germany, and Austria. The emails urged the potential victims to click a link to "go online to submit your correct address so we can deliver your package today". The goal of this phishing campaign was to steal email login credentials (email address and password).
While the email body content is typical for a package delivery service phish, the notable difference was in one of the subject variants. The subject "COVID-19 vaccine distribution- Re-confirm your delivery address" implied to the recipient that the specific package is supposedly a COVID-19 vaccine.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
bf78ad88ad9124adde7b3fdfb867b5e848d042ae56acbb75bcfd71962c6a5fd8 |
SHA256 |
DOWNLOAD-NEW VACCINES-COVID-19-REPORT-SAFETY1.xlsx.iso |
|
2a0b7eba6ec8d395dcc4485e2369c2ec289819c378e0f1f81a87a7622e0da17c |
SHA256 |
DOWNLOAD-NEW VACCINES-COVID-19-REPORT-SAFETY1.xlsx.exe |
|
hxxp[:]//putrajayagemilang[.]com/covid_19_vaccine_delivery/dh?lo=[base64 of recipient email] |
URL |
January 14, 2021 DHL themed phishing link |











