BEC Taxonomy: A Proofpoint Framework
Business Email Compromise (BEC), a type of email fraud, is one of the most financially damaging threats to businesses of all sizes and across industries, overshadowing most other types of cybercrime in terms of monetary loss. In 2020 alone, BEC schemes cost companies and individuals about $1.8 billion and comprised 44% of total monetary loss, according to the FBI and Internet Crime Complaint Center’s (IC3) annual cybercrime report. This represents a $100 million increase from 2019.
Unfortunately, as BEC schemes have evolved, the terms utilized by cybersecurity professionals to explain its tactics and techniques have become ambiguous, conflated with other terminology, and overall misused. Such ambiguous phraseology confuses and ultimately hampers a cybersecurity professional’s ability to do world-class research and a company’s ability to conceptualize the problem.
In this blog post, and a series of follow-on posts, Proofpoint researchers will introduce our email fraud taxonomy, which encapsulates BEC and provides a framework with how to approach this ever-costly threat.
The BEC Taxonomy Dilemma
BEC is often used to describe an entire subclassification of email threats in a sweeping, generalized fashion. What people often mean when they use BEC is that one or more tactics and techniques associated with financially motivated, response-based, socially engineered, email deception have been observed in an attack. That is a mouthful and has led to BEC being too inclusive to be useful in terms of research and customer prioritization of threat risks and exposure.
The Proofpoint Solution
To simplify and specify the important aspects of BEC, and email fraud writ large, Proofpoint researchers have created the following Email Fraud Taxonomy. The purpose is to help make it manageable for companies and researchers to label and understand the specific email fraud facing them.
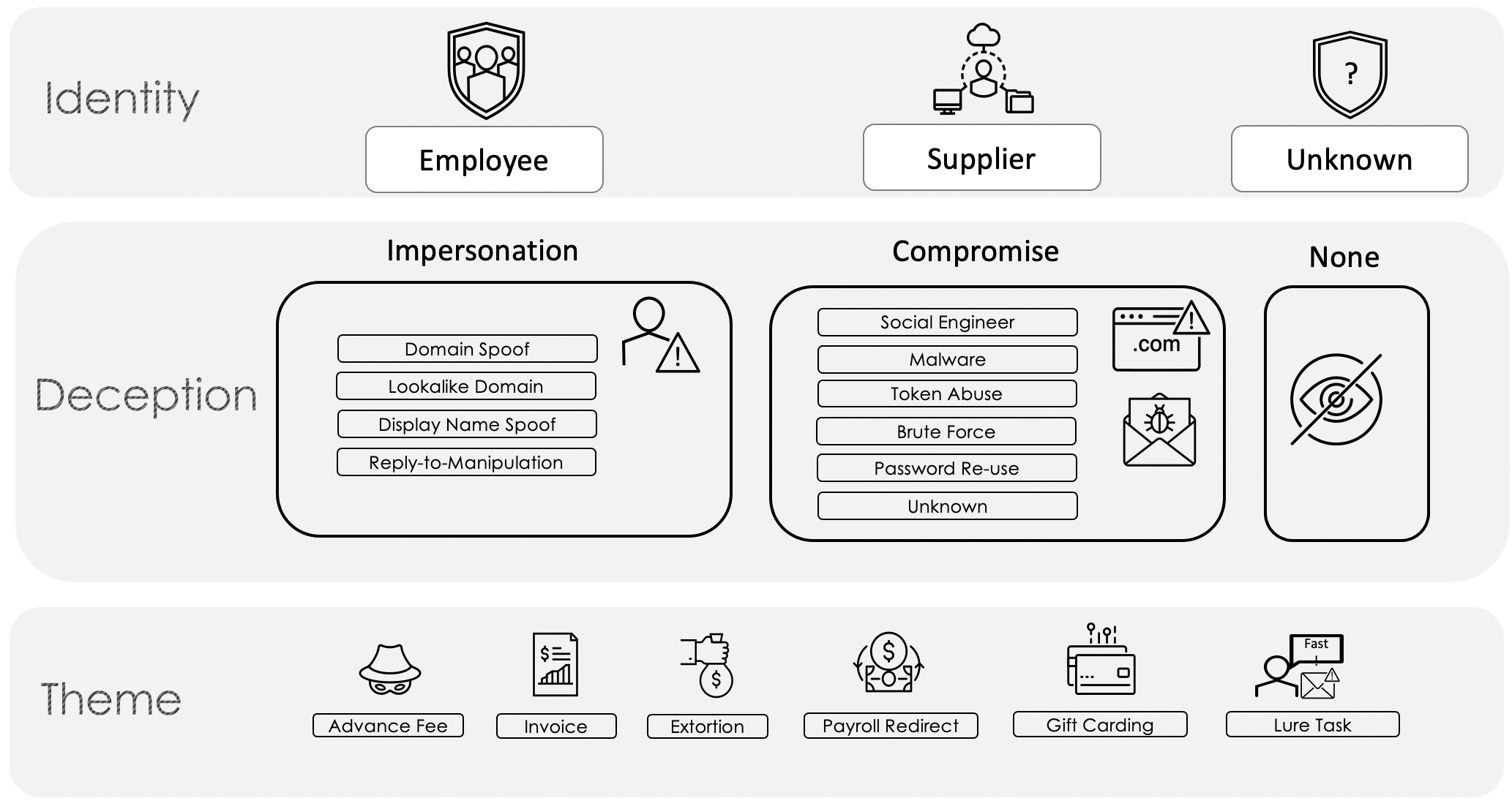
Figure 1: BEC Taxonomy
Identity
Proofpoint takes a people-centric approach to email fraud, which is why our taxonomy map begins at the top with Identity. In this tier, Identity is synonymous with who the threat actor is pretending to be. Consumers of this map can adjust this level to make it more granular to suit their needs, such as expanding Employee into two categories, Executives and General Employees.
Deception
The following tier, Deception, is a bucketed grouping of techniques utilized by email fraud threat actors. Divided into Impersonation, Compromise, and None, Proofpoint defines the first two as an attack in which the threat actor manipulates one or more message headers to mask the origin of the message, and an attack in which a threat actor gains access to a legitimate mailbox, respectively. The None category is for instances when other tactics are utilized such as those that require no impersonation and/or fraudulent emails are sent from free email providers with no spoofing.
Theme
The final tier, Theme, is by far the most important part of this taxonomy because the most relatable and actionable information is typically derived from this tier. The themes included have been constructed to represent categories that are relevant to the BEC threat landscape and resonate with most businesses. By design, they are generic enough to account for nuance, yet specific enough for rapid manual identification purposes.
Keep Reading…
It is in our next BEC blog post that we will begin to define and scope each of the categories in the Theme tier and show the Email Fraud Taxonomy in action.











