The days of deploying the same controls for all employees are over. The threat profile for each employee, department, team, job role and access to controls is entirely different. In part 1 of this blog series, we covered the evolving threat landscape and how today’s top cybersecurity risks are people-centric. This post will discuss how to choose the proper solutions for protecting your employees and why it’s so important.
How Do You Protect Your Employees?
Criminals have different motivations for targeting different people in your organisation, so it’s important to understand who your Very Attacked People™ (VAPs) are. Who is vulnerable? Who is likely to be attacked? Who has privileged access?
When you understand who does what in your organisation, and why they might be on attackers’ radar, you can implement defences that work against the threats that target specific job roles.
Let’s look at three examples:

Figure 1. People are complex and different.

Figure 2. Protect your employees, how and where they need it.
Hear more about these examples in this short extract from our webinar:
Webinar Video: The Right Protection for the Right People
Stop malware from reaching your people and increase operational efficiency
Security controls often focus on endpoint detection and response by remediating attacks that have already broken through defences. The early phase in the attack chain is often neglected, but it’s so important to prevent attacks before they cause damage.
Increase your defences in the initial stages of the attack chain by protecting your number one threat vector—email security. If you block more threats upfront and have fewer emails reaching users’ inboxes, there will be fewer phishing reports for your IT teams to review. Also, because your organisation will spend less time addressing attacks that have slipped past defence, you can improve your operational efficiency.
Consider PerkinElmer, Inc., which was able to block 99% of threats from getting through. Now, it’s teams can work more efficiently because they’re spending far less time assessing a flood of cyber threats. Jim Forsyth, PerkinElmer’s senior network engineer, global IT infrastructure, said:
“Financial hacking groups targeted us, putting personal credentials at risk. Ransomware threats are real. Our spam and antivirus solutions weren’t adequate anymore… Proofpoint TAP (Targeted Attack protection) helped tremendously… It reduced malicious emails, attachments, and URLs getting through by 99%.”
You can read the full PerkinElmer customer story here.
Protecting your number one threat vector with a platform approach
Setting up effective defences to deflect threats early in the attack chain reduces your risk profile. Your people can’t click malicious links or download malicious files if those threats never reach their inbox. A targeted, platform approach to email security can help in protecting your employees. It includes:
- Implementing controls to block threats from entering your organisation by email. Checking the authenticity of emails helps to block impersonation attempts.
- Increasing user resilience by educating your people. If an email does get through, are your people trained to make sure the email is legitimate? Do they know to triple check that the attachment or link isn’t malicious before they click or open it?
- Using post-delivery remediation, so if the user does click a malicious link, these unknown URLs can be isolated at the time of the click, preventing malware from entering your organisation.
- Building automation into the workflow to improve operational efficiency. If a user reports a malicious email, that email can be pulled out automatically from everyone’s inbox.
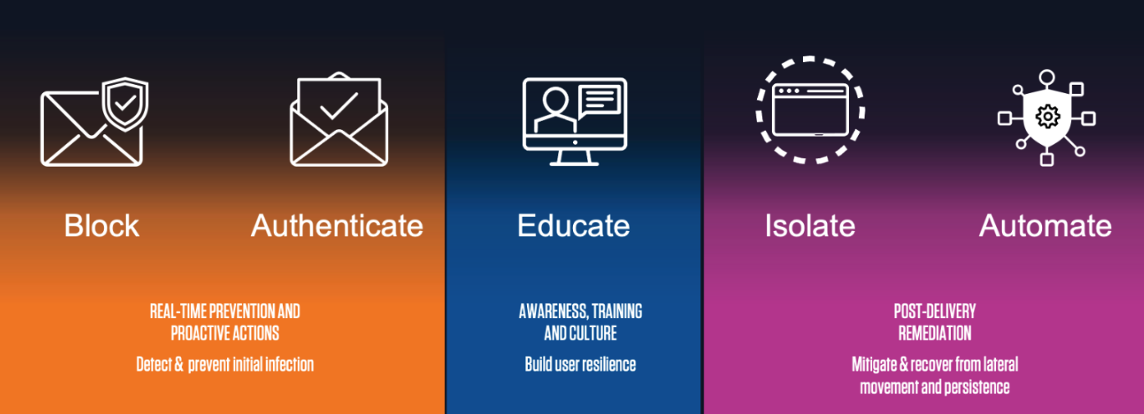
Figure 3. The platform approach to protecting your people.
Learn more
Get a comprehensive view of your risk posture across your email infrastructure with a free email rapid risk assessment from Proofpoint.
And learn more about how to protect your number one threat vector and identify your organisation’s VAPs in our webinar, “Protecting People: The New Perimeter”.











