As regular readers of this blog know, the cybersecurity landscape is constantly evolving.
And while the rise in adoption of cloud-based applications is encouraging us to rethink security solutions, one concerning fact remains: email-based credential harvesting remains one of the most fruitful tactics for today’s threat actors.
The data points featured below reveal that impostor email attacks are more prevalent—and effective—than ever.
To help organizations like yours create an effective and adaptive cybersecurity strategy, I’m teaming with Marc Rogers, Executive Director, Cybersecurity at Okta to host a webinar tomorrow, October 24th at 10am PST, “Prevention and Response Strategies for Phishing Attacks.” Hope to see you there.
Impostor email continues to soar, despite increased security investment.
Last year, nearly half (48%) of all organizations had more than five unique identities spoofed and more than five unique people targeted by impostor email attacks.
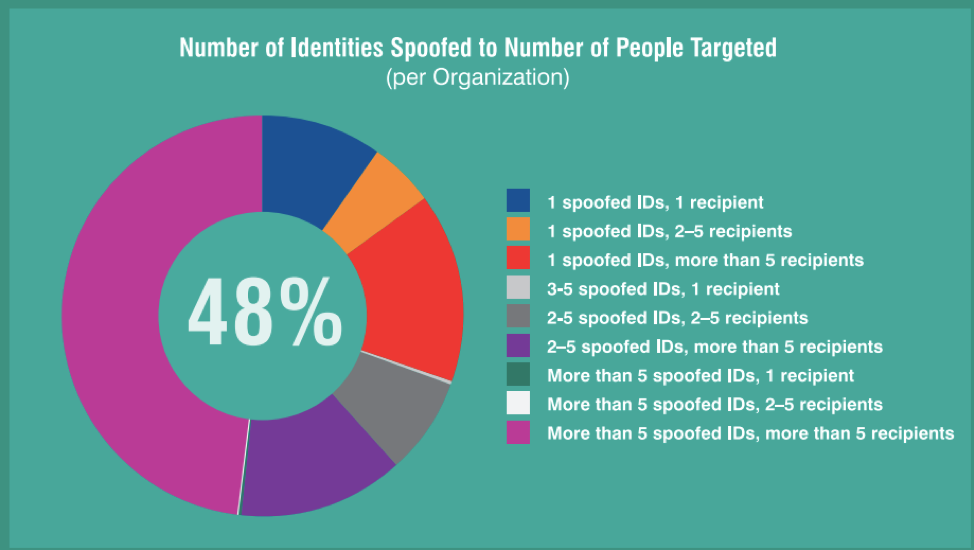
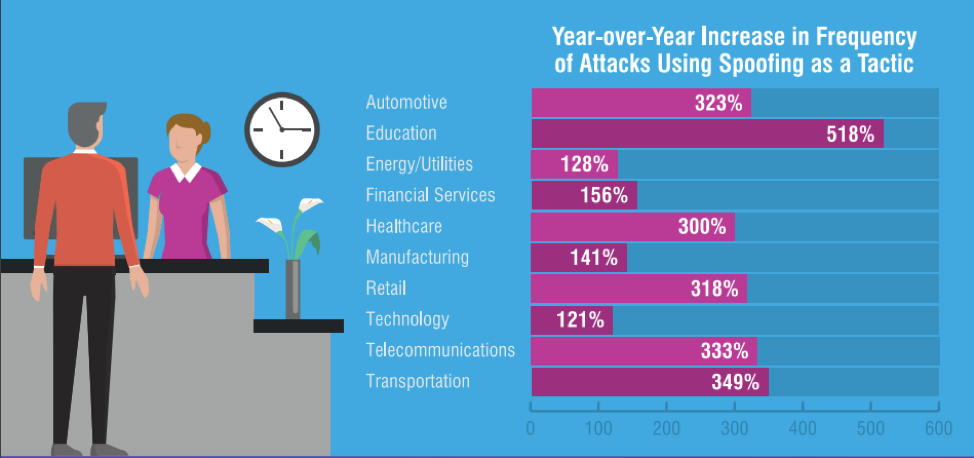
Impostor email attacks affect companies of all sizes, in all industries
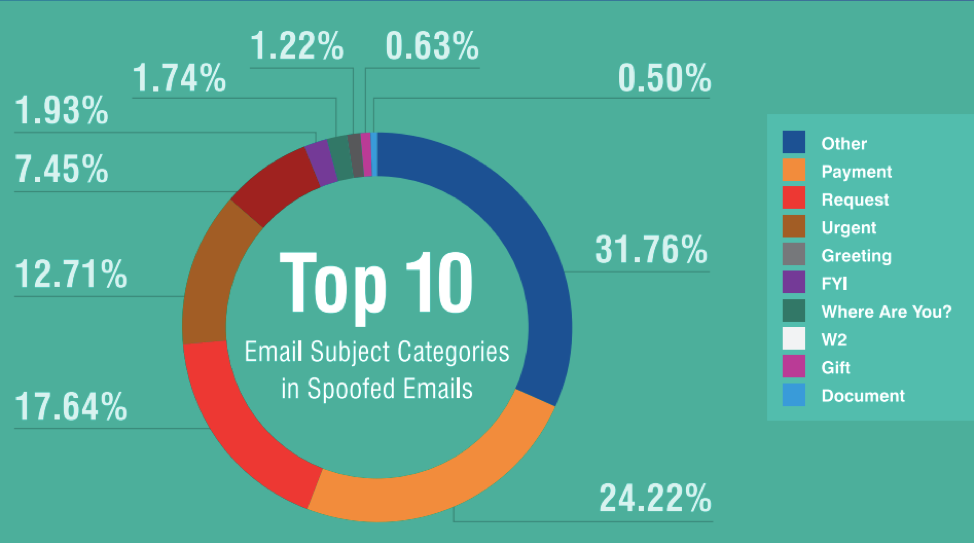
Top email subject categories in spoofed email
I hope you’ll join us to hear more about the anatomy of impostor email scams and how to fight back tomorrow. Register for the webinar here.











