Detection and Prevention
 Data Security
Data Security
Early warning signs of insider risks and endpoint data loss
Tell tale signs of endpoint data loss by accident or suspicious activity by insiders are not similar to that of your usual hacker or malware in your system
Stop data loss with Endpoint DLP and ITM platform
Detect accidental and malicious file download, upload, deletion, cut, copy, paste, rename and printed across
- Web
- USB
- Local cloud sync
- Print jobs
- Email attachment
- Raw text in an application
Prevent risky data interaction on common endpoint channels based on source URL, data classification label, file extensions, user groups, USB devices, cloud storage vendors and many more.
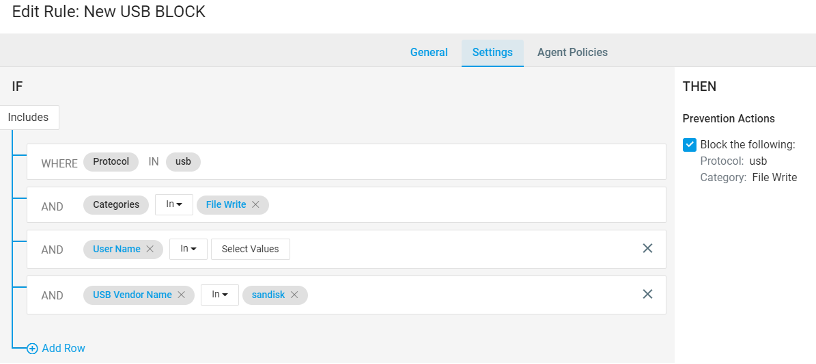
Detect suspicious activity by insiders with ITM
Identify privilege abuse, security controls bypass, unauthorized access, application misuse, illegal activity, fraud, IT sabotage, and other out-of-policy behaviors with an easy to use insider threat rules engine
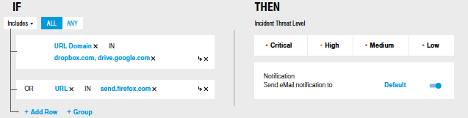
Risky behaviour threat hunting
Leverage the powerful search and filter engine to proactively identify risks based on customized data explorations. Build your own exploration for your organization or use preset explorations based on the wisdom of our customers
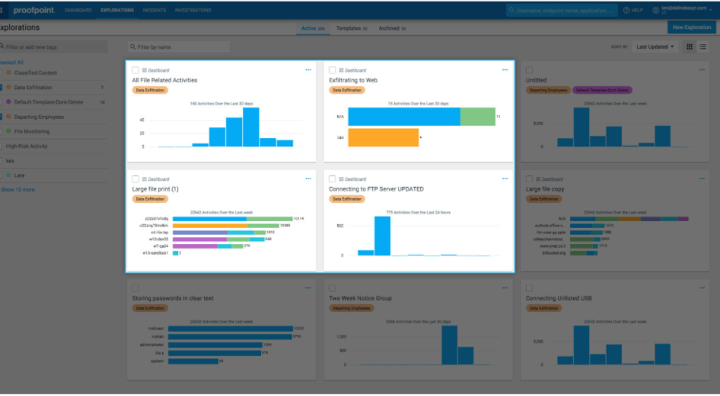
Lightweight endpoint architecture
Endpoint agents collect the telemetry and conduct the prevention actions. Running primarily in user mode with our patented file driver helps ITM achieve industry-leading lightweight architecture. Customers often run us in parallel with other endpoint security products without the traditional headaches of end user complaints nor performance degradation.











