In this blog series we cover how to improve your company’s security posture with actionable insights. In our previous blogs, we covered people risk, origin risk, business email compromise (BEC) risk, risk efficacy and TOAD attack risk. We also discussed how threat metrics need proper context so you can gain a deeper understanding of threats to your business.
In this post, we’re going take a closer look at the new TAP Threat Intelligence Summary—which is available to all Proofpoint Targeted Attack Protection (TAP) customers who use the Proofpoint Aegis threat protection platform. We’ll explain why it is an invaluable resource for providing actionable insights and explore some of its key reports.
Overview of the Threat Intelligence Summary
The Proofpoint TAP Threat Insight Dashboard provides you with a diverse set of tools in an intuitive interface to help you seamlessly manage and monitor security events and alerts. Plus, robust search and filtering capabilities ensure you can quickly identify and analyze threats.
The new Threat Intelligence Summary keeps security teams up to date about the evolving email threat landscape with accessible, actionable global threat intelligence. They can use these insights to take a proactive approach to identifying and addressing risks.
Now, let’s take a closer look at some of its key reports.
Global Threat Insights
The Proofpoint Premium Threat Intelligence Service (PTIS) highlights critical developments in the email threat landscape. This includes zero-day exploits, high-profile malware, vulnerabilities and campaigns.
When you click on the Related Campaigns link in the report, you can see if your business has been targeted by a specific actor or activity. You can also see whether any malicious email messages were delivered or require follow-up. Click on the attribute tags, and you can view a list of the campaigns and threats that are related through actor attribution, technique or other shared characteristics.
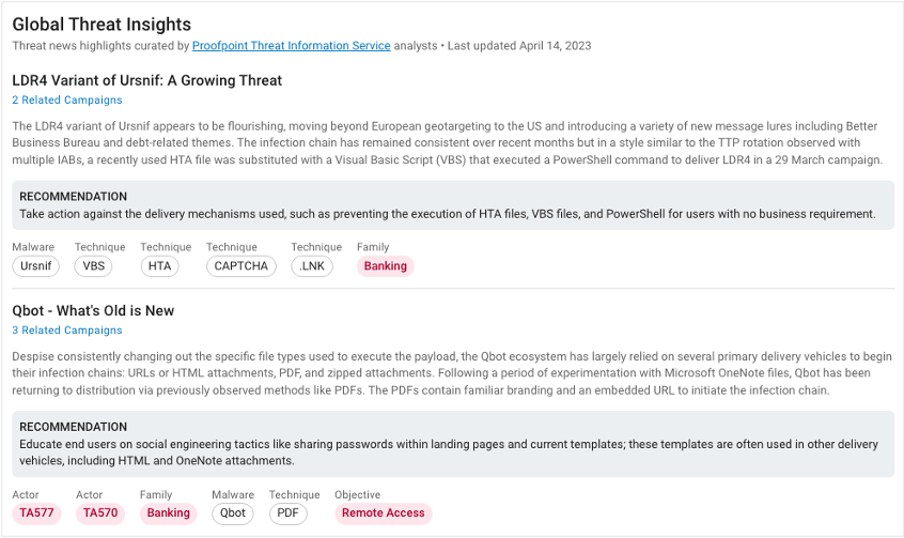
Global Threat Insights in the TAP Threat Intelligence Summary.
Top Global Campaigns
Updated daily, this report provides information on the most prominent campaigns observed by Proofpoint customers worldwide. Monitoring these trends gives you early warning signs of emerging threats so you can take proactive measures to safeguard your business.
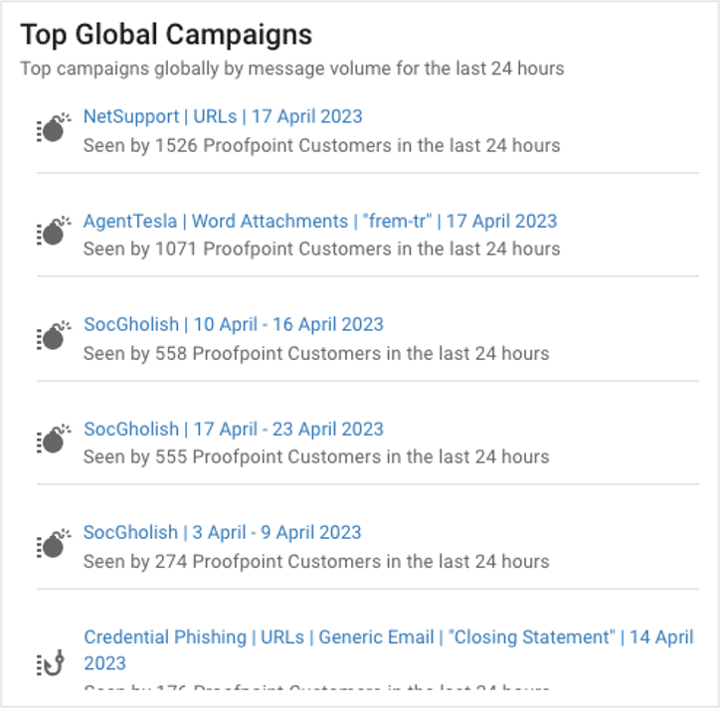
Top Global Campaigns in the TAP Threat Intelligence Summary.
Threat Landscape Overview (Global and Vertical)
These reports offer critical situational awareness data to help you benchmark your company’s security posture against others in your vertical. Detailed charts provide views of email threat activity by family, malware and actor. This data helps you to understand your true risk level so you can bolster your security measures where needed.
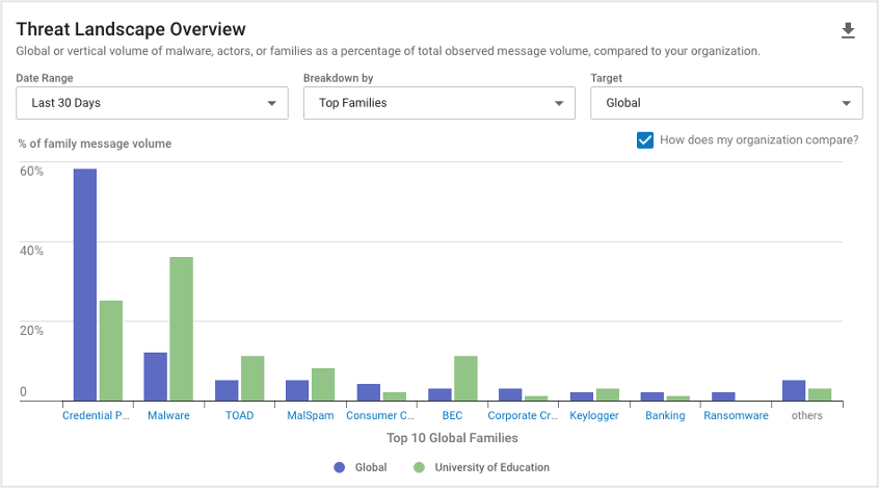
Threat Landscape Overview (Global) by Top Families.
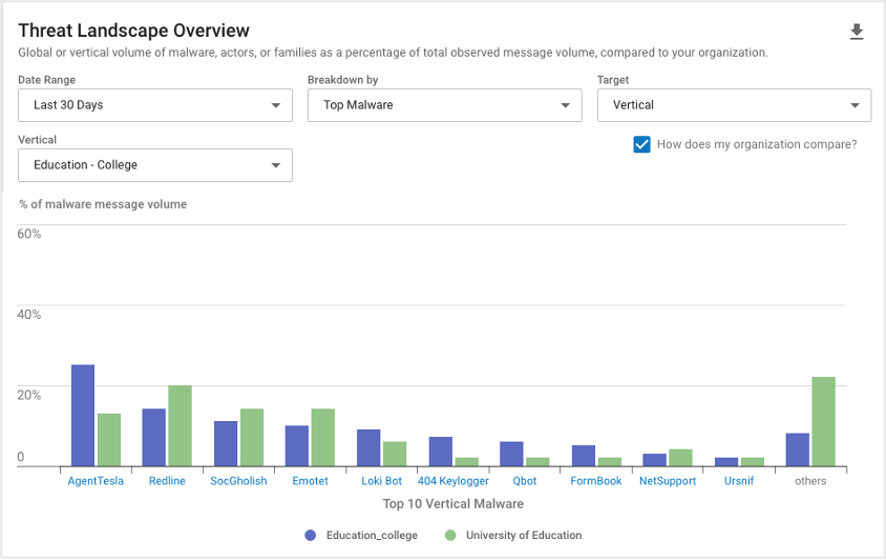
Threat Landscape Overview (Vertical) by Top Malware.
The Threat Landscape Overview chart provides more context and detail to complement and enrich the Industry Attack Index Comparison charts in the Organization Report.
So, for example, if your company’s Attack Index is noticeably higher than the index for peers in your industry, you can toggle the Industry Comparison Report to breakdown by Threat Family to look for specific categories of email threats that could be driving the increase.
Once you identify these categories, you can go to the Threat Landscape Overview and select the same vertical and date range. Then, select the Top Families breakdown. By comparing the families in question, you can confirm and quantify the difference in message volume.
From here, you can use the Effectiveness Report’s new Categories option to view your company’s effectiveness against this threat. Then, you can use the filters for the Effectiveness Trend chart to identify areas for defensive improvements.
Global and Vertical Malicious Message Volume Trends
These reports compare your company’s threat activity to global and vertical trends over the past six months. These reports can help you to identify anomalies, address potential security gaps and align your defenses with current threat patterns.
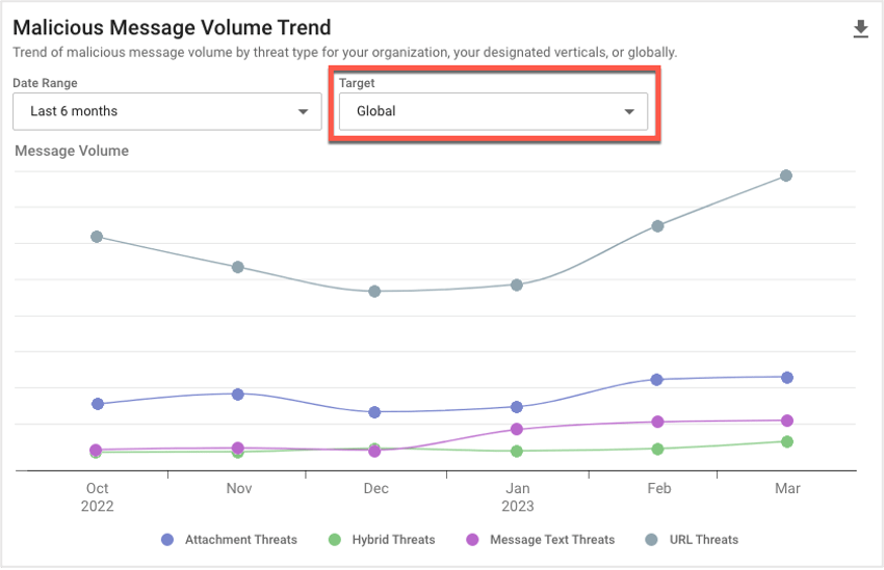
Global Malicious Message Volume Trend overview.
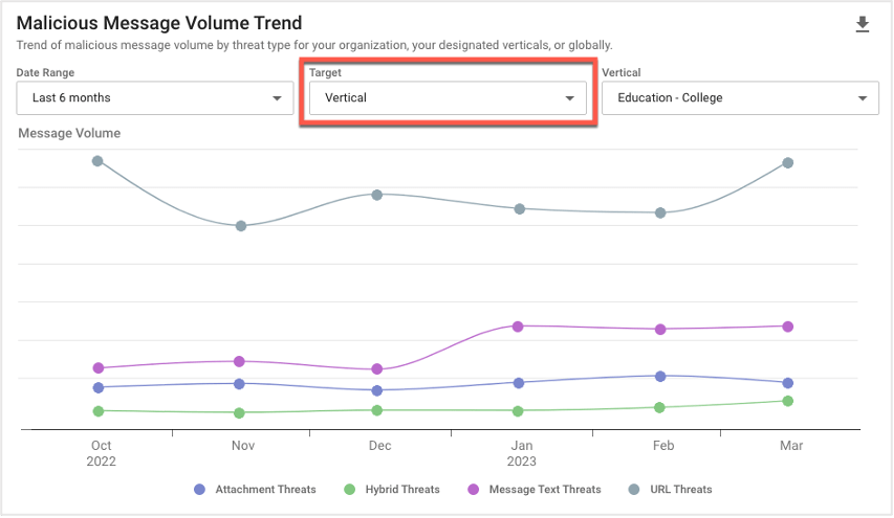
Vertical Malicious Message Volume Trend report.
For example, say that you notice a significant increase in the volume of email threats targeting your business. You can compare your company’s message volume against global and vertical trends to determine whether this increase is focused on your business—or whether it’s part of a broader trend in the threat landscape.
Global Top 5 Vulnerabilities
This report displays vulnerabilities (by CVE) that have the highest percentage growth of exploit attempts. It’s based on data from the Proofpoint Emerging Threat global network. Your security team can use this report to prioritize its patching efforts and fortify your environment against the vulnerabilities that are currently the most actively exploited.
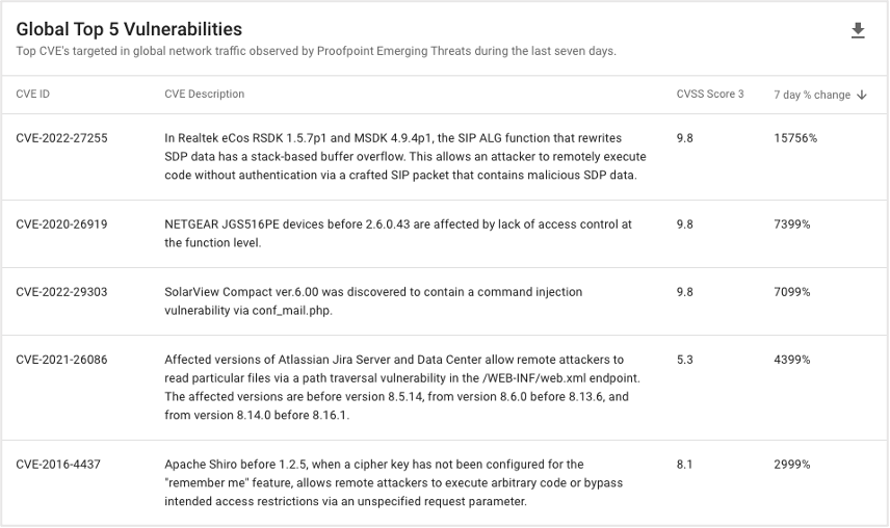
Global Top 5 Vulnerabilities shown in the TAP Threat Intelligence Summary.
Targeted controls
You can significantly reduce your company’s cybersecurity risks when you adjust your targeted controls based on what you learn from the Threat Intelligence Summary. Here are some ways you might want to use these insights:
- Email filtering and blocking. When you have key data about top global campaigns and emerging threats, it’s easier to customize your email security rules. You can also block suspicious emails that are associated with known threats.
- Patching and vulnerability management. The global top five vulnerabilities can help you to prioritize your patching efforts. It helps you focus your efforts on addressing the vulnerabilities in your systems and software that threat actors are actively targeting.
- User awareness and training. When you know the latest social engineering techniques, phishing campaigns and malware trends, you can create targeted security awareness programs. Employees who are educated are much better able to recognize threats and report them.
- Endpoint security. You can use insights from the threat landscape and global trends reports to adjust settings in your endpoint security solutions to make them more robust. You can also choose advanced cybersecurity solutions to plug any security holes.
- Incident response and threat hunting. When you have indicators of compromise (IOCs) and TTPs from known threats at your fingertips, you can put them to use into your security operations. Use them to improve your ability to detect, contain and remediate incidents.
- Security Information and Event Management (SIEM). Threat insights can help you configure your SIEM system so that it’s more effective detecting and responding to threats. You can incorporate relevant threat indicators and patterns into your SIEM rules and correlation logic to prioritize and escalate security events.
Stay up to date with the latest trends
Insights in the Threat Intelligence Summary are valuable in ways that go beyond protecting your organization. They also help you to easily monitor current trends, which you can share among peers. When you’re aware of the latest cybersecurity trends, you’re able to join in more conversations, participate more actively in forums and industry groups, and be a part of other information-sharing initiatives. All of these activities help you to stay ahead of emerging threats and enhance your collective defense capabilities.
Get more insight into your company’s specific cyber risks
The Threat Intelligence Summary and Threat Insight Dashboard in Proofpoint TAP can help you elevate the security posture of your business. Learn more about the Targeted Attack Protection Threat Insights Dashboard and Actionable Insights from Proofpoint.
If you want to know the biggest cyber threats to your business, reach out for a free Rapid Email Risk Assessment. One of our security experts can help you identify some of the most significant cyber threats your company faces, like domain risk. Even better: They can show you how to mitigate them.











