Have you struggled with productivity-sapping prevention tools that aren’t built for the hybrid and remote work world? You aren’t alone. Security teams around the globe worry about losing intellectual property and sensitive business information on top of regulated data loss.
With insider threats on the rise, it’s more important than ever to get the right the balance between reducing data loss risks and unintentionally blocking legitimate business activities.
The new visibility and prevention capabilities from Proofpoint discussed below can help you achieve the right balance between risk reduction and business enablement.
Enhanced Endpoint DLP prevention and detection capabilities
Over the past year, many customers have expressed concern about the complexity of tackling data loss through the manual correlation of disparate alerts. They also worry about incomplete visibility from unconnected solutions. These risks could lead to catching potential data exfiltration late or leaving major evidence gaps in insider investigations.
Proofpoint Insider Threat Management (ITM) and Endpoint Data Loss Prevention (DLP) can help address these issues. We built these solutions within our Proofpoint Information Protection Platform, which is modern, scalable and cloud-native. Proofpoint Cloud App Security Broker (CASB) and Proofpoint Email DLP share this platform under the Enterprise DLP suite.
And now, if you’re an existing Proofpoint ITM software-as-a-service (SaaS) or Endpoint DLP customer, you can benefit from new data loss prevention capabilities around sensitive data movement to and from cloud sync folders and the ability to simulate detection rules during the rule configuration process. These features, described in more detail below, will be available to you with no change to your current workflow.
Preventing sensitive data movement to and from cloud sync folders
In most organizations, syncing files to personal cloud storage solutions can be native through cloud sync folders on endpoints. Users pay little attention to file locations when they’re saving files as long as they can easily find and use them to collaborate later. And with increased remote work, we see an uptick in the use of personal cloud sync folders as the first staging location in data exfiltration attempts.
Customers can now prevent sensitive data movement to cloud sync folders when the data movement is clearly out of policy or if a malicious user is trying to hide their tracks. You can define lists of permitted and prevented values for users, file extensions, and the cloud storage provider name. We support the sync folders from Microsoft OneDrive, Google Drive, Box, Apple iCloud and Dropbox cloud storage providers out of the box.
Also, you can protect files from being exfiltrated to cloud sync folders based on source URL or file content using Microsoft Information Protection (MIP) sensitivity labels. The prevention rule will block the exfiltration even if the user attempts to first rename or in any way manipulate the file.
In the simplified example shown below, the security team used our prevention rule template to specify the type of activities (“file write”), user groups (“domain users”), MIP classification labels (multiple, critical labels specific to the organization) and common personal cloud storage providers (“iCloud Drive” and “Dropbox”). Once the rule is in place, the user will be blocked from moving files that meet the rule conditions with a simple blocking message.
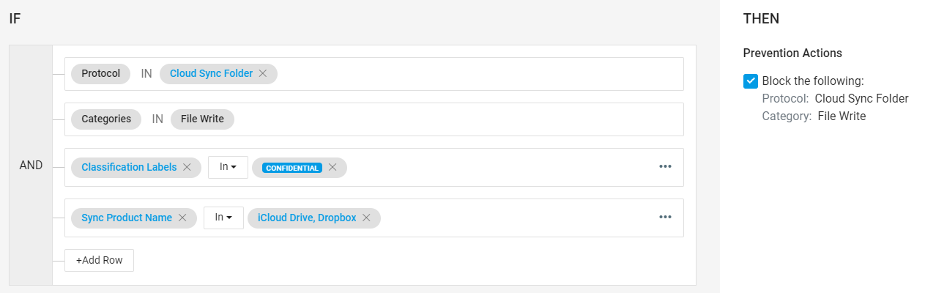
Figure 1: Proofpoint prevention rule editor
With cloud storage an everyday reality in most organizations, security teams have to contend with multiple versions of sensitive data duplicated across the endpoint and cloud sync folders with lax sharing permissions. With our proven, lightweight endpoint agent and patented file driver, Proofpoint Endpoint DLP provides visibility and detection and prevention capabilities without the traditional headaches of a heavyweight endpoint agent.
Common use cases for MIP labels and cloud sync prevention
Following are a few common use cases for detecting and preventing sensitive data movement:
- User groups: Prevent users who’ve given their notice from copying sensitive files from specific locations onto USB devices
- Classification (MIP) label: Prevent any file marked as confidential based on the MIP label from exfiltration through unlisted USB devices
- Reduced alert triage: Focus on detecting exfiltration of data marked as sensitive through MIP labels rather than all data downloads from sanctioned sites such as SharePoint or Salesforce
Test before use with the new detection rule simulator capability
The new detection rule simulator capability allows you to see how often a newly created or existing detection rule has fired in a specific time frame. That helps security administrators and policy analysts improve the accuracy of their detection suite within ITM and Endpoint DLP.
Also, when an analyst knows there is risky behavior occurring in the organization, it gives them more confidence in the merits of a newly created rule. They may have been blind to the frequency of activity prior to implementing the detection rule.
In the example below, you can see how Proofpoint Endpoint DLP allows you to explore two activities that would’ve triggered a specific rule in the past 90 days. You could then verify that the two activities were what you intended to identify in your organization.
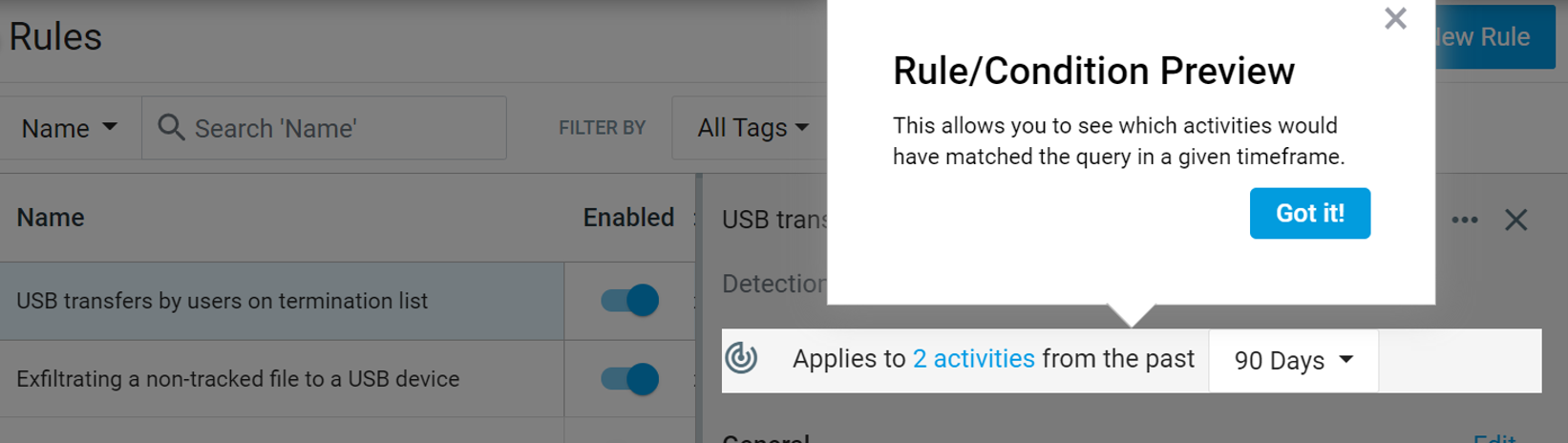
Figure 2: Proofpoint Endpoint DLP rules and conditions
And in the following screenshot, you can see that the detection rule around data exfiltration to USB by users on a termination list has brought up risky activity by “Carol Brown” with the sensitive file marked as “Confidential.” Endpoint DLP blocked this activity.
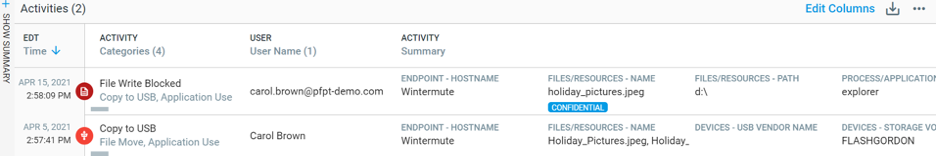
Figure 3: Proofpoint Endpoint DLP explorations view
We look forward to rolling out additional Endpoint DLP and ITM features in the Proofpoint Information Protection Platform that can help make your organization more secure in this rapidly changing world. Learn more about our latest capabilities on the Proofpoint Endpoint DLP page.











