Data doesn’t move, people do. And your users—who could be negligent, compromised or malicious—interact with your sensitive data every day. Have you struggled with preventing people from exfiltrating sensitive data? You are not alone. Security teams around the globe are worried about losing intellectual property and sensitive business information on top of regulated data loss.
With insider threats on the rise, it’s more important than ever to get right the balance between the preventing of data loss risks and the pain of blocking legitimate business activities. We’ll discuss how our visibility and prevention capabilities help you get the balance right between data loss prevention (DLP) and business enablement.
Enhanced Endpoint DLP capabilities and smoother incident response workflows
Today, we’re excited to announce our enhanced Endpoint DLP capabilities which detect sensitive data movement and prevent such movement or exfiltration to USB devices attached to the endpoint. These features will be available to you with no change to your current workflow if you are an existing Proofpoint Insider Threat Management (ITM) SaaS customer.
Over the last year, many customers have expressed the complexity of tackling data loss through manually correlating disparate alerts and incomplete visibility from unconnected solutions. They ran the risk of catching potential data exfiltration late or leaving major gaps of evidence in insider investigations. That’s why Proofpoint built its ITM and Endpoint DLP within a modern, scalable, cloud-native information protection platform, shared with CASB and Email DLP under the Enterprise DLP suite.
Microsoft Information Protection integration: increased data context, reduced alert fatigue
Customers want to leverage their existing data classification to optimize their data loss and insider threat visibility and detection. Now, they can do that. Across the Proofpoint Enterprise DLP suite, including Endpoint DLP and ITM, we integrate with the customer’s Microsoft Information Protection (MIP) data classification. Classification labels provide more context about files.
When a file with a MIP label is downloaded to an endpoint, you can use the label to hunt for unknown risks, create rules for proactive alerting, and generate meaningful reports. We will detect MIP labels during any data movement, and optionally generate an alert using that label. This can be seen within the green box in the screenshot below.
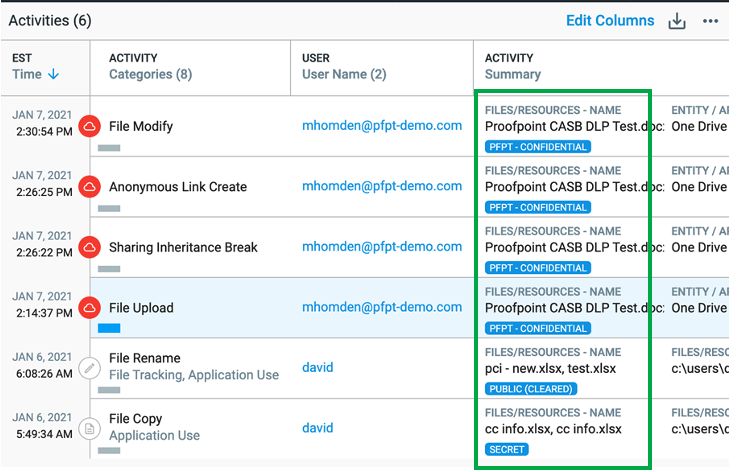
Figure 1: MIP labels seen within the Explorations and Alerts tabs
On top of this visibility, you can detect the movement of sensitive data using new alert rules and conditions. For example, you may only want to detect the movement of data from your corporate CRM system if classified with sensitive labels and by specific user groups. The Proofpoint rule editor allows you to adapt an existing alert with two additional Boolean statements to select the relevant user groups and specify the labels to be tracked.
In the example below, you see a critical level data exfiltration rule for a specific classification label, “Company Confidential”, and for users within a specific business unit. Given the criticality of this alert, you will get a notification within one of your Slack channels and within your SOAR.
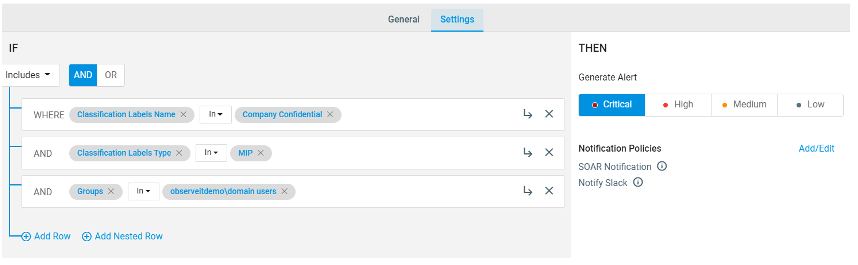
Figure 2: Sample data exfiltration rule with MIP classification label and user group at a critical level
Prevention of sensitive data movement to USB devices
Customers can now prevent sensitive data movement to USB devices when the data movement is clearly out of policy or if a malicious user is trying to hide their tracks. You can define lists of permitted and prevented values for users, file extensions and devices. In addition, you can protect files from being exfiltrated to USB based on source URL or file content using MIP classification labels. The prevention rule will block the exfiltration even if the user attempts to first rename or in any way manipulate the file.
In this simplified example, the security team used our prevention rule template to specify the type of activities (“file write”), user groups (“domain users”), MIP classification labels (multiple, critical labels specific to the organization) and non-corporate USB devices (“sandisk”, “2Wire”, “3Com”). Once the rule is in place, the user will be blocked from moving files that meet the rule conditions with a simple blocking message.
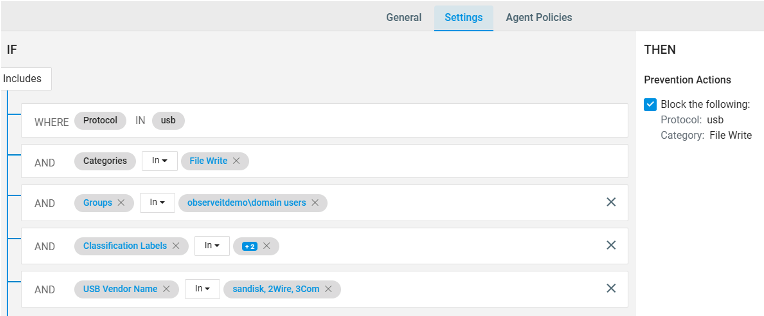
Figure 3: Prevention rule editor
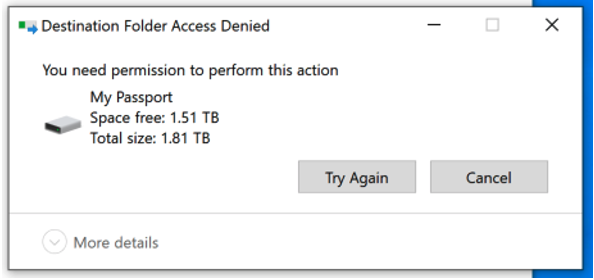
Figure 4: Blocking message to the end-user
In the past, security teams had to get creative around blocking USB device usage either by blocking the USB hardware port or use legacy, heavyweight and productivity-sapping DLP solutions. With our proven lightweight endpoint agent and patented file driver, we provide prevention capabilities without creating more headaches for security teams.
Common use cases for MIP labels and USB prevention
Here are a few common use cases for detecting and preventing sensitive data movement:
- User groups: Prevent users, who’ve given their notice, from copying sensitive files from specific locations onto USB devices
- Classification (MIP) label: Prevent any file marked as confidential based on the MIP label from exfiltration through unlisted USB devices
- Reduced alert triage: Focus on detecting exfiltration of data marked as sensitive through MIP labels rather than all data downloads from sanctioned sites such as SharePoint or Salesforce
The start of the year has already been a busy time with a bounty of new product features. We look forward to rolling out additional endpoint DLP and ITM features in our platform and making your organizations more secure in this rapidly changing world.
Learn more about the platform capabilities on Endpoint DLP page.











