After getting approval to run your security awareness program, you might be tempted to start simulated phishing assessments, and train users on topics like ransomware, credential phishing, and other advanced topics like business email compromise. But having a strategic plan in place to provide foundational knowledge, understand your vulnerabilities, and focus your training is important to maximize people-centric risk reduction while minimizing user time investment.
The Importance of Foundational Training
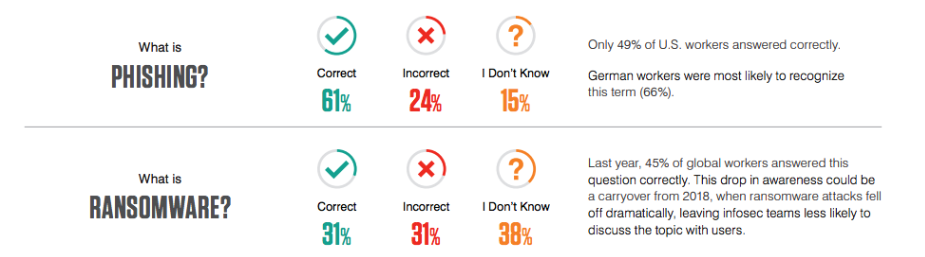
End user survey information from 2020 State of the Phish
For those working in IT and infosec, training on advanced topics seems logical, as those might be the most relevant threats facing your organization. However, there could be foundational knowledge missing that would leave end users unprepared for these exercises. In our 2020 State of the Phish, we found that many end users struggle to identify the definitions of terms like phishing and ransomware. In our multiple-choice survey of working adults from around the world we found:
- Only 61% correctly identified the definition of phishing
- Only 31% correctly identified the definition of ransomware
This is why we highly recommend foundational training in core topics like security essentials, phishing, and other topics you deem important, before you assess or train on more advanced topics. Our software, like many others, allows for onboarding training assignments for new hires which we recommend to include several fundamental training modules. That way, you’re always providing foundational training for all users before providing more advanced assessments and training.
Vulnerability: Who Are Your Very Attacked People?
Most organizations that conduct security awareness training evaluate end-user vulnerabilities, whether via simulated phishing attacks or question-based knowledge assessments. Far fewer look more in-depth at user behavior in order to understand which of their users are being attacked and how frequently. This is one of the ways in which we calculate organizations’ Very Attacked People™, or VAPs.
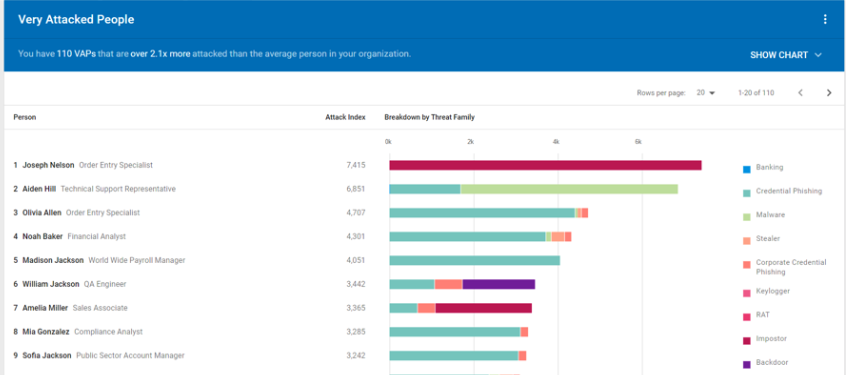
Sample representation of Very Attacked People™ (VAP) report
This information allows administrators to focus program efforts and reduce risk more quickly. It may also provide context as to why attackers are targeting these users. You can not only keep a closer eye on these users or ones with similar titles, but put in place other adaptive controls like Browser Isolation.
Additionally, Proofpoint’s Targeted Attack Protection (TAP) provides greater insight into if users are targeted with malicious content. Knowing if users are clicking simulations is helpful, knowing if they’re also clicking on real malicious content is even more important – even if the click on the URL is blocked. This data can provide invaluable insight into potential organizational risk and gaps.
Beyond Phishing: Passwords, Compliance, Mobile Security, and More
Phishing is the most discussed threat in security awareness training, but focusing your program solely on email-based threats can leave significant gaps in other important topical areas. Consider using a broad-based knowledge assessment to understand users’ knowledge of cybersecurity topics, in addition to your own internal policies or guidelines.
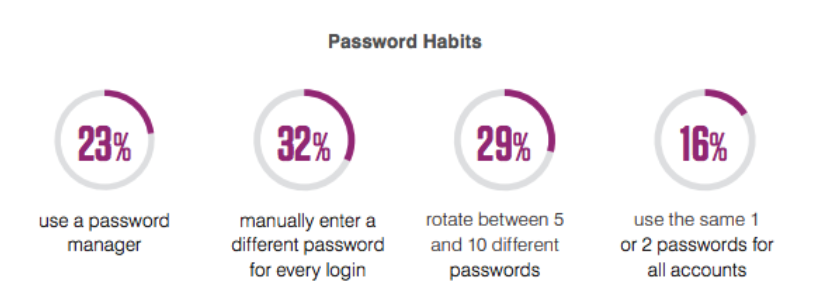
Password habit findings from a survey in the 2020 State of the Phish Report
Our global surveys of working adults have revealed a number of risky behaviors, including the following:
- 45% of working adults admit to password reuse
- Only 49% password-protect their home Wi-Fi networks
- 26% believe they can safely connect to a free Wi-Fi network in a trusted location (like a coffee shop or airport), and another 17% aren’t sure if open-access networks in these locations are safe or not
These behaviors open your organization to significant risk, so we highly recommend diversifying a program to address these and other potential areas of weakness.
One helpful tactic we’ve found to further these topics is providing users real-life stories and context of successful attacks or how attackers operate can help provide a “why” to users and better change their behavior and understanding.
Training on Need and Vulnerability
It's critical to align security awareness training exercises to real and potential threats to your organization. Planning ahead is a great practice, but agility is important as well. We recommend you adapt your program as circumstances dictate. As 2020 has taught us, there are always variables that can lead to new knowledge gaps and risky user behaviors.
Here are some examples of situations where you may change your plan based on need or vulnerability:
- Your phishing assessments show users are demonstrating an understanding of link-based attacks, but are struggling with attachment-based simulations
- Your organization is increasingly the target of business email compromise-style attacks
- Your email security team notices attackers using a specific brand of phishing lure or type of attack being leveraged against your users
- In your knowledge assessment, you notice a specific department struggles with an essential topic
One of the features our customers enjoy is Auto-Enrollment from simulations or knowledge assessments into a training assignment. This feature allows customers to target training to users who need it most if they don’t pass an assessment, but doesn’t force users to complete it in that moment. Using this targeted approach is a good way to train on vulnerability and need rather than requiring all training assignments for all users. It also saves user time in the process and is typically easier to get buy-in from stakeholders.
Testing Users Out
An additional tactic to focus user time is the ability to test-out users from training. If users have taken their foundational training, continuously don’t engage with simulations, and demonstrate through a knowledge assessment they understand the topics you need them to, it may make sense for those users to take less training overall. Communicating this “test-out” capability to users may help build positive sentiment and get users more focused on carefully engaging with your assessments, as they know they can save their own time through demonstrating performance.
Every organization is going to have a unique threat landscape, user base, and security awareness culture. Adapting your program to these constraints and ensuring you’re targeting your training program to the right people at the right time will ensure you’re not only running a comprehensive program, but a targeted and effective one that maximizes the limited 1-2 hours of security awareness training per user per year most organizations have budgeted to reduce your organization’s people-centric risk.
Follow our blog as we provide free guidance on how to build a successful security awareness training. Watch our panel webinar: Benchmarks & KPIs You Need to Know for Security Awareness Training.











