Security awareness training can be a valued part of the organization’s security and privacy culture, producing measurable results, rather than a must-do compliance exercise. It provides objective measurement of people-centric risk and has shown consistent results in lowering that risk in organizations across the globe. Timing is critical to your security awareness training program, particularly when it comes to identifying training needs, identifying users and groups, defining activities and establishing and managing schedules.
Recommended Order of Activities
Identify key groups who may need a different curriculum or specific training tailored to their needs.
Popular groups our customers utilize include:
- Very Attacked People (VAPs): Users who are the most attacked according to your email security or other security teams.
- VIPs: C-Level executives, board members and other staff who may need specific training and guidance because of their importance to the organization. Note that VIPs may fall into the category of VAPs.
- Role and department-specific groups: Users in human resources, finance, legal, compliance, development or other roles may need legally mandated or other specific training. Consider different knowledge assessments and simulations specific to these groups as your security awareness training program gets more advanced.
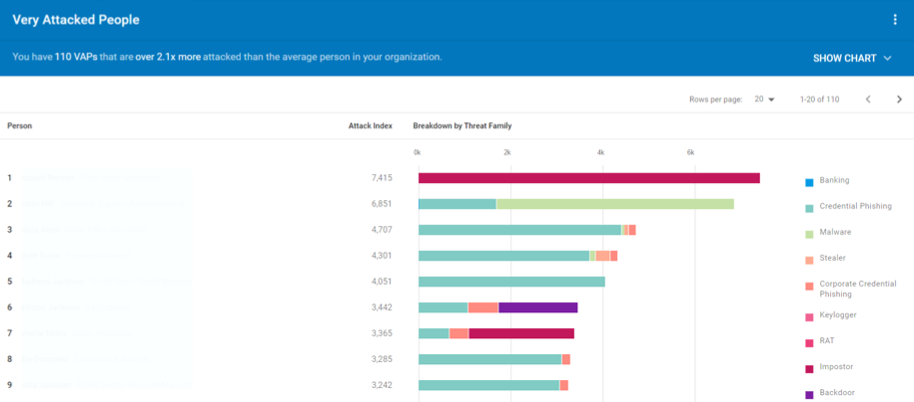
Very Attacked People Report from Proofpoint Targeted Attack Protection
Identify the key activities you will include in your security awareness training program:
- User assessments such as phishing, USB, and smishing (SMS/text phishing) simulations or knowledge assessments
- Computer-based training based on user needs and the current threat landscape
- Awareness activities (posters, webinars, newsletters, videos) to introduce concepts and reinforce key messages
- In-person activities such as lunch and learns or training sessions. Get creative. For example, some of our customers have created cybersecurity escape rooms that have been successful.
Define the order of activities
- First, user assessments provide insight on the training assignments needed to improve user understanding of phishing, data protection, mobile security, and other critical people-centric security topics. You can find out user risk through simulations or knowledge assessments. In identifying training needs, organizations need to analyze their risk landscape. This is where threat intelligence plays a critical role. Threat intelligence will help you understand the current and emerging threats users may be experiencing.
Get a baseline and prepare before program start
- Two months prior to launch, we recommend sending a test phishing simulation to a small “in the know” group to identify any hidden technical issues. Then send a moderately-difficult baseline phishing test to all employees – rather than having them taken to a landing page if users fail take them to a 404 page.
- One month prior to launch, announce the program to users and, if deploying an email reporting add-in, provide guidance on its purpose and how to use it. Finally, if you have access to content like posters, images, or other security awareness materials, post them around the office or on a wiki about your program.
Customers who take these extra due diligence and planning steps have experienced more successful programs.
Frequency of Activities
We generally recommend the following recommendations in our best practices documentation for frequency and timing of activity:
- Sending a phishing test every four to six weeks and mixing up the types of themes and lures used.
- Using auto-enrollment on phishing tests at least once a quarter and using a targeted follow-up module, depending on the type of attack sent.
- Reviewing VAP reports monthly or bimonthly. Depending on what is seen there, admins should decide who should receive targeted training and which training content to use.
- Assigning organization-wide training at least quarterly.
- Repeating broad CyberStrength knowledge assessments and blind phishing tests at least once a year to compare to baseline assessments.
- To reinforce learning retention, schedule at least bi-annual security awareness activities like webinars, contests, or in-person (if possible) activities.
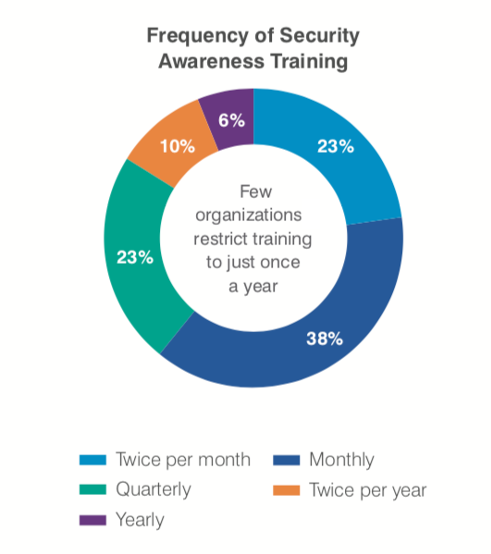
Organizations should create an annual framework to schedule the components and frequency of their security awareness training activities, with flexibility expected based on assessments or the threat landscape. Our 2020 State of the Phish Report found that security awareness training has progressed beyond annual and quarterly activity, to monthly or even bi-monthly training. We generally recommend monthly or anything that is more frequent. This would include targeted training, awareness campaigns and knowledge assessments.
Modifying frequency or order
Your security awareness program needs a continuous approach. From the initial assessment baseline, future assessments can help track user proficiency and provide a measure of risk reduction. Here are indicators that you should modify the frequency or order of activities:
- When specific user threats become more prevalent, or attackers use a specific brand or lure, modify assessment content like simulated phishing campaign templates or use threat-driven security education to better manage the risk.
- If your organization experiences an event, such as a data breach, consider updating your planned activities and frequency of communication, assessments, and training related to that event.
- If new laws or regulations requires additional training, follow up with a customized knowledge assessment to see how users have retained that training content.
- If your organization releases or updates a policy or has doubts about user knowledge of an existing policy, again a customized knowledge assessment can help you identify gaps in user understanding and guide training efforts.
- If a security awareness program was stopped for more than six months, it may make sense to relaunch the program to ensure users understand context and importance.
- We do not recommend ramping up the training frequency of users too much—even with repeat offenders who struggle with assessments. For instance, if you conduct monthly phishing assessments and selectively enroll users who “fail” into a single training, that’s a targeted approach. If you take those users and assign them 4 trainings, our customers reported users feel overly targeted and begin to have negative sentiment with the program.
Timing is not an isolated concept for your security awareness training program, it is literally the sum of all efforts. It is the right training, the right people, and many other tactical, organizational and strategic components that produce the composite result of ‘the right time.’
Don’t try to boil the ocean with your security awareness training program out of the gate. Do the appropriate analysis up front, backed with threat intelligence and assessments, and work throughout the organization to build a realistic plan with top down support.
This approach not only applies to new security awareness training programs but also to existing ones. Security awareness training has proven its value in reducing people-centric risk at thousands of companies. Learn more about how to implement it to achieve measurable results within your organization.











