

Guide Users
Simplify behavior change with automated, risk-based learning
Transform your high-risk employees. Change risky behaviors and foster a strong security culture with cybersecurity awareness training.
Introducing Proofpoint Satori™ Phishing Simulation Agent – Automatically deploy attack-informed simulations.
See the announcements from Protect 2025.
Educate and motivate your people so they can become part of your security solution
Security awareness training alone is not enough. To drive behavior change and build a security-minded culture, organizations must go beyond mere compliance-based awareness programs. Identify and focus on high-risk individuals, actively engage and motivate them and cultivate a security-conscious culture.
Focus on, engage and empower high-risk individuals
Gain insights into individuals who represent the greatest risk with intelligence that’s derived from Proofpoint People Risk Explorer. Engage them with targeted security education tailored to their roles, behaviors, skills and the specific threats they face.


Scale your security awareness program with smart automation
Create a behavior change program by designing targeted campaigns that adapt to individuals’ unique risks and behaviors. Automatically enroll them in a tailored curriculum that includes security education, assessments and other interventions.
Drive behavior change and build a strong security culture

Motivate people and keep them engaged through gamified learning, role-relevant content and real-world scenarios. Assess people’s attitudes and beliefs about security with a culture survey that is both concise and efficient.
Build resilience against emerging threats
Equip people with the right knowledge, tools and attitudes to protect against human-activated threats and the latest attack tactics. Adjust education and threat simulations based on what’s happening in the current threat landscape.

Key features of Proofpoint’s ZenGuide™
Detect human risk through a whole new lens
Proofpoint’s Security Awareness Training helps you identify high-risk individuals and measure human risk by evaluating their roles, behaviors, vulnerabilities, attack risk and business privileges. Run a data-driven behavior change program that goes beyond training and phishing simulations.
We detect and measure human risk based on:
- Behavioral choices
- Threat context
- Roles and business privileges
- Skills and cultural attitudes
- /USB/SMS simulations based on real-world attacks

Automate risk-based security education
Effortlessly create and customize sophisticated, targeted campaigns for your high-risk employees and enroll them automatically.
You can save time and effort with:
- Adaptive Groups, which give you the flexibility to manage learner groups based on various attributes and allow you to automatically assign activities based on individuals’ risk profiles, behaviors, roles and more
- Pathways, which let you easily design curriculum that includes various activities and conditions, such as education, phishing simulations, and assessments, for targeted groups

A personalized learning experience
ZenGuide offers a wide range of security topics, difficulty levels, formats, styles and languages. With bite-sized nano- and micro-learning, you can engage global learners with a unique learning experience and maximize the impact you have on employees.
ZenGuide also enhances learning effectiveness through:
- Just-in-time coaching
- Contextual guidance
- Gamified content
- WCAG support for improved accessibility

Measure and benchmark program success
ZenGuide measures real-world behavior changes and benchmarks them against your industry peers.
When integrated with People Risk Explorer, it reveals high-risk individuals and their risky behaviors, and tracks changes in human risk over time. This ensures better risk communication and ongoing support.

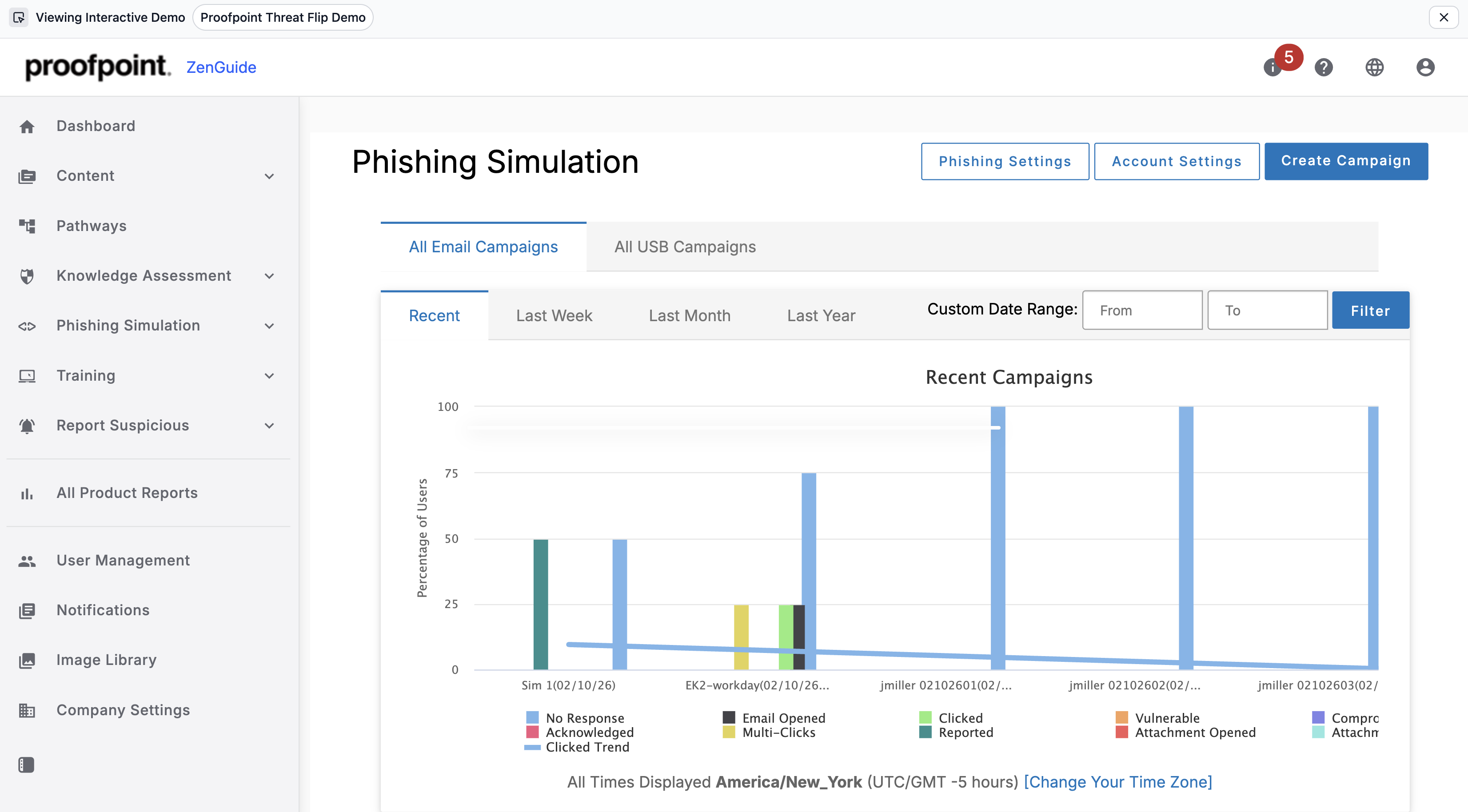
Transform real phishing attacks into AI-powered learning
AI ThreatFlip Workflow allows security teams to convert real-world threats into phishing templates with a single click. Using AI, it automatically defangs threats, removes sensitive data, and suggests timely, relevant guidance on phishing lures, helping bridge the gap between SOC and Security Awareness teams.
AI-powered ThreatFlip enables you to:
- Turn real phishing emails into safe, ready-to-run simulations
- Eliminate manual effort to create templates and phishing lures
- Train employees using AI-generated simulations based on real attacks
- Reinforce learning with real-time Teachable Moments
- Drive measurable behavior change using real-world threat data
Provide an easy report button
ZenGuide equips your people with an easy-to-use report suspicious button, streamlining threat reporting—even when they are accessing email via mobile devices—and reinforcing positive reporting behavior.
The latest developments in mitigating human risk

2024 State of the Phish – Today’s Cyber Threats and Phishing Protection
Read More
Beyond Security Awareness: Moving Toward Sustained Behavior Change

Proofpoint ZenGuide

Proofpoint User Protection
Request a demo
Learn how our integrated platform helps you:
-
Stop cyberattacks
-
Prevent data loss
-
Reduce human risk across your environment










