People’s beliefs and behaviours are key pillars of culture. In Germany pedestrians wait for a light to cross the street in the name of safety. In parts of Asia slurping while eating is a way of indicating to a host you’re enjoying their meal.
So how does your security awareness program drive user behaviours and beliefs in a way that is beneficial? Let’s take a look.
Are Users the Problem or Solution?
It starts with the perception of end users by Infosec departments. Infosec departments frequently view users primarily as a problem. Which is understandable since the 2019 Verizon Data Breach Investigations Report (DBIR) found 94% of breaches are from attacks targeting people. Without users activating attacks, Infosec’s workload would significantly diminish.
And changing that world view, which takes time, is an important first step in how administrators think of their users and their program. This change is possible – we have many customers who have talked about how their educated users have completely flipped the traditional “users are a problem” script and turned their behaviour into something positive.
Engaging with Email Doesn’t Have to Be Bad
One of the first education initiatives we see most of our security awareness training customers complete is focused on email, the No. 1 threat vector. The oversimplified message is not to open, click, download, or be persuaded to respond to emails. Even if you think it’s legitimate - verify what you’ve received and don’t take action because of it.
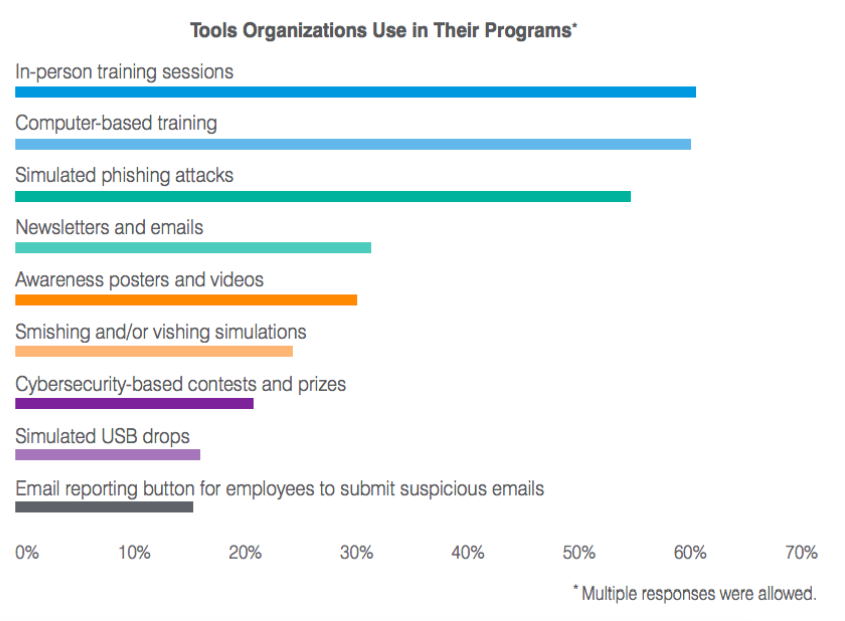
Tools Organisations Use in Their Programs
The less heard message in these programs is what to do with these emails if users think it’s potentially malicious other than avoid it. We found in our 2020 State of the Phish that only 15% of organisations are utilising an email reporting tool in their security awareness programs, and that overall awareness remains low among users of how to use these types of tools.
Providing a simple, one-click email reporting add-in experience for users has a few impacts – it gives them a quick out if they’re unsure what to do and gets a potentially dangerous message to the right team to investigate further. While it simplifies the initial back-and-forth with users about including information like headers, this tool can also create additional volume of messages for an already over-burdened incident response team though.
Culture with Closed-Loop Email Analysis and Response (CLEAR)
Letting users report suspicious emails is great – but providing feedback to them is essential in reinforcing their behaviours with concrete examples. One of the most effective ways to do this is the feedback loop available in our CLEAR solution.
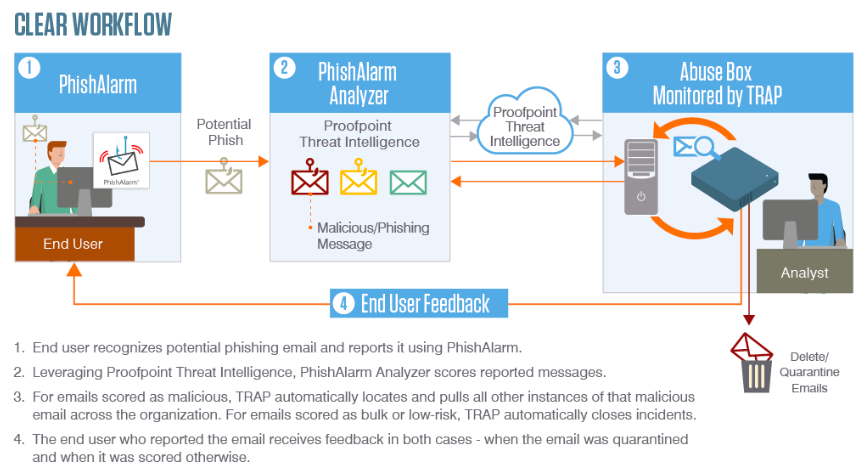
After users report a message our included threat intelligence and dedicated URL and attachment sandboxing will classify the message after analysis. Depending on the classification, the CLEAR workflow will initiate customised messaging back to end users – letting them know what type of message it was they reported (spam, bulk, malicious, etc.) and thanking them for their contribution.
Especially as IT teams are working around the clock to protect their now remote workforces, this time savings is especially important. One customer realised a $345,000 savings in a full-time incident response equivalent headcount over three years, which you can read more about in this Forrester Total Economic Impact™ report.
Our customers have seen this workflow benefit their organisation for incident response teams and users:
“The ability to turn all employees into part of the IT Security team, by reporting phish with a button in outlook and then to pull back out of all employee email if condemned, is very powerful.”
By providing definitive answers and feedback to users about what it was they reported, users are solidifying their beliefs and sharpening their skills at identifying malicious messages. And IT departments make well-trained users a valuable asset against increasingly targeted and sophisticated attacks.
To take it a step further, many of our customers have set up quarterly or monthly contests and rewards, which provide some type of gift to users to thank them. This further reinforces their beliefs and behaviour in a positive way for a security awareness culture.
Elevating Security Awareness Communication to Stakeholders
Another essential component to culture is communication. With the above-mentioned email reporting and remediation loop in place, Infosec teams have new metrics to share. We frequently hear Infosec professionals talk about “click rate” or “failure” in terms of user susceptibility to simulated phishing attacks. But now Infosec departments can communicate a new key metric: user reporting rate.
We found in our 2020 State of the Phish there was more variance in reporting rate than click rate, so it’s a better metric to track and share with stakeholders. We also found the best organisations we found had an over 70% reporting rate of simulated phishing emails, an amazing feat that can have a huge impact on exposure to dangerous business email compromise and spear phishing attacks.
Sharing a reporting rate to stakeholders demonstrates user resilience and skill, rather than the negative connotation implied by a click or failure rate. And Infosec departments can tell stories about user-reported targeted attacks that were stopped due to an educated and aware user. Communicating to stakeholders and users about how they’re protecting their organisation can elevate your program and build a strong, natural culture of security awareness.
Ready to start building a culture of security awareness in your organisation? Learn more about our CLEAR solution.











