Following a letter by Senator Ron Wyden back in July calling for government-wide use of email authentication, The Department of Homeland Security (DHS) announced on Monday that it would increase security for anyone receiving email from federal agencies or visiting a federal website.
At a meeting coordinated by DHS, the New York District Attorney's Office and the Global Cyber Alliance, Assistant Secretary Jeanette Manfra announced the department would issue a binding directive requiring agencies to use two security protocols — DMARC, which prevents fraudsters from sending fake emails, and HTTPS, which encrypts web traffic.
This is welcome news for citizens and organisations in the fight against cybercrime.
Government agencies worldwide are prime targets for cybercriminals, who frequently will spoof their identities in order to steal personal information or money from the general public, companies or indeed from the agencies themselves. There is no better example of this than the Internal Revenue Service (IRS) around tax-year end.
Companies like Proofpoint have been evangelising the use of DMARC for years, and while enterprises have moved up the adoption curve, governments around the world have tended to lag. This new directive very much echoes those initiatives announced by the UK government in June 2016, when they issued similar guidelines and set a deadline of October 1, 2016 for all UK agencies to have published a DMARC record and start blocking fraudulent emails abusing their domains.
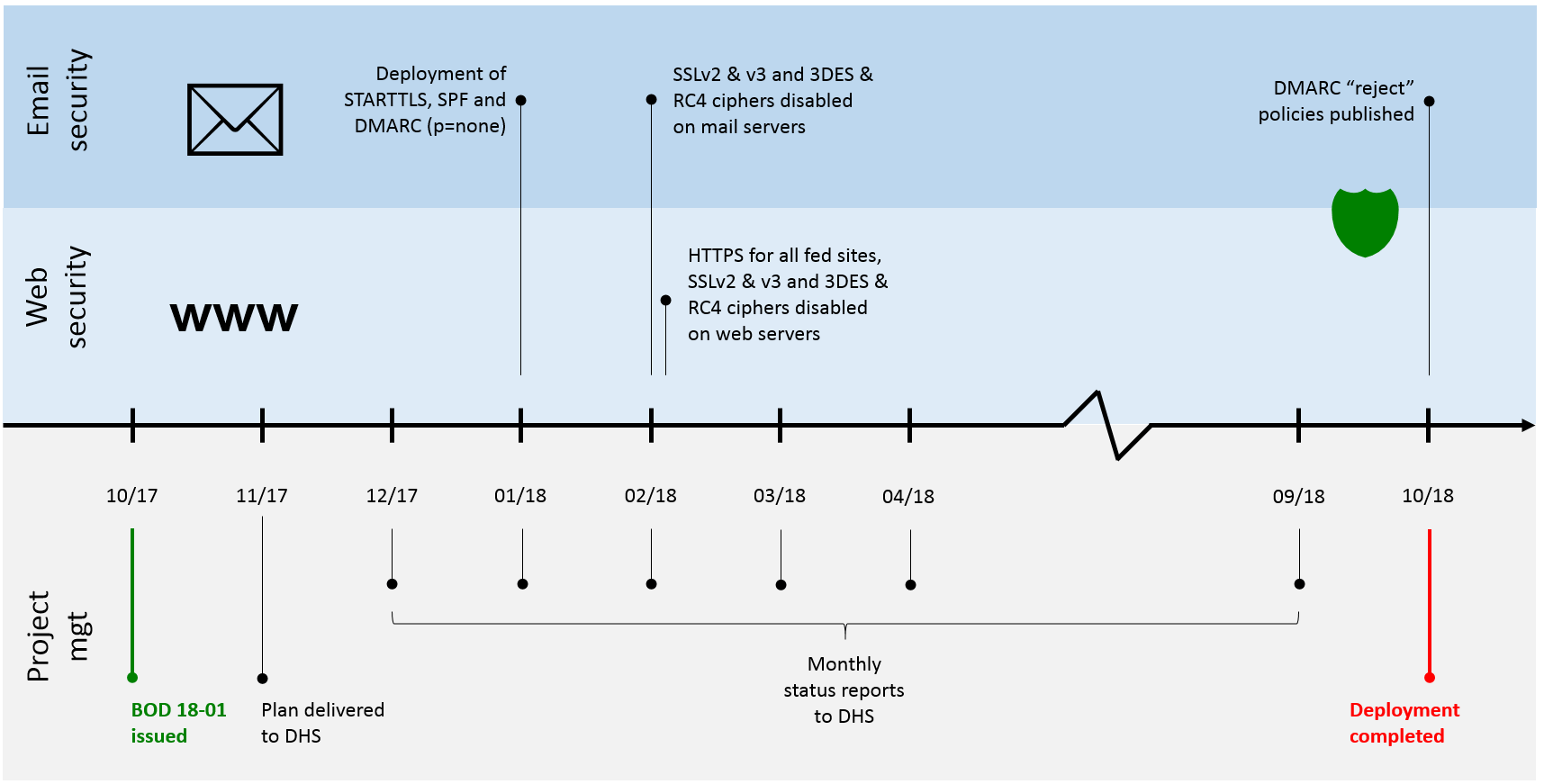
Anyone with hands-on experience of a DMARC implementation project will likely view the timelines issued by the DHS as challenging (see below). While it’s unclear precisely which government agencies will need to comply, there is undoubtedly a lot of work here: even at a parent U.S. State Department level, two-thirds of departments have yet to publish DMARC records and none of them has progressed beyond monitoring mode. Government agencies typically have complex email infrastructures and will require significant expertise as well as resources to ensure their DMARC implementation is risk free – in other words, that they are not blocking legitimate email.
That said, the benefits are clear: in the UK, Her Majesty’s Revenue and Customs (HMRC), often compared to the U.S. Internal Revenue Service, has embraced and promoted the use of email authentication for several years. Once the most phished organisation in the UK., HMRC was one of the first government agencies worldwide to deploy email authentication controls to rebuild consumer trust in the email channel. In November 2016, their then Head of Cyber Security announced their DMARC implementation was complete and had seen them block over 300 million phishing emails.
When implemented, DMARC is a significant barrier to cyber criminals who are attempting to impersonate official agencies. It stops criminals from spoofing agencies’ domains and sending emails on their behalf to unsuspecting recipients. Without DMARC, cybercriminals have a powerful tool to lure employees of the agencies into accidently opening the door to a hack, fool agency partners, and trick U.S. citizens to giving away information that can have substantial consequences.
Securing government communications to its citizens is paramount and this new directive can only help propel the adoption of the same security standards across more and more enterprises, thereby bringing a greater collective security to email and web technologies.
Proofpoint recognises that authentication expertise is not commonplace and stands ready to help federal agencies overcome the challenges that come with implementing DMARC while meeting the project deadlines specified by DHS. To help stop criminals from spoofing domains and sending emails on their behalf to unsuspecting recipients, we encourage organisations to download our free email authentication kit: https://www.proofpoint.com/us/email-authentication-kit and visit our DMARC creation wizard: https://stopemailfraud.proofpoint.com/dmarc-start/.

