Overview
Tax season and the rounds of phishing lures that accompany it are annual traditions in the US. This year, we tracked malware distribution in addition to the customary phishing schemes among the email threats related to federal taxes. We also saw this tradition extend north of the border to Canada, where taxes are due on April 30th.
Analysis – Malware Delivery
Tax-related themes are frequent lures for phishing emails and websites. This year, though, Proofpoint researchers examined several campaigns that also distributed malware through tax- and IRS-themed emails. In the first campaign we tracked, recipients were encouraged to read the new IRS privacy policy in an attached document. The email contains several elements of social engineering, explaining why recipients needed to open the document and why they should enable the embedded macros -- in this case, a bogus claim of mandatory encryption. Once enabled, the macros download Dridex botnet ID 1105.
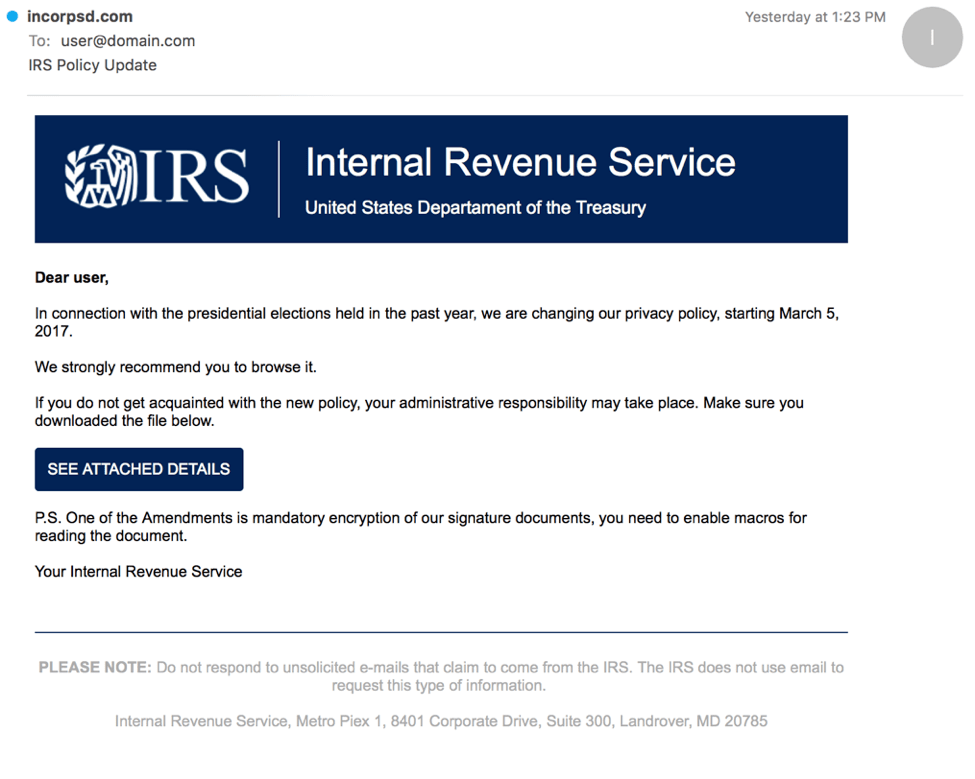
Figure 1: IRS tax "privacy policy update" email lure
Another email campaign targeting US recipients offered a special "loyalty tax refund" program. While the social engineering in this lure was far less sophisticated, the attached malicious document delivered Sage ransomware via embedded macros. Sage ransomware made headlines earlier this year for its very large ransoms, generally asking users for $2,000 USD to decrypt their files.
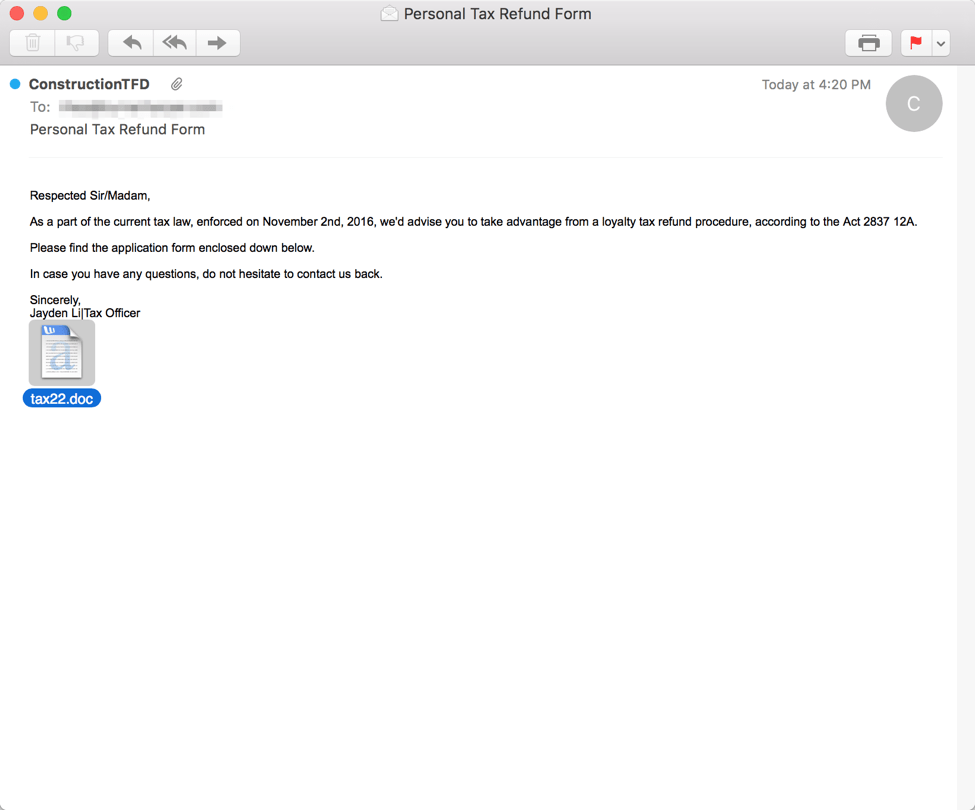
Figure 2: Email lure with attached document that delivers Sage ransomware if the user enables the document macros.
A separate campaign delivering Sage during the third week of February was noteworthy because it used links to zipped JavaScript files (Figure 3) instead of attached malicious documents. The email lure uses a missed payment deadline aligned to the date of the message to create a sense of urgency around the email. When recipients click the link and decompress the archive, the JavaScript file installs Sage.
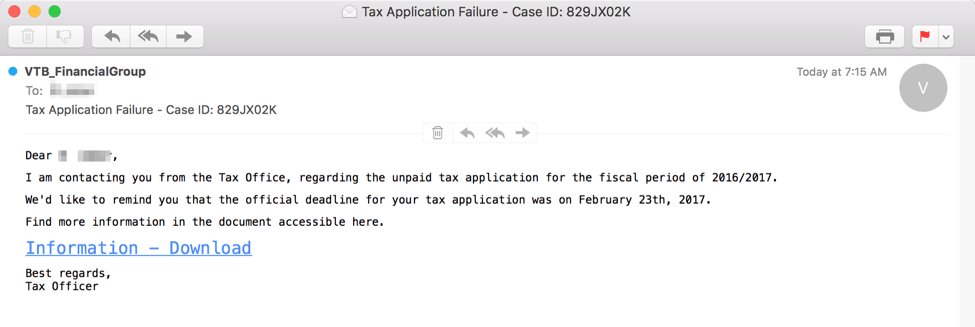
Figure 3: Tax-themed email lure distributing Sage ransomware via a malicious link to a zipped JavaScript file
Another malicious email campaign leveraging tax-themed lures delivered LuminosityLink via attached macro-laden Excel spreadsheets. LuminosityLink is a remote access Trojan (RAT) that includes a comprehensive keylogger capable of injecting code into most running processes on infected PCs. Proofpoint has also observed LuminosityLink being used to download additional payloads based to targets identified as high value by attackers based on analysis of infected systems. An example of the malicious spreadsheet appears in Figure 4.
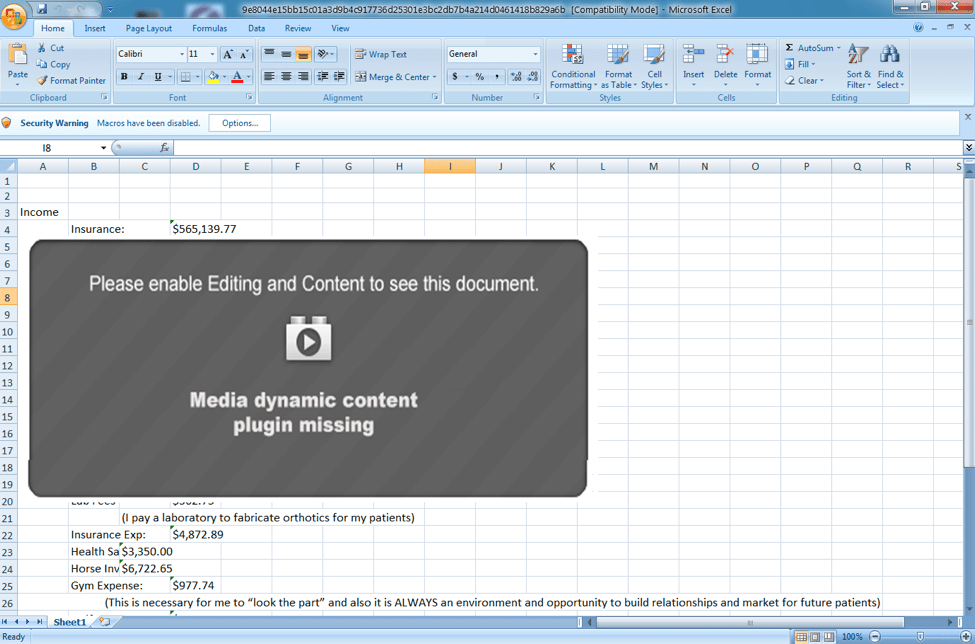
Figure 4: Socially engineered spreadsheet with apparent tax deductions and an image explaining why recipients should enable macros
“The Trick”, also known as TrickBot and TrickLoader, has emerged recently as a high-profile banking Trojan with links to the infamous Dyreza banker and the actors behind it. On February 22, we observed a well-crafted socially engineered attack delivering The Trick under the guise of documents to be completed for the Canadian Revenue Agency (the Canadian equivalent of the US Internal Revenue Service).
The professional-looking email, shown in Figure 5, includes instructions and contact information related to the attached “secure documents” (Figure 6). The documents download The Trick when recipients enable macros.
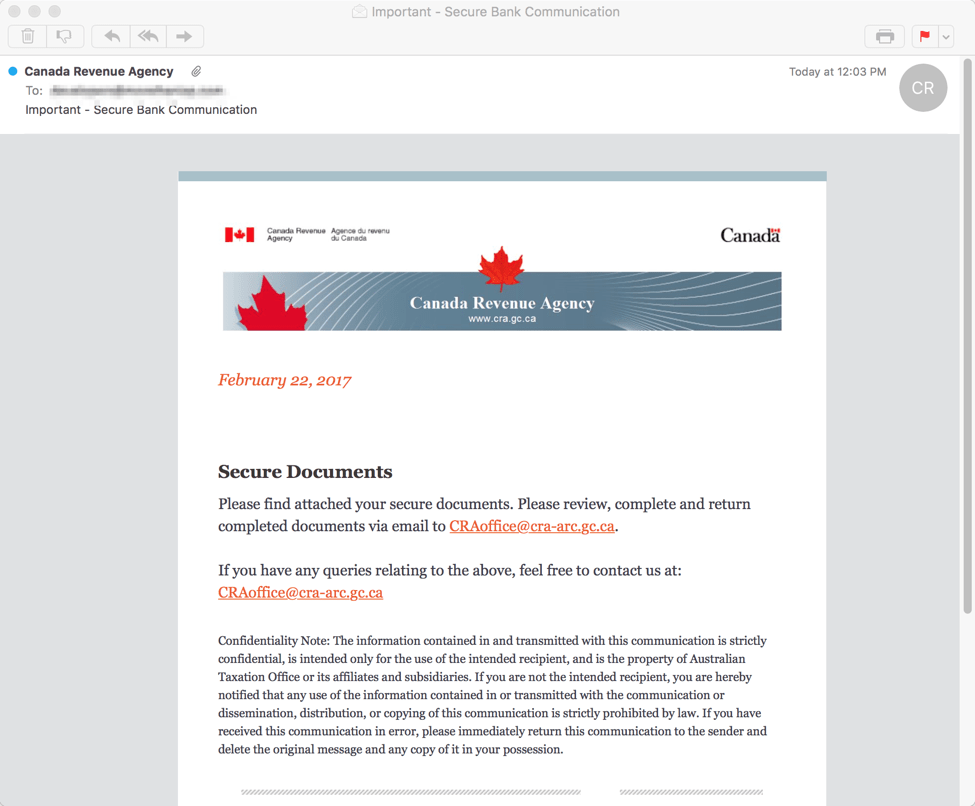
Figure 5: Lure email delivering bogus documents related to Canadian tax information
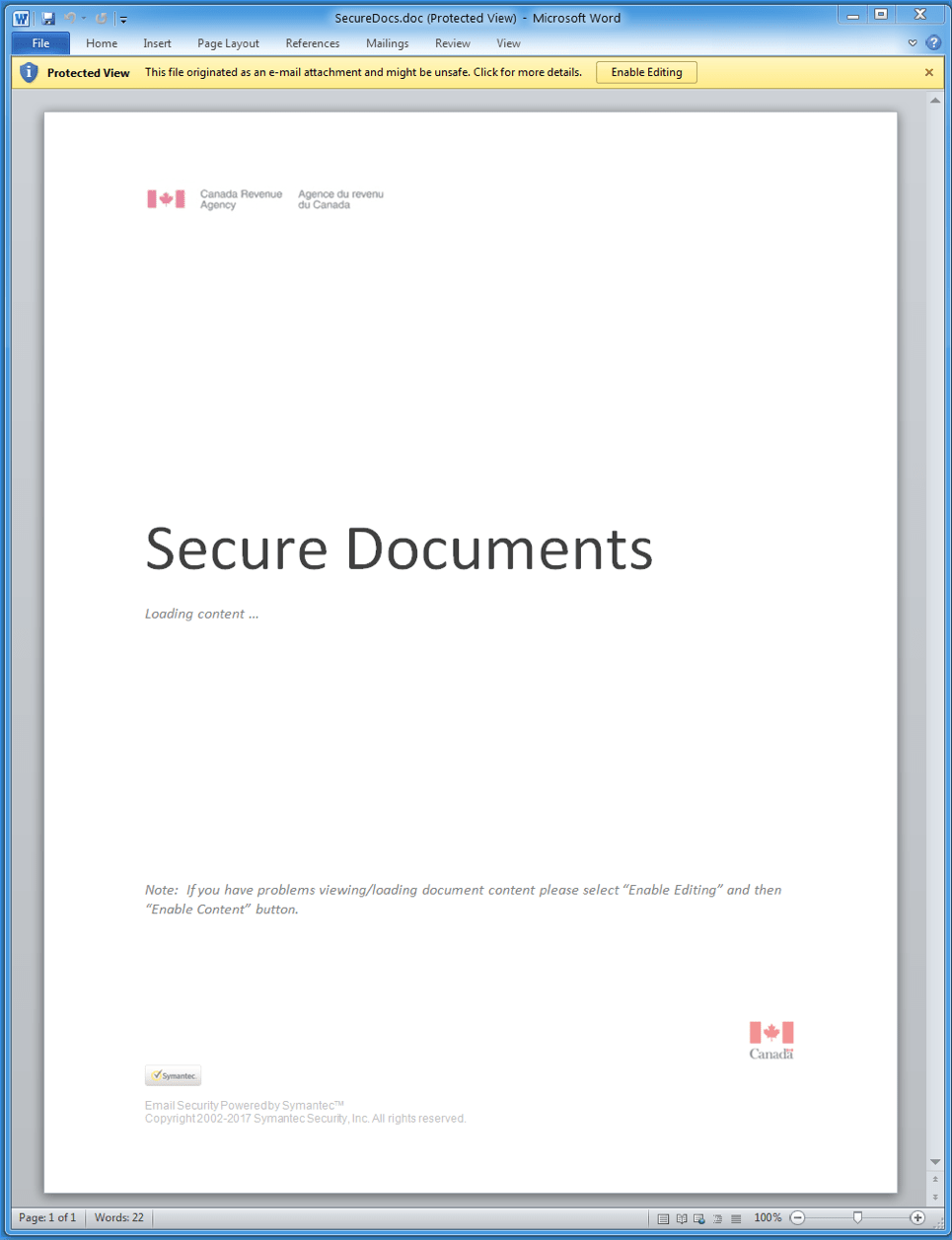
Figure 6: Lure document that downloads The Trick banking Trojan when recipients enable macros
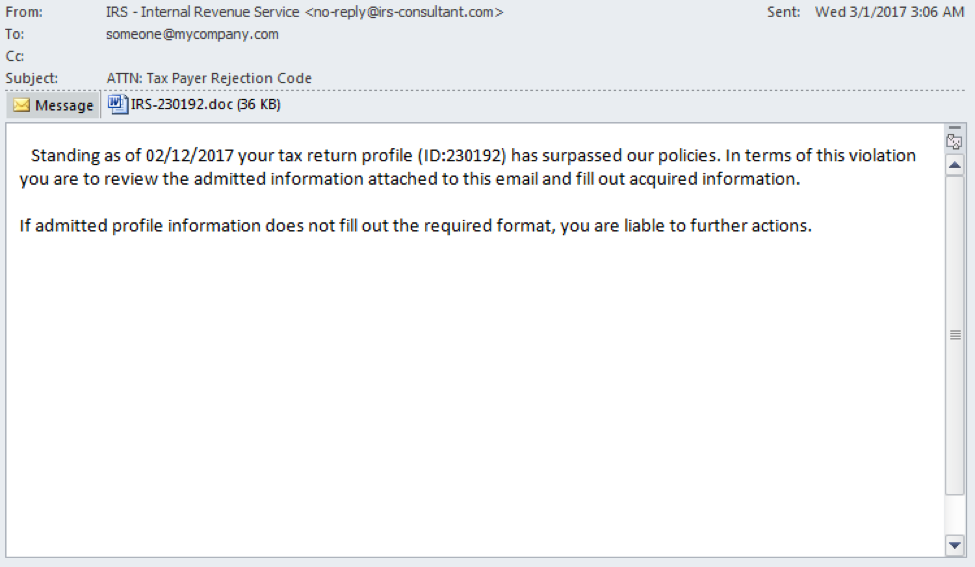
Figure 7: Email from irs-consultant.com domain
The attached document is blank, but if unsuspecting or curious recipients enable content, macros install Philadelphia ransomware, which was first documented last fall. According to our colleagues at bleepingcomputer.com, “Philadelphia is being sold as a low cost ransomware solution that allows any wannabe criminal to get an advanced ransomware campaign up and running with little expense or complexity.” Figure 8 shows the Philadelphia ransomware ransom screen.
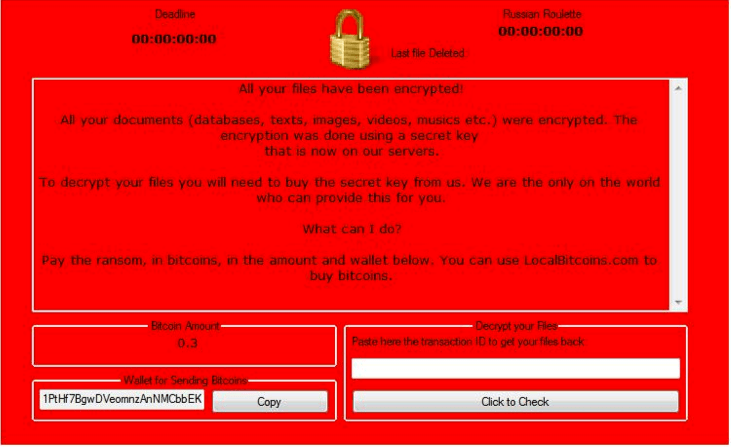
Figure 8: Philadelphia ransomware ransom screen
As these examples demonstrate, tax-themed email campaigns encapsulate the broader trends we highlighted in our 2016 Threat Report: large-scale distribution of ransomware via email, geographic targeting of banking Trojans, variation of payloads, and increasing adoption of URLs in place of document attachments.
Analysis – Phishing
Although the use of tax-related lures and documents to distribute a variety of malware payloads, including relatively new variants like Sage and The Trick, was striking, tax-themed phishing remained the most popular attack. These phishing schemes continue to employ a variety of templates and attack styles and, for the first time, adopted some of the more sophisticated approaches we have previously observed in Gmail and PayPal phishing schemes.
Figure 9 shows an example lure purporting to be from the IRS, although savvy recipients will quickly recognize that the domain is not a valid US government TLD.
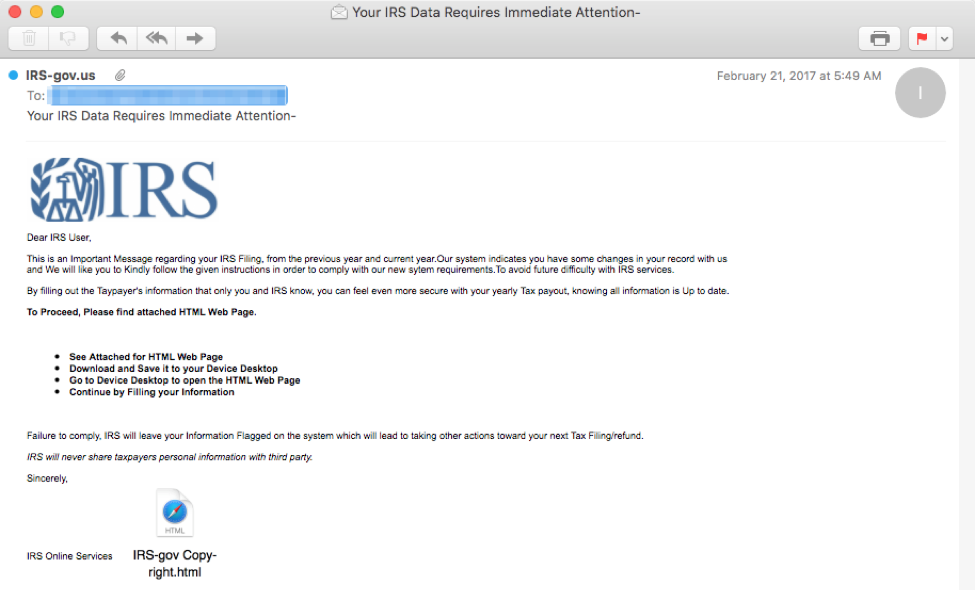
Figure 9: Lure email bearing a phishing form
The attached document “IRS-gov Copyright.html” is a phishing page (Figure 10) that sends the personal information collected in the form back to the attacker. The use of HTML attachments rather than links is not a novel approach, but in this case the stolen branding and template used accurately mirror real pages from irs.gov. The email lure, despite some grammatical errors, also effectively uses the stolen IRS branding and imparts a sufficient sense of urgency to encourage users to submit the form.
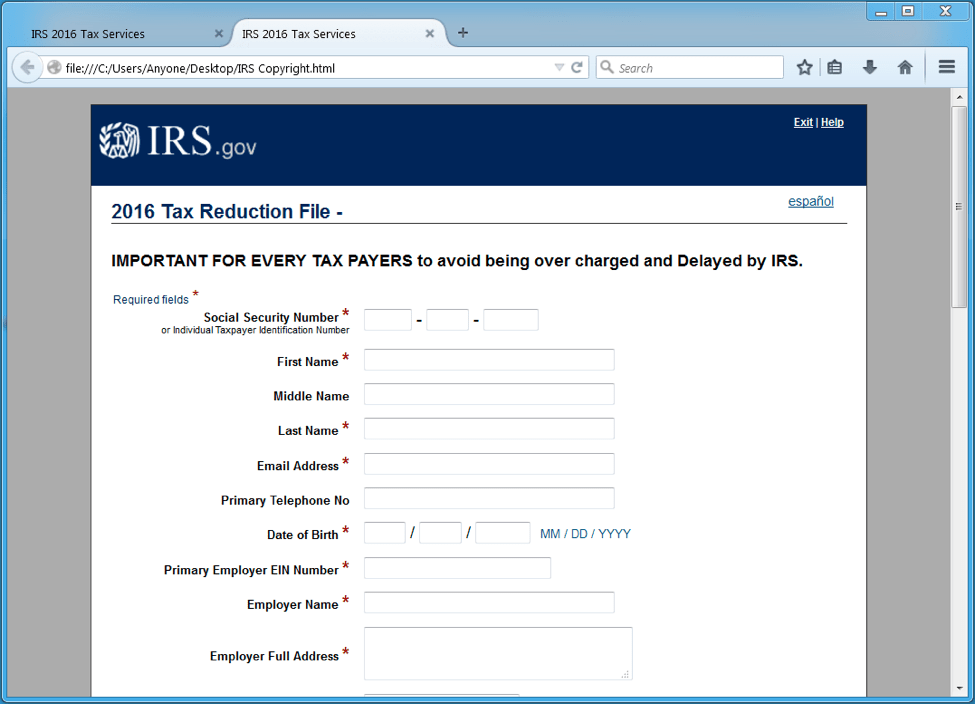
Figure 10: Phishing page attached to an IRS-themed lure email
This level of quality is not universal, however, as other recent examples feature noticeable grammatical errors and haphazard punctuation that should raise red flags for most recipients.
Many of these phishing pages are based on templates that have been in use for several years. For example, the page in Figure 11 resembles other pages collects much of the same information but has actually been used by phishing actors since 2013 when the PIN fraud attacks were first observed.
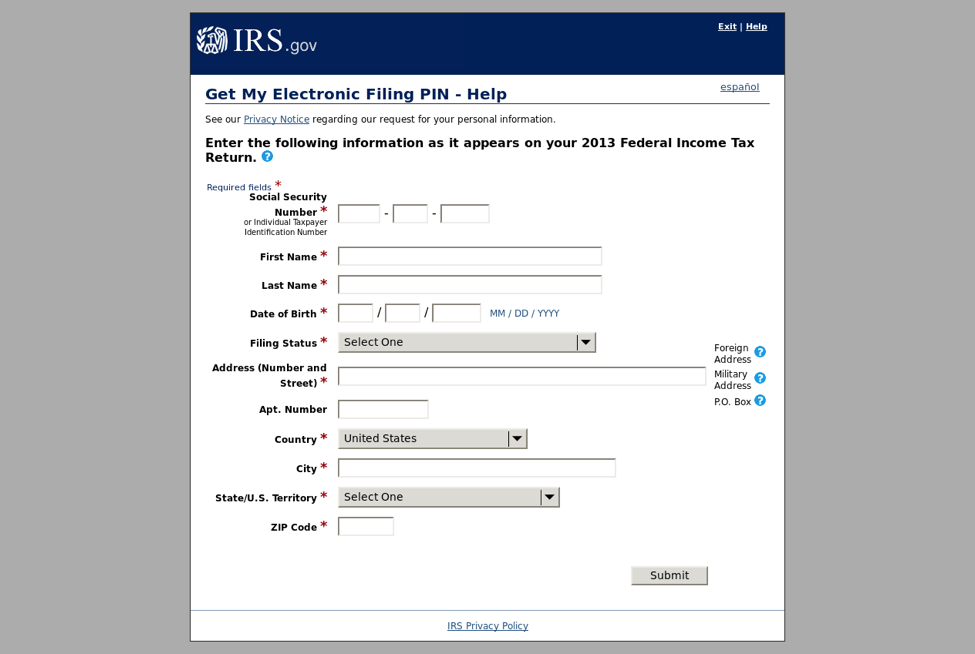
Figure 11: PIN fraud attack first used in 2013
W2 forms and requests have become a popular lure in a variety of email based scams. In another example, phishers target personal information via a form to submit federal W2 information, again lifting IRS branding and images directly from IRS.gov.
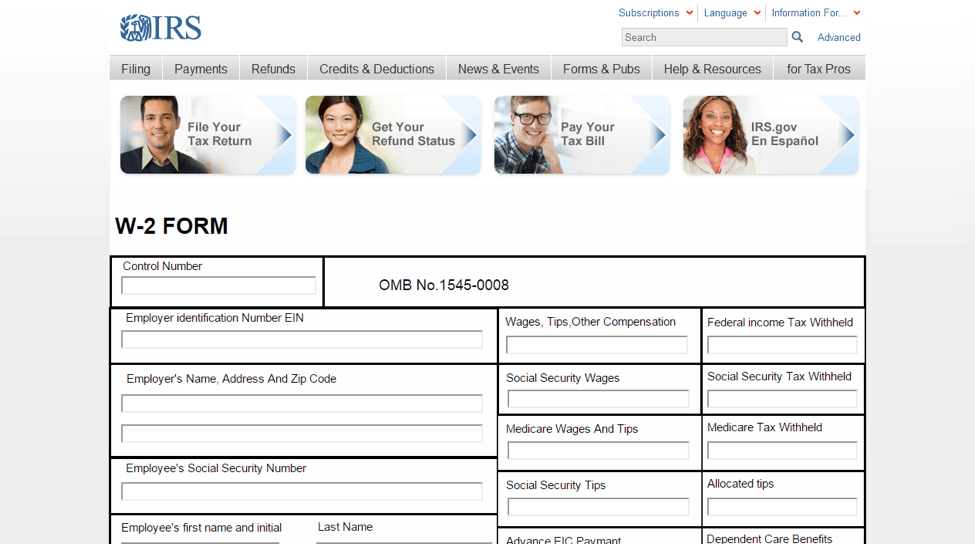
Figure 12: W2 form phishing template
We have also observed the reuse of forms capturing IRS login information that we first described last year. As noted, phishers extensively reuse templates and related code from previous campaigns, and they have little incentive to innovate extensively as long as existing templates and tools remain effective. While the templates described above continue to be used because they are still effective, we are beginning to see some of the more sophisticated techniques in tax-themed phishing that we have observed in recent PayPal and Gmail phishing campaigns. While still not at the level of these attacks, some are employing the now common technique of utilizing JavaScript AES encryption, allowing page content to bypass intrusion detection systems and many antivirus applications. Combined with fairly convincing social engineering (Figure 13), these newer templates are potentially both more effective and harder to detect.
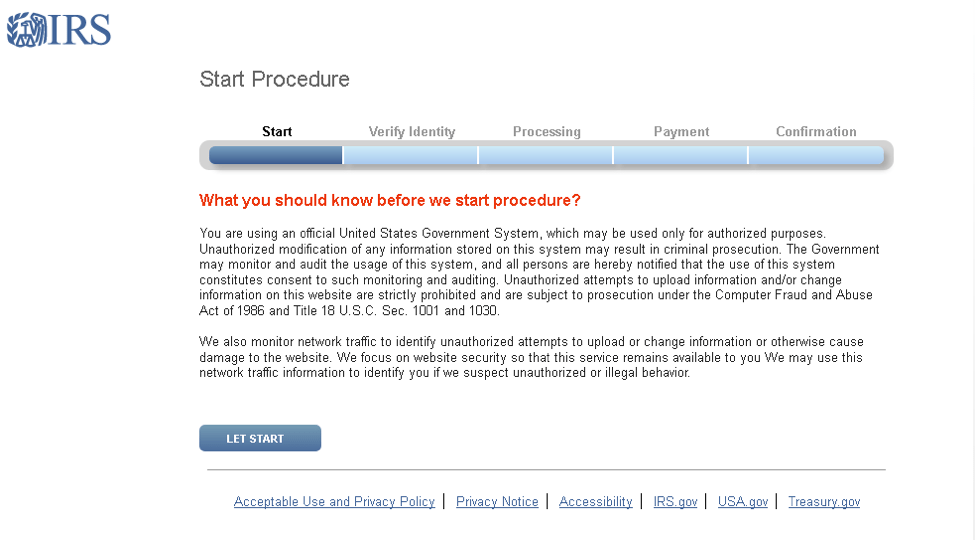
Figure 13: Fake IRS landing page leading to a template that uses JavaScript AES encryption
Clicking “LET [sic] START” leads to a page where victims begin to enter personal information (Figure 14).
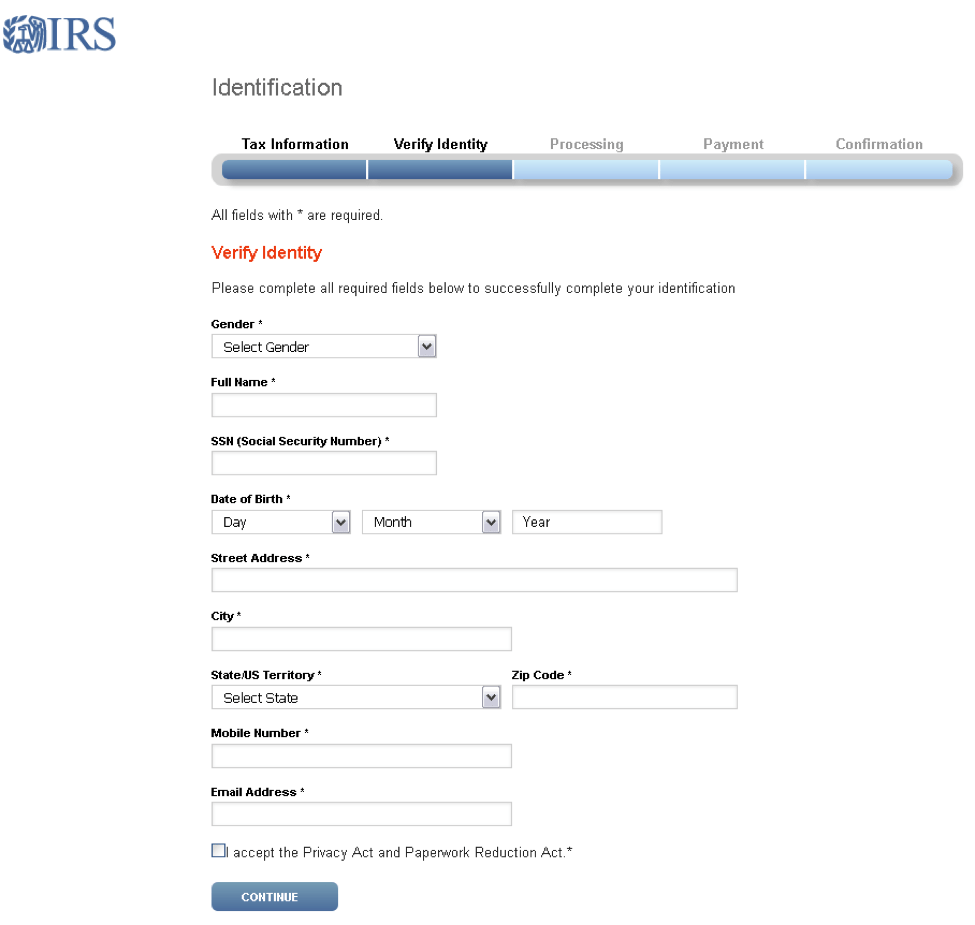
Figure 14: Phishing template utilizing JavaScript AES encryption to bypass intrusion detection systems
Another technique of recent, more sophisticated phishing campaigns is to deliver fake notices to victims while their information is "processing". Figure 15 shows an animation displayed while the page appears to retrieve victims’ most recent tax refund amounts, creating a sense of legitimacy by incorporating the small wait time users would expect from an online form that must find their information from among millions of records.
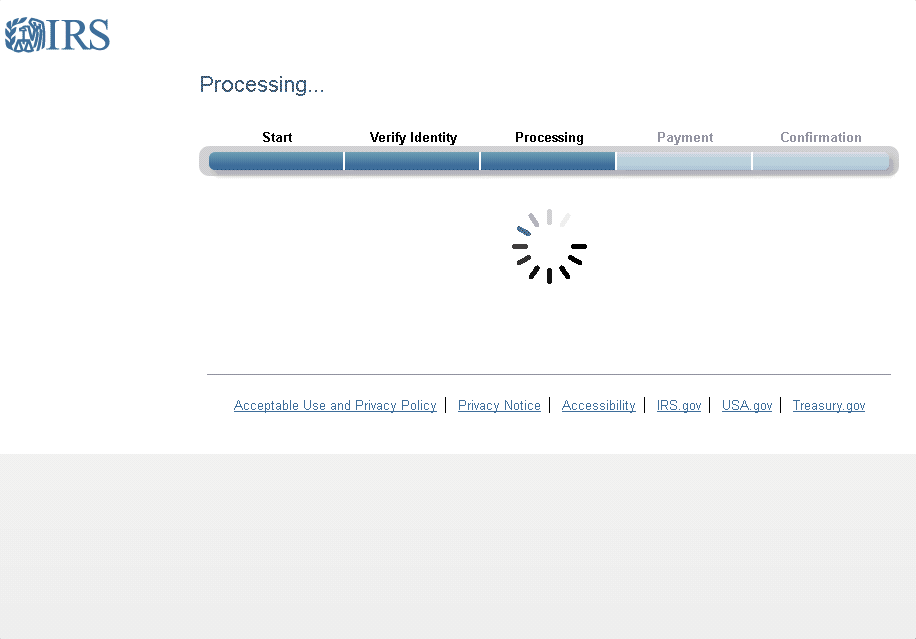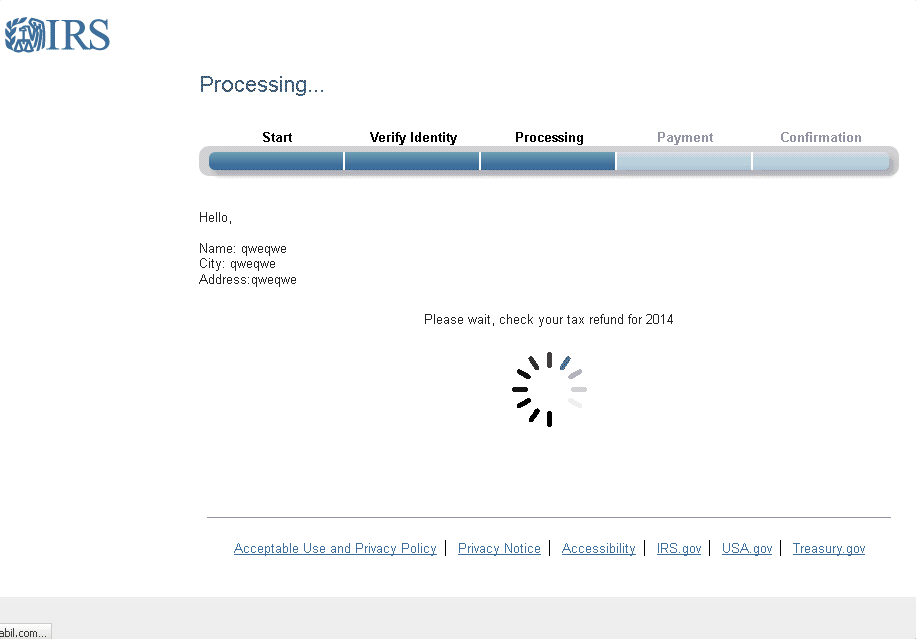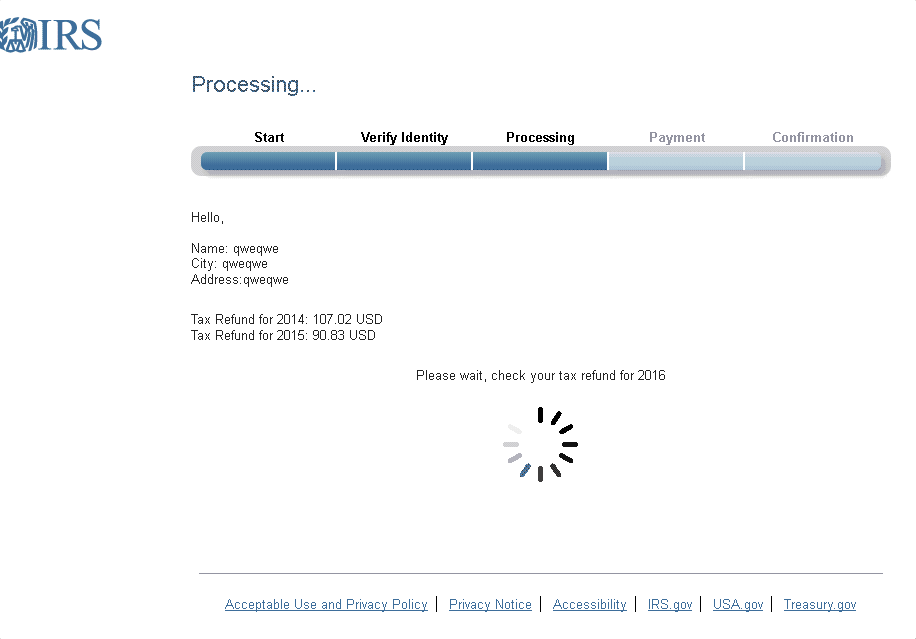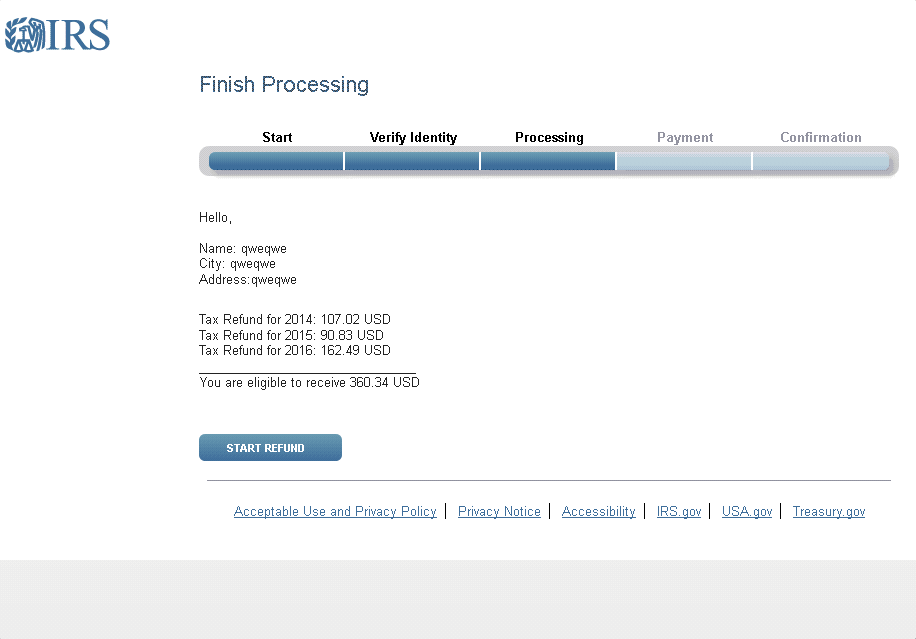
Figure 15: Animation of the “refund processing” page used in a common phishing campaign.
Starting the refund process brings victims to a page on which they can begin debit/credit card information. After recipients select their bank, a complete debit/credit card phishing page appears (Figure 16).
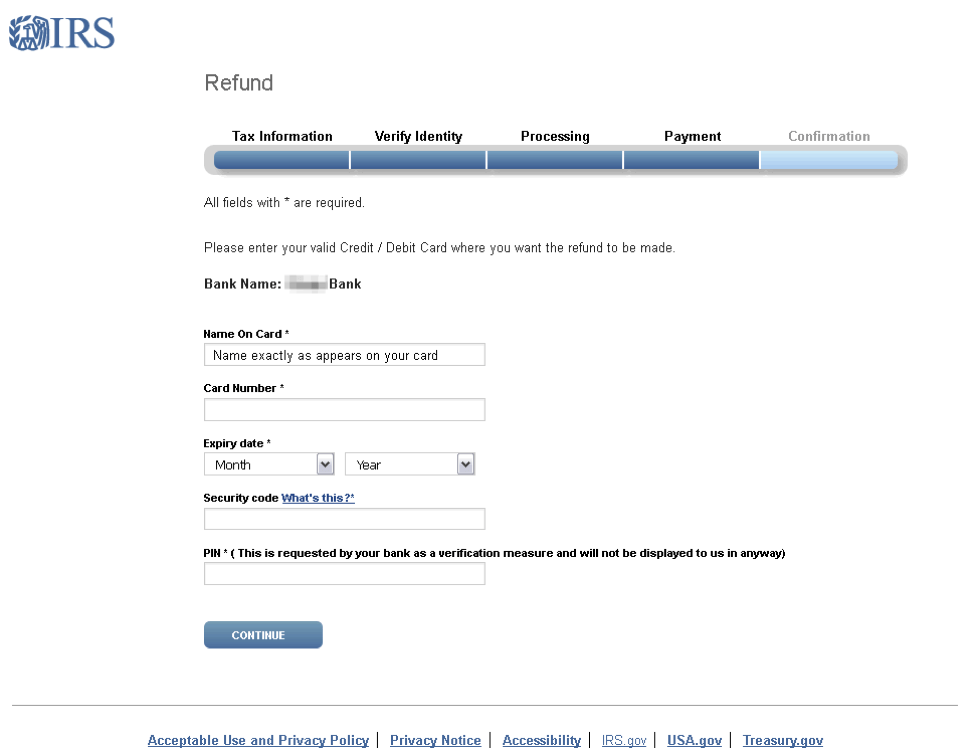
Figure 16: Credit card phishing page using an IRS-themed template
Once users complete the page, they are presented with a reassuring landing page before they are redirected to the genuine IRS website.
Brands for commercial software and services related to taxes also make popular and realistic lures. For example, we are observing multiple TurboTax templates in circulation right now. Some are single-page template, purportedly used to retrieve account information. Once the first page is complete, the template presents victims with a form requesting additional personal information.
In a nod to the prevalent use of smartphones for many tasks that previously required a PC, other templates offer support for mobile devices, (Figure 17).
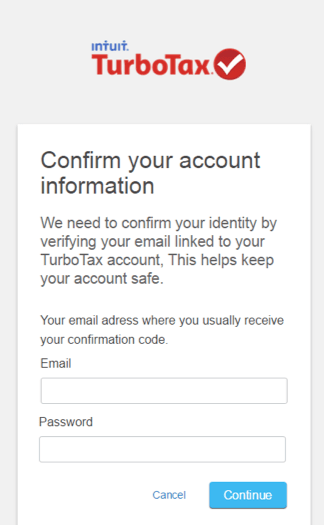
Figure 17: TurboTax template with mobile device support
Users now expect mobile tax filing applications to accept images of identifying information and W2s; many templates leverage that expectation and prompt victims to upload these documents which can then be used for identity theft.
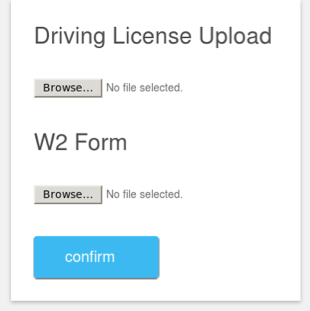
Figure 18: Mobile phishing page that prompts victims to upload identifying information. Note the use of the UK-English expression “driving license,” rather than the American-English “drivers license.”
Conclusion
This year, as in most years, tax season brings a variety of phishing schemes seeking to steal important personal and financial information. While we continue to see high degrees of code reuse and template theft, as in broader phishing, we observed a number of more sophisticated campaigns as well that borrowed techniques from phishing schemes we regularly track. Many of these campaigns targeted tax preparation services with a wider variety of templates and lures than we have observed in the past.
At the same time, tax-themed emails were used to distribute relatively new malware variants, reflecting the latest trends we have observed in the broader malware landscape. These shifts, both in techniques and payloads, demonstrated that this well-worn lure is benefitting from updates in email-based attacks. As April 15 approaches, we will continue to watch for additional threats and signs of innovation, and organizations and individuals should remain alert for increasingly sophisticated tax-theme email lures.
IRS / Turbotax ETPRO Coverage
ETPRO CURRENT_EVENTS Successful IRS Phish Sept 14 M1 - 2813012
ETPRO CURRENT_EVENTS Successful IRS Phish Sept 14 M2 - 2813013
ETPRO CURRENT_EVENTS Possible Successful Generic Phish Jan 14 - 2815781
ETPRO CURRENT_EVENTS IRS Phishing Landing Jan 15 - 2815799
ETPRO CURRENT_EVENTS Successful IRS Phish Jan 15 - 2815800
ETPRO CURRENT_EVENTS Successful IRS Phish Jan 22 - 2815926
ETPRO CURRENT_EVENTS Successful IRS Phish Jan 04 2017 - 2824211
ETPRO CURRENT_EVENTS Successful IRS Phish Jan 05 2017 - 2824234
ETPRO CURRENT_EVENTS Successful IRS Phish Jan 20 2017 - 2824570
ETPRO CURRENT_EVENTS Successful IRS Phish M1 Jan 31 2017 - 2824709
ETPRO CURRENT_EVENTS Successful IRS Phish M2 Jan 31 2017 - 2824710
ETPRO CURRENT_EVENTS Successful IRS Phish M3 Jan 31 2017 - 2824711
ETPRO CURRENT_EVENTS Successful IRS Phish M4 Jan 31 2017 - 2824712
ETPRO CURRENT_EVENTS Successful IRS Phish Feb 07 2017 - 2824813
ETPRO CURRENT_EVENTS Successful IRS Phish M1 Feb 22 2017 - 2825069
ETPRO CURRENT_EVENTS Successful IRS Phish M2 Feb 22 2017 - 2825070
ETPRO CURRENT_EVENTS Successful IRS Phish M3 Feb 22 2017 - 2825071
ETPRO CURRENT_EVENTS Successful Turbotax Phish Jan 04 2017 - 2824212
ETPRO CURRENT_EVENTS Successful Turbotax Phish Jan 31 2017 - 2824713
Indicators of Compromise (IOCs)
Dridex 1105
|
IOC |
IOC Type |
Description |
|
irsnews[.]info/Policy_Update3.doc |
URL |
URL to Dridex doc |
|
ff9e17f9692e3f34b68af54ffffb0bbadf8a371f412f0639596f456a9c4f8518 |
SHA256 |
Policy_Update3.doc |
|
86[.]110.117.205/0210.exe |
URL |
Dridex document getting payload |
|
5.101.120[.]73 |
IP |
Dridex Loader C&C |
|
188.226.154[.]38 |
IP |
Dridex Loader C&C |
|
91.121.30[.]169 |
IP |
Dridex Loader C&C |
|
51.254.129[.]140 |
IP |
Dridex Loader C&C |
|
185.129.148[.]246 |
IP |
Dridex Loader C&C |
|
80.90.203[.]245 |
IP |
Dridex Worker C&C |
|
216.126.225[.]189 |
IP |
Dridex Injects C&C |
|
173.196.157[.]250 |
IP |
Dridex Injects C&C |
Sage - Attachment
|
IOC |
IOC Type |
Description |
|
016358afcd1e0c6ed8efb490e6ad38724048bf81cc0620de9c4b39f6d81d14ba |
SHA256 |
Attachment |
|
hxxp://tiranainternational[.]com/hoteltiranacom/joomla_style[.]jpg |
URL |
Document payload |
|
mbfce24rgn65bx3g.pbt2ac[.]com |
Hostname |
Sage C&C |
|
mbfce24rgn65bx3g.9dpnlu2[.]com |
Hostname |
Sage C&C |
|
7gie6ffnkrjykggd[.]onion |
Domain |
Sage payment |
|
7gie6ffnkrjykggd.pbt2ac[.]com |
Hostname |
Sage payment |
|
7gie6ffnkrjykggd.9dpnlu2[.]com |
Hostname |
Sage payment |
Sage - URL
|
IOC |
IOC Type |
Description |
|
mangosdemadera[.]com/wp-includes/info.php |
URL |
URL in email |
|
29138552aee9e03bbc5b426c8b36b5f5ce87c2034ee58c9578aaa6f0f6571d3a |
SHA256 |
Information.zip downloaded from initial URL |
|
29138552aee9e03bbc5b426c8b36b5f5ce87c2034ee58c9578aaa6f0f6571d3a |
SHA256 |
info_344.js inside information.zip |
|
hxxp://taxinginfo.trade/file[.]jpg |
URL |
JavaScript payload |
|
mbfce24rgn65bx3g.io23zc[.]com |
Hostname |
Sage C&C |
LuminosityLink
|
IOC |
IOC Type |
Description |
|
9e8044e15bb15c01a3d9b4c917736d25301e3bc2db7b4a214d0461418b829a6b |
SHA256 |
Attachment |
The Trick
|
IOC |
IOC Type |
Description |
|
fcdfe2b640fd560c2c72becd2dc27e004cd91638a47ce5845b5ec3b338c0e190 |
SHA256 |
Attachment |
Philadelphia - Attachment
|
IOC |
IOC Type |
Description |
|
7bf232cf3fd70906d8fa3a7dc9569d1d67ebb72303a710c3f55ce0564e250231 |
SHA256 |
Attachment |
|
hxxp://worldprocessing.co/philly-germany[.]exe |
URL |
Document payload |
|
hxxp://apocalipsisz.es/bridge[.]php |
Domain |
Philadelphia C&C |
|
hxxp://clearvisionwear.us/wp/bridge[.]php |
Domain |
Philadelphia C&C |
|
hxxp://iigenesis.com/bridge[.]php |
Domain |
Philadelphia C&C |
|
hxxp://philipjonescoachhire.com/bridge[.]php |
Domain |
Philadelphia C&C |
2013 phish page
|
IOC |
IOC Type |
Description |
|
hxxp://weareagenius.com/wp-content/plugins/gravityforms/fonts/irs=gov/confirm.mem/start[.]php |
SHA256 |
Phishing landing page |
W2 phish page
|
IOC |
IOC Type |
Description |
|
hxxp://www.tashconferences[.]com/new/w2-form/ |
SHA256 |
Phishing landing page |
AES phish page
|
IOC |
IOC Type |
Description |
|
hxxp://www.tax-refund-irs-gov.radyobabil[.]com/ |
SHA256 |
Phishing landing page |
TurboTax mobile
|
IOC |
IOC Type |
Description |
|
hxxp://tapeunlimited[.]com/js/zip/index/ |
SHA256 |
Phishing landing page |











