Business email compromise (BEC) and email account compromise (EAC)—a collective $26B problem—are issues that organizations of all sizes, in all industries, must address.
Our “Combatting BEC and EAC” blog series dives into how you can stop these threats at your organization. Each post focuses on one of seven key steps. We tackle the second in this blog post: authenticating email with the Domain-based Message Authentication Reporting and Conformance (DMARC) standard.
Email-Based Identity Deception
As we’ve already explored in this series, BEC attacks are perpetrated when attackers spoof a trusted identity to lure their targets into providing sensitive information and rerouting funds. Since these attacks rely on publicly available research and social engineering rather than malicious links or attachments, they can be especially hard to detect using traditional tools and methods. While these attacks have become more refined and targeted in recent years, it’s essential to protect employees, customers and business partners from attacks that utilize an organization’s trusted domains.
Why DMARC Works
The DMARC standard allows organizations to ensure that only legitimate senders are using their trusted domains to message employees, customers and business partners. Using a combination of Sender Policy Framework SPF) and Domain Keys Identified Mail (DKIM) alignment, organizations can effectively prevent domain spoofing attacks.
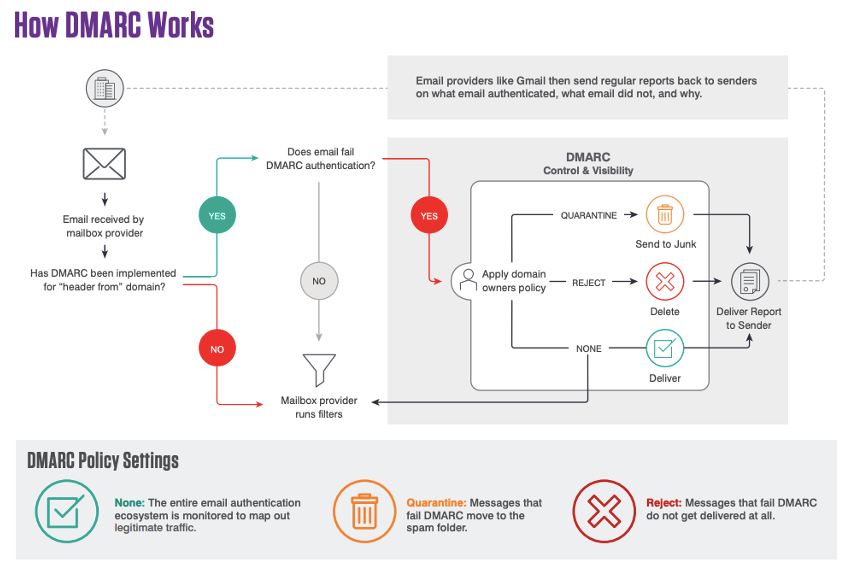
DMARC is an incredibly effective solution because it is completely deterministic—any sender using trusted domains that don’t meet the standard will be blocked by a receiver enforcing DMARC. And because this protection takes place at the domain level, messages will be blocked regardless of their payload, whether it’s a message containing a malicious time-delayed URL, an attachment, or a BEC attack that has no malicious content at all. Because of this, organizations can take back control of their domains on an internet-wide basis, and ensure that their suppliers, customers and employees can trust emails from their domains.
While adoption is growing, many organizations aren’t taking advantage of this standard. As of September 2020, 51% of the Global 2000 do not have a DMARC policy. Further, 86% of the Global 2000 have not implemented a “reject” policy, the strictest and recommended level of DMARC protection, which prevents fraudulent emails from reaching their intended target.
The adoption problem reaches across industries. In an examination of the member airlines of the International Air Transport Association (IATA), Proofpoint found that 61% of these organizations do not have a published DMARC record. When Proofpoint researchers investigated DMARC adoption among U.S. state governments, they found that 44% do not have a published DMARC record. Why is there such a pervasive gap in DMARC adoption? Implementation is complex.
Implementing DMARC Is Complex
While DMARC is an incredibly effective tool for organizations to use in the fight against BEC, it is a complex journey that requires a large amount of effort and resources to implement on your own.
A lackluster implementation can cause teams to block a significant amount of legitimate mail and senders, interrupting the normal flow of business.
Proofpoint’s Email Fraud Defense consultants can ensure that email authentication is implemented properly. They have years of experience and have implemented thousands of DMARC records for organizations of all sizes in all industries. From working with third-party senders and implementing project plans to troubleshooting common alignment problems, they are with organizations during every step of the way.
Email Fraud Defense offers the only true secure email gateway integration in the industry with Proofpoint Email Protection. Because of this, users are able to have full visibility into all messages coming into and going out of their organization, enabling a much more accurate and faster implementation. This also speeds up inbound DMARC enforcement to protect an organization’s employees as quickly and effectively as possible.
In addition to this, Email Fraud Defense provides even more tools to help against additional imposter tactics, such as full lookalike domain protection.
To find out if your organization is adequately protected from BEC and EAC attacks, take our complimentary assessment here.











