About the Series:
Business Email Compromise (BEC) and Email Account Compromise (EAC) afflict businesses of all sizes across every industry. More money is lost to this type of attack than any other cybercriminal activity. The FBI reported that from June 2016 to June 2019, companies reported $26.2B in losses. And in 2019 alone, BEC scams accounted for more than half of all cybercrime losses—an estimated $1.77B. The average loss per BEC incident in 2019 was $74,723.
An indication of how pervasive a problem BEC/EAC is: Proofpoint blocks over 15,000 BEC/imposter messages a business day or nearly 4 million messages a year.
In this series, we cover BEC/EAC attack types that Proofpoint considers the most important for a business to be aware of. In each of these posts, we explain what the attack is and how it works so that you can better understand these BEC/EAC attacks and can better protect yourself. In this post, we focus on BEC/EAC payroll diversion scams.
What Are BEC Payroll Diversion Scams
BEC payroll diversion scams are similar to other BEC attacks by relying on impersonation and social engineering to convince the target victim to send money to the attackers. In this case, the attackers target the payroll process of a company or organization and attempt to redirect legitimate payroll payments from their intended destination accounts to accounts under the attacker’s control. This is different than gift card scams in that the employee being impersonated is typically not a VIP, whereas in a gift card attack the impersonated employee is typically a CEO or other high-level executive. To better protect against these kinds of scams, it is critical that security solutions are capable of using more than just a pre-defined list of executives to detect impostor email.
BEC payroll diversion scams are by necessity very focused in their targeting. To succeed, these scams must correctly identify someone in the HR or payroll department to make changes to an employee’s direct deposit information.
To understand the scope of the problem, the FBI’s IC3 reported that the dollar loss associated with payroll diversion increased 815% between Jan 1, 2018 and June 30, 2019. Proofpoint has seen and blocked more than 35,000 payroll diversion scams protecting US$2.2 M per day in the first half of 2020. Our research shows that the Monday and Tuesday are the most popular days of the week for these scams, the second and last weeks of the month are the most popular weeks for these scams, and “Direct Deposit” is the most popular lure.
How BEC Payroll Diversion Scams Work
The crux of a successful BEC payroll diversion attack is the redirection of payroll funds from their intended, legitimate destination to an account under the attacker’s control. Figure 1 shows the steps in a typical BEC payroll diversion attack.
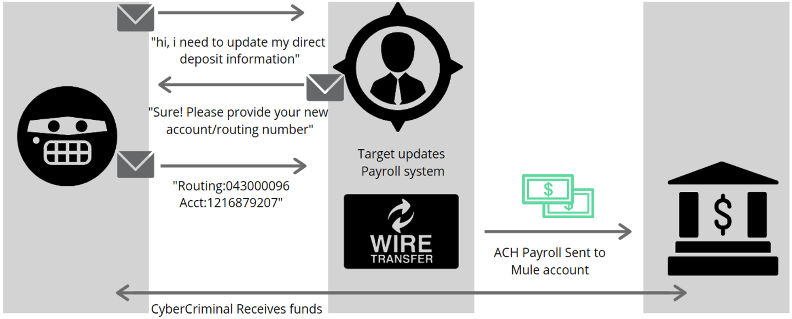
Figure 1 Stages of a BEC Payroll Redirection Attack
BEC payroll diversion scams rely heavily on intelligence gathering. A successful BEC payroll diversion attack requires the attackers identify the correct target for their attack and demonstrate credible familiarity with the payroll process so as not to arouse suspicion. Both of these require the attackers invest time and energy into extensive reconnaissance and intelligence gathering prior to launching their attack.
Unfortunately, this type of intelligence can be gathered from publicly available sources such as a company’s website or alternatively LinkedIn.
Like many BEC attacks, payroll diversion scams rely heavily on a combination of impersonation, social engineering, and urgency.
When attackers launch a BEC payroll diversion attack, they try to convince someone at the target company or organization who can make changes to the payroll disbursement system that they are the employee they claim to be or someone authorized by the employee to make changes to their payroll information. In these exchanges, they will seek to convince their target to change the destination of payroll disbursements for the employee they’re impersonating to an account under their control. Depending on the sophistication of the threat actor, they may include a reason why reverting to a paper check sent in the physical mail is not possible.
This is used as a tactic to circumvent secondary financial controls for account information updates.
Figure 2 shows an example of the final email in the exchange used in BEC payroll diversion scams. It’s worth noting that this email has no malicious links or attachments: it relies purely on social engineering in a scenario that’s set up over multiple seemingly-legitimate emails.
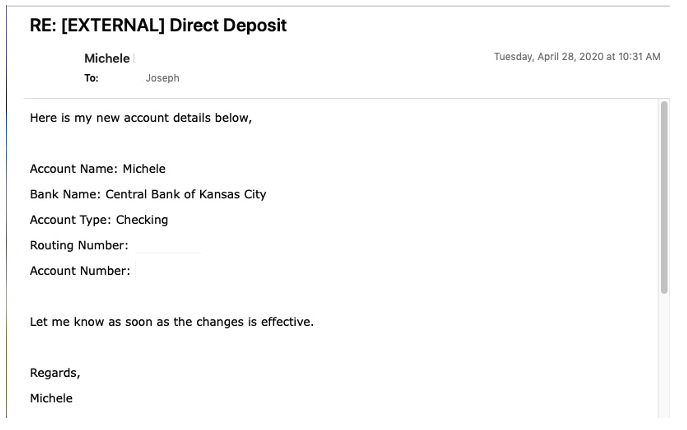
Figure 2 Example of False Email Requesting Changes for BEC Payroll Diversion Attack
In a successful attack, the target victim will make the changes and the issue will be closed. Ideally for the attacker, the issue will be closed with little notice by the target victim. In this case, making the attack look as much “business as usual” as possible is key to a successful attack.
If the attack is successful and the changes are made, the final step is for the money to be transferred into an account under the attacker’s control at which point the attacker can retrieve the funds. This is important to note because the attack may take up to two weeks to incur financial loss after the payment instructions have been successfully updated. It’s worth noting that because of this two week delay, BEC payroll diversion attackers tend to prefer to levy their scams in the second or fourth week of the month. The FBI notes that many times the target accounts are actually pre-paid card accounts, which enables the attackers to quickly utilize the diverted funds.
How Proofpoint Protects Against BEC/EAC Payroll Diversion Scams
Proofpoint provides a people-centric multi-layered solution to help organizations protect against payroll diversion scams. First, as part of Proofpoint Email Protection, Impostor Classifier dynamically analyzes a wide range of message attributes, including the sender/receiver relationship, header information, domain, and message body to determine if a message is a BEC message. Proofpoint Email Protection delivers unique value to Proofpoint customers in the following ways:
- Analyzing and blocking 15,000 BEC messages per day globally gives each Proofpoint customer an unfair advantage as Impostor Classifier has observed countless payroll diversion attacks to compare message body contents against.
- Being in mail flow allows Proofpoint’s BEC detectors to understand the sender/target relationship, which is a critical detection ingredient.
- Detecting impostor email isn’t limited to a pre-defined list of executives or VIPs. Because payroll diversion attacks do not typically target VIPs, preventing these attacks requires inspecting all messages. Impostor Classifier inspects all messages not just messages for VIPs.
Second, in the event there isn’t enough data to identify a message as an impostor message, Proofpoint enables administrators to alert the user that the message is suspicious using email warning tags. These visual cues help users take extra precautions with the email in question. In addition to the impersonated sender alert, Proofpoint’s email warning tags support other situations including external sender, new sender and newly registered domains.
Last, but not least, Proofpoint provides security awareness training to help organizations turn users into part of their defense. Because BEC payroll diversion scams rely on social engineering to trick end users, it’s critical to train employees. With Proofpoint you can use BEC/EAC threat data to tailor that training to your specific threats. For example, you can plan training about BEC payroll diversion scams for the individuals involved in your payroll business process during the second and fourth week of the month if that’s borne out by your specific threat data. Not only can Proofpoint help organizations teach users to spot BEC payroll diversion scams, but we can also enable those users to report those messages as suspicious and automate the investigation and remediation of those reported messages to their internal abuse mailbox.
Are You Protected?
BEC payroll diversion scams are a growing form of BEC attacks out there. However, these scams are also some of the most lucrative with Proofpoint stopping an estimated $2.2M per day in BEC payroll diversion scams. These scams are also highly targeted and require detailed knowledge to be successful. These two points are good news for defenders because it provides clear direction on what you can do to help better protect against these scams. One, you can ensure that people who have the ability to change payroll disbursement information are aware of the risks and receive additional training and protection. Two, you can work to ensure that critical information regarding payroll policies and procedures are not publicly available in a way that can facilitate these kinds of scams.
One of the most important things you can do to help protect against BEC/EAC payroll diversion scams is to understand how prepared your organization is to combat them. Find out by taking our BEC/EAC readiness assessment here.











