If you’re a security professional at a company that processes credit card and debit card payments, then you’re no doubt familiar with the Payment Card Industry Data Security Standards (PCI DSS) and all that these requirements entail.
With the PCI DSS V4.0 release last year, it’s time to start thinking about how to meet the anti-phishing mechanisms requirement that will be mandatory in March 2025.
In this blog, we’ll cover what you should know so you’ll be ready to meet the requirements of V4.0.
Why the PCI DSS were created
Prior to the PCI DSS, the payment card industry lacked consistent security measures, which led to rampant security breaches, data theft and fraud. Individuals and businesses lost money, and the privacy and security of cardholders were compromised. Public trust in the payment card industry also took a hit.
In 2004, major stakeholders, including Visa, Mastercard, Discover and American Express, formed the Payment Card Industry Security Standards Council (PCI SSC) to remedy this situation. The council set out to define a unified set of security standards and best practices for the industry to follow. From that focused effort, the PCI DSS were born.
The council’s overall objective is to protect cardholder data and maintain the integrity of the payment card industry. Compliance with the PCI DSS is critical for all businesses that handle payment card information, including merchants, financial institutions and service providers. Failure to meet these guidelines can have significant consequences.
Anti-phishing mechanisms in PCI DSS V4.0 regulations and testing
Section 5.4 of PCI DSS V4.0 states that anti-phishing mechanisms must be in place to protect your business, suppliers and financial partners against phishing attacks. Requirement 5.4.1 mandates the implementation of processes and automated mechanisms to detect and protect personnel against phishing attacks.
Notably, this requirement is not satisfied by security awareness training alone, which means that other methods will be needed when this requirement stops being noted as a best practice and becomes mandatory in March 2025.
With this mandate, PCI DSS auditors will be looking for companies to have anti-spoofing controls such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting & Conformance (DMARC). In the next section, we take a closer look at what these controls are and how they help to increase security.
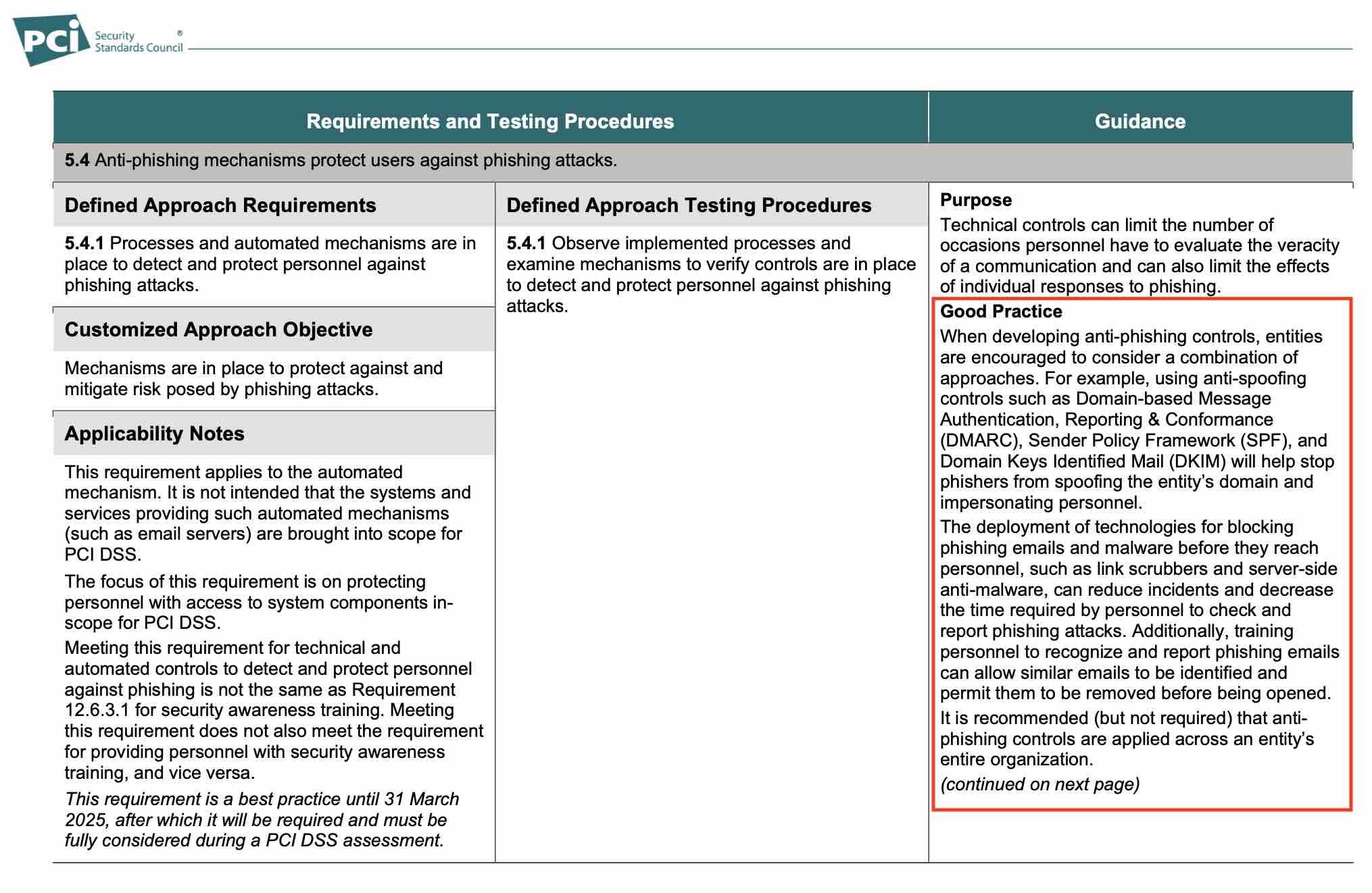 Overview of PCI SSC requirements and testing procedures and guidance.
Overview of PCI SSC requirements and testing procedures and guidance.
What to know about email authentication
Here's what you should know about email authentication.
Sender Policy Framework (SPF)
SPF is an email authentication method. It helps prevent email spoofing by verifying that the sending mail server IP address is authorized to send emails on behalf of a specific domain. Without SPF, bad actors can send malicious emails claiming to be from an entity they are not.
Depending on your level of experience and familiarity with email infrastructure, properly configuring your SPF record could be a complex task. It involves configuring DNS records to ensure that your mail servers are correctly allowed to send.
Even if you succeed at creating a SPF record, you can create opportunities for malicious actors to examine and exploit your infrastructure and software-as-a-service systems. This can occur when the SPF record is:
- Overly permissive
- Not obfuscated
- Not actively managed
DomainKeys Identified Mail (DKIM)
On the other end of the email exchange, DKIM allows a recipient’s mail server to verify the authenticity of the sender and ensure it has not been altered in transit by adding a digital signature (key) to outgoing emails. Properly setting up DKIM includes:
- Generating public and private keys
- Configuring your mail server with the private key
- Publishing a DKIM record with the corresponding public key
Setting up DKIM is often more complex than creating an SPF record. And because keys must be rotated semi-regularly, DKIM can be more troublesome to maintain.
The DMARC connection
SPF and DKIM are prerequisites for implementing DMARC and determining what action to take if messages fail authentication. It is critical to understand the impact of setting a DMARC policy as it could have significant implications on email delivery.
DMARC policies include:
- “none” (“do nothing” if a message fails both SPF and DKIM verification)
- “quarantine” (“quarantine the message” if a message fails both SPF and DKIM verification)
- “reject” (“reject the message” if a message fails both SPF and DKIM verification)
DMARC also provides detailed reporting about the successes and failures of handling emails claiming to be from your domain. These reports include information about the email authentication results (whether they passed or failed). And you can use them to monitor the health of your overall email environment.
These reports will help you to identify the unauthorized use of your domains. It is therefore essential for your business to have the technology in place to receive, process and analyze both DMARC aggregate and forensic reports.
Even without PCI DSS requirements, implementing DMARC with a strong “reject” policy is a best practice that every company should adopt. But all too often, concerns about the complexity of implementation, lack of resources or simply not knowing where to start have prevented many businesses from starting their DMARC journey.
Will you be ready to meet the requirement?
March 2025 may sound like a long way away, but it will be here before you know it. Unless you already have SPF, DKIM and DMARC with a “reject” policy in place, you need to start the planning process now.
Depending on the complexity of your environment, implementation could be significant. If you are not a DMARC expert, it can take a lot of time to work out the kinks related to blocking the right emails and letting valid emails through.
Keep in mind, more than just technical planning is involved. There should also be budgeting to make sure that funding will be there in 2025 when you need it.
Good news: There’s expert support available
Proofpoint is an industry leader in email security and has partnered with companies of all sizes and industries to help them reach their p=reject DMARC objective.
Our world-class consultants can guide you through each step of implementing DMARC. Starting with a customized project plan, they can help you identify all legitimate senders and make sure they authenticate properly. They can also recommend and prioritize tasks and publish a DMARC reject policy that won’t block valid email.
Since Proofpoint is the only security vendor that provides true integration between email authentication and an industry-leading secure email gateway, we can help mitigate the risks of impostor threats by enforcing DMARC on inbound traffic. This integration ensures that your business can meet the PCI DSS V4.0 anti-phishing requirements.
Don’t wait until the last minute to get started on your DMARC journey. You don’t know what issues you may need to overcome—and you don’t want to risk missing the deadline. Reach out to Proofpoint today to learn how we can help you meet PCI DSS requirements, increase your overall security posture and break the attack chain.











