Microsoft – The Threat Actor’s Playground. A Blog Series.
This post is an ongoing blog series about the different types of people-centric email attacks Microsoft misses. These attacks cost organisations millions of dollars every year in losses and cause frustration for information security teams and users alike due to outdated detection technologies and the inherent limitations of Microsoft email security.
In this series, you can expect to learn more about Microsoft missing various types of account compromise attacks, which we’ll explore in-depth and provide recent examples of:
- Business email compromise (BEC)
- Ransomware
- Supplier fraud
- Account compromise
- Weaponised file sharing
Subscribe to our blog at the bottom of this page to stay up to date on these misses that may impact your organisation. Also, use our Threat Assessment process to better understand your organisation’s risks.
Microsoft account compromise attacks that were missed
Account compromise attacks are a common tactic for malicious actors. “The 2021 Human Factor Report” from Proofpoint notes that credential theft accounts for about two-thirds of attacks. And according to Verizon’s “Data Breach Investigations Report”, 60% of attacks involve credentials.
Other types of attacks can use malware, like keyloggers, to steal credentials from users or even socially engineer users (e.g., consent grants) to gain access to their accounts.
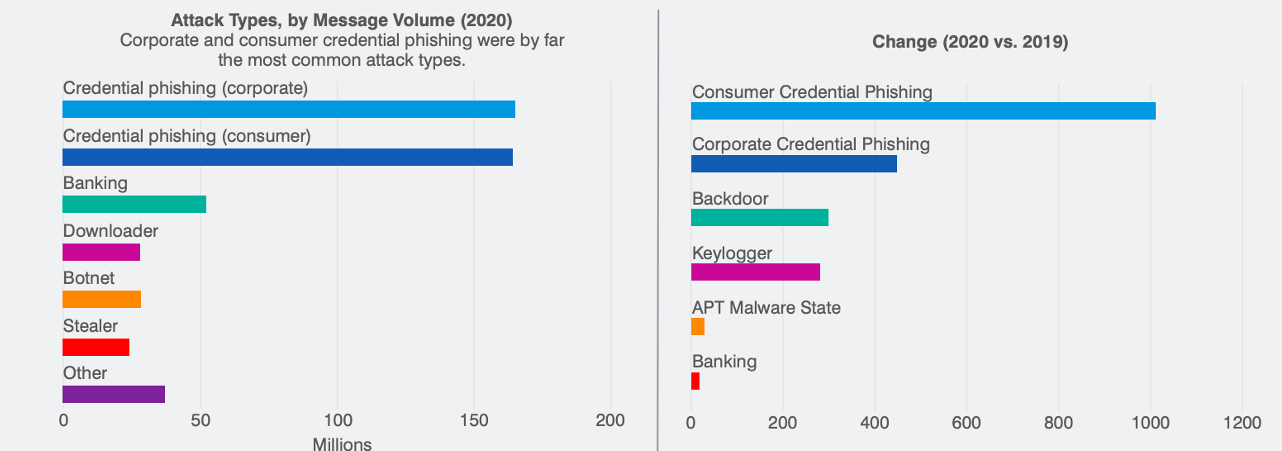
Figure 1. Credential phishing by message volume from “The Human Factor 2021 Report”.
Account compromise attacks can hurt organisations’ bottom line. According to the “2021 Ponemon Report: Cost of Cloud Compromise and Shadow IT”, cloud account compromises cost organisations $6.2 million annually, on average.
With more and more organisations increasing their use of cloud applications, the risk of account compromise attacks is growing. It’s already high. Consider the research Proofpoint conducted in 2020 on account compromises, which found that:
- 95% of organisations are targeted for account compromise
- 52% of organisations have users compromised
- 32% of organisations have files manipulated by attackers
In a month’s time frame, Proofpoint detected, in just a limited data set of rapid risk assessments, more than 112,000 credential theft, keylogger and downloader threats that had slipped past Microsoft email security perimeter defences.
At one large software firm with almost 15,000 employees, more than 13,000 credential threats were delivered to employees. At a smaller insurance firm with fewer than 1,000 employees, almost 1,800 threats were delivered to users. That’s almost two threats per user, in just one month. And at an international media organisation with 2,000 employees, more than 25,000 credential threats were delivered to employees, overwhelming internal IT security resources.
Below are examples of account compromise and credential theft attack types missed by Microsoft that were discovered during recent Proofpoint rapid risk assessments.
Microsoft 365 credential harvest attack overview:
We see many credential threats using the same tactic: imitating Microsoft to get past Microsoft perimeter defences. Even with multifactor authentication in place, attackers are becoming increasingly more adept at compromising email accounts, leading to extremely dangerous email account compromise (EAC) attacks, where attackers can assume the corporate identity of victims.
Here’s one example of a Microsoft attack that was missed:
- Environment: Microsoft 365
- Threat Category: URL-Based
- Attack Type: Credential Theft
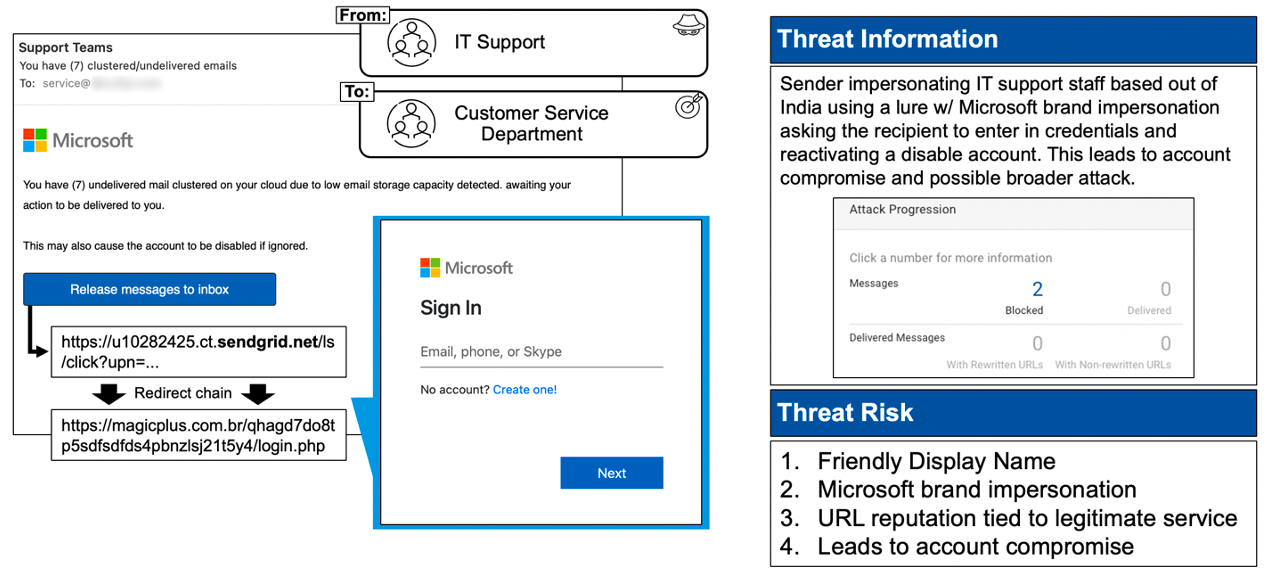
- Target: Customer Service Department
Figure 2. Credential theft attack, missed by Microsoft, which was attempting to steal Microsoft Office 365 credentials and compromise the account.
The anatomy of the attack:
This credential theft attack bypassed native Microsoft email security controls. The impostor, purporting to be IT support staff, used a friendly display name and Microsoft brand impersonation in an attempt to compromise the victim’s account. Using a legitimate URL (in this case, sendgrid.net) is a common tactic that Proofpoint sees bad actors using to bypass URL scanning defences.
In fact, over 50% of URLs that Proofpoint observes from malicious actors use a SharePoint, OneDrive or other file-sharing “legitimate” site. That’s why Proofpoint always predictively sandboxes these threats to determine whether they’re malicious and, if they are, prevents them from being delivered to users.
In a proof of concept, Proofpoint detected this credential harvesting attempt and would have stopped it from being activated.
Account compromise attack overview:
Not all attacks go after Microsoft 365 accounts. With a growing number of cloud accounts, attackers frequently target accounts that may have less protection than Microsoft 365. Malicious actors, such as those in the example below, can use partners’ accounts that are already compromised to improve the likelihood of victims activating an attack.
Here’s an example of a Microsoft attack that was missed:
- Environment: Microsoft 365
- Threat Category: Attachment-Based, Containing URL-Based Threat
- Attack Type: Credential Phishing
- Target: School Counselors and Administrators
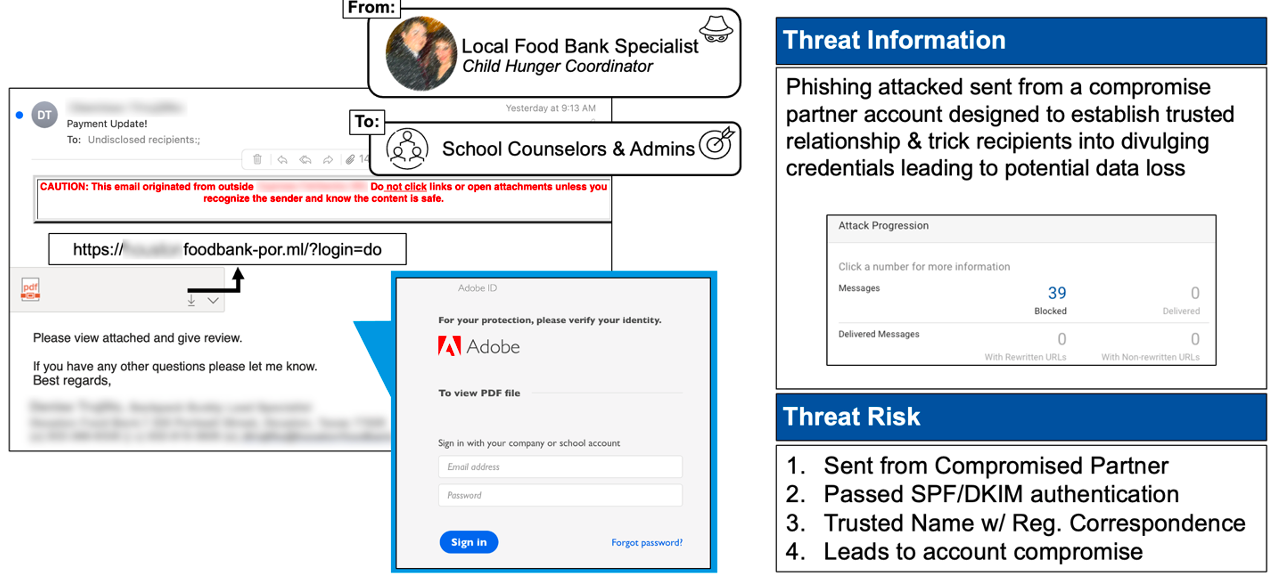
Figure 3. The above credential page is impersonating an Adobe software login.
The anatomy of the attack:
This credential harvest attack was sent from a legitimate, compromised partner account the customer communicates with regularly. As the above image shows, the page uses Adobe brand impersonation, with the attacker attempting to harvest that software’s credentials. Microsoft failed to stop the attack for a few reasons:
- It was a compromised partner account, so it passed SPF/DKIM authentication and is a trusted name with regular correspondence from Microsoft’s static reputation scoring
- The malicious payload (URL) used sandbox obfuscation techniques by being contained within the attachment and not the email itself
- The URL was not detected by Microsoft’s reputation scan, which struggles to identify new malicious URLs
The above attack was very sophisticated, which is why we recommend layers of defence for effective email security. Our Nexus Supplier Risk Explorer feature, for instance, can rank and prioritise the risk level of supplier domains to see if a supplier or partner presents a risk. This is one of the signals we use to assess if potential emails are threats.
DocuSign hybrid threat overview:
People are more likely to activate attacks when they see popular and well-known brand names in malicious emails. When sent from a seemingly legitimate account—in this case, a compromised office administrator—the attack becomes more difficult to detect and more dangerous.
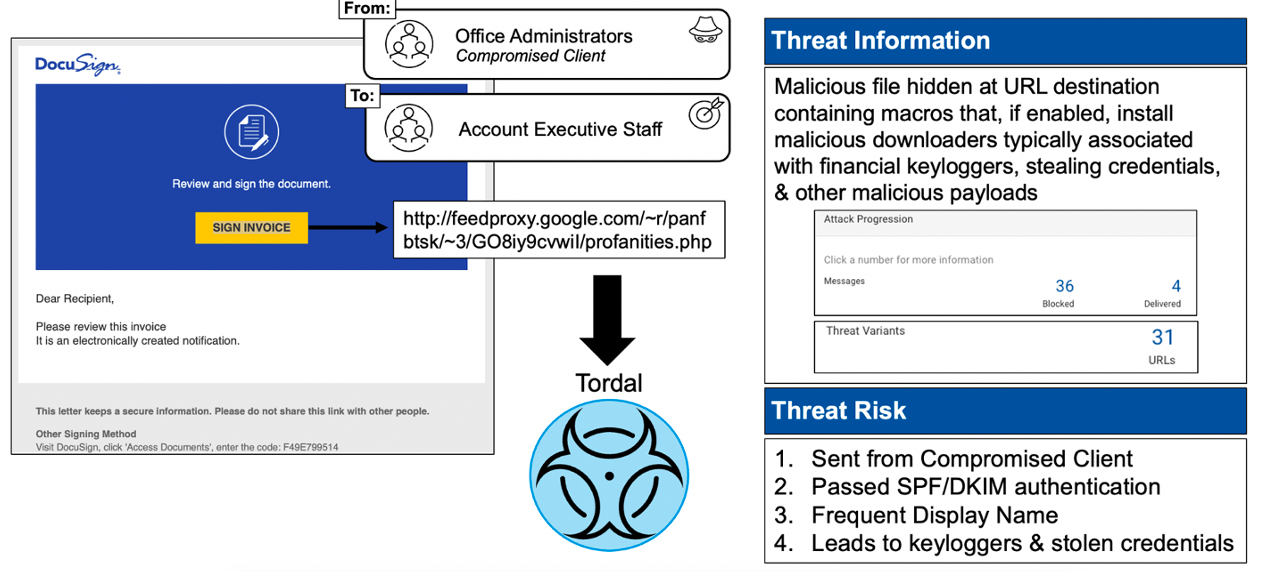
Figure 4. DocuSign hybrid attack from a compromised account, which could lead to keyloggers, stolen credentials and more compromised accounts.
Here’s one example of a Microsoft attack that was missed:
- Environment: Microsoft 365
- Threat Category: URL-Based, Leading to Macro-Enabled Attachment
- Attack Type: Downloader
- Target: Account Executive Staff
The anatomy of the attack:
In this attack sent from a compromised client, the message contained a malicious file containing macros that, if enabled, could install downloaders containing keyloggers and ultimately lead to further compromised accounts. Microsoft missed this threat for a few reasons:
- Since it was a compromised partner account, it passed SPF/DKIM authentication and is a trusted name with regular correspondence from Microsoft’s static reputation scoring
- Microsoft didn’t detect the abuse of the DocuSign brand in the message
- The malicious payload used sandbox evasion tactics
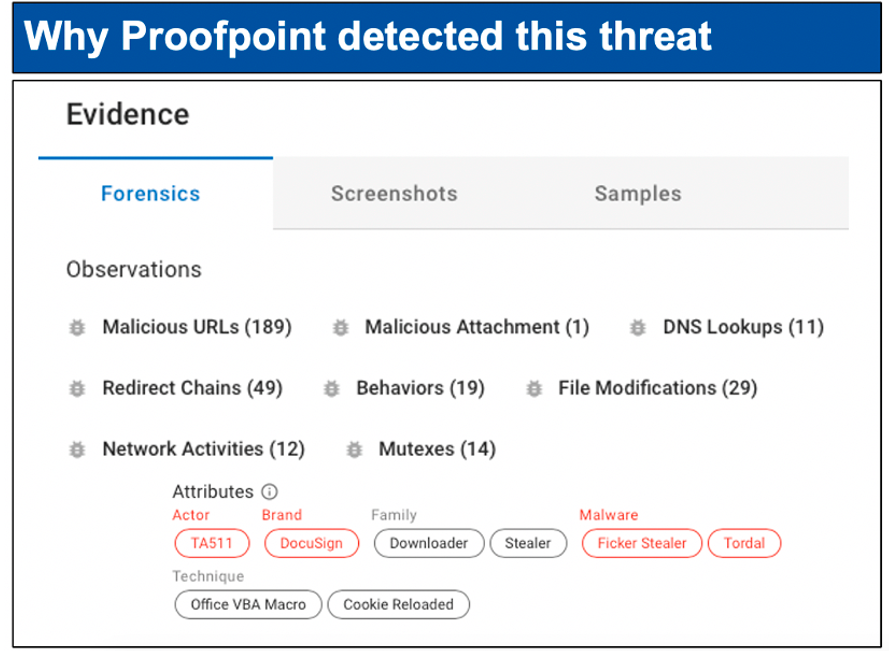
Figure 5. Proofpoint provides detailed visibility into people-centric attacks, arming teams with details about the attack, campaigns involved, and people targeted to understand how and why attackers are trying to cause damage.
Proofpoint’s advanced email security detected and would have blocked these threats from being activated.
How Proofpoint helps stop account compromise
Proofpoint is the only vendor that provides an end-to-end, integrated solution with multiple layers of protection to combat account compromise. We’ve built multilayered detection techniques to defend against constantly evolving threats, including Proofpoint URL Defense, Proofpoint Attachment Defense and Advanced BEC Defense.
Because account compromise is a common problem, we built the Supplier Risk Explorer for our Email Fraud Defense product and include analytics from these insights. This unique tool can provide your team with valuable information about suppliers that may pose a risk to your organisation.
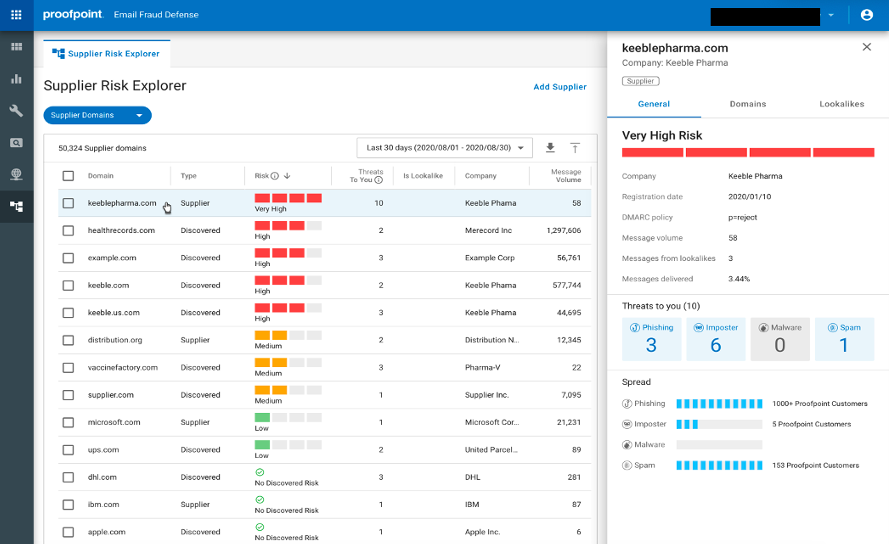
Figure 6. Supplier Risk Explorer identifies supplier domains and provides visibility into which suppliers may pose a risk to your organisation.
Also, Proofpoint provides details on suspicious login activities and potentially malicious third-party applications with our included SaaS Defense feature, delivering insight into account compromise. To protect against compromised accounts further, you can take proactive actions, such as applying extra controls to your Very Attacked People™ with our technology partners. Or you can supplement protection with our Information Protection Platform, which will help you identify and protect against compromised users and data loss.
Again, it’s important to note that in all the examples of the attacks outlined above that Microsoft missed, Proofpoint would have detected and blocked the messages.
Recommendations to prevent account compromise attacks
Proofpoint takes a layered approach to stop account compromise attacks with our Targeted Attack Protection platform alongside our Information Protection Platform, so there are more layers to protect organisations. Some of the layers in our Threat Protection Platform include our leading detection, isolation, authentication, education, and automated remediation capabilities.
There is no one tool or strategy to stop account compromise attacks, which is why a layered, integrated threat protection solution is necessary. To learn more about how the Proofpoint Threat Protection Platform can help protect your environment, take a free Email Rapid Risk Assessment.