Table of Contents
While cybersecurity threats continue to evolve, keyloggers remain one of the most persistent and dangerous tools in an attacker’s arsenal. These stealthy programmes operate silently in the background, capturing every user’s keystroke, from login credentials and personal information to confidential business communications.
In today’s human-centric threat landscape, keyloggers are a direct assault on the most vulnerable link in any security chain: your people. By targeting the very act of typing, these malicious tools can harvest passwords, financial data, and sensitive corporate information. Keyloggers make credential theft easier than ever for cyber criminals who understand that compromising human behaviour is often more effective than breaking through technical defences.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is a Keylogger?
A keylogger is a type of software or hardware that secretly records every keystroke a user types on their computer, mobile device, or keyboard. These programmes run invisibly in the background, capturing everything from passwords and credit card numbers to emails and instant messages without the user’s knowledge.
Keyloggers can serve both legitimate and malicious purposes depending on who deploys them and why. Organisations sometimes use keyloggers for employee monitoring, parents may install them to track their children’s online activities, and law enforcement agencies might employ them during investigations. However, the vast majority of keylogger incidents involve cyber criminals who use these tools to steal sensitive information from unsuspecting victims.
When used maliciously, keyloggers represent one of the most direct threats to personal and corporate security. They bypass many traditional security measures by capturing information at the source — the moment someone types it. This makes them particularly dangerous for harvesting login credentials, financial information, and confidential business data. Unlike other malware that might target specific files or systems, keyloggers focus on human behaviour, making every employee a potential entry point for data breaches and account compromises.
Types of Keyloggers
Anticipating different types of keylogger methods helps organisations identify potential threats and implement appropriate defences. These malicious tools can be broadly categorised based on how they operate and where they’re deployed in your technology environment.
Software Keyloggers
Software keyloggers are the most common type encountered in cyber-attacks today. These programmes are installed directly on a target computer, often bundled with other malware or disguised as legitimate software. They can be distributed through phishing emails, malicious downloads, infected websites, or compromised USB drives. This makes these methods relatively easy for attackers to deploy without requiring physical access to the target system.
Hardware Keyloggers
Hardware keyloggers are physical devices that connect between a keyboard and computer, often disguised as ordinary keyboard connectors or USB adapters. While they require physical access to install, they offer attackers significant advantages by capturing keystrokes from the moment a computer boots up, including BIOS passwords and disk encryption keys. These devices store captured data in internal memory that attackers must physically retrieve, making them less common in remote cyber-attacks but potentially more dangerous in insider threat scenarios.
Browser-based Keyloggers
Browser-based keyloggers are becoming a bigger problem as more of our work moves online. These crafty programmes specifically target your web browser and online activities. Some use JavaScript code injected into compromised websites to capture whatever you type while visiting. Others focus on form-grabbing — basically stealing whatever you enter into web forms like login pages or payment portals. What makes them particularly dangerous is their ability to capture credentials for multiple online services while flying completely under the radar, often without leaving any trace on your hard drive.
Other Specialised Types
Organisations should also be aware of more sophisticated keylogger variants that pose elevated risks. Kernel-level keyloggers operate at the deepest layer of an operating system, giving them administrative-level access that makes them extremely difficult to detect with standard security tools. These advanced threats often require specialised security solutions and can intercept keystrokes before they’re processed by any application.
Other specialised types include memory-injection keyloggers that modify browser memory tables and API-based keyloggers that hook into system functions. However, these remain primarily concerns for high-value targets and advanced persistent threat scenarios.
How Do Keyloggers Work?
A keylogger’s main goal is to silently capture a targeted user’s keystrokes as they type on their device. Installation of a keylogger could be intentional for business purposes, or a user could install it after being tricked by a malicious attacker. Attackers have several modes of infection, including phishing, drive-by installations, vulnerable browsers, or adding malicious content to a seemingly innocent programme installation package.
A truly stealth keylogger runs as a background process without any clues that could give it away. For example, a Windows installation could be performed without any input from the computer owner and immediately log keystrokes without noticeable performance degradation on the device. Targeted users who investigate running processes must identify the malicious background process, but many users cannot differentiate between necessary Windows executables and malicious content.
Good keyloggers organise keystrokes so that an attacker can identify credentials linked with specific accounts. For instance, a targeted user types their bank website into a browser window and then types their credentials into the banking website. The keylogger captures all these keystrokes into a file stored on the local device or directly in the cloud. To avoid losing information due to a loss of Internet connection, a keylogger will usually log keystrokes in a hidden folder and transfer the content to an attacker-controlled server when an Internet connection is available.
Organising log files by application allows an attacker to quickly identify and link stolen credentials with account locations such as websites, local applications, or local network services. Some Trojan malware includes keyloggers but also gives remote control to an attacker, so that the transfer of log files is unnecessary. The attacker can instead remotely access the system and obtain the log files from the local device.
Keylogger programmes are often used for parental monitoring on a minor’s device. For instance, if a minor uses chat programmes to talk to friends online, parents may want to monitor conversations. The keylogger works in the same way as a malicious keylogger, but its use is for protecting a child rather than for nefarious purposes.
Some other standard functionality in a keylogger includes:
- Regularly emails an attacker with the latest keystrokes. This method of sending keystrokes to an attacker is more easily detected when the targeted user’s email account is used, leaving a trail in the “Sent” box pointing to the attacker’s email address.
- Wireless transmission of stolen data using Wi-Fi technology or the device’s data plan, if it’s available.
- In some cases, keyloggers include malicious applications that allow remote control of the local devices.
- Copying clipboard content to detect stored passwords when users copy and paste a password into a window. For instance, stealing clipboard content could give an attacker access to the keys associated with a user’s cryptocurrency wallet.
- Screenshots of desktop windows. With this feature, an attacker can capture information when the user has autofill configured on their browser. For instance, a user might have a cookie stored that remembers the account name for a financial website. The user types the password into the website, but only the password and not the username is captured. With screenshots, the attacker has the auto-filled username in the image, and the password is then keylogged.
- Activity tracking to capture user mouse clicks and device actions. By tracking mouse clicks, the attacker can determine the files and folders commonly opened. This could give a remote attacker the ability to determine important files that contain sensitive information.
Keylogger Use Cases: Malicious and Legitimate
The distinction between legitimate and malicious keylogger use often comes down to consent, ownership, and intent. While the underlying technology remains the same, the context and purpose of deployment determine whether keyloggers serve as valuable security tools or dangerous cyber weapons.
Legitimate Uses
- Corporate monitoring: Organisations track employee productivity and ensure security compliance on company devices with proper notification
- Parental control: Parents monitor children’s online activities to protect them from cyberbullying and inappropriate content
- Security testing: Ethical hackers and developers use keyloggers during penetration testing and usability research with consent
Malicious Uses
- Espionage: Cyber criminals target trade secrets, confidential business data, and government intelligence
- Financial fraud: Attackers steal banking credentials, credit card numbers, and personal information for identity theft
- Credential harvesting: Hackers capture login information to bypass security measures and gain deeper network access
The fundamental difference between legitimate and malicious keylogger use lies in transparency, consent, and legal authority. Legitimate applications protect organisations and families through authorised monitoring, whereas malicious uses violate privacy laws and cause significant financial and reputational damage to victims.
Signs of a Keylogger Infection
Detecting keylogger infections can be challenging since these programmes are designed to operate silently in the background. However, several warning signs may indicate your system has been compromised by keystroke logging malware. Some of the key warning signs to watch for include:
- Slower device performance: Keyloggers consume system resources to capture and process keystroke data, which can cause noticeable slowdowns in computer performance. Users may experience longer boot times, delayed application responses, or general system sluggishness that wasn’t present before.
- Unexpected text behaviour or typos: Some keyloggers can interfere with normal typing functions, causing unusual autocorrect behaviour, repeated characters, or text that doesn’t appear as expected. Users might notice their typing feels “off” or that certain keys seem to register differently than usual.
- Antivirus/EDR alerts: Modern security software can detect many keylogger variants through signature-based detection and behavioural analysis. Pay attention to any security alerts about suspicious processes, unauthorised system modifications, or blocked network connections from unknown applications.
- High network activity from unknown sources: Keyloggers need to transmit captured data to attackers, which can create unusual network traffic patterns. Monitor for unexpected data uploads, connections to unfamiliar IP addresses, or network activity during periods when you’re not actively using internet applications.
- Unusual pop-ups or browser behaviour: Browser-based keyloggers may cause unexpected pop-ups, redirects to unfamiliar websites, or changes to browser settings without user consent. New toolbars, modified search engines, or homepage changes can indicate malicious software installation.
- Increased CPU usage or system resource consumption: Check your task manager for processes consuming unusually high CPU or memory resources, especially programmes you don’t recognise. Keyloggers running continuously in the background can cause sustained increases in system resource usage.
- Suspicious files or unknown processes: Look for unfamiliar files in system directories, temporary folders, or startup programmes that you didn’t install. Unknown processes running with administrative privileges or processes that restart automatically after being terminated may indicate the presence of a keylogger.
If you notice multiple warning signs occurring simultaneously, it’s crucial to run comprehensive security scans and consider seeking professional IT support to investigate potential keylogger infections.
How to Detect a Keylogger
Malicious software authors code stealth features into their programmes to avoid detection, but users have several resources available to help them detect an installed keylogger. Good anti-malware applications detect keyloggers and block them from being installed. Still, malware writers continually change the payload and strategies coded into their software to avoid detection by device defences. It’s still difficult for anti-malware software to detect zero-day threats, which means the malware has not been seen in the wild.
If you suspect that you have a keylogger running on your computer, the first step is to review a list of processes running on the machine. On Windows computers, these processes are shown in Task Manager.
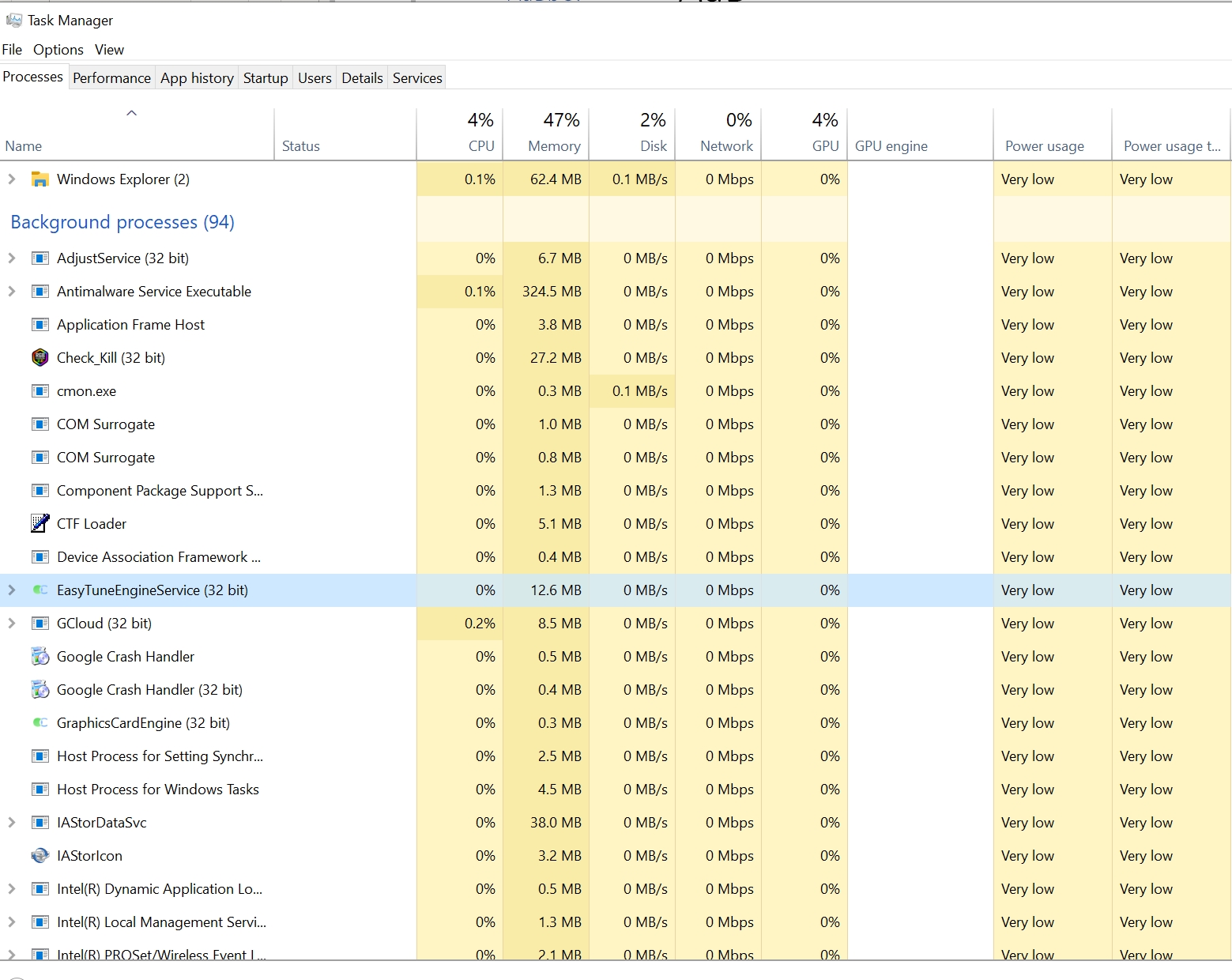
In the screenshot above, 94 background processes are running. A keylogger would appear on this list, but as you can see, it would be difficult to identify a legitimate programme from malware.
For a keylogger to run after a reboot, the service must be configured in Windows to load automatically. Click the “Startup” tab in Task Manager to view a list of executables that run after a reboot.
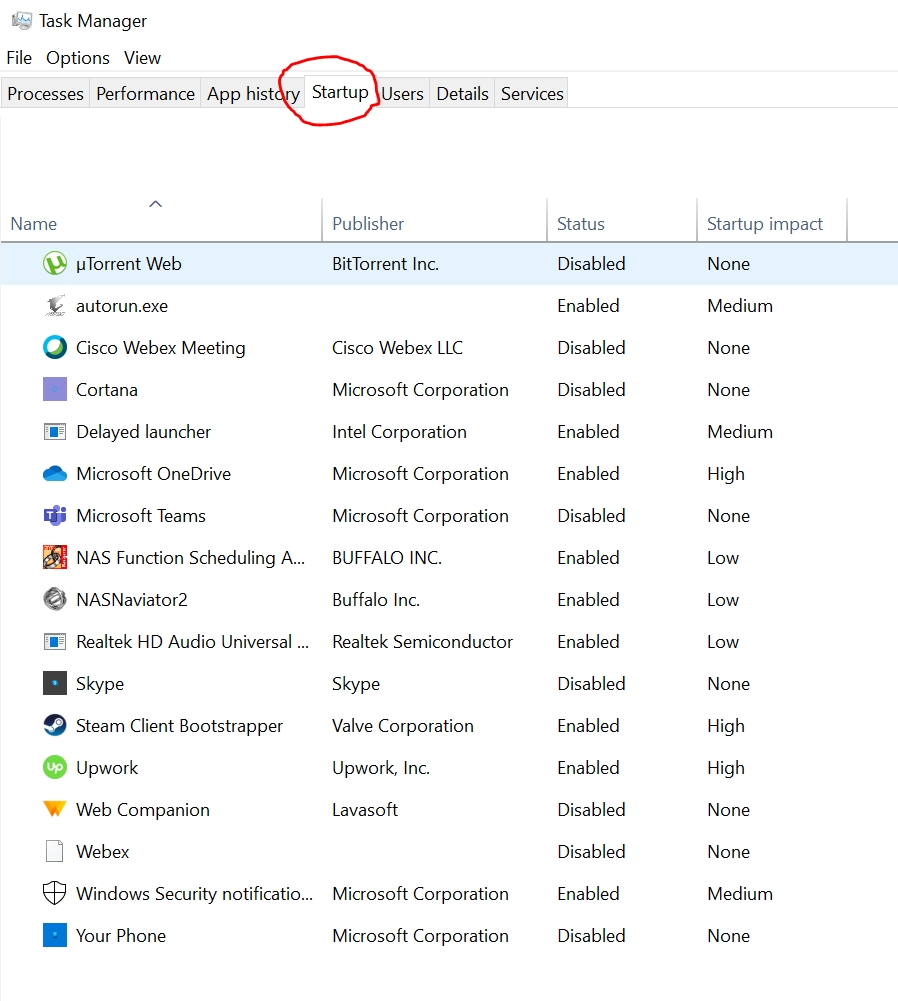
Browse through the list of startup executables to identify if Task Manager shows suspicious programmes. You can disable a startup programme from this tab, but it doesn’t entirely remove the malware from your computer. The executable still exists, and malware developers code for when the application is disabled, and then restart it.
The best way to detect keyloggers is to run anti-malware applications designed to quarantine and remove malicious software. It’s best if the anti-malware programme detects the malicious code before it loads into memory, but false negatives are a possibility if malware can avoid detection. Avoid false negatives by consistently updating your anti-malware software. Updated anti-malware software will detect the latest attacks, including keyloggers. Don’t install software that is not distributed by the official vendor, and never run executable files attached to email messages. If your operating system includes a firewall, outgoing connections might be blocked, but never rely on application firewalls to completely block keyloggers or any malware.
How to Prevent Malicious Keyloggers
Preventing keylogger infections requires a comprehensive security strategy that addresses both technical vulnerabilities and human behaviour. The most effective approach combines multiple layers of defence to create barriers at every potential entry point.
Email Protection and Phishing Defence
Email remains the primary delivery mechanism for keylogger malware, making robust email security essential for prevention. Deploy advanced email filtering solutions that can detect and block malicious attachments, suspicious links, and phishing attempts before they reach users’ inboxes. Modern email security platforms use machine learning and threat intelligence to identify keylogger-laden attachments disguised as legitimate files.
- Implement advanced email filtering with real-time threat detection and attachment scanning
- Block suspicious domains and URLs that commonly host keylogger downloads
- Use email authentication protocols like SPF, DKIM, and DMARC to prevent spoofing attacks
OS and Software Updates
Keeping operating systems and applications current is one of the most effective defences against keylogger infections. Software updates often include security patches that address vulnerabilities that keyloggers exploit to gain system access. Establish automated update policies to ensure consistent protection across all devices.
- Enable automatic updates for operating systems, browsers, and critical applications
- Prioritise security patches and deploy them as soon as vendor testing is complete
- Maintain software inventory to track which applications need updates across the organisation
- Test updates in staging environments before deploying to production systems
Application Control and EDR Tools
Endpoint Detection and Response (EDR) solutions provide real-time monitoring and behavioural analysis to detect keylogger activity before it causes damage. These tools monitor for suspicious API hooking, unauthorised driver installations, and anomalous input behaviours that indicate keylogger presence. Deploy EDR platforms with kernel-level visibility and memory inspection capabilities for comprehensive protection.
- Deploy EDR solutions with keylogger-specific detection algorithms and behavioural monitoring
- Implement application whitelisting to prevent unauthorised software installation
- Use endpoint protection platforms that combine antivirus, anti-malware, and behavioural analysis
- Enable real-time threat intelligence feeds to stay current with emerging keylogger variants
Employee Training to Avoid Malicious Links/Downloads
Human error remains the weakest link in keylogger prevention, making comprehensive security awareness training essential. Regular phishing simulations and education programmes help employees recognise and avoid the social engineering tactics that deliver keylogger malware. Training should cover identifying suspicious emails, understanding safe download practices, and recognising the urgency tactics used in phishing attacks.
- Conduct regular phishing simulations that include keylogger-themed attacks and malicious attachments
- Provide interactive training modules and ongoing continuous education on recognising suspicious emails and social engineering attempts
- Establish clear reporting procedures for employees to report suspected phishing attempts
Secure Endpoint Practices
Implementing robust endpoint security controls creates additional barriers against keylogger installation and data exfiltration. USB port blocking prevents keyloggers from being installed via physical devices while also stopping data theft through unauthorised storage devices. Combine these controls with privilege restrictions to limit the potential impact of successful keylogger infections.
- Block unauthorised USB devices using device control policies and hardware identifier whitelisting
- Implement least-privilege access to limit the scope of potential keylogger compromise
- Use network segmentation to contain keylogger infections and prevent lateral movement
Strong Authentication and Password Management
Multifactor authentication significantly reduces the impact of keylogger attacks by requiring additional verification beyond captured passwords. Password managers eliminate the need to type sensitive credentials, removing the primary target of keylogger attacks. Deploy these solutions organisation-wide to create multiple barriers against credential theft.
- Implement multifactor authentication across all systems, especially for privileged accounts
- Deploy password managers to reduce manual password entry and improve credential security
- Use biometric authentication where possible to bypass keyboard-based credential entry
- Establish password policies that require unique, complex passwords for different systems
Prevention as a Layered, People-Centric Approach
Effective keylogger prevention requires understanding that technology alone cannot solve human-targeted threats. The most successful organisations adopt a human-centric security model that combines technical controls with continuous education and behavioural change initiatives. This approach recognises that employees are both the primary target and the strongest defence against keylogger attacks when properly equipped and trained.
By implementing these layered defences, organisations create multiple checkpoints that keyloggers must bypass to succeed. When one layer fails, others remain in place to prevent compromise. This comprehensive approach ensures that even sophisticated keylogger campaigns face significant barriers to success, protecting both individual credentials and organisational data from keystroke logging threats.
How to Remove a Keylogger
The steps to remove a keylogger depend on the installed malware. Complex, well-written keyloggers can persist on the system even after you think it’s been removed. The best way to remove a keylogger is to run a scan on your system and let the anti-malware application remove it. Most anti-malware software allows you to quarantine suspicious applications instead of automatically deleting them. In a quarantined scenario, the executable files are moved to a directory on the device where users can review them before permanently deleting the files.
If you think that you have a keylogger installed on your device, the first step is to disconnect from the Internet so that any attacker with remote control on the machine will no longer be able to connect. It also stops the malware from communicating with an attacker-controlled server and uploading stolen data to a third-party cloud location.
An infected machine should not be on your private network, but you must transfer an anti-malware application to the infected device. If you don’t already have anti-malware installed, you must download it from the Internet or transfer the installation files from a network computer to the infected one. You can also transfer files from a mobile device such as a smartphone or a portable drive. You should be careful when transferring files from another device, as malware will occasionally transfer files to the connected device.
After installing anti-malware software, run a scan on the computer. The anti-malware programme can be configured to automatically delete files or quarantine them. It should also remove the binaries from memory so that the keylogger can no longer record keystrokes.
How Proofpoint Can Help
Keyloggers remain one of the most persistent and dangerous threats in today’s cybersecurity landscape, silently capturing everything from login credentials to confidential business communications. These attacks succeed because they target the human element — the keystrokes, behaviours, and daily interactions that traditional security tools often overlook.
Proofpoint’s human-centric cybersecurity platform recognises that people are both the primary target and the strongest line of defence against keylogger attacks and credential compromise. Our integrated approach combines advanced AI-driven threat detection with behavioural analytics to create multiple layers of protection against keystroke logging threats.
Rather than treating employees as vulnerabilities to be controlled, Proofpoint’s solutions empower organisations to transform their workforce into active defenders through proactive threat intelligence, adaptive security training, and real-time protection across email, cloud applications, and collaboration platforms. This comprehensive approach ensures that even if keyloggers bypass traditional defences, organisations maintain robust protection through multi-layered security controls and educated users. Contact Proofpoint to learn more.











