Data doesn’t lose itself; people move data in risky ways and into risky locations. And attackers are trying very hard to access your cloud apps and sensitive data through your users.
In a 2020 study of anonymized customer cloud data, Proofpoint found that at least 50% of organizations had at least one user’s cloud account compromised through OAuth abuse (across all cloud apps used in each organization). Nearly one-third (32%) of those compromised organizations had malicious post-access activity—including file manipulation in cloud apps such as Salesforce, one of the most popular enterprise applications.
Salesforce goes to great lengths to protect its applications and organization from attacks. However, Salesforce management can be a compliance nightmare for your organization because IT or business application teams separate from security involvement handle that task. The responsibility for protecting your users’ access to Salesforce apps, preventing sensitive customer and business data leakage from those apps, and complying with data security regulations falls on your security team.
Proofpoint can help your security team with these challenges by providing best-in-class cloud threat detection and comprehensive data loss prevention (DLP) capabilities that can protect your organization from account takeovers, sensitive data leakage and malicious file uploads in your Salesforce applications and accounts.
Safeguarding user access to your organization’s Salesforce apps
Security teams want to prevent external attackers from accessing Salesforce apps in the first place. Most organizations enable user access to Salesforce through the organization’s identity and single sign-on (SSO) providers such as Microsoft Active Directory (AD), Azure AD or Okta Identity Cloud.
Common examples of risky or suspicious logins:
- An attacker uses a user’s account credentials to log in after compromising those credentials
- A user is highly attacked by phishing campaigns and has had their credentials stolen in the past (this user would fall on our Very Attacked People™ (VAPs) list)
- A user logs in from a previously unknown IP address, non-corporate virtual private network (VPN) client or through an unmanaged device
For all these use cases and more, the Proofpoint Cloud App Security Broker (CASB) solution can accurately detect account takeover fraud attempts when users access Salesforce with credentials stored in Microsoft AD, Azure AD or Okta Identity Cloud.
Proofpoint is unique among CASB vendors because we combine email threat telemetry (from Proofpoint Advanced Threat Protection to identify VAPs and recently phished users), cloud threat telemetry (from CASB to identify known threat infrastructure) and user behavior analytics.
This approach gives us greater accuracy and fewer false positives when differentiating between suspicious logins (by attackers masquerading as your users), risky logins by legitimate users and legitimate logins (by your users doing their jobs).
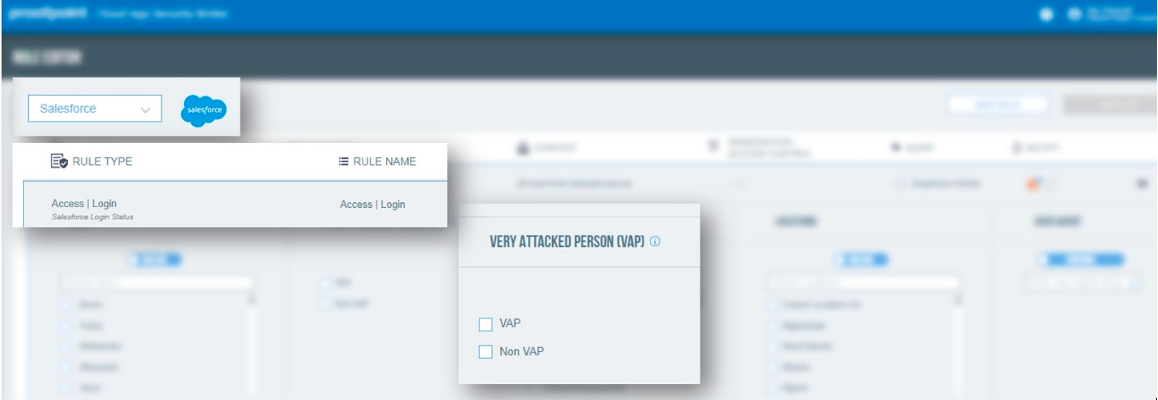
Figure 1. Proofpoint CASB access control policies for Salesforce apps.
Proofpoint customers also want controls against those risks. Following confirmation of a login using compromised credentials, Proofpoint CASB can prevent attackers from using those credentials further. Our automated detection and remediation capabilities leverage your existing investments in popular identity providers (such as Microsoft and Okta) and Proofpoint Threat Response to stop attackers in their tracks.
Security teams can isolate risky login traffic from the rest of your network through Proofpoint CASB and Proofpoint Browser Isolation. That reduces alert fatigue and increases confidence that only legitimate users doing their jobs can access your sensitive data in Salesforce.
Protect users from leaking sensitive customer or business information
Security teams want to stop accidental data leakage and compliance violations when their users, partners or customers enter sensitive data into the organization’s Salesforce app. Common examples of data leakage:
- A negligent user publicly shares files with sensitive business information (such as customer financials or nonpublic financial information)
- A user accidentally uploads the organization’s intellectual property (such as product designs or road maps) onto a publicly accessible forum in Salesforce Communities
- An insider downloads large customer lists from Salesforce CRM before they leave the firm—taking the data with them
In these cases, and others, Proofpoint CASB can use your existing data discovery and classification efforts with our DLP detectors to detect sensitive data and prevent data loss through our Isolation and Proofpoint CASB Proxy products.
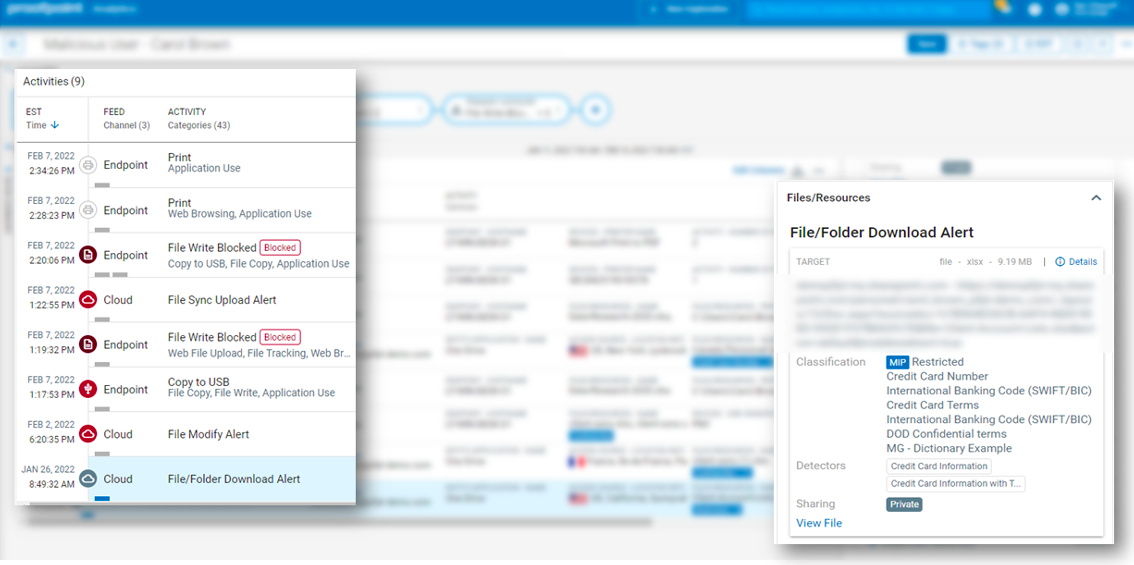
Figure 2. DLP alerts within the Proofpoint Information and Security Platform, including a sensitive file download alert from the Salesforce CRM app.
The advantage of working with Proofpoint is that our DLP capabilities are integrated across channels. DLP detectors built once can be used across CASB, Proofpoint Endpoint DLP, Proofpoint Email DLP and Proofpoint Web Security. And security alerts from all those products are streamed into one timeline view on the Information and Cloud Security platform.
That means your security teams can visualize the before, during and after of each DLP alert or data movement activity without manual effort—no more jumping between DLP consoles as with legacy DLP products. Your teams can save time, reduce alert fatigue and accelerate response to security incidents.
Manage compliance requirements
Security teams want to stop compliance violations when their users, partners or customers enter sensitive data into the organization’s Salesforce apps. Common examples of potential compliance violations:
- An organization’s customer provides their Social Security number or credit card number in plain text in a Salesforce Case
- A salesperson enters sensitive information into a field in the Salesforce CRM that violates customer data policies
- Users violate security policies by discussing customer names and details in a companywide Salesforce Chatter group
For these use cases and others, Proofpoint CASB scans for and alerts security teams about sensitive information appearing in fields and feeds such as Salesforce Case, Task, Chatter and more.
Our DLP detectors identify sensitive data, and the detectors are shared across DLP channels. So, a DLP detector initially built to detect sensitive data leaving the endpoint can be used to detect that same sensitive data in Salesforce. Based on security policies, we will redact that sensitive information within the Salesforce app.
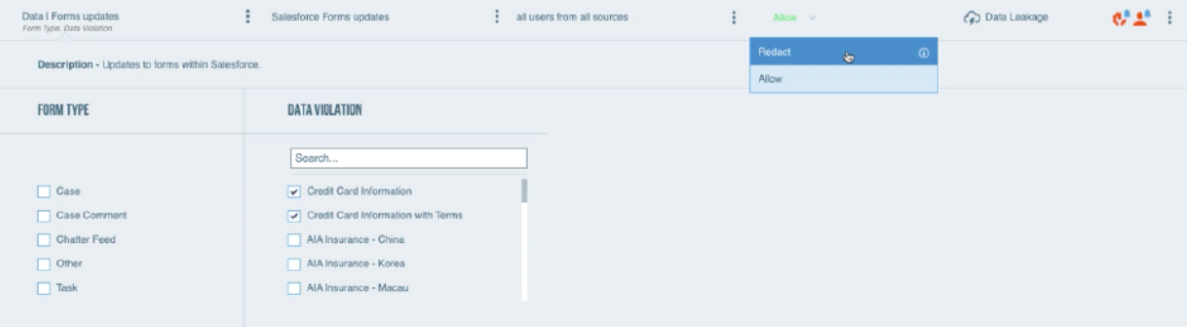
Figure 3. Proofpoint CASB field-level DLP policies for Salesforce apps.
Field-level DLP is critical for most organizations to meet their regulatory and audit requirements that govern Personally Identifiable Information (PII), personal and customer financial data, and protected health information (PHI).
Beyond Salesforce: Manage your customers’ data safely with Proofpoint CASB across your cloud apps
The move to the cloud and the rise of the remote workforce have brought new security and compliance risks. Cloud account takeover, excessive sharing of data and unapproved cloud applications present considerable challenges for security teams. Securing IT-approved and tolerated software-as-a-service applications—such as Microsoft 365, Google Workspace, Box, Dropbox, Salesforce, Slack, AWS, ServiceNow and thousands more—is a priority.
Proofpoint has the only CASB solution that can meet your security needs around data loss, cloud threats and cloud asset access with the fastest time-to-value. It extends our Information and Cloud Security Platform to cloud apps. Proofpoint can protect your users from cloud threats, safeguard sensitive data and intellectual property, govern cloud and OAuth apps, and help your organization stay data security and privacy compliant.
You can deploy Proofpoint CASB in multiple ways: with agentless API connectors, SAML gateway-based adaptive access controls or the inline CASB Proxy. Learn more about Cloud App Security Broker with Proofpoint.











