Threat actors use numerous techniques to obtain account credentials for the simple reason that they open the door to a host of downstream tactics.
When they have credentials, cyber criminals don’t need to break through your perimeter or hunt for existing vulnerabilities to get in. Instead, they can lay in wait undetected, moving through your network, laying multiple malicious payloads, stealing data and targeting other high-value users along the way. Any effective defense against this type of attack requires that you have an understanding of which risky identity is likely to be on the receiving end of it.
Any single identity can be compromised and should be protected accordingly. However, some are more at risk from attacks than others and others are more valuable. When you gain visibility into the identities that are most at risk, you can apply and improve controls where they are needed most.
Here’s a look at the identities you should focus your efforts on as well as some tools that can help.
3 categories of risky identities
Risky identities can be grouped into three categories:
Unmanaged identities
- Service accounts typically go unmanaged by privilege access management (PAM) tools because they are often undiscovered during implementation. In addition, machine identities may be misconfigured to incorrectly allow for interactive login by humans.
- Local admins are set up to facilitate IT support requests on endpoints and are often forgotten after they are created.
- Privileged accounts are often not actively managed because they are not consistently discovered.
Misconfigured identities
- Shadow admins are commonly misconfigured due to the complexity of nested identity groupings in Active Directory. This can make it extremely difficult to see the complete rights and entitlements of all identities. As a result, shadow admins can be granted unintended excessive privileges.
- Identities configured with weak or missing encryption and those that do not enforce strong passwords also fall into this category.
Exposed identities
- Cached credentials are commonly stored on endpoints, browsers, memory, registry and disk. As a result, they can be easily exploited using common attacker tools.
- Cloud access tokens stored on endpoints are also a common means for attackers to gain access to cloud assets.
- Remote application sessions, such as RDP, may be improperly closed. If this happens, cybercriminals can use them to compromise an open session and its privileges—often without the risk of detection.
These identities are risky.
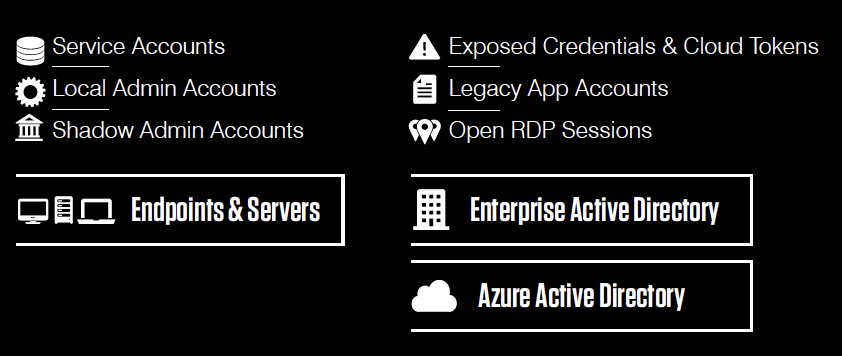
This is where risky identities live.
Proofpoint Identity Threat Defense
Over 90% of attacks rely on compromised identities. That’s why you need Proofpoint Identity Threat Defense. Proofpoint can help you detect active threats and eliminate the gaps in your identity posture that can be exploited by attackers.
Identity Threat Defense is undefeated in more than 160 red team exercises (and counting). It can help you:
- Discover and prioritize your identity vulnerabilities
- Automatically remediate risks on your endpoints and servers
- Detect active threats in the middle of the attack chain at the point of privilege escalation and lateral movement
Proofpoint gives you the tools to keep cyber criminals out and detect them early if they do get in. Our security controls can help you discover and fix identity vulnerabilities before threat actors try to exploit them. At the same time, our deceptive controls alert security teams as soon as a threat actor tries to escalate privileges or move laterally throughout the organization.
If cyber criminals do get past your initial defenses, Proofpoint can help you catch them. Our platform plants deceptive content, or trip wires, that only a threat actor would interact with. Rather than using behavioral analytics for catching attackers, these deceptive lures give you a viable and proven way to catch privilege escalation and lateral movement.
Illuminate your security blind spots
Proofpoint Identity Threat Defense can find the identity risks that exist on 1 in 6 enterprise endpoints. Discover attackers and stop them before they move laterally in your environment by getting your free identity threat assessment.
Get your free copy of New Perimeters
Read more about your risky identities and how to find them in our latest issue of New Perimeters—Identity Is the New Attack Surface.











