We’ve just completed four Proofpoint Protect 2024 conferences. If you’re unfamiliar with Protect, it’s an annual security conference that brings together Proofpoint customers, prospects, partners and many dozens of our staff in cities around the United States and London. At all four conferences, I had the opportunity to co-present multiple sessions about the need for improved identity security and how the Proofpoint Identity Protection solution can help.
But I didn’t just share what I know. I also learned more than a few things about identity threat detection and response (ITDR) from the approximately 500 session attendees and my 11 co-presenters in my seven breakout sessions. I was fortunate enough to co-present with security professionals from CyberArk, Toromont Cat, Turkcell, Tetra Pak and Darling Ingredients, as well as members from our own Proofpoint security team.
7 Takeaways from Protect 2024
There were so many valuable takeaways. I want to share some of what I learned here.
1: There’s intense interest in ITDR
Clearly, there is intense and growing interest in improving identity security in general and identity threat detection and response (ITDR) solutions in particular. While most of the attendees didn’t have much direct experience with ITDR, the drive to learn drove intense interest in our ITDR-centric breakout sessions. Which is why we delivered sessions on the topic seven times across the four Protect conferences.
2: The middle of the attack chain is often new territory
Related to the topic of identity security is the middle of the attack chain, which is where persistence, information gathering, privilege escalation and lateral movement occur. Unfortunately, it’s this middle part where many organisations have major gaps in their existing security defences. Initially, this part of security seemed foggy in the minds of many attendees of our sessions. But I think the sessions provided some important clarity for why it’s so critical.
I find that using the attack chain as a framework is an excellent way to explain the purpose of ITDR solutions like our Identity Threat Defense product. With this framework, it’s easier for defenders to consider the exact steps attackers must take and how they can better defend against them.
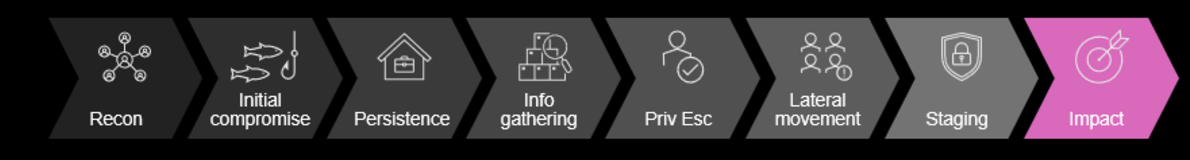
Steps in the attack chain.
3: Deceptions are a game-changer
Audiences were really captivated by our discussion of the use of deceptions for detection and response. The idea of deceptions challenged them to think differently about how to best detect and respond to active threats. For many years now, organisations have been trying to detect active threats using signatures and behaviour-based detective approaches. These methods have had varied success at the expense of significant time and money. The challenge of minimising both false positives and false negatives has proved daunting for many organisations.
Deceptions turn detective analytics on its head. Instead of hunting for threat actors by using massive amounts of data and applying highly tuned detective analytics, deceptions enable an organisation to know when a threat actor is present and is attempting to move around the organisation (in the middle of the attack chain). While deceptions have not gained broad mainstream adoption yet, the audiences in our Protect breakout sessions left with a new way to think about detection and response.
4: AD hygiene is increasingly important
Non-spoiler alert: Active Directory (AD) is a security mess at every organisation that uses it. The reasons for this are largely the same everywhere. For starters, many hands administer it over many years, and most organisations lack comprehensive AD governance. And the list goes on—from short-term and quick fixes to one-off projects to mergers and acquisitions. Those are just the more common contributors. Ironically, the result of all this is that AD can now reasonably be seen as a key tool for attackers.
Given all the attacker tools that are available to automatically take advantage of AD’s misconfigurations and exposures, is it any wonder that interest in ITDR is rising? This interest is driven, in part, by the need for improved AD hygiene. You can read more about the challenges of AD hygiene in this newly published report.
5: MFA isn’t enough
Account takeovers of SaaS-based identity providers—such as Microsoft Entra ID, Okta and Google—are increasingly recognised as a key security challenge as well as a primary source of initial compromise. For attackers to reach the middle of the attack chain, they must successfully make some kind of initial compromise. Many in the audience were surprised to learn that most account takeovers detected by Proofpoint have multifactor authentication (MFA) in place. The key takeaway is that MFA is good. But, given the current tools and techniques used by attackers, it’s not good enough. Today, identity-centric defence-in-depth is required.
6: There are often barriers to adding more security
Another non-spoiler alert: Many organisations are challenged to acquire and deploy new security controls of any type. This includes ITDR. Every organisation has limits, including staff and budgets. That’s nothing new. But a topic that came up multiple times is how the deployment of ITDR challenges the way that security organisations themselves are structured and how identity security is managed.
A common debate was about which team should own the problem—and thus the solution—to the identity security problem. Is it the SOC team, or IT operations, or the identity management team or the vulnerability management team? The stark reality is that one of the key contributors to major breaches are these gaps in organisational problem ownership. It’s in these gaps that there’s a lack of identity security controls—and where threat actors consistently slip through. Organisations that have leading security operations have figured out how to organise and apply ITDR solutions to this problem. Now we must bring the rest along with us.
7: There are multiple drivers to ITDR
What drives organisations to invest in ITDR? For most, it seems to come down to various outside forces. It might be the results from red team exercises or penetration tests. Or it could be documented weaknesses in an audit, or a security incident, or a breach at the organisation or at one of its industry peers. It might even be a CISO who has a vision and a drive to innovate. All these factors serve to drive organisations out of their comfort zones and embrace improved identity security and ITDR.
Conclusion
Clearly, the need for improved identity security is a growing concern among a broad swath of security professionals. My experiences at Protect 2024 are but one viewpoint. But, as has been said in other contexts, the first step to solving a problem is recognising you have one. Given that, I think the security industry is well on its way to solving this one.
If you want to continue this discussion, please join Carlos Rivera of Info-Tech Research Group and me in the upcoming webinar: ‘Securing Identities: The Critical Role of Identity Threat Detection & Response’.











