“The attacker only has to be right once. Defenders have to get it right every time”. This well-known saying has shaped countless cybersecurity strategies. The belief is that a single compromise of our defences can lead to a catastrophic outcome.
As new risks emerge and attackers develop tactics to evade controls, defenders face the daunting task of protecting an ever-expanding array of connected identities. Many companies now embrace resilience strategies, accepting that an incident is inevitable — “It’s not a matter of if, but when”. That’s because defenders have been fixated on the impossible task of protecting everything within the business.
But a new industry approach to cyber defence in recent years has emerged that points the path towards a better way. Instead of protecting everything, defenders should aim to neutralise attackers’ tactics, techniques and procedures (TTPs), which are hard to replace. This disrupts the completion of the attack chain.
What is the attack chain? And how does identity threat defence, also known as identity threat protection, disrupt it? That’s what we’re here to discuss.
The enduring relevance of the attack chain
No other concept has captured the essence of successful cyber attacks like the attack chain (aka the “cyber kill chain”), which was developed by Lockheed Martin in 2011. Even 12 years later, the attack chain remains relevant, while defenders struggle to prevent the most impactful incidents.
While cyber criminals don’t follow the same steps every time, the basic phases of an attack are pretty much always the same:
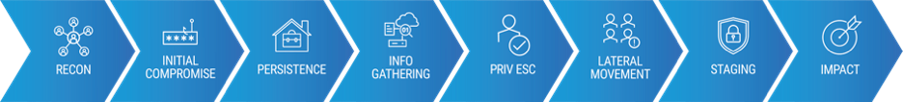
Steps in the cyber attack chain.
The challenge of initial compromise
The first phase in the attack chain is the initial compromise. Modern cyber criminals use an array of tactics to infiltrate companies and wreak havoc on their systems, from BEC attacks to cloud account takeovers and ransomware incidents.
One trend is to exploit trusted third-party relationships to compromise companies through their suppliers. What seems like an innocuous initial email can escalate into a full-scale compromise with great speed. Once attackers gain unrestricted access to a company’s domain, they can infiltrate email accounts to commit fraudulent activities.
One alarming twist to credential phishing emails is that they can evade detection. They leave behind no traces of compromise or malware. Even with the rise of multifactor authentication (MFA), these attacks continue to surge.
Once accounts are compromised through a credential phishing email or a vulnerable remote desktop session, businesses face the next phase of the attack chain: privileged escalation and lateral movement within their networks.
Next phase: privilege escalation and lateral movement
This is the middle of the attack chain. And it’s where threat actors try to breach a company’s defences. Often, they do this by compromising the identities of employees, contractors, service providers or edge devices. Their main goal is to use this initial access to elevate their privileges, typically targeting Active Directory (AD).
AD, which many businesses around the world use, is susceptible to compromise. It can provide attackers with unparalleled control over a company’s computing infrastructure. With this access, they can engage in lateral movement and spread malware across the business, causing more harm.
Finally, the risk of data loss
Attackers don’t rely on a single stroke of luck. Their success hinges on a series of precise manoeuvre. Monetary gains through data exfiltration are often their objective. And once they have navigated the intricate web of identities, they can target valuable data and orchestrate data theft operations.
Defenders must disrupt this chain of events to prevent the loss of sensitive data, like intellectual property or customer identifiable data. Then, they can gain the upper hand and steer the course of cybersecurity in their favour.
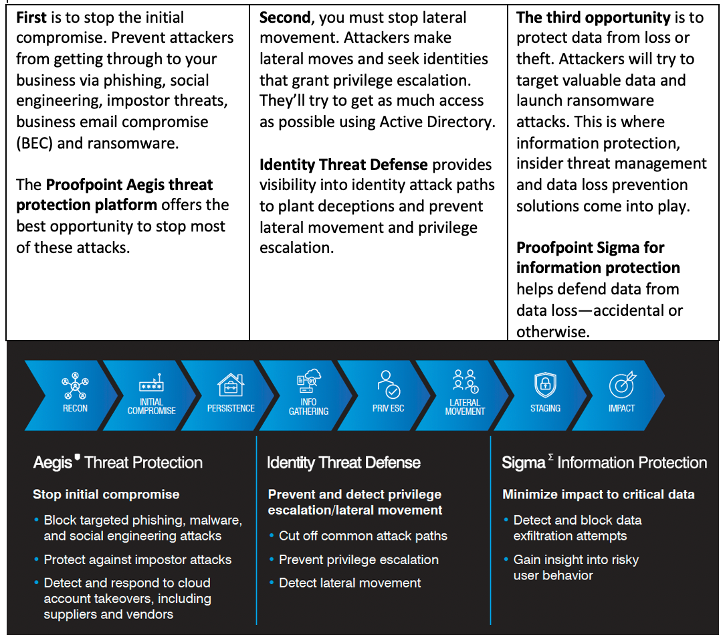
The three best opportunities to break the attack chain.
Building a map of your organisation
The best way to break the attack chain is to build a picture of it within your organisation and look at it in its entirety. With that view, the patterns become unmistakable:
- Most initial compromises are due to phishing and compromised credentials.
- Most privilege escalation and lateral movement occurs through Active Directory.
- Most data exfiltration happens through either those same compromised identities, or the actions of an insider that already has that level of access.
On the path to data exfiltration, cyber criminals will move through networks and systems from one identity to another, escalating their privileges as they go. A typical business has almost infinite attack paths due to the simple fact that AD connects almost every computing asset in the company.
In practice, this could mean anything from using cached credentials on a compromised endpoint to finding a single server where the domain user group is a local admin, enabling their tools to run in that context, or innumerable other combinations.
How do attackers understand and choose from the multitude of attack paths available? They take an approach similar to navigating the real world—the use mapping applications.
The same way you might consult Google or Apple Maps to get around in a new city, an attacker with a compromised identity might use conceptually similar tools to get to where they want to go. Bloodhound, Impacket and PingCastle are examples of these tools. The destination is always the highest level of privilege in AD (known as a tier 0 entitlement, or simply domain administrator).
If an attacker gets into your “city”, you could close roads to stop them from getting to your key assets. But if your people use a road for real traffic flow, closing it isn’t an option. So, you need to set a tripwire on that road to detect attackers while allowing the real traffic to pass through.
These traps could be deceptions or fake credentials which an attacker could use to log in to systems in your environment. These traps will alert you when an attacker tries to use the road. And with that visibility, you can prevent other, bigger issues—like ransomware or data theft.
What really makes attackers miserable is when they can’t get from where they are to where they want to go. If they can’t continue along the path their tools point them to, they’ll give up and leave your environment.
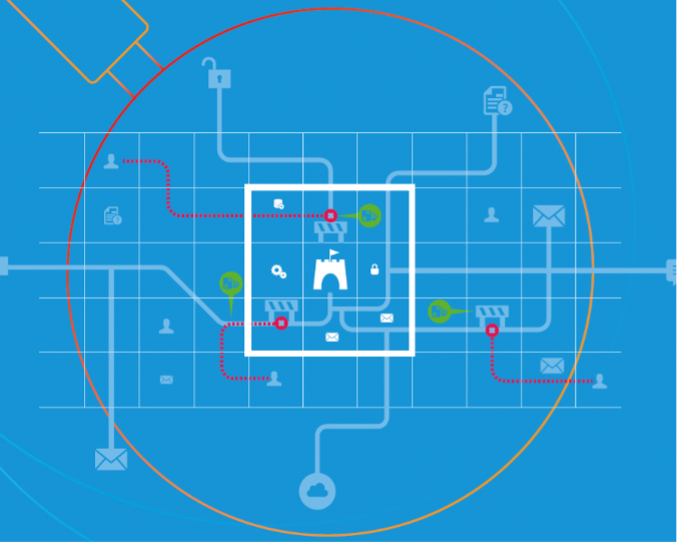
Attackers map networks and systems.
Spotlight on identity threat detection and response (ITDR)
The term ITDR represents a groundbreaking shift in cybersecurity practices. It introduces a new class of tools and best practices to protect and defend identities from bad actors. And it expands how organisations think about how they protect identities. Rather than simply making sure that users who access systems are legitimate, it expands the scope to include proactive defence against identity-based threats.
Today ITDR is now a major cybersecurity market category. This new status is a clear indicator that identities deserve the same amount of control and protection that teams give to networks, systems and software. And this change can’t come soon enough: ESG Research, The Identity Security Paradox found that more than half of enterprises had breaches because of exploited identities and credentials.
Gartner introduced the term ITDR in early 2022 while highlighting security and risk management trends. At the time, Gartner Research Vice President Peter Firstbrook emphasised that businesses had made considerable strides to improve identity and access management (IAM) capabilities. But he noted that “much of it has been focused on technology to improve user authentication, which actually increases the attack surface for a foundational part of the cybersecurity infrastructure. ITDR tools can help protect identity systems, detect when they are compromised and enable efficient remediation”.
The SolarWinds incident in 2020 was an example of how threat actors get access to vulnerable environments. It is a stark reminder of how we should think about identities. It is challenging to prevent a well-resourced adversary from gaining initial access to an environment via a malicious software update or similar supply chain attack. But the subsequent lateral movement, via Golden SAML, toward the ultimate target (often data in Microsoft 365) is much more detectable and preventable than the highly sophisticated method of initial compromise.
When you view the attack chain in its totality, it’s clear that identities play a pivotal role in attacks. As a result, defenders should focus their efforts on proactively protecting them to prevent similar incidents. This starts with investing in comprehensive identity management. Doing so enables businesses to fortify their security posture and protect their valuable assets.
The role of ITDR solutions
If you want to stop cyber attackers from escalating their attacks, you need to adopt proactive measures. You also need comprehensive security controls. With the robust controls in an ITDR solution, you get tools to help you:
- Block targeted phishing and malware attacks
- Detect and respond to account takeovers with speed
- Identify and halt lateral movement
- Prevent privilege escalations
- Fortify defences against data exfiltration attempts
ITDR solutions help you proactively defend against threats at their earliest stages. They do this by scanning each endpoint and identity repository to deliver bottom-up and top-down views into risks related to unmanaged, misconfigured and exposed identities. This gives security teams the visibility they need to take away the attack paths through Active Directory that attackers want to use to deploy ransomware and steal data.
ITDR solutions are a critical tool to break the attack chain. They can help you stop attacks before they can become devastating incidents.
In conclusion
The rise of ITDR as a critical market category proves that awareness about identity-centric risks is growing and that there’s a collective commitment to bolster defences in today’s dynamic threat landscape.
By embracing ITDR and its associated practices, defenders can confront emerging threats head-on. We can ensure the resilience of our businesses in the face of ongoing identity-based challenges. By combining ITDR with solutions across the attack chain that block initial compromise and tools to defend data, we are better armed to break the attack chain.
Identity is your new perimeter. So you need a new set of tools to defend it. Proofpoint Aegis for threat protection and Proofpoint Sigma for information protection join forces with Proofpoint Identity Threat Defense to break the attack chain, providing a platform approach to protect your people and defend your data.
Find out more about ITDR
Break the attack chain. Detect and prevent identity risk to stop lateral movement and privilege escalation with ITDR solutions from Proofpoint.
Get your free copy of New Perimeters
Find more articles and learn how to break the attack chain with Identity Threat Defense in New Perimeters—Identity Is the New Attack Surface.











